



The CYFIRMA research team recently detected a malicious android APK targeting Indian Defence Personnel. Our research revealed that the attack has been active since July 2021.
The APK file in this case is a decoy copy of a promotion letter to the “Subs Naik” rank. Once the victim falls prey to this malicious APK, and upon installation, this app appears as an Adobe reader application icon (look-alike) on the device. Further research revealed that the threat actors were using a variant of publicly available Spymax RAT since its source code is already available on underground forums. Spymax offers different android package builds – and one of the builds has a web view feature that allows the threat actors to inject any web link into the web view module. After the successful installation of the generated APK, it takes the shape of an actual android app. In this occurrence, the threat actors injected a google drive link where-in the threat actor deployed a pdf file containing a list of Indian defense personnel who were awarded promotions to a higher rank.
The threat actors behind the attack are using strategic social engineering techniques, to deliver this and other malicious APK files through WhatsApp as a delivery mechanism. For more details on social engineering tactics, we recommend reading one of our research reports: (Advanced Social Engineering Attacks).
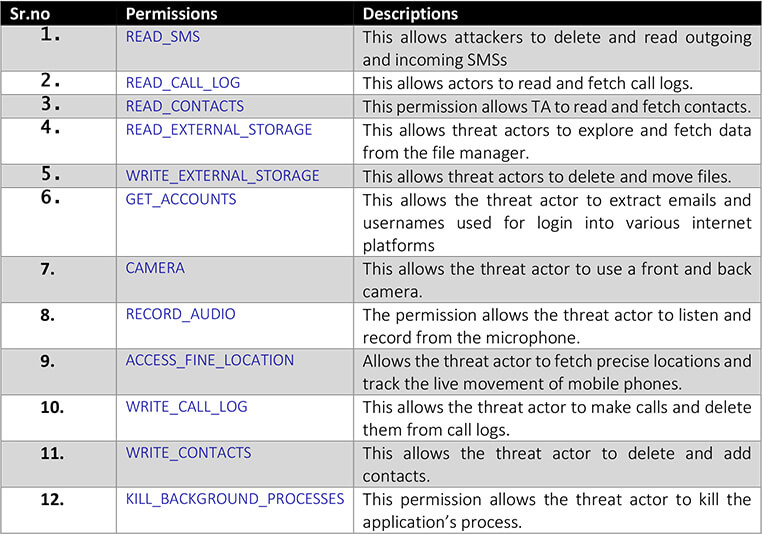
Threat actors are luring Indian Defence Personnel with decoy promotion letters to install malicious android-based Spyware with the aim to exfiltrate confidential information from their devices. The malicious applications obtain several permissions to device resources like – access camera, audio, internet, Wi-Fi, and storage – access to any one of these can be dangerous and catastrophic for national security.
As the target is specifically the defense personnel and since the campaign has been running for quite some time, it is suspected that nation-state threat actor groups are behind the attack to exfiltrate sensitive information. At this moment and with the data analyzed, the CYFIRMA research team cannot attribute the current attack to a specific nation-state threat actor group. What we can infer is that the threat actors involved are less equipped and use easily available RAT. The social engineering techniques used to deliver the malicious APK seem not well-planned.
Below is a screenshot related to a WhatsApp chat that reveals how the threat actors have used social engineering techniques to deliver the malicious APK via WhatsApp as a delivery medium.
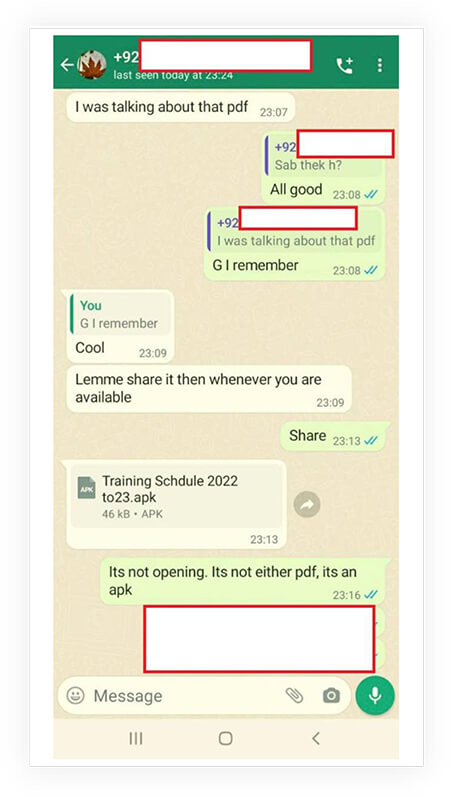
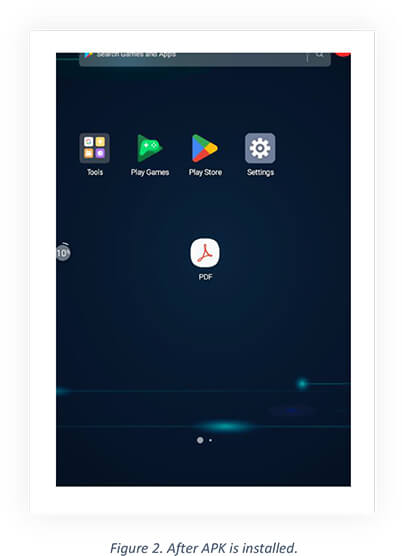
Upon installation of this malicious APK, it disguises itself as a PDF application and appears as a PDF icon on the device.
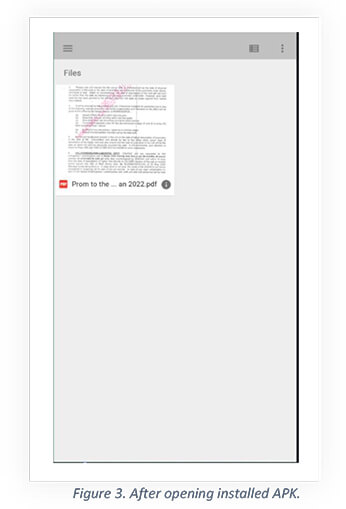
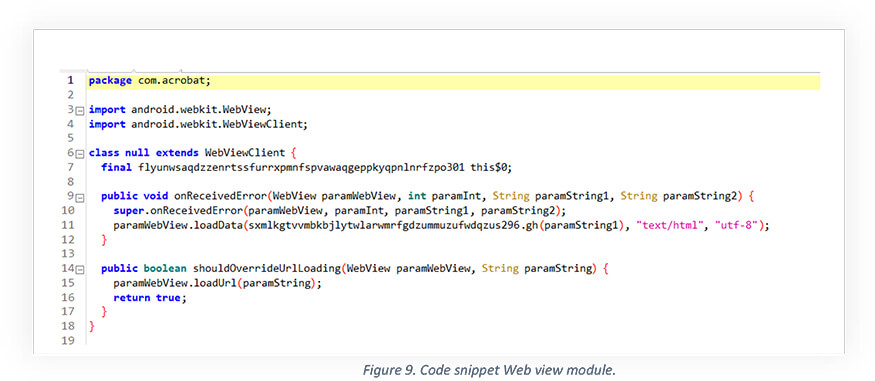
On clicking the App, it opens a google drive link using the web view module which leads to a letter related to the promotion of defense personnel in pdf format as shown below.

CYFIRMA Research team performed a code review of the malicious APK file. Details as below.
Sample Details:
MD5: 8A5C06AE6FD206CEF418BE4B21180F41
SHA1: 54d4f70a9a1d2163d69159f796bb04ced2e68e77,
SHA256: f1fed8fe6c00d3924f65f76e246d1024e51acf096c4388ffdc618086474a2edc
We analyzed the malicious APK file and observed the following code in the “AndroidManifest.xml file.
The code above indicates that the malicious APK used to acquire many dangerous permissions and the permissions mentioned indicate that the malicious APK has the following capabilities:

The source code is highly obfuscated to evade detection and thwart the analysis process as shown in the code snippet.

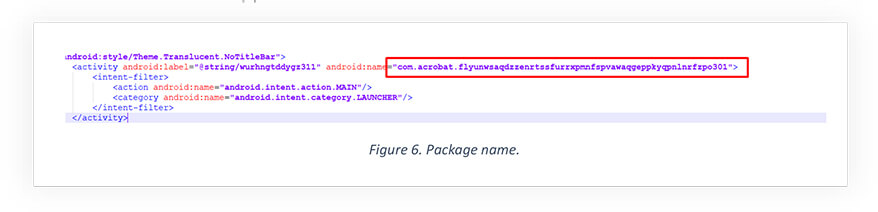
The package is using com.acrobat.flyunwsaqdzzenrtssfurrxpmnfspvawaqgeppkyqpnlnrfzpo301 name to uniquely identify the app in the device. As part of making the app fully undetectable, the package name was also wrapped with a layer of encryption.
The threat actor has obfuscated class names to avoid detection from virus protection algorithms as observed in the screenshot above.
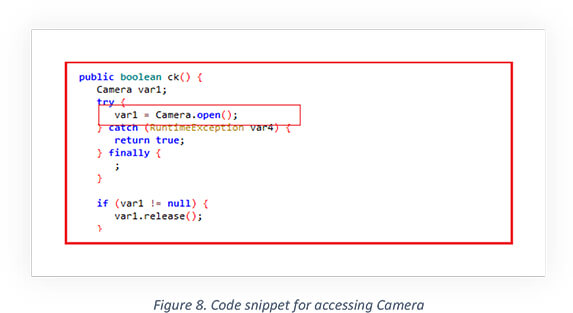
Below is the code snippet for controlling the camera application. The app allows threat actors to use front and back cameras to access the video feeds which can be used to carry out a breach of confidential visuals and video content at will.
This module allows the app to open a landing page that works as a web view.
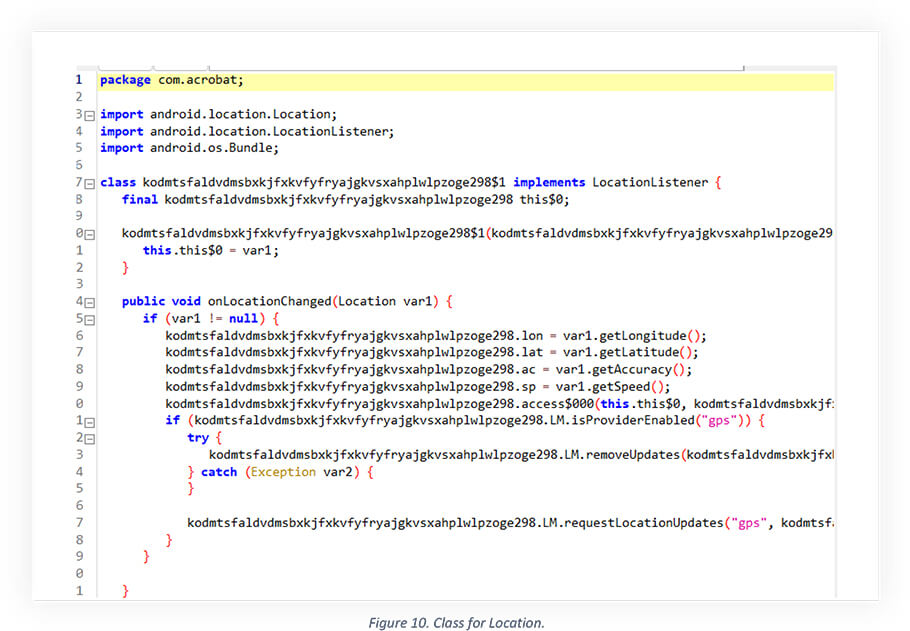
The malicious app allows the threat actors to access the victim’s precise location. The logic defined below is used to access the location of the victim and allows threat actors to keep live track of the victim’s location.
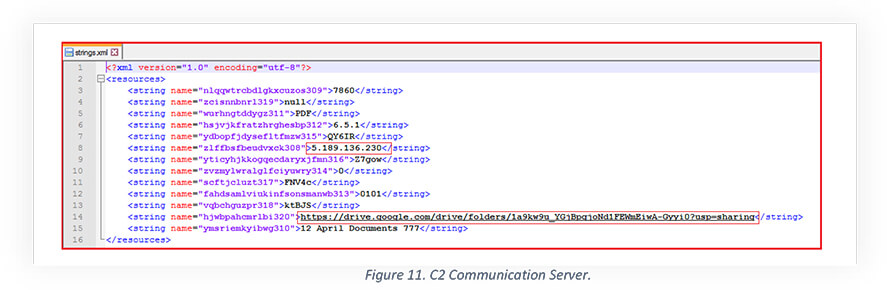
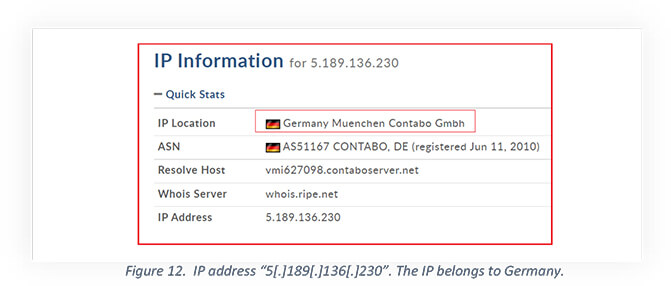
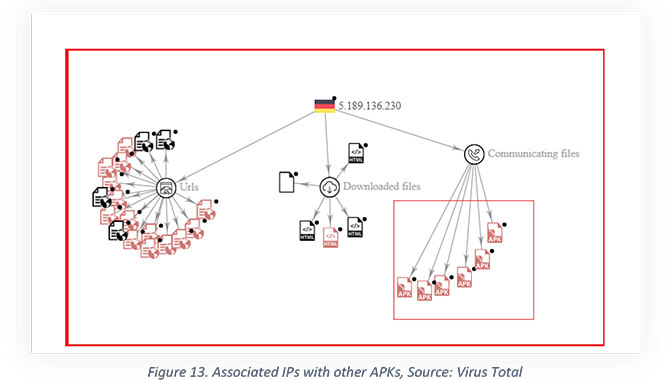
Upon launching, this malicious file, opens a Google Drive URL “https[:]//drive[.]google[.]com/drive/folders/1a9kw9u_YGjBpgjoNd1FEWmEiwA-Gyyi0?usp=sharing” which is hardcoded in the app’s “strings.xml” file as shown above. Also, the string.xml mentioned above contains one IP address “5[.]189[.]136[.]230” which belongs to C2 Server using port number 7860.
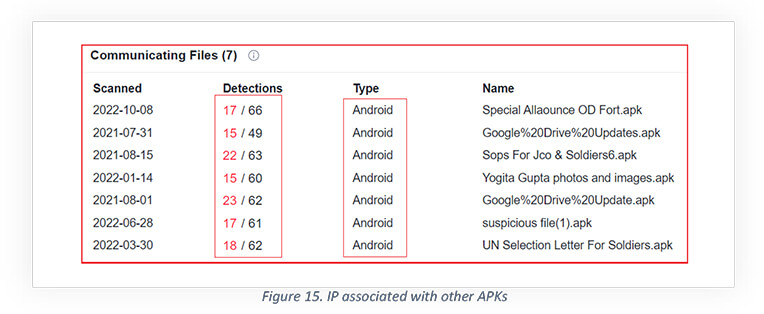
Further as shown below, the IP is associated with other malicious APKs, HTML, and URLs.
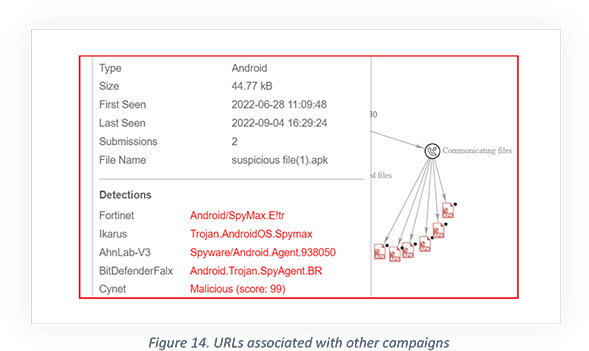
The associated URLs have been used for malicious/phishing purposes in past and the associated communicating APK files are also malicious and detected as spyware by different security solutions.
Following are the hashes corresponding to the communicating files mentioned above:
C&C Server:
5.189.136.230
Following are the names, types, detections, and dates corresponding to the associated communicating files with the IP address “5[.]189[.]136[.]230”. It seems the files are part of the same campaign active since Jan-2022.
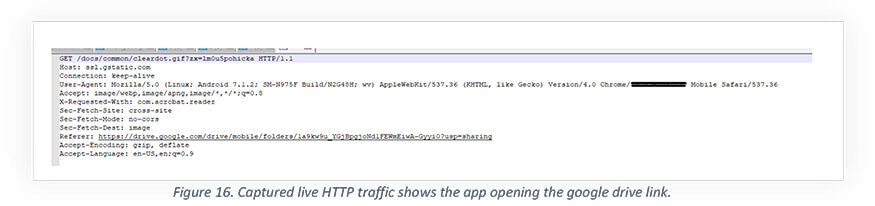
Below is the network traffic captured during the opening of the google drive link.
From captured traffic, we observed the C2 server being active and exfiltrating the data from mobile. Below is captured raw data in HEX value:
| Sr.no | Tactics | Technique ID | Technique Name |
| 1 | Initial Delivery | T1476 | Deliver Malicious Apps via Other Means |
| 2 | Initial Access | T1268 | Conduct social engineering |
| 3 | Initial Access | T1444 | Masquerade as a Legitimate Application |
| 4 | Execution | T1436 | Commonly Used Port |
| 5 | Collections | T1433, T1412, T1432, T1429, T1512, T1533, T1430 | Access Call Log, Capture SMS, Messages Access, Contact List, Capture Audio, Capture Camera, Data from Local System & Location Tracking |
| Sr.no | Tactics | Technique ID | Technique Name |
| 1 | 67dcf9607cdc1966d64aadb3c25d6a08 4dfa877800d0ce233e75b8fc2e41e89a dea441cfaae7a9f86080f3cf34c7f47b bee5884c10f50f094a810cb592fe83db 93d3b042e9121a871e8a023f05d3477b de8b063d405ee5bf715fc1053e0a2a03 bf2187a03fdc0e7c8999d2e1cdeae6d4 |
MD5 | Samples |
| 2 | 5.189.136.230 | IP | C&C Server |