



Risk Score: 8
Confidence Level: High.
Suspected Malware: TimeTime Malware.
Function: Ransomware.
Threat actor Associations: Unknown
First Seen: Dec 2021.
Brief Introduction: TimeTime ransomware is currently trending. It is written in C#.Net (C# is a general-purpose, multi-paradigm programming language) and not obfuscated in any way. After encryption, the “.timetime” extension is added to encrypted files. The ransom demand is observed to be lower compared to other ransomware groups. TimeTime ransomware wants victims to pay only €100 through Paysafecard. The ransom note “@[email protected] and decryptor executable “@[email protected]” is dropped by the ransomware on the system. The ransomware deletes shadow volume copies and the ransomware excludes some of the folders like AppData, Windows, Common Files, WindowsPowershell, ProgramData, Program Files from encryption.
TimeTime Ransomware Analysis:
File Details: As shown in Figure1 and Figure3, following are the details related to the ransomware “TimeTime”.
File Type: Windows PE-32 Executable
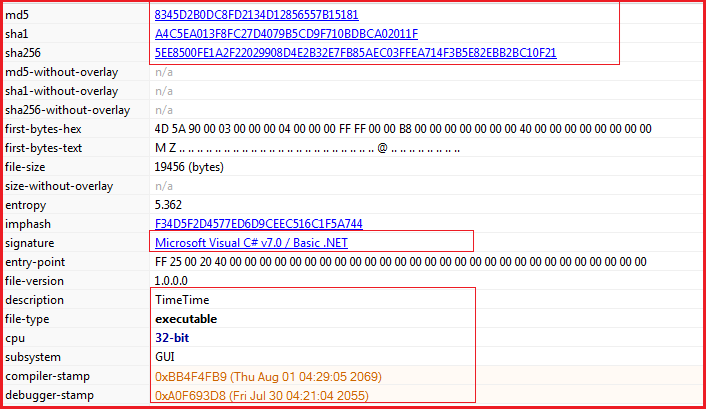
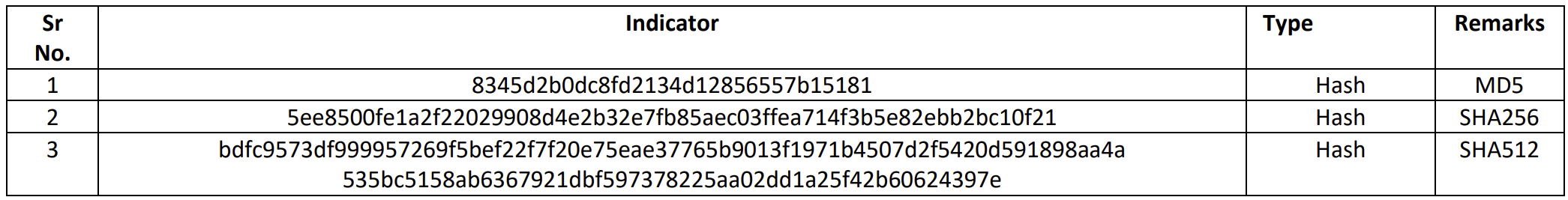
MD5: 8345d2b0dc8fd2134d12856557b15181
SHA256: 5ee8500fe1a2f22029908d4e2b32e7fb85aec03ffea714f3b5e82ebb2bc10f21
Subsystem: GUI
Compilation Time: 1st Aug 2069 (Fake/Suspicious)
As shown in Figure1, the malware is PE-32 bit .Net binary and is not packed (see Figure2).
Figure1
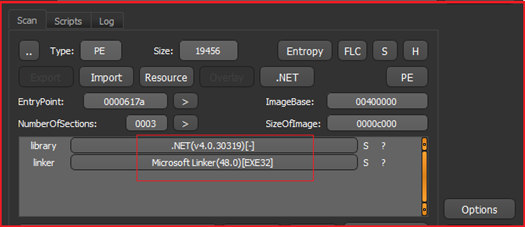
Figure2
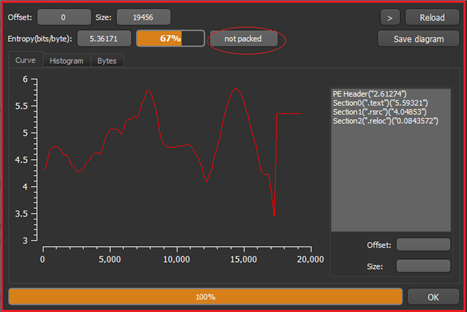
Figure3 below shows the hashes corresponding to malware and the binary has GUI subsystem and a suspicious compile time of Aug 2069 which most probably is fake. The executable is written in C#.Net.
Figure3
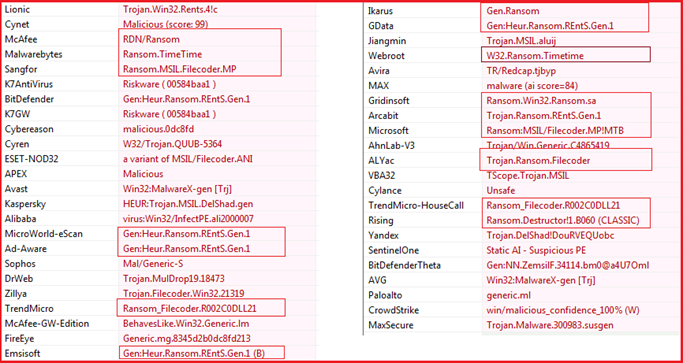
The different anti-malware solutions detected the file as malicious (see Figure4) and many of them detected as Ransomware. One anti-malware solution “Webroot” specifically relates it to “TimeTime” ransomware.
Figure4
The malware implemented the ASLR and DEP which provide hindrance during analysis.
Figure5
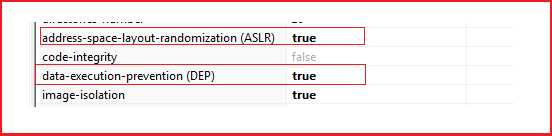
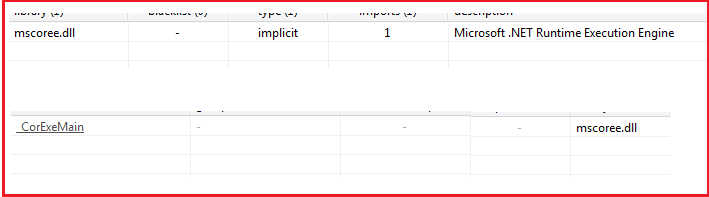
Figure6 and Figure7 show the sections present in the malware and the libraries/API imported by the malware and look quite normal for a .Net Binary.
Figure6
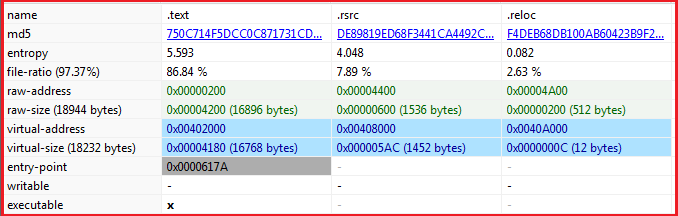
Figure7
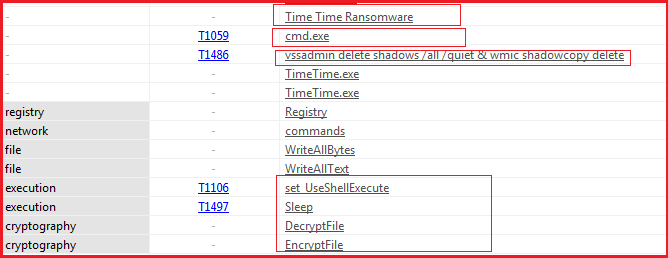
Some of the strings as shown in Figure8 indicate the malicious functionality of the malware as it is using the command line and deleting volume shadow copies through it. The name of the malware (TimeTime) is mentioned, and the strings also indicate the functionality of encryption/decryption that may be present in the malware. So further exploration is required.
Figure8
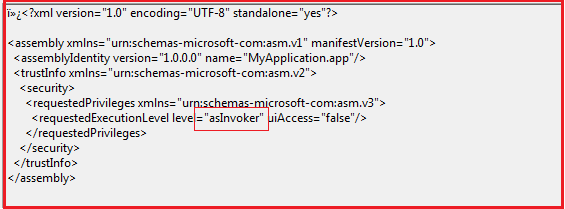
The meta-data shows that the malware can be executed with any permission acquired by the user as shown in Figure9.
Figure9
Upon execution, the malware encrypts the files and adds the extension “.timetime” to each encrypted file as shown in Figure10. The malware also drops the ransom note .txt file with the name “@[email protected]” on Desktop and other folders containing warnings and instructions for the victim to follow.
Figure10
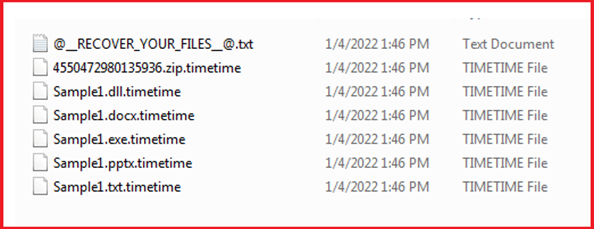
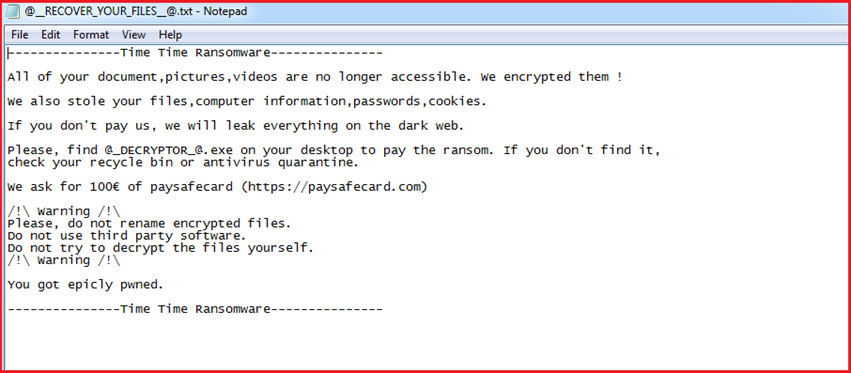
Figure11 shows the contents carried by ransom note dropped by the “TimeTime” ransomware on execution. It states that all of the victim’s pictures, videos, files were encrypted and lots of precious data which includes files, computer information, passwords, cookies, etc. stolen by the malware, and if the victim does not pay the ransom then all this information will be leaked on the dark web. Further, the ransom note also states that the victim should not rename encrypted files or use third-party software for decryption. The ransom note demands the amount of €100 through “paysafecard.com”. Paysafecard is a prepaid online payment method independent of bank accounts, credit cards and other usual financial systems. Customers have to buy the vouchers from local outlets and pay online by entering the code at the respective website.
Figure11
The ransom note also mentions the file “@[email protected]” which was dropped by ransomware on the desktop to decrypt files and on execution, a window pops up as shown in Figure12. On the left ““@[email protected]” is shown which was dropped on the desktop and on the right side the pop-up window is shown which also mentions that the victim’s files are been encrypted and demand psf code to enter for decrypting files. Upon execution, the ransomware after dropping this “@[email protected]” file also executes it, and a pop-up window is displayed on the screen without user intervention.
Figure12
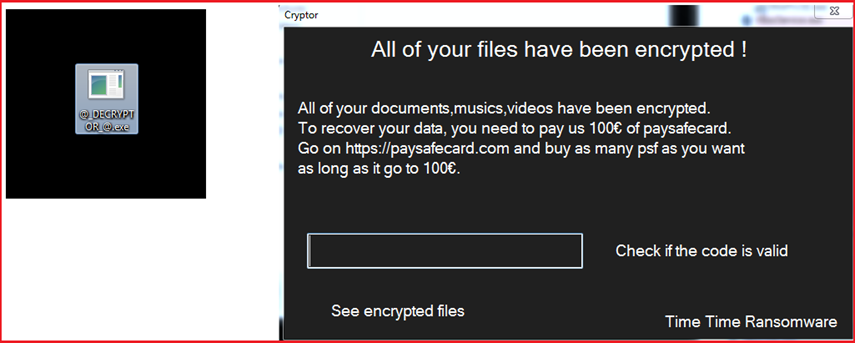
Figure13 below shows the process tree corresponding to malware execution. The ransomware deletes shadow volume copies by using window utilities vssadmin and wmic by executing commands “vssadmin delete shadows /all /quiet” and “wmic shadowcopy delete” over the command prompt. The malware also executes command “bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no” to disable windows boot recovery option and command “wbadmin delete catalog -quiet” also executes to delete backup catalog to prevent victim from system recovery.
Figure13
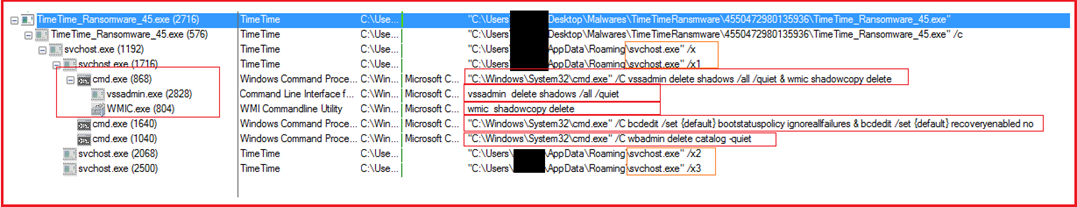
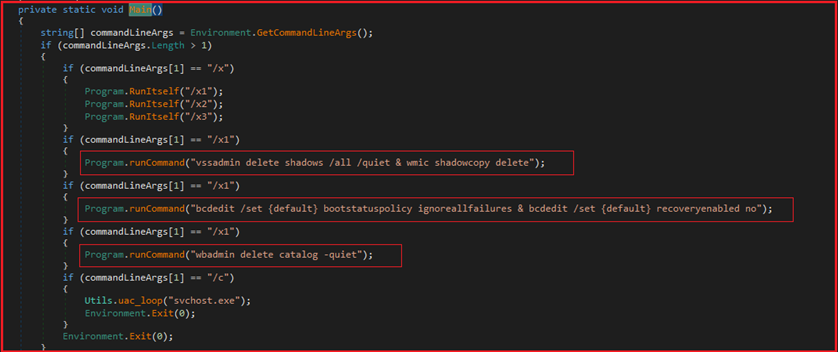
Figure14 shows reverse-engineered code corresponding to malware and the logic is defined to execute the above-mentioned commands to delete shadow volume copies, delete the backup catalog and to disable windows boot recovery option. As per the command line argument “/x”, “/x1”, /”x2” or “/x3” passed corresponding commands will execute.
Figure14
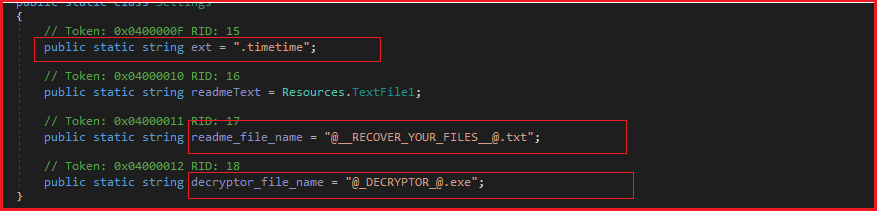
Here in Figure16 below shows the malware initializing strings for the extension “.timetime”, ransom note file “@[email protected]” and decryptor executable file name “@[email protected]” which is further used to add an extension to the encrypted files and drops the ransom note and decryptor executable with the same name on the system.
Figure16
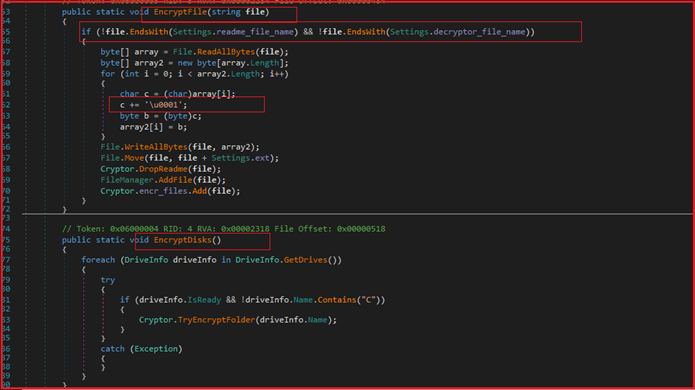
As shown in Figure17 below, the ransomware defined the logic to encrypt files and disks. Before encrypting files, the ransomware checks the name of the file and if it is not equivalent to “@[email protected]” and “@[email protected]” then it encrypts the file and during the encryption process “\u0001” is added to each byte.
Figure17
As shown in Figure18, the ransomware excludes some of the folders containing strings AppData, Windows, Common Files, WindowsPowershell, Microsoft\Provisioning, ProgramData, Program Files, Cache, $ from encryption.
Figure18
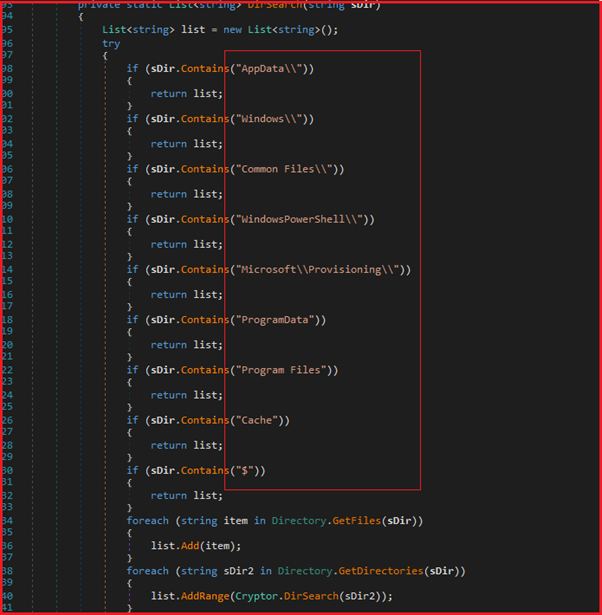
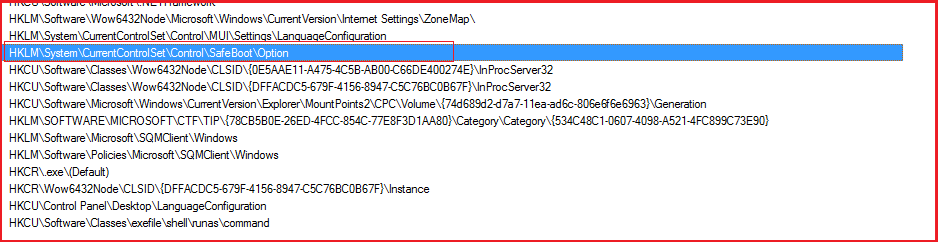
Figure19 shows a snippet for registry access by the ransomware and using “safeboot” option to gain persistence and run in safeboot mode.
Figure19
The ransomware creates a new registry entry named “TimeTime” under HKCU. A new value is created each time under “HKCU\TimeTime” whenever a file has been encrypted by the ransomware (see Figure20 below).
Figure20
The ransomware has the following functionality/capabilities:
・Capability to collect system information.
・Synchronization capability to handle multiple processes and threads and to access shared resources.
・Capability to handle windows/GUI functions.
・Capability to search Drives, Folders.
・Capability to access registry entries and manipulate them.
・Capability to create new threads and processes.
・Ability to access registry entries and manipulation.
・Capability to sleep or deactivate when want to hide itself.
・Ability to handle, search, open, write, access files.
・Ability to encrypt files.
・Capability to handle command line arguments and command execution.
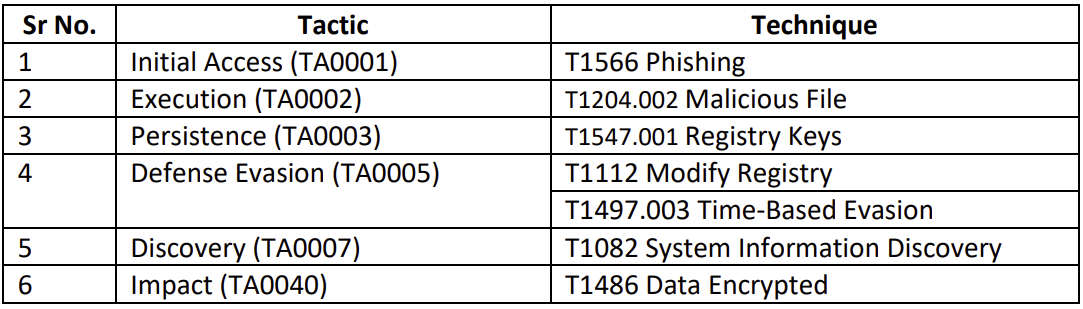
Mitre Attack Tactics and Techniques:
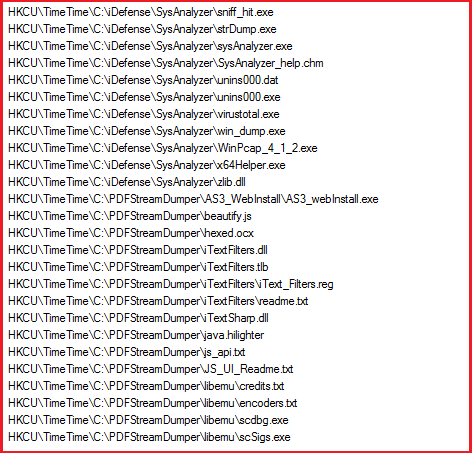
List of IOCs:
Recommendations:
・Implement complex password policy with renewal at regular intervals.
・Implement Multifactor Authentication policy.
・Regularly update all software on all systems, network and other devices and turn on automatic updates if possible.
・Implement Role-Based access policy and restrict it to minimal as per the requirement.
・Implement Internal threat management policy which includes training employees on the latest threats and ransomware attacks and what to do in such scenarios.
・Restrict employees’ ability to click or open suspicious/unauthorized links and files, specifically on organization devices.
・Must implement regular back-ups policy, more than one back-ups and kept one on a separate network and other isolated offline at a different place.
・Use best-in-class IDS/IPS, firewall and other antivirus/anti-spam/anti-ransomware and anti-malware solutions.
・Regular audits are necessary from third party.
・Regular vulnerability assessment and patching policy.