



8 Mar 2021
SilentFade (“Silently running Facebook Ads with Exploits”) gang, the hacker group infamous for cyberfraud, and known for their sophisticated and rare modus operandi to target Facebook users, has grown leaps and bounds to become a global threat defrauding victims to the tune of millions. The malware can run ads on Facebook, without the user’s knowledge, by exploiting a bug on the platform. The social network giant revealed that the malware has a Chinese origin and allowed hackers to siphon $4 million from user’s Facebook linked payment accounts.
Researchers recently noticed Frank rootkit and after having analyzed it, found that it has many similarities to the campaign TTP’s run by the SilentFade gang. A rootkit is a malicious software that allows an unauthorized user to have privileged access to restricted areas of the operating system and designed to remain stealthy and persistent.
The latest investigation, which has brought to light the SilentFade group’s activities in Southeast Asia, apart from multiple geographies, shows that the group, despite being legally prosecuted via its front/shell company, continues to target the mammoth Facebook userbase through their lucrative advertising platform.
The highest number of incidents for the past two months were detected in India, Brazil, Indonesia, Italy, Germany, Algeria, Malaysia, Russia, France, and Egypt.
Following are the country-wise incident numbers:
India – 603
Brazil – 255
Indonesia – 221
Malaysia – 137
Philippines – 96
Vietnam – 71
Thailand – 27
Singapore – 24
Window Trojans
Credential theft
Vulnerabilities and Exploits
Malware Implant
The primary motive of the attackers appears to be:
Financial Gains
Exfiltrating Sensitive Information
Arrives on victim devices via Adware bundles and pirated software installers.
Run Malicious Ads using Compromised Accounts and linked victim payment methods.
Possibly downloaded by other malware.
According to Facebook, the SilentFade gang began operating in 2016, when it first developed a malware strain named SuperCPA, wherein CPA refers to Cost Per Action, primarily focused on Chinese users. This malware was said to be an unknown entity but believed to be used for click-fraud, through an install base in China.
The social media giant revealed that the group abandoned the SuperCPA malware in 2017 when they developed the first iteration of the SilentFade malware. This early version infected browsers to steal credentials for Facebook and Twitter accounts, with a focus on verified and high-follower profiles.
Development on SilentFade gathered steam in 2018 when its most advanced version and the one used in the 2018 and 2019 attacks came to the spotlight.
Facebook discovered SilentFade’s operations in February 2019, following reports from users of suspicious activities and illegal transactions originating from their accounts.
During the subsequent investigation, Facebook said it found the group’s current and previous malware strains, as well as campaigns dating back to 2016, and even tracked down the gang’s operations to a Chinese company and two developers, which the company sued in December 2019. Facebook stated that it found ads by the two SilentFade developers posted on underground hacking forums where they were willing to buy web traffic from hacked sites or other sources, and have this traffic redirected towards the pages hosting the SilentFade-infected software bundles.
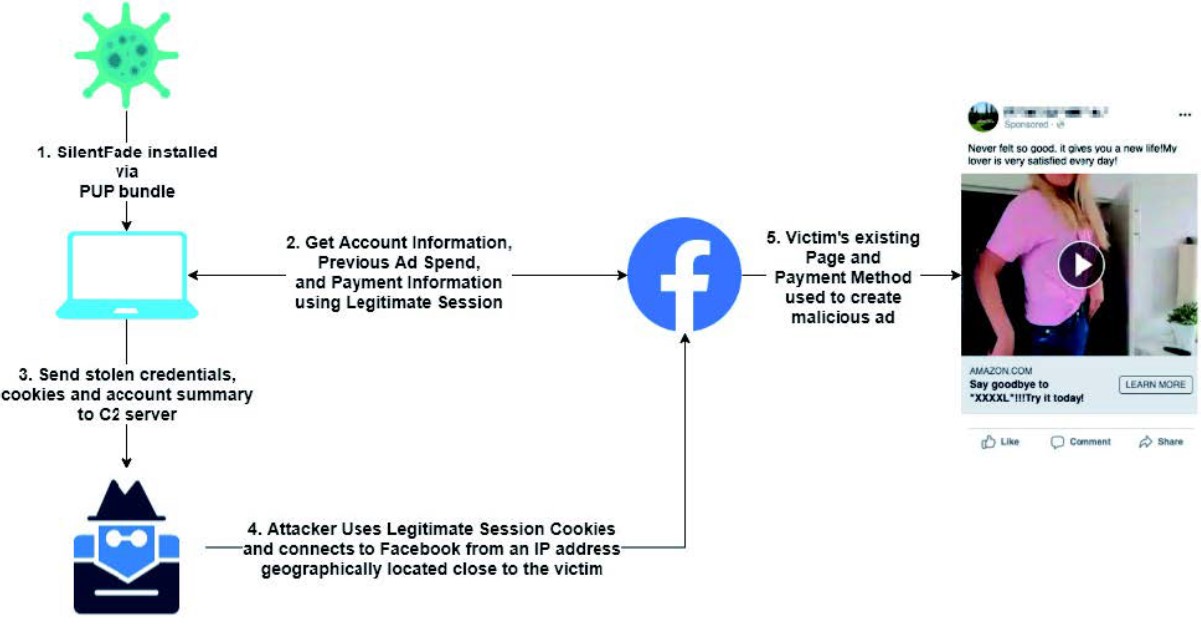
The malware consists of many components with the main downloader component being included Potentially Unwanted Programs (PUPs) bundles as Facebook platform itself was not used to propagate the malware. The downloader application (seemingly legitimate) either download a standalone malware component or a Windows service installed as “AdService” or “HNService”.
Once installed, SilentFade allows attackers to steal only Facebook-specific stored credentials and cookies from major browsers, including Internet Explorer, Chromium, and Firefox.
After stealing Facebook-related credentials, SilentFade obtains the metadata of a Facebook account which is the payment information and total amount previously spent on Facebook ads using the Facebook Graph API.
The stolen data is then sent to the C2 servers as an encrypted JSON blob through custom HTTP headers.
The C2 server stores the data and logs the IP address of the incoming request for the purpose of geolocation.
SilentFade would then be able to use the compromised user’s payment method (credit card, bank account, or PayPal account) to promote malicious ads on Facebook.
SilentFade utilized a combination of a Windows trojan, browser injections, clever scripting, and a bug in the Facebook platform, showing a sophisticated modus operandi rarely seen with malware gangs targeting Facebook’s platform.
As the name suggests, SilentFade’s credential-stealing DLL component only retrieved Facebook-specific stored credentials and cookies located on the compromised browser, thus illustrating the dedicated target persistence.