



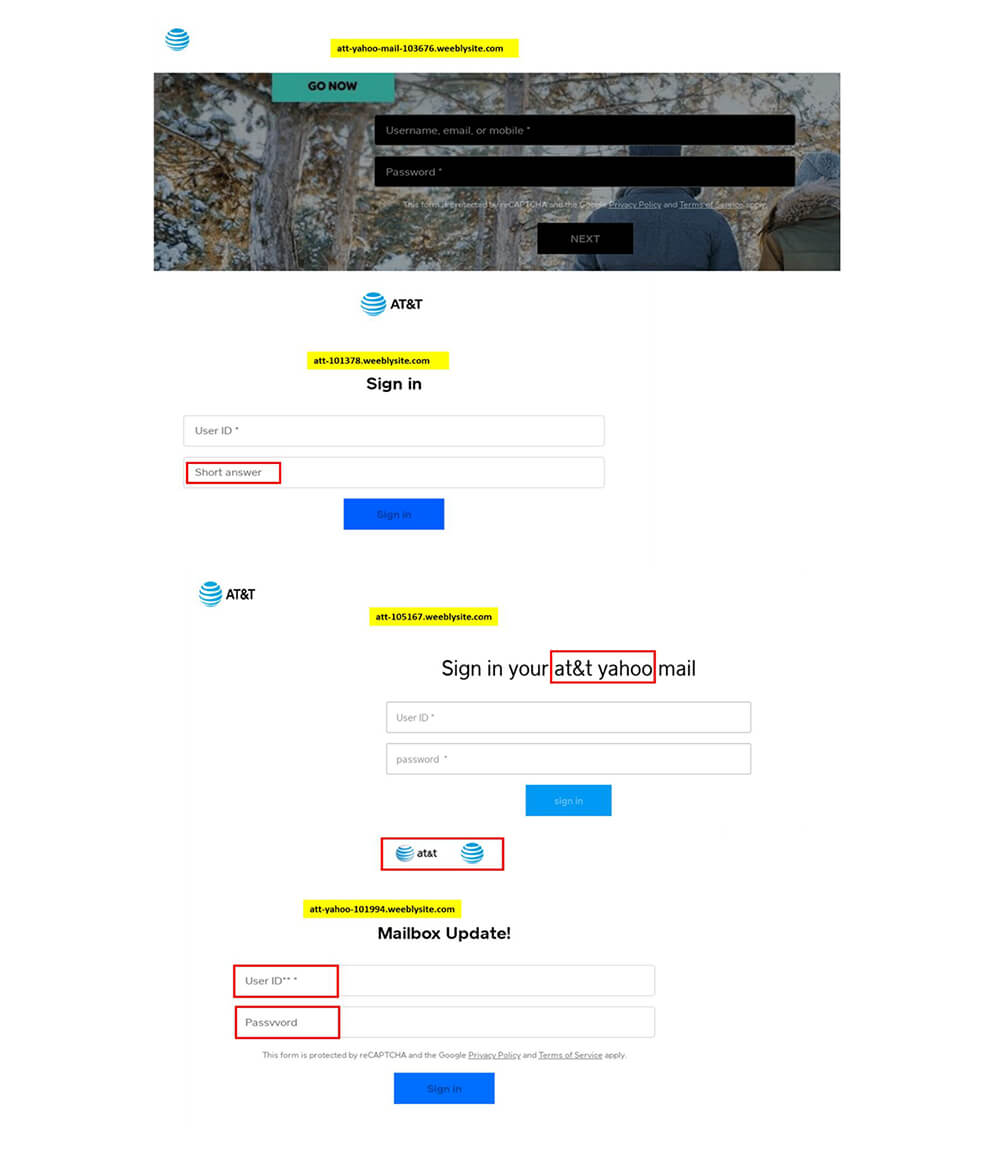
The CYFIRMA research team observed threat actors using free website builders to clone and deceive popular brand websites for phishing attacks. This research paper will detail how phishing attacks targeting AT&T users leverage free website builders like Google Sites and Weebly Sites.
Attack Type: Impersonating legitimate websites, credential harvesting, and account takeover
Recently, a data breach at Australia’s second-largest wireless carrier led to 9.8 million customers’ personal information being exposed. Similarly, the breach at a Malaysian Mobile Virtual Network Operator (MVNO), accounting for the exposure of 1.2 million subscribers’ data, and allegedly perpetrated by the financially motivated Desorden group, indicated the focus of threat actors towards the telecom industry. Research on ongoing attacks on the telecom industry led us to phishing attacks targeting AT&T customers where the threat actors were observed to be using free and popular website builders like Google Sites and Weebly Sites.
In contrast to the large number of cyberattacks that use dark web infrastructure to carry out malicious activities, threat actors are increasingly utilizing web- based application platforms to ensure that phishing emails reach the potential victim’s inbox. In this regard, websites impersonating trusted brands are created for both fraud and credential theft attacks. Google Sites and Weebly Sites are among the two free website builders that make it easy to create authentic- looking websites. As is the norm among threat actors, these free website builders significantly contribute to phishing attacks by facilitating the impersonation of popular brand pages, to exploit free services for malicious purposes. During our investigation, we discovered numerous AT&T phishing websites built with Google Sites and Weebly Sites.
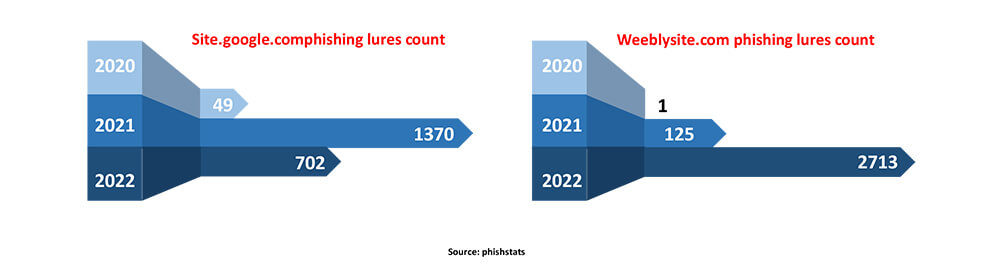
Free online services being used for malicious activities is old news, but it is important to keep an eye on these services to understand the evolving threat landscape. We noticed several phishing URLs that utilized iPhone 14 Pro as lures using sites. google.com. This URL and the examination of recent data breaches in the telecom industry led us to an ongoing phishing attack targeting AT&T users using Weebly and Google Sites website builders. Based on the available data, usage of Weebly in phishing attacks has increased significantly compared to Google Sites.

Creating websites on Weebly and Google Sites is a no-brainer activity, and the drafted site will be up and running as soon as it’s published while using reliable infrastructure provided by well-known brands. Additionally, these free services also provide the option to customize the URLs that threat actors can use to mislead legitimate users to malicious sites.
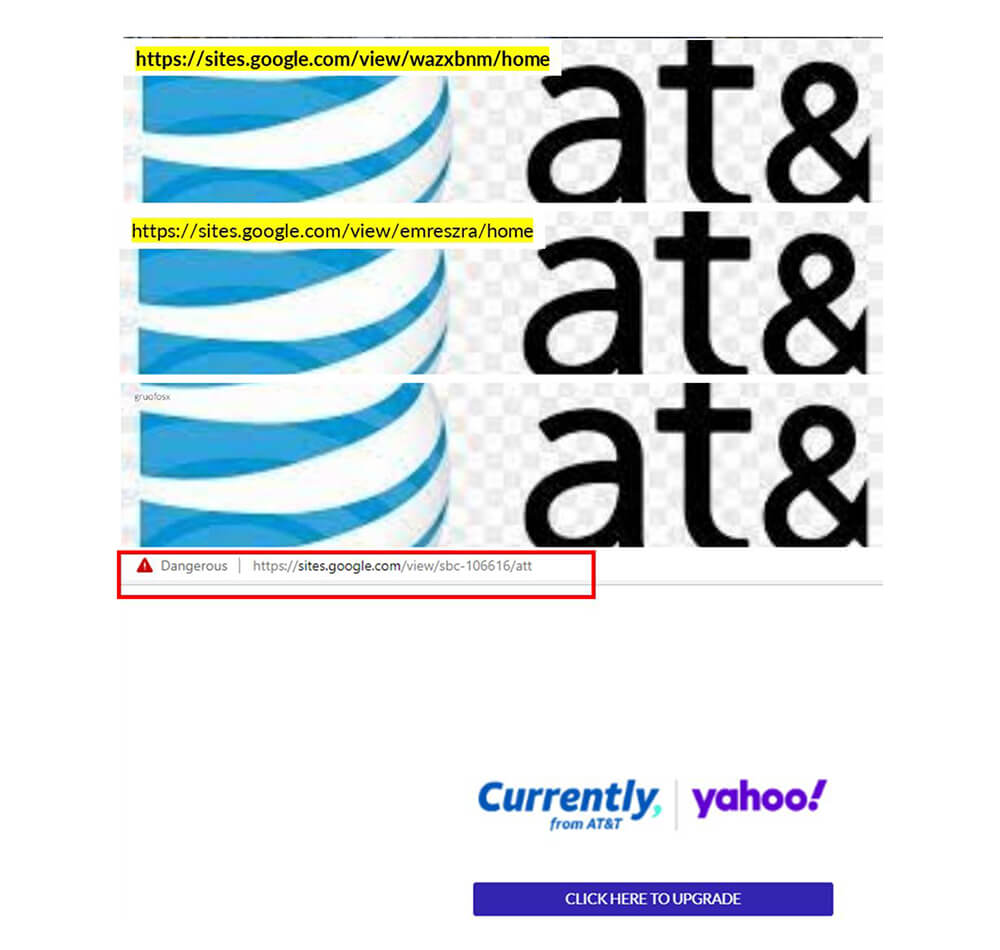
AT&T Phishing Attacks Powered by sites. google.com
In our research, we observed numerous phishing sites created using free services that were targeting AT&T users. Investigation of AT&T phishing sites that leveraged Google Sites led us to another free service provider, Weebly.
AT&T Phishing Attacks Powered by Weebly
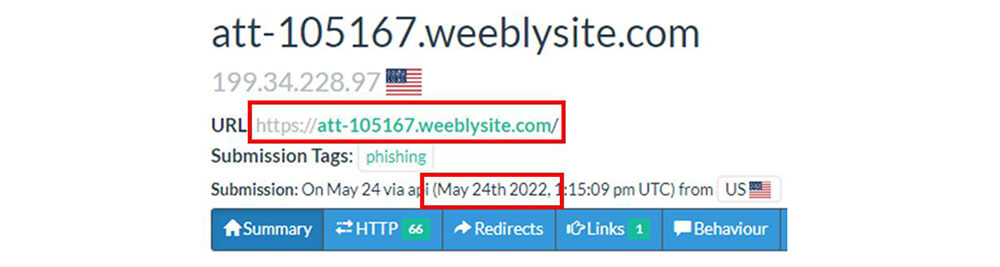
We noticed Weebly’s free service has been used to attack AT&T users for the last five months starting from the last week of May 2022. The highest activity in this regard was seen last month as part of one of the observed campaigns.
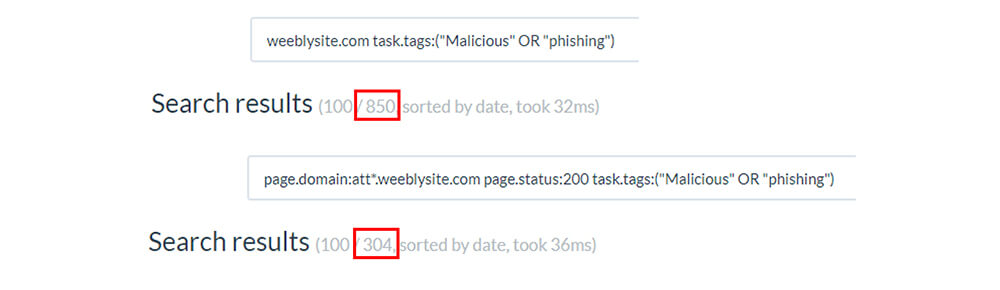
We observed a total of 850 suspicious (malicious or phishing) URLs associated with Weebly out of which 304 active (Response code 200) URLs are linked to AT&T and 200+ link to inactive sites.
Cyberattacks targeted at the telecom industry have a variety of objectives. While some attacks primarily pose a threat to the targeted businesses and their finances, others may also have repercussions for the clients or users of the targeted businesses. Cyberattacks that target telecom services pose a particularly serious risk because the unavailability of these fundamental services could affect business production and other crucial sectors, such as emergency services, energy supply, and the health sector, in addition to being inconvenient for individual users.
Hackers find self-service options and telecom customer accounts to be appealing targets. As with access to a customer’s webmail, self-service portal credentials can be sold to other hackers and used as a starting point for additional criminal activity. Hackers, for example, can order a new sim card using a compromised self-service system while posing as the customer, allowing them to hijack the customer’s mobile number and use it for other criminal activities. The volume of customer data stored in telecom companies turns them into the go-to targets for cyber-attacks.
To increase their chances of successfully tricking security solutions, threat actors are utilizing every free tool and service they can find, with compromised websites and phony login pages for well-known brands leading the way. In the observable campaign, free website builders Weebly and Google Sites are used as ammunition to target the telecom giant AT&T. The majority of websites hosted on free website builders are themed around pornography, phishing, dating, and marketplaces that are becoming alternatives to underground sites. According to a recent report on phishing statistics, four out of five phishing attacks make use of web services, tools, and hosting that is not immediately interpreted as malicious. This has significant ramifications for security software that checks the validity of email links by following them to determine whether they are malicious or not.
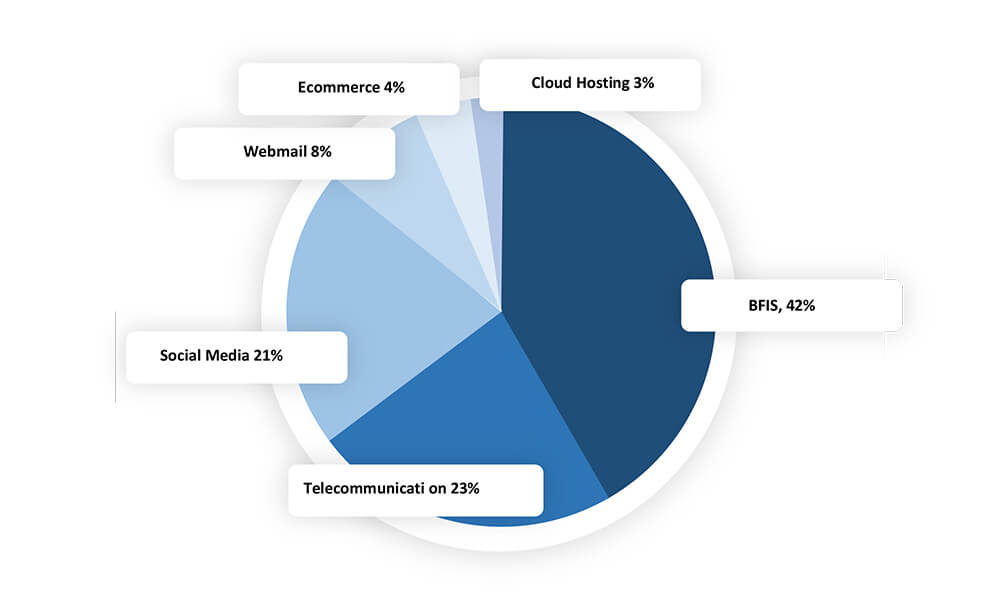
After banking and finance, telecommunications was the sector that phishing campaigns targeted the most. Herein, 23% of detected phishing attacks were caused by telecom incidents. According to the data that is currently available, 4 out of every 5 phishing sites were set up on infrastructure that did not require any financial investment on the part of threat actors, such as free services and tools or compromised websites.
The following are the possible impact of a phishing attack:
Exfiltration of data : Stolen credentials make it possible to sign into victims’ accounts directly, which enables the exfiltration of data from the victims’ inboxes and accounts, including emails, attachments, and data.
Access to people of interest : Threat actors use compromised accounts to pose as individuals of interest to facilitate communication to gather the necessary intelligence.
Persistent data collection : Threat actors can setup forwarding rules from victim inboxes to actor-controlled dead drop accounts, giving them long- term access to the data they have collected.
Data leak: To increase their credibility with victims, hackers post compromised information on their own or other websites. Such information may be related to employees, organizations, email addresses, customers, or suppliers leading to financial and reputational damage to the compromised organization.
Expanded cyber-attack: Stolen account-based information may be sold on dark web marketplaces, enabling more extensive cyberattacks on compromised accounts.