



Date: 29-June-22
Author: Manoj Kumar (CYFIRMA-Malware Research Team)
Suspected Malware: Matanbuchus
Function: malware Loader
Risk Score: 8
Confidence Level: High1`
Threat actor Associations: BelialDemon
DeCyfir presence: Yes
Matanbuchus, offered as part of malware-as-a-service, has been available on underground forums for a rental price of $2500 since February 2021. Recently, the CYFIRMA research team observed this malware reappear through spam campaigns. CYFIRMA team monitoring the campaign has attributed this malware to the BelialDemon threat actor. The email contains a malicious attachment in .html format having embedded base64 which on execution drops a zip file. Upon clicking the Html attachment, it drops a zip archive file and this zip file contains an MSI file. On executing the MSI file, it shows the fake Adobe error message to the user while dropping the malicious dll file in the background. This malicious dll file is loaded by regsvr32.exe along with the command-line argument. This dll file belongs to the Matanbuchus malware family, and it is trying to download additional payloads through C&C servers.
Sample Details:
File Type: Html
MD5: 5303835908B6D8313A9E226F7B025217
SHA1: EB10D1FBCC4D10899E532C6D8B4AFADDF08EBC9C
SHA256: E3B98DAC9C4C57A046C50CE530C79855C9FE4025A9902D0F45B0FB0394409730
This malware sample was written in a combination of Html and JavaScript language. Threat actors deliver this malicious Html file to the user through spear-phishing techniques such as the scanned document attached to the email.
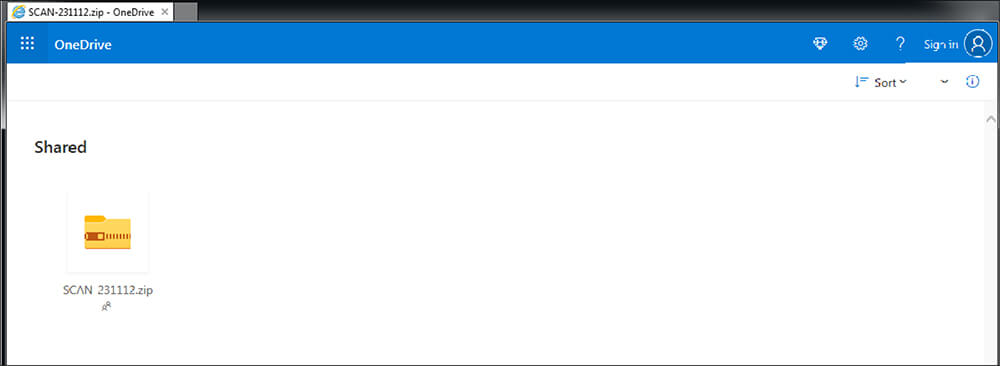
Threat actors are using the OneDrive string as a title in the HTML title tag and using a drive image in the Html file to pretend that this scanned document is in the OneDrive location to lure the user and convince them that this file is legitimate.
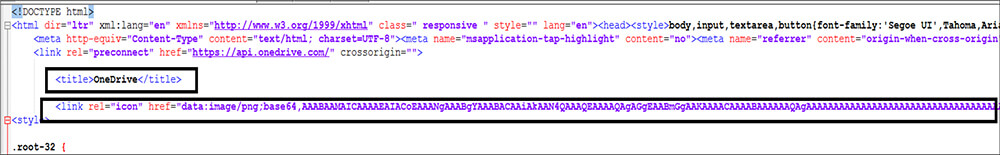
As shown in the below figure, the Threat actor embedded the malicious zip file in the JavaScript in base64 format, where the file name is Scan-23112.zip[MD5: A2D5F84B134F7A0F00C18770AB29876E].
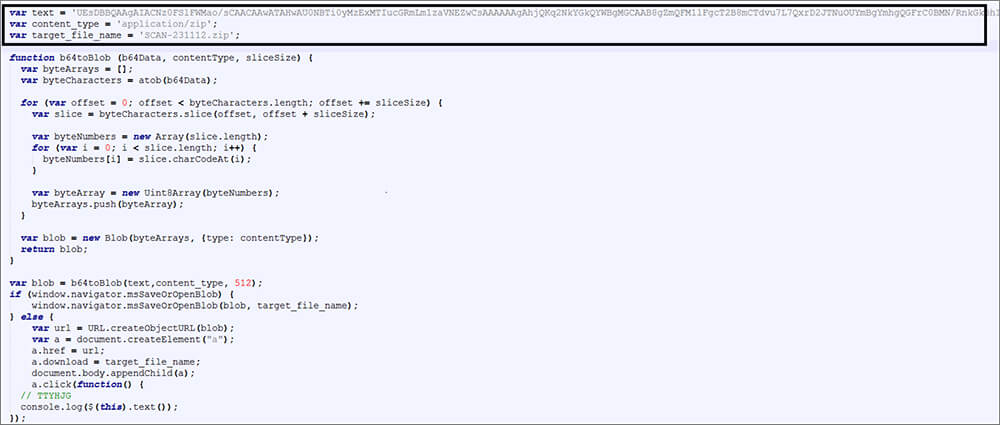
Once the user clicks that attached file, this Html drops the zip file in the Downloader folder and executed Matanbuchus malware from this location. After extraction, the dropped zip file is found to contain an MSI installer file.
MD5: 4D5DA2273E2D7CCE6AC37027AFD286AF
SHA256: 5DCBFFEF867B44BBB828CFB4A21C9FB1FA3404B4D8B6F4E8118C62ADDBF859DA
File Size: 229376 (bytes)
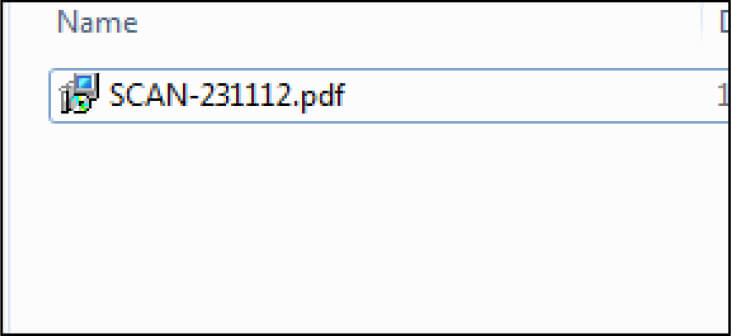
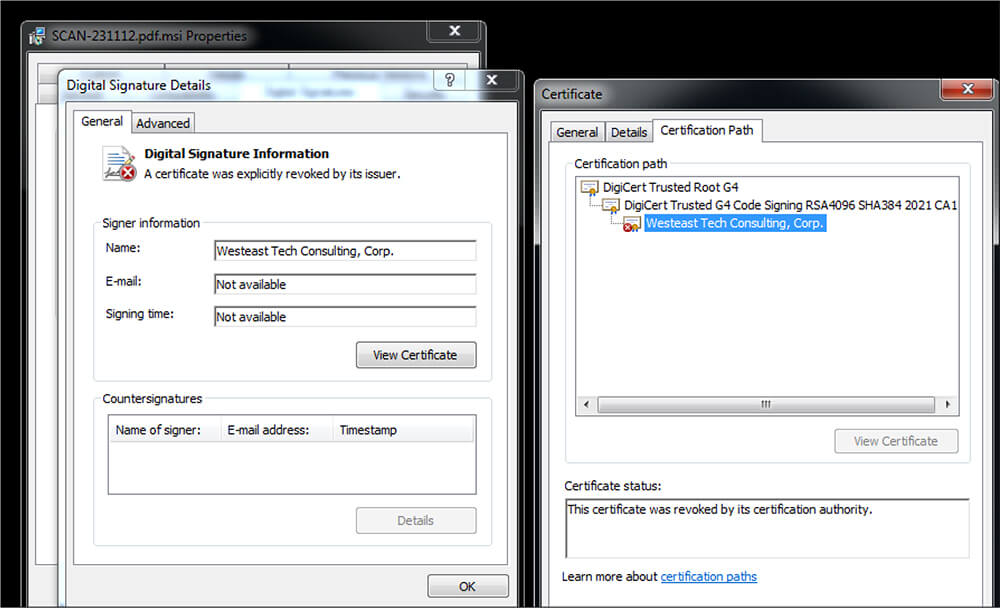
This MSI file is having a digital signature as “Westeast Tech Consulting, Corp.” This certificate was revoked by its certification authority.
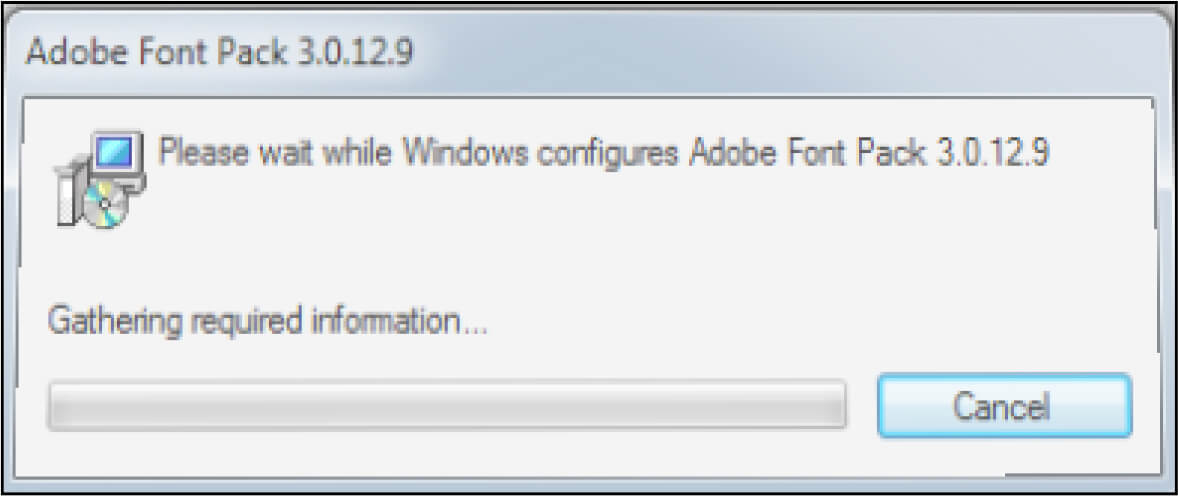
Upon execution of this MSI file, as shown in the below figure, the file pretends to configure Adobe Font pack version 3.0.12.9 in the user system and follows it up by throwing a fake error message to deceive users.
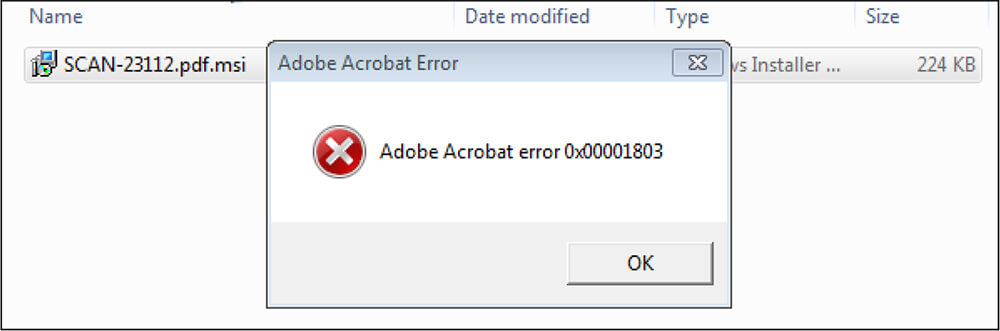
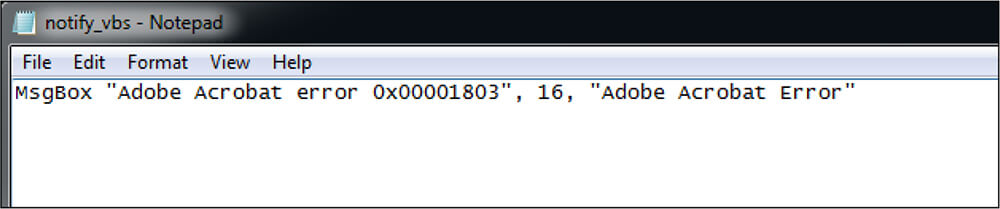
Fake error message
In the background, the MSI file creates the AdobeFontPack folder in the location “C:\Users\username\AppData\Local”, followed by dropping two files – dll[main.dll] file and vbs[notify. vbs] file.
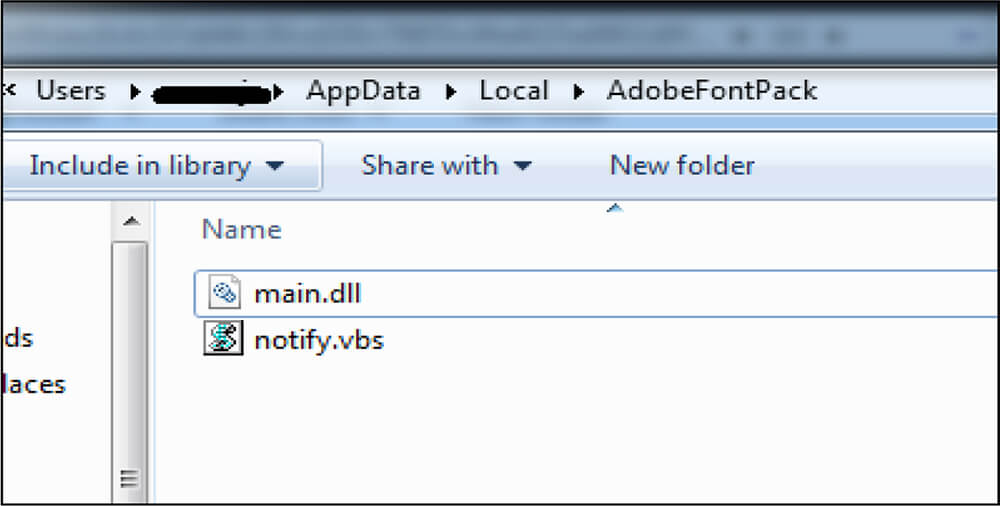
Notify.vbs file[MD5: 0308AA2C8DAB8A69DE41F5D16679BB9B] contains the fake error message that is displayed on execution of this MSI file.
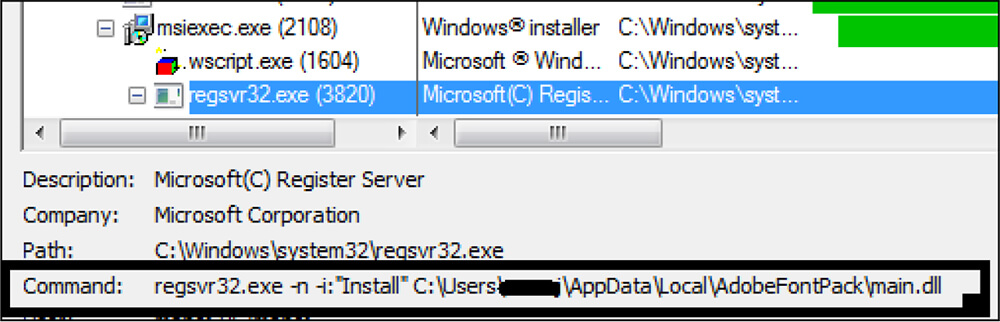
This MSI file loads this malicious dll file[ main.dll] through regsvr32.exe with arguments being -n -i “install”. regsvr32.exe is a command-line utility to register and unregister OLE controls, such as DLL files and ActiveX controls in the Windows Registry. This malware uses the -n parameter to prevent calling the DllRegisterServer method and uses the -i parameter which will invoke the DllInstall method.
This DLL file is establishing a connection to the C&C server for download and trying to download another malware which is Cobalt Strike beacon payload. At the moment these C&C servers are not alive.
Sample Details:
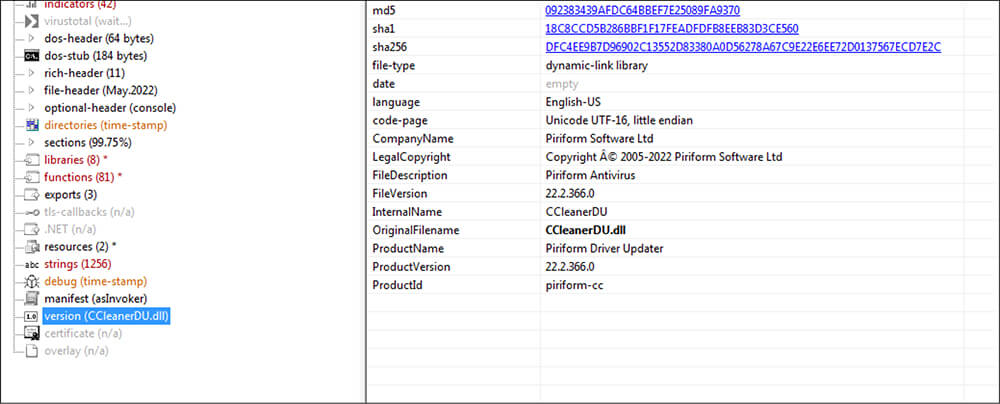
File Type: Windows PE [dynamic-link-library]
Architecture: 32 Bit
MD5: 1C5A0D343167085442299C29F3D88056
SHA1: 3815625D50B7C9290C4BF424E356C332E6DD295B
SHA256: 8833F28DC0CADD4B3C5676981B2A76E1C0683F2E2B8E3DAC8270622C12E032EF
Subsystem: console
Compilation Time: Thu May 12 03:42:49 2022
This malicious dll file is having version information and the company name in version information as “Piriform Software Ltd” as well as using the internal name as cclener.dll to lure unsuspecting users to believe that this file is legitimate.
This DLL file is having the following three export functions.
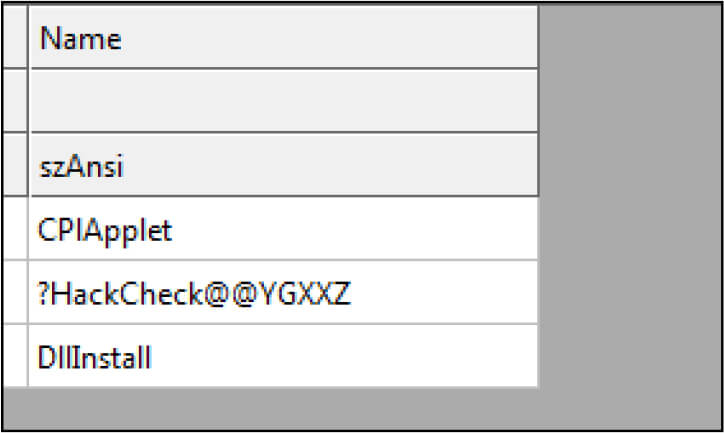
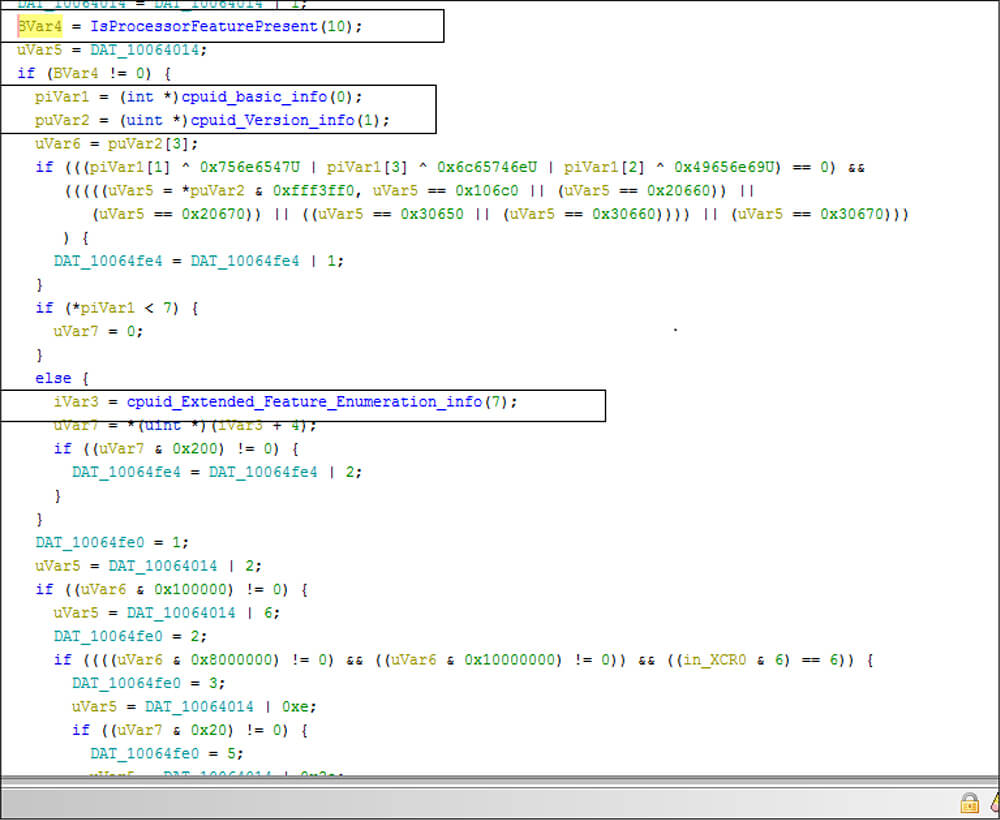
This dll having anti-debugging capabilty ,this dll file is checking presences for any debugger by calling APIs such as IsProcessorFeaturePresent(),IsDebuggerPresent(), QueryPerformanceCounter().
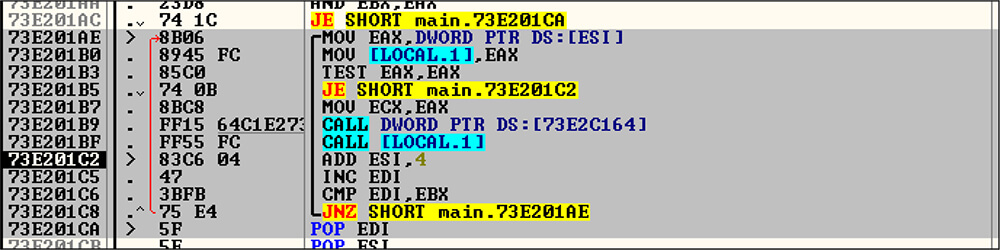
This DLL file contains malicious code in the DLL main function instead of the Exported API function. Threat actors use a customized decryption method to decrypt the malicious code. This malicious DLL file is calling the below do.. while to decode the malicious content. This loop will execute a total of 11 times. In each iteration of this loop, this code will run a different function [XORing the encrypted file].
In that iteration of 5 to 10 [Do..while loop] this DLL file is calling the decryption functions. This malicious DLL file is using a combination of two key pairs to generate one XOR key for decrypting the encrypted contents. In this combination of key pairs, one of the keys is a constant value which is “1010101” while another key is different for each decryption function execution (6 times).
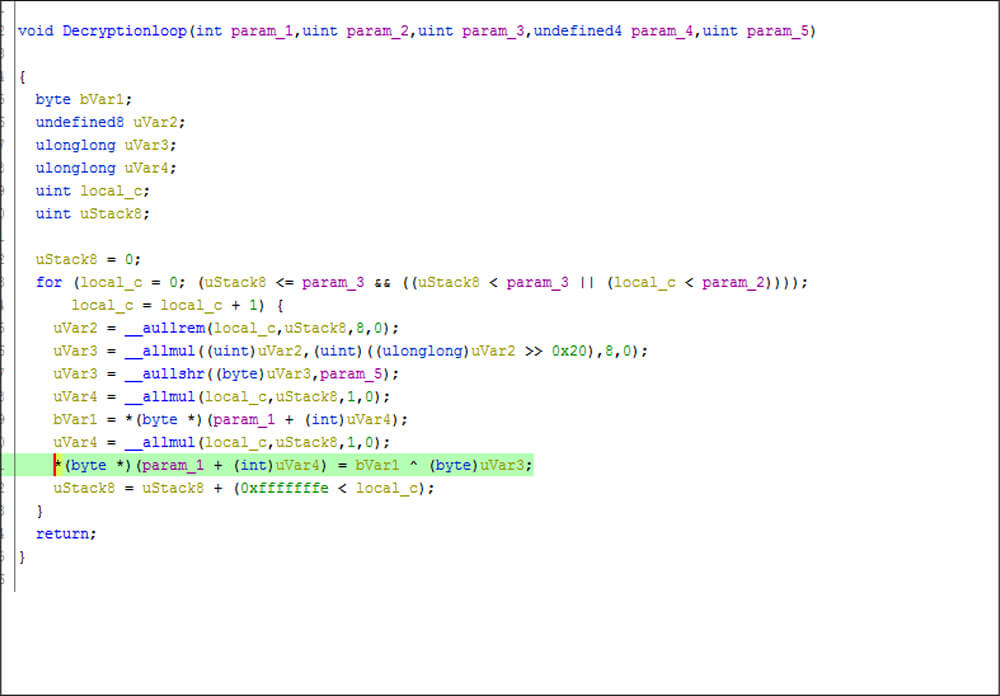
Decryption loops
These keys are listed in the following table:
| Iteration | Key Pair | Decrypted Content |
|---|---|---|
| 5th | 7EBC317 | DllRegisterServer |
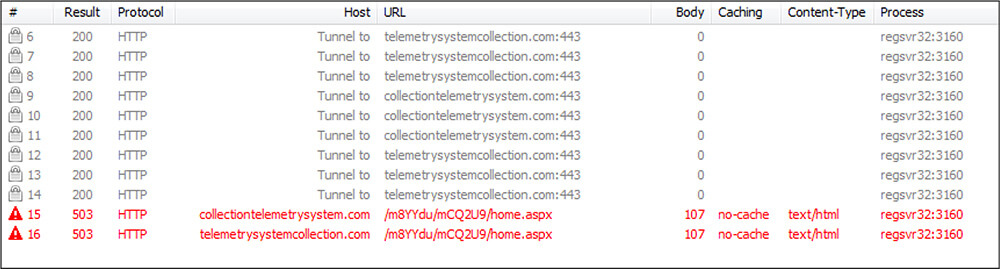
| 6th | 7EBBFA3 | hxxps://telemetrysystemcollection.com/m8YYdu/mCQ2U9/auth.aspx |
| 7th | 7EBB327 | hxxps://collectiontelemetrysystem.com/m8YYdu/mCQ2U9/auth.aspx |
| 8th | 7EBCBE5 | hxxps://telemetrysystemcollection.com/m8YYdu/mCQ2U9/home.aspx |
| 9th | 7EBB357 | hxxp://collectiontelemetrysystem.com/m8YYdu/mCQ2U9/home.aspx |
| 10th | 7EBCD07 | hxxp://telemetrysystemcollection.com/m8YYdu/mCQ2U9/home.aspx |
The below code snippet is one of the functions [Key pair] associated with them.
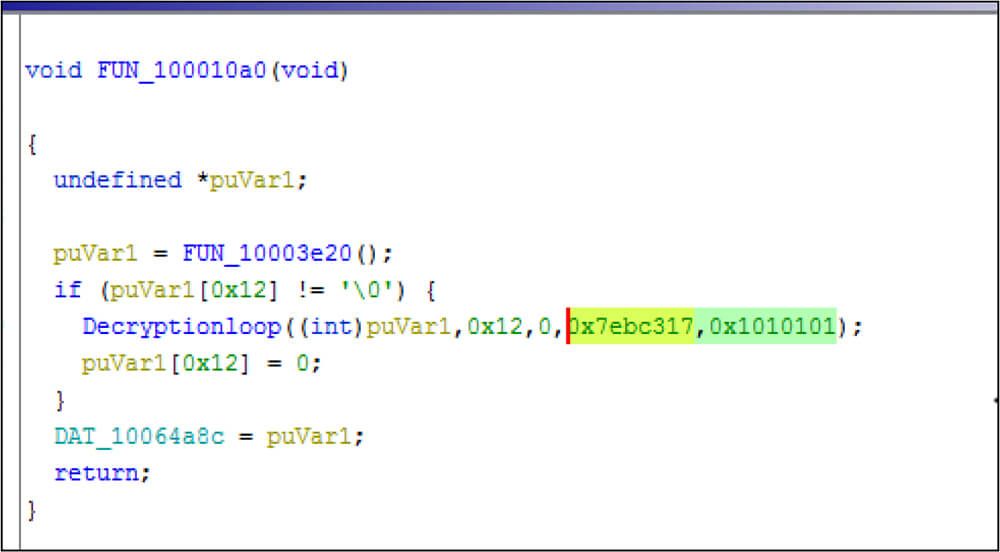
Key pairs of the 5th Iteration in do..while loop
The following code snippet is decoded malicious content in the memory after these do .. while loop execution is completed.
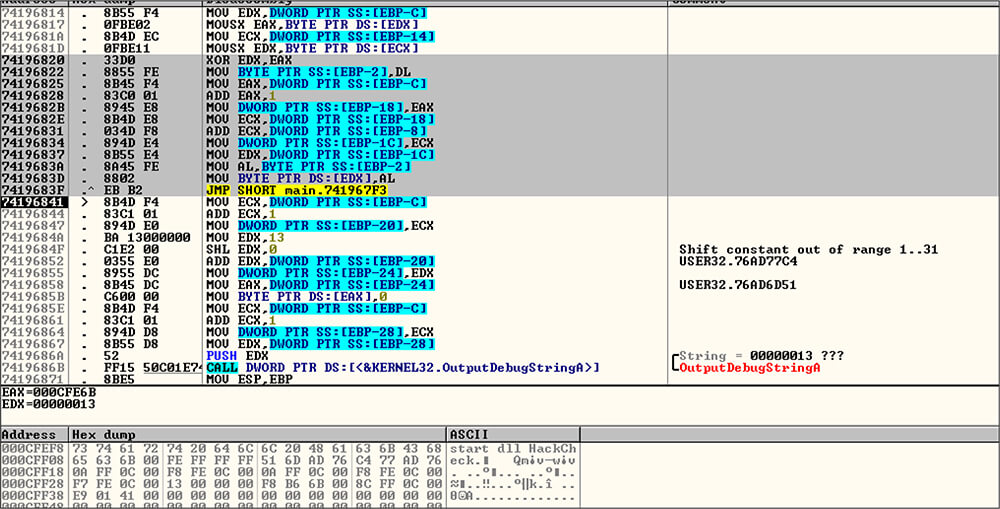
After that this malicious dll file executes an exported API function, namely ?HackCheck@@YGXXZ (a.k.a HackCheck), which has customized decryption logic. This function runs this decryption loop and decrypts the encrypted string “klyjl8|tt8Py{s[p}{s.”[which is hardcoded in the binary file] by XORing logic then print that output string by OutputDebugStringA API call. The decrypted string is “start dll HackCheck”.
Matanbuchus malware is distributed through phishing or spear-phishing emails having malicious attachments. The malware is attributed to threat actor BelialDemon, who is a member of several underground forums and marketplaces. This Matanbuchus malware loader has resurfaced and uses spear-phishing as an initial vector for infection having Html file as an attachment. The threat actor utilizes the HTML smuggling technique to deliver the malicious zip file to the user and disguises it as AdobeFontPack and installs the same into the system, while in the background, it is dropping Matanbuchus loader dll file in the location “C:\Users\username\AppData\Local\AdobeFontPack”. The threat actor loads the malicious main.dll file akin to an older trick known as Squiblydoo where Qbot was using regsvr32.exe along with arguments. Additionally, this malware loader tries to download the Cobalt Strike beacon payload.
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | 5303835908B6D8313A9E226F7B025217 | MD5 | SCAN-231112.html |
| 2 | A2D5F84B134F7A0F00C18770AB29876E | MD5 | Scan-23112.zip |
| 3 | 4D5DA2273E2D7CCE6AC37027AFD286AF | MD5 | SCAN-231112.pdf.msi |
| 4 | 1C5A0D343167085442299C29F3D88056 | MD5 | main.dll |
| 5 | hxxps://telemetrysystemcollection[.]com/m8YYdu/mCQ2U9/auth[.]aspx | URL | C&C server |
| 6 | hxxps://collectiontelemetrysystem[.]com/m8YYdu/mCQ2U9/auth[.]aspx | URL | C&C server |
| 7 | hxxps://telemetrysystemcollection[.]com/m8YYdu/mCQ2U9/home[.]aspx | URL | C&C server |
| 8 | hxxp://collectiontelemetrysystem[.]com/m8YYdu/mCQ2U9/home[.]aspx | URL | C&C server |
| 9 | hxxp://telemetrysystemcollection[.]com/m8YYdu/mCQ2U9/home[.]aspx | URL | C&C server |
| 10 | FuHZu4rQgn3eqLZ6FB48Deybj49xEUCtDTAmF | String | File string |
| 11 | klyjl8|tt8Py{s[p}{s | String | Obfuscated string of start dll HackCheck |
| 12 | start dll HackCheck | String | Decoded string |
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Initial Access (TA0001) | T1566. 001: Phishing:Spearphishing Attachment |
| 2 | Execution(TA0002) | T1059.007: Command and Scripting Interpreter:JavaScript T1204.002 : User Execution: Malicious File |
| 3 | Defense Evasion(TA0005) | T1218.007: System Binary Proxy Execution: Msiexec T1218.010: System Binary Proxy Execution: Regsvr32 T1497.001:Virtualization/Sandbox Evasion : System Checks T1497.003:Virtualization/Sandbox Evasion : Time Based Evasion |
| 4 | Command & Control (TA0011) | T1132.001: Standard Encoding Technique T1071.001: Application Layer Protocol: Web Protocols |