Published On : 2022-01-09
Supersuso is a ransomware intended to encrypt sensitive data in order to restrict access to it. During the encryption process, this malware sample adds the extension .ICQ_SUPERSUSO to mark inaccessible files. When the encryption process ends, Supersuso malware creates a ransom note #Decrypt#.txt
Malicious Sample Analysis:
MD5:CCFACEE2EBA9FCDB7FDDD4E9D7B846FF
SHA256: 8C142BFDA0D07A7E62C1D761CB9DF9B3F99F19479431DFC3F778408FE113F4C8
File Type: Windows PE-32 Executable
Subsystem: GUI
Compilation Time: Wed Sep 01 20:02:12 2021
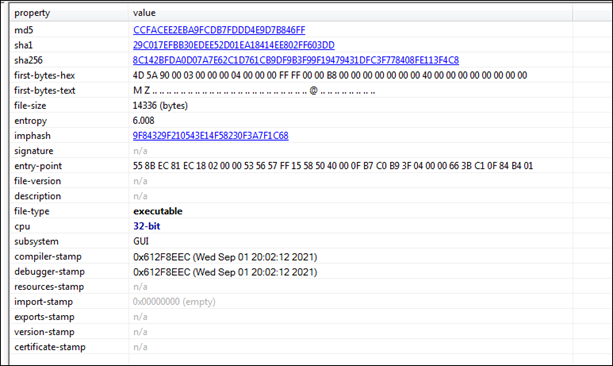 Fig 1
Fig 1
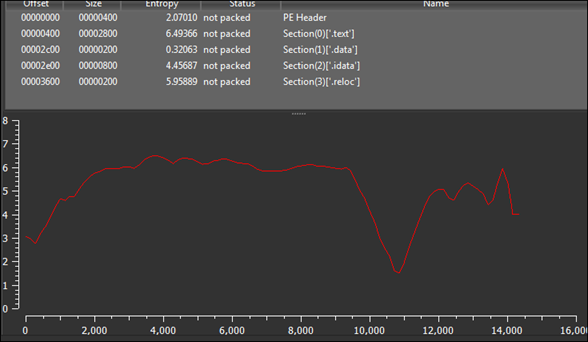 Fig 2
Fig 2
As shown in the above figure, this malware sample is a 32-bit Windows executable file, having a GUI subsystem and compile-time on 01 Sep 2021. Figure2 shows that this malware sample was not packed.
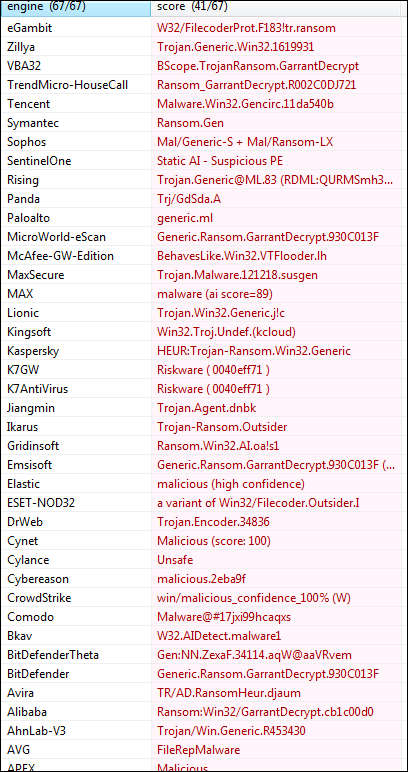 Fig 3
Fig 3
These are malicious sample files detected through various anti-virus engines and most of them are detected as a Ransomware.
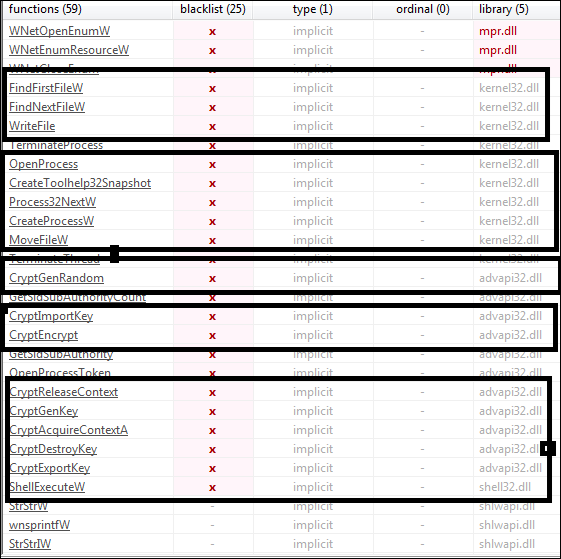
Fig 4
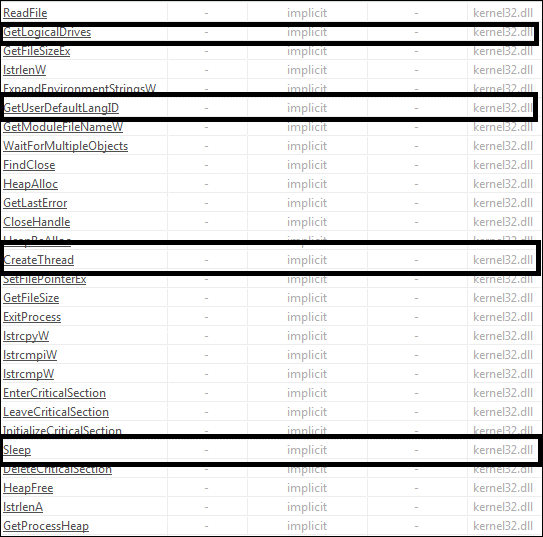
Fig 5
 Fig 6
Fig 6
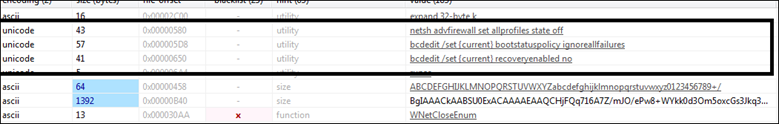
Fig 7
As shown in the above figures the APIs imported by the ICQ_SUPERSUSO Ransomware and indicate the following functionality/capability in the malware:
- Synchronization capability to handle multiple processes and threads and to access shared resources.
- Ability to handle windows/GUI functions.
- Ability to search Drives, Folders and exclude some specific files/folders from encrypting.
- Ability to create new threads and processes.
- Ability to access and manipulate access rights of the running processes.
- Enumeration of network resources and existing network connections.
- Capability to check the access rights of user.
- Ability to access folder paths.
- Dynamic memory allocation and manipulation capability.
- Capability to load other DLLs, libraries, and processes in memory.
- Capability to sleep or deactivate when want to hide itself.
- Ability to handle, search, open, close, write, access, perform operation and manipulating files.
- Ability to handle, search, access and manipulating processes in memory.
- Ability to encrypt files.
- Capability to handle command line arguments/strings of the process.
- Capability to create snapshots of other processes include their heaps, modules, and threads.
- Capability to delete all volume shadow copies on a system
- Capability to disable firewall
- Capability to terminate running process
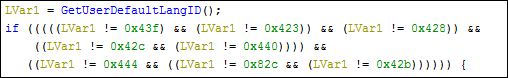
Fig 8
As shown in the above fig, Countries excluded from this ICQ_SUPERSUSO ransomware attack are mentioned:
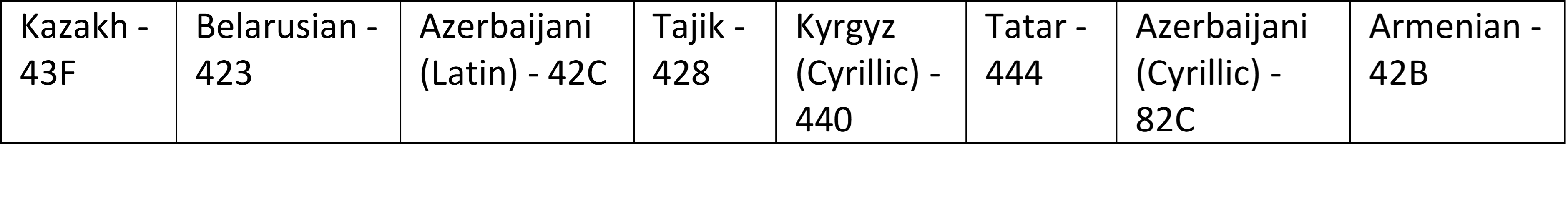
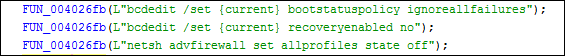
Fig 9
Disable firewall setting:
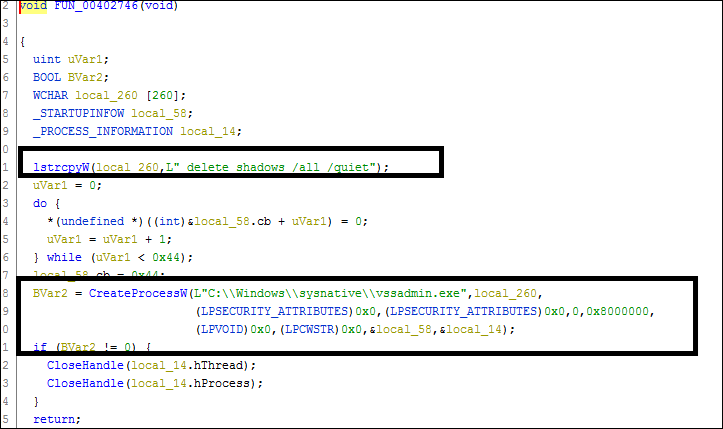
Fig 10
Delete all volume shadow copies on a system:
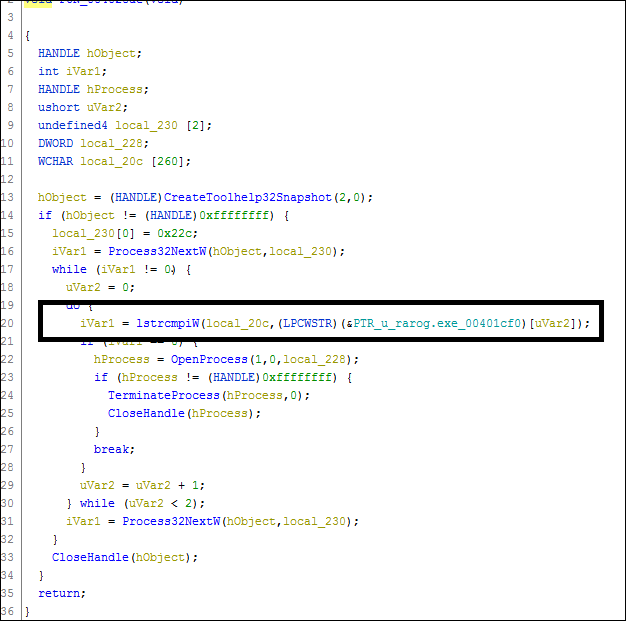 Fig 11
Fig 11
Rarog Cryptocurrency Mining Trojan. This Ransomware terminates the Rarog Process if found on the affected system.
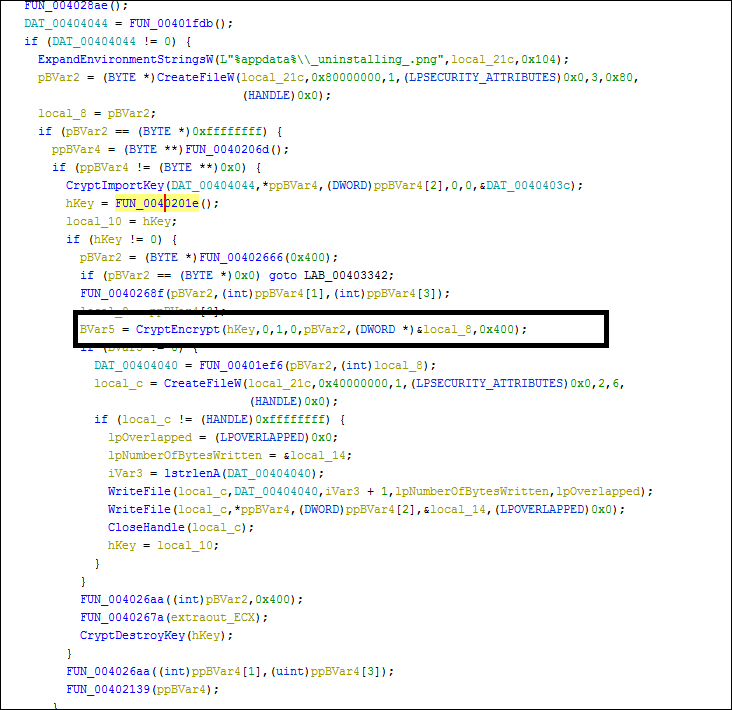
Fig 12
The file is encrypted by CryptEncrpt function:
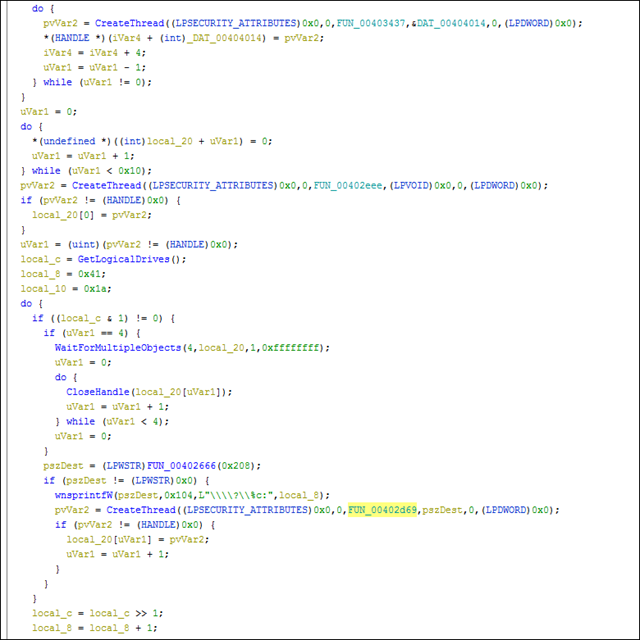
Fig 13
The Malware sample creates threat-starting and threat-calling addresses. See below code snippet and the encrypt executable file.
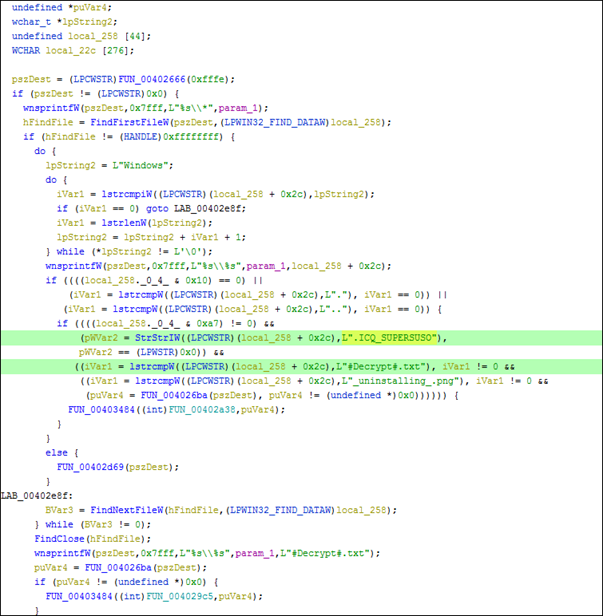
Fig 14
Once this malware sample is an encrypted file, this malware sample adds the extension .ICQ_SUPERSUSO and creates a ransom note # Decrypt#.txt
MITRE Attack Tactics and Techniques:
| No. |
Tactic |
Technique |
| 1 |
Initial Access (TA0001) |
T1566 Phishing |
| 2 |
Execution (TA0002) |
T1059 Command and Scripting Interpreter
|
| 5 |
Discovery (TA0007) |
T1083 File and Directory Discovery
T1057 Process Discovery |
| 6 |
Impact (TA0040) |
T1486 Data Encrypted
T1490 Inhibit System Recovery |
List of IOCs:
| No. |
Indicator |
Type |
Remarks |
| 1 |
CCFACEE2EBA9FCDB7FDDD4E9D7B846FF |
Hash |
MD5 |
Recommendations:
- Ensure you have a view on your external threat landscape and your security team is receiving threat intel that is relevant
- Implement a complex password policy with renewal at regular intervals.
- Implement a Multifactor Authentication policy.
- Regularly update all software on all systems and networks and other devices and turn on automatic updates if possible.
- Implement a Role-Based access policy and restrict it to minimal as per the requirement.
- Implement an Internal threat management policy that trains employees on the latest threats and ransomware attacks and what to do in such scenarios.
- Restrict to click or open suspicious/unauthorized links and files, specifically on organization devices.
- Must implement regular back-ups policy, more than one backup, and keep one on a separate network and other isolated offline at a different place.
- Use reputatable IDS/IPS, firewall, and antivirus/anti-spam/anti-ransomware and anti-malware solutions.
- Regular audits are necessary from a third party.
- Regular vulnerability assessment and patching policy.




 Fig 1
Fig 1 Fig 2
Fig 2 Fig 3
Fig 3

![]() Fig 6
Fig 6


![]()

 Fig 11
Fig 11

