



The following list contains recent campaigns observed by CYFIRMA Threat Intelligence (CTI) that are attributed to the Lazarus Group and or its affiliates in 2022.
High-level summary of recent campaigns observed by CYFIRMA attributed to the Lazarus Group in 2022.
Out of the 13 campaigns observed by CTI in 2022, the majority of campaigns were targeted at multiple counties across the globe, however, a couple of the campaigns observed by CTI appeared to target specific nations.
The below figure illustrates all the counties which were targeted in these campaigns.
Most Targeted Countries
The following figure illustrates the countries which were subject to the Lazarus Group campaigns.
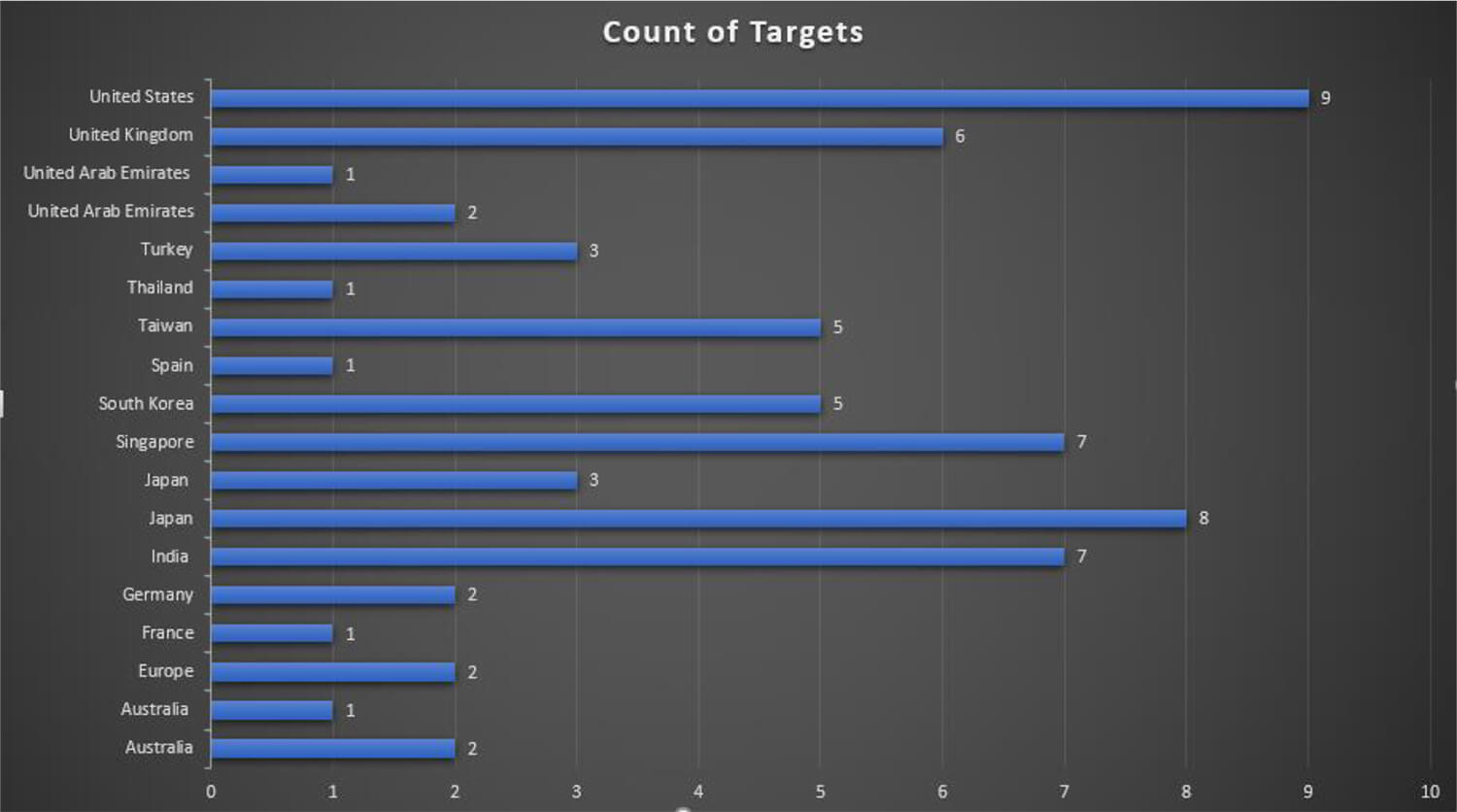
The United States and Japan have the most favorable targets for Lazarus Group and were targeted in 9 and 8 campaigns respectively. Countries like Singapore, India, and United Kingdom – while not at the top – remain to be of particular interest to the Lazarus Group and were also featured in multiple of their campaigns.
Lazarus Group is known to carry out attacks for financial gains and it can be assessed that the threat actor group similar to financially motivated cyber criminals may opt to attack multiple disparate targets for high returns. However, as the above figure illustrates some of the targeted countries, we observed in 2022 campaigns were part of only one campaign and more interestingly, some of the campaigns were only targeted at specific nation-states. For example, Japan was the only target for the campaigns MUD NATIONALS, UNC029, and UNC028.
Most Targeted Technology
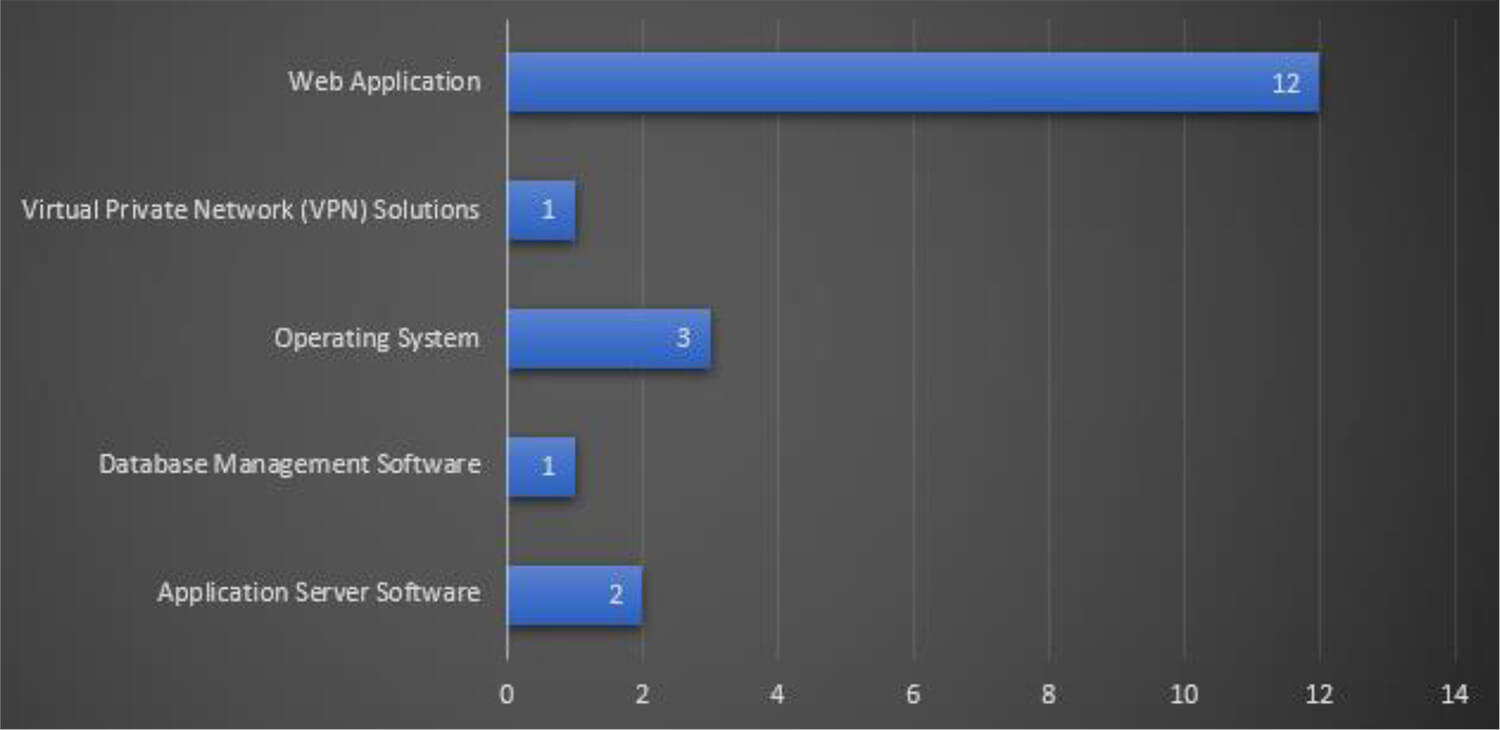
The Lazarus Group leveraged vulnerabilities and exploits in Application Server Software, Database Management Software, Operating systems, Virtual Private Network (VPN) Solutions, and Web Application to infiltrate the network and systems of potential victims.
The below figure illustrates the technologies that target the threat actor group during these campaigns. From the trends, it can be seen that exploiting weaknesses in web application- related software and products is the most favored method by the Lazarus Group. In addition, attempts to exploit remote access solutions such as VPNs have been observed which have been the focal point of cyber criminals these days.
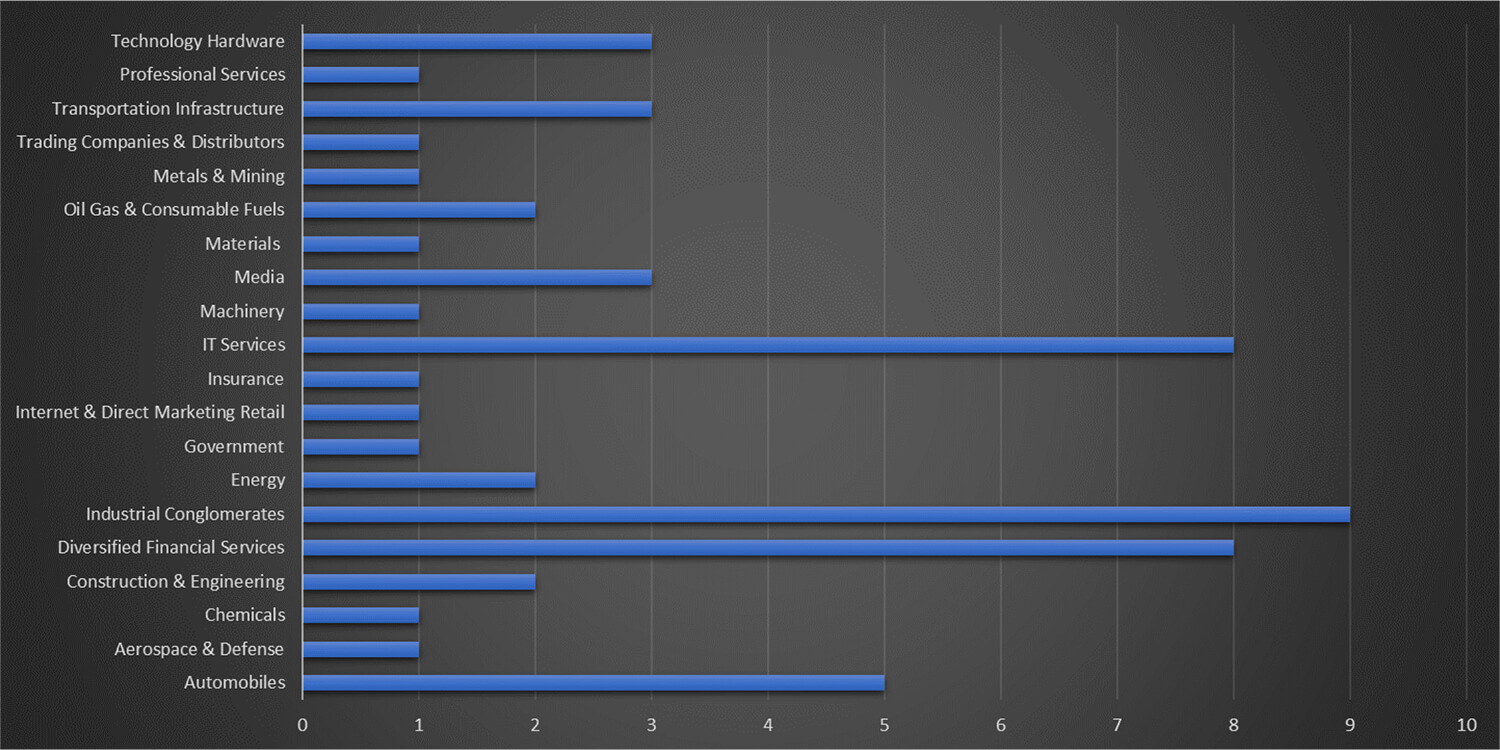
Most Targeted Industry
From the campaign observed by CTI in 2022, Lazarus Group attacked organizations from more than 20+ industry verticals. The majority of these attacks were focused on Industrial Conglomerate organizations, working in the financials, IT sector, and automobile sectors.
Malware/ Tools observed
Below is the list of all the malware used by the Lazarus Group during these campaigns. Only a few of the malware were leveraged by the threat actor in multiple campaigns and most of the malware was seen in only one campaign.
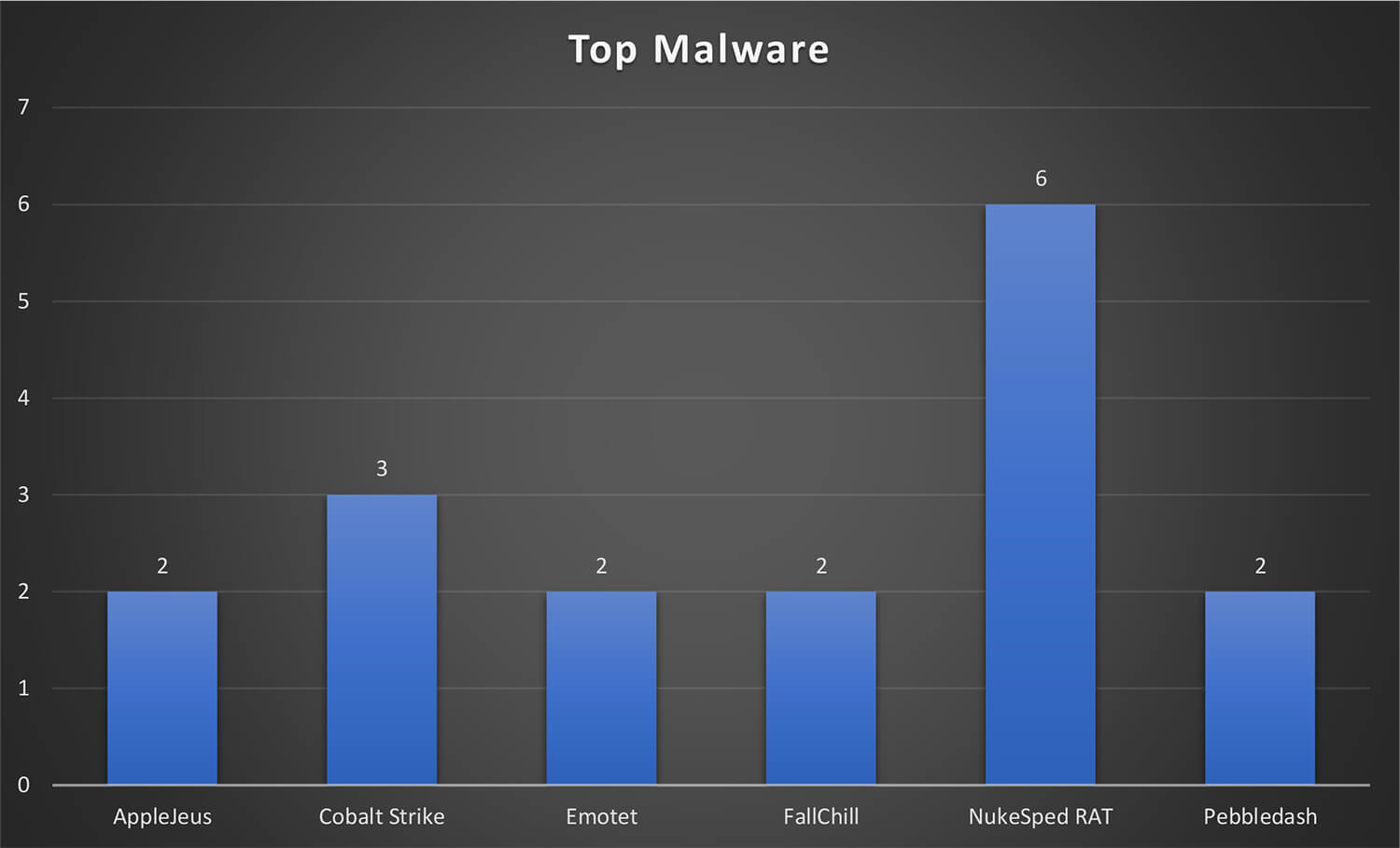
Top Malware
While numerous malware were used by the Lazarus Group in these campaigns, the NukeSped RAT was the most observed malware in multiple campaigns followed by Cobalt Strike. Other malware including AppleJeus, Emotet, FallChill, and Pebbledash were also leveraged in more than one campaign.
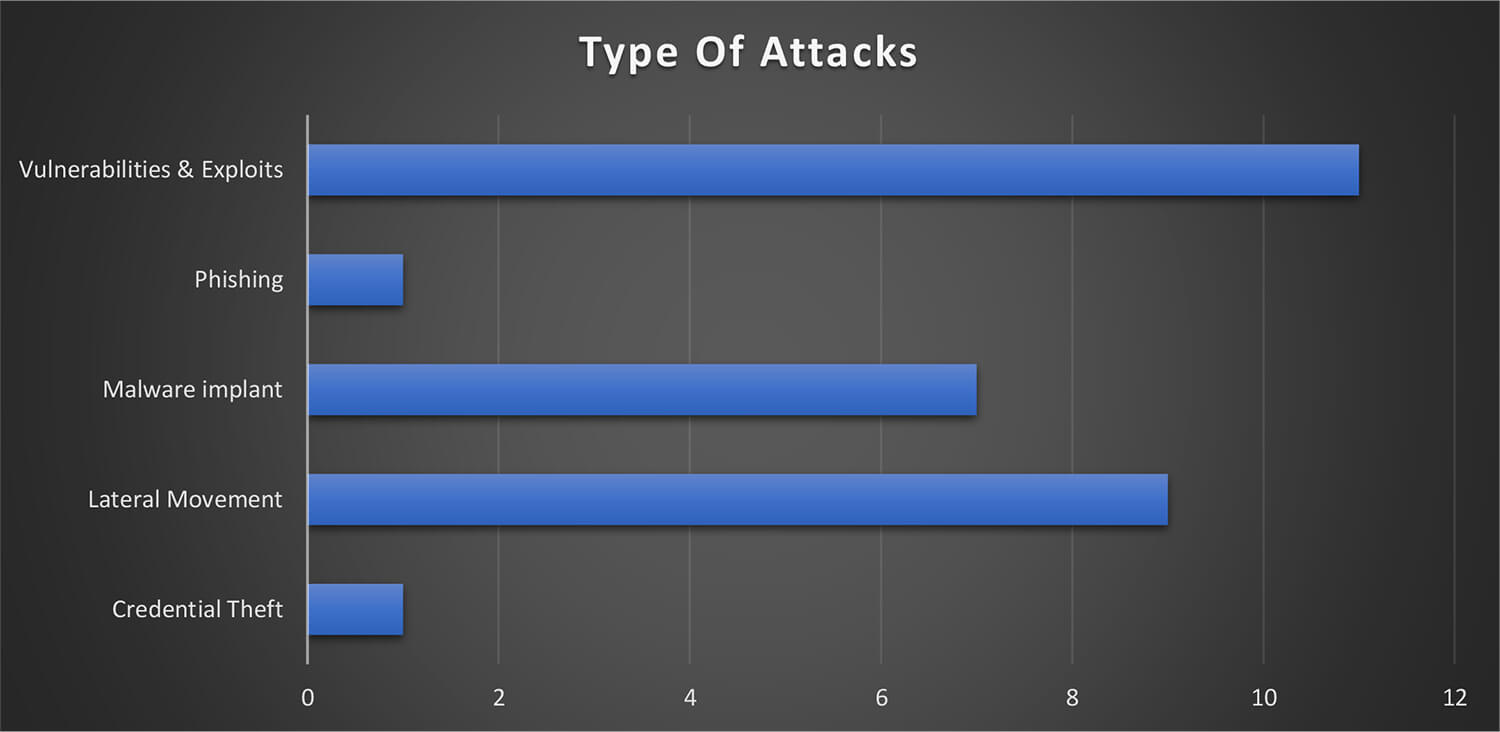
Type of Attacks
The majority of the observed campaign carried out by the Lazarus Group involved heavy use of exploiting vulnerabilities in internet exposed systems including weakness in email/ VPN appliances. The use of malware implants and lateral movement into the organization was a common tactic. The method of phishing and credential theft was only observed once out of 13 campaigns tracked by CTI.
Threat Actor Profile
Alias: APT 38, APT-38, APT38, Andariel, AppleJeus, Appleworm, Bluenoroff,B ureau 121, Covellite, Dark Seoul, Group 77, Group77, Guardians of Peace, Hastati Group, Hidden Cobra, Labyrinth Chollima, Lazarus, NICKEL ACADEMY, NewRomanic Cyber Army Team, Operation DarkSeoul, Operation GhostSecret, Operation Troy, Silent Chollima, Stardust Chollima, Unit 121, Whois Hacking Team, ZINC
Researchers describe the Lazarus Group to have 3 subgroups as listed below. While the Lazarus Group tend to concentrate on espionage-style attacks, other subgroups such as Bluenoroff are specialists in cyberattacks that largely have a financial element.
Origin: North Korea
Active: 2007 – Present
Description: Since at least 2009, Lazarus Group has been observed as a highly sophisticated cybercriminal group that is known to be affiliated with the North Korean government (as per the Council of Foreign Relations – CFR). They are known to the U.S. government as Hidden Cobra. The person involved in the Lazarus Group operations is known as a member of an organization affiliated with Lab 110, a component of DPRK military intelligence.
They are capable of rapidly developing, mutating, and evolving existing exploits/malware in their malware development unit. Recently, they are observed targeting cryptocurrency exchange companies.
Lazarus Group’s targets have primarily been South Korea (organizations of political relevance), Bangladesh Bank, Sony Pictures Entertainment, and some other Unites States- based organizations. Lazarus Group is believed to be divided into at least two subdivisions: the first, named Andariel, which focuses primarily on attacking the South Korean government and organizations, and the second, Bluenoroff, whose main focus is monetization and global espionage campaigns. Some of the long-standing campaigns attributed to them are Operation Flame, Operation 1Mission, Operation Troy, DarkSeoul, Ten Days of Rain, the Sony Pictures Entertainment attack, the SWIFT-related bank heists, and WannaCry.
Targeted Countries: Australia, Brazil, Brunei, Canada, Chile, China, Darussalam, Democratic People’s Republic of Korea, France, Germany, Guatemala, Hongkong, India, Indonesia, Islamic Republic of Iran, Japan, Myanmar, Philippines, Poland, Republic of Korea, Russia, Thailand, United Kingdom, United States, Vietnam, Bangladesh.
Targeted Industries: Aerospace & Defense, Capital Markets, Consumer Finance, Cryptocurrency, Defense, Diversified Financial Services, Energy, Entertainment, Government, Hotels, Investment Trusts (REITs), Media, NGO, Real Estate, Restaurants & Leisure, Technology, Telecommunications., Thrifts and Mortgage, Banks
Tools: The group has been known to utilize following tools in their attacks chain: NestEgg, Tdrop2, SHARPKNOT, RawDisk, Destover, CleanToad, ELECTRICFISH, Quickcafe, Http Dr0pper, NachoCheese, DeltaCharlie, PowerBrace, BTC Changer, HotelAlfa, Castov, Volgmer, DoublePulsar, Plink, BlindToad, PowerRatankba, PowerShell RAT, RomeoNovember, ValeforBeta, PEBBLEDASH, Koredos, RomeoEcho, RomeoWhiskey, ARTFULPIE, RomeoGolf, Yort, NukeSped, RomeoFoxtrot, Vyveva, Troy, Bookcode, Bitsran, CheeseTray, RedShawl, SierraCharlie, TFlower, Hawup, SheepRAT, FallChill RAT, Stunnel, RomeoCharlie, RomeoDelta, Rifdoor, Jokra, Romeos, SierraAlfa, SLICKSHOES, Aryan, ClientTraficForwarder, HOPLIGHT, WolfRAT, Tdrop, Andaratm, BanSwift, Recon, 3Rat Client, Duuzer, BUFFETLINE, EternalBlue, netsh, Mydoom, Concealment Troy, Dacls RAT, KillDisk, BADCALL, MATA, OpBlockBuster, CookieTime, Dtrack, Hermes, ATMDtrack, Mimikatz, COPPERHEDGE, DyePack, RomeoMike, Hotwax, RomeoBravo, Gh0st RAT, PowerTask, RomeoAlfa, Wormhole, Brambul, Fimlis, AuditCred, BISTROMATH, Joanap, HTTP Troy, KEYMARBLE, Rising Sun, Bankshot, PhanDoor, 3proxy, ProcDump, RatankbaPOS, VHD, HOTCROISSANT, PSLogger, RomeoHotel, PowerSpritz, HtDnDownLoader, WbBot, VSingle, BLINDINGCAN, TAINTEDSCRIBE, BootWreck, Contopee, Dozer
Malware: The group has been known to utilize following malware in their attacks chain:
AuditCred, Volgmer, WannaCry, BADCALL, APPLEJEUS, HARDRAIN, MATA, ThreatNeedle, Destover, Bankshot, RATANKBA, Proxysvc, Vyveva, Torisma Spyware, FALLCHILL, HOPLIGHT, DarkComet, KEYMARBLE, TYPEFRAME
Motive: CTI believes that Lazarus Group and associate groups’ activities are aligned to the political interests of North Korea and attacks are primarily motivated by financial or/and political gains.
Recent Activity:
The threat actor has been observed exploiting the Log4i remote code execution vulnerability to inject backdoors that fetch information-stealing payloads on VMware Horizon servers. Lazarus Group uses NukeSped to install an additional console-based information-stealer malware, which collects information stored on web browsers. In some attacks, Lazarus Group was observed deploying Jin Miner instead of NukeSped by leveraging Log4Shell.
MITRE ATT&CK TTPs
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | TA0042: Resource Development | T1583.001: Acquire Infrastructure: Domains T1583.006: Acquire Infrastructure: Web Services T1587.001: Develop Capabilities: Malware T1588.004: Obtain Capabilities: Digital Certificates |
| 2 | TA0001: Initial Access | T1189: Drive-by Compromise T1566.001: Phishing: Spearphishing Attachment |
| 3 | TA0002: Execution | T1059.003: Command and Scripting Interpreter: Windows Command Shell T1203: Exploitation for Client Execution T1204.002: User Execution: Malicious File T1047: Windows Management Instrumentation |
| 4 | TA0003: Persistence | T1098: Account Manipulation T1547.001: Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder T1547.009: Boot or Logon AutoStart Execution: Shortcut Modification T1543.003: Create or Modify System Process: Windows Service T1542.003: Pre-OS Boot: Bootkit |
| 5 | TA0004: Privilege Escalation | T1134.002: Access Token Manipulation: Create Process with Token T1547.001: Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder T1547.009: Boot or Logon AutoStart Execution: Shortcut Modification T1543.003: Create or Modify System Process: Windows Service T1055.001: Process Injection: Dynamic-link Library Injection |
| 6 | TA0005: Defence Evasion | T1134.002: Access Token Manipulation: Create Process with Token T1564.001: Hide Artifacts: Hidden Files and Directories T1562.001: Impair Defenses: Disable or Modify System Firewall T1562.004: Impair Defenses: Disable or Modify Tools T1070.004: Indicator Removal on Host: File Deletion T1070.006: Indicator Removal on Host: Timestomp T1036.005: Masquerading: Match Legitimate Name or Location T1027: Obfuscated Files or Information T1542.003: Pre-OS Boot: Bootkit T1055.001: Process Injection: Dynamic-link Library Injection T1218.001: Signed Binary Proxy Execution: Compiled HTML File |
| 7 | TA0006; Credential Access | T1110.003: Brute Force: Password Spraying T1056.001: Input Capture: Keylogging |
| 8 | TA0007: Discovery | T1010: Application Window Discovery T1083: File and Directory Discovery T1057: Process Discovery T1012: Query Registry T1082: System Information Discovery T1016: System Network Configuration Discovery T1124: System Time Discovery T1033: System Owner/User Discovery |
| 9 | TA0008: Lateral Movement | T1021.001: Remote Services: Remote Desktop Protocol T1021.002: Remote Services: SMB/Windows Admin Shares |
| 10 | TA0009: Collection | T1560: Archive Collected Data T1560.002: Archive Collected Data: Archive via Library T1560.003: Archive Collected Data: Archive via Custom Method T1005: Data from Local System T1074.001: Data Staged: Local Data Staging T1056.001: Input Capture: Keylogging |
| 11 | TA0011: Command and Control | T1071.001: Application Layer Protocol: Web Protocols T1132.001: Data Encoding: Standard Encoding T1001.003: Data Obfuscation: Protocol Impersonation T1573.001: Encrypted Channel: Symmetric Cryptography T1008: Fallback Channels T1105: Ingress Tool Transfer T1571: Non-Standard Port T1090.002: Proxy: External Proxy |
| 12 | TA0010: Exfiltration | T1048.003: Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol T1041: Exfiltration Over C2 Channel |
| 13 | TA0040: Impact | T1485: Data Destruction T1491.001: Defacement: Internal Defacement T1561.001: Disk Wipe: Disk Content Wipe T1561.002: Disk Wipe: Disk Structure Wipe T1496: Resource Hijacking T1489: Service Stop T1529: System Shutdown/Reboot |
The Lazarus Group has been known to be spearheaded by the North Korean government in alignment with their political and economic goals to target organizations and exfiltrate sensitive information to assist their local companies. It is widely established that the group’s primary motive is financial gains to overcome the effect of long-standing sanctions. The group is known to leverage new strategies and custom toolkits with their campaigns, as a result, the cyber operations may appear irrational. However, it is suspected the North Korean threat actors tend to operate on a wider scope as opposed to other nation-state threat actors and are likely to continue their operations similarly.
CTI suspects North-Korean threat actor groups will likely continue collaboration with Chinese and/ or Russian threat actor groups to meet their objectives. Doing so, they may offer their services/expertise as part of the Hacker-as-a-Service (HaaS) model to steal sensitive information in return for financial gains. Not only such cooperation will have a common target but will also provide some form of relief from the sanctions that have been enforced by the government of other nation states on these countries.