



Risk Score: 8
Confidence Level: High
Suspected Malware: Karma Leak Malware.
Function: Ransomware.
Tactic Used: Data Encryption.
Other Malwares related to Karma: GangBang, Milihpen, JSWorm
First Seen: June 2021
Target Industry: Multiple
Brief Introduction:
“Karma Leak” was first been detected in June 2021 and is a new ransomware. Another group with same name in 2016 has not any link to the current working threat group “Karma Leaks”. It has been observed that the Karma has somewhat linkage to Milihpen and Gangbang in accordance with similarity in coding part.
Karma Ransomware is constantly evolving, upgrading and improvement is a regular process. It encrypts all files except some extensions on the compromised system and appends the encrypted files with extension .KARMA_V2. Earlier it used the extension .KARMA. Karma ransomware also drops the ransomware note into each folder with name KARMA_V2-ENCRYPTED.txt.
Detailed “Karma Leaks” Ransomware Analysis:
File Details: As shown in Figure1, following are the details related to the malware “Karma Leaks”.
File Type: Windows PE-32 Executable
MD5: 21e7fb1c4d27ebdfc0d081e59cbeca8f
SHA256: 84d24a16949b5a89162411ab98ab2230128d8f01a3d3695874394733ac2a1dbd
Subsystem: GUI
Compilation Time: Sept 2021
Figure1
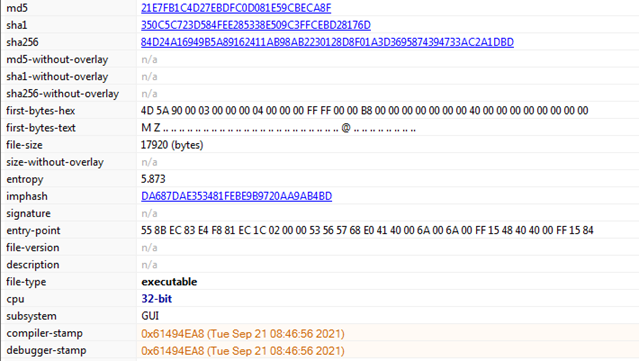
Figure2
As shown in Figure1 and Figure2 above, the file corresponding to ransomware “Karma Leaks” is Windows-PE 32 bit executable. It has GUI subsystem and compilation time is Sept 2021 which is quite recent.
The Figure3 below tells us that the file is not packed and Figure4 shows different hashes corresponding to the malware.
Figure3
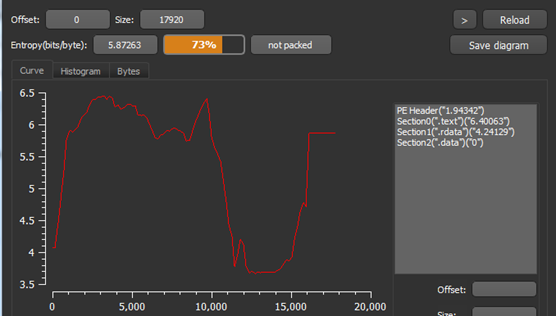
Figure4
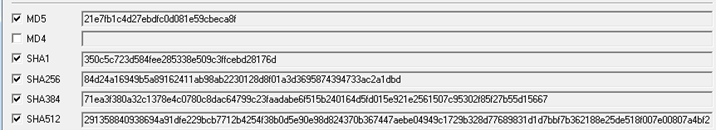
Figure5 shown below provides us information that the malware implemented Data Execution Prevention.
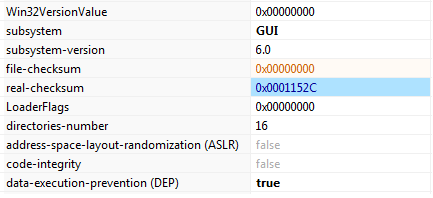
Figure6
We have checked the dark web for Karma Leaks onion website through TOR and it is currently unavailable as shown above in Figure6.
Figure7
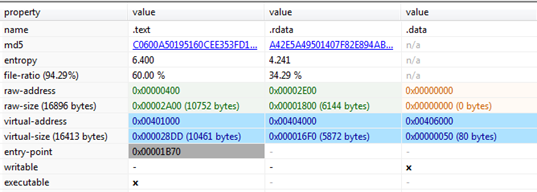
Figure7 above mentioned only three sections are part of the malware and look quite normal except the .data section which is a virtualized section only because it takes up no space on disk and only will be used during execution. Further, as we mentioned earlier, the malicious file subsystem is GUI, but it does not have any resource section which generally contains menus, icons corresponding to any GUI application.
Figure8
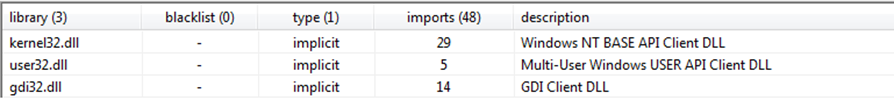
The malicious file imports libraries Kernel32.dll, user32.dll and gdi32.dll as mentioned above in Figure8. The kernel32.dll used for memory, hardware or low-level access and manipulation. The gdi32.dll is used for graphics handling and manipulation while user32.dll is used to handle user-interface components. The APIs/functions corresponding to these above-mentioned DLLs imported by the malware are shown below in Figure9.
Figure9
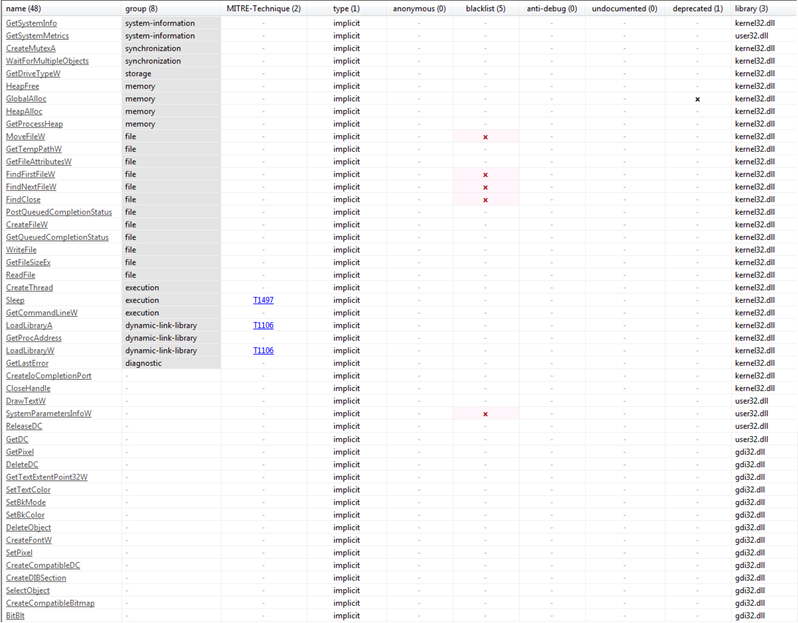
Above mentioned functions give us an indication that the “Karma Leaks” have the following capabilities or functionality:
Figure10
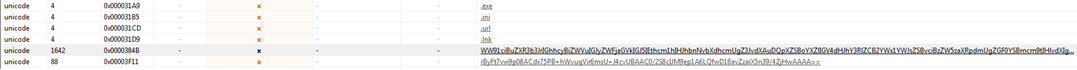
Figure10 above shows the extensions .exe, ini, .url, Ink which are not supposed to be encrypted by the ransomware. The file types mentioned in Figure11 given below are the files which are accessed and encrypted by the ransomware when we executed it over our analysis machine.
Figure11

Figure12
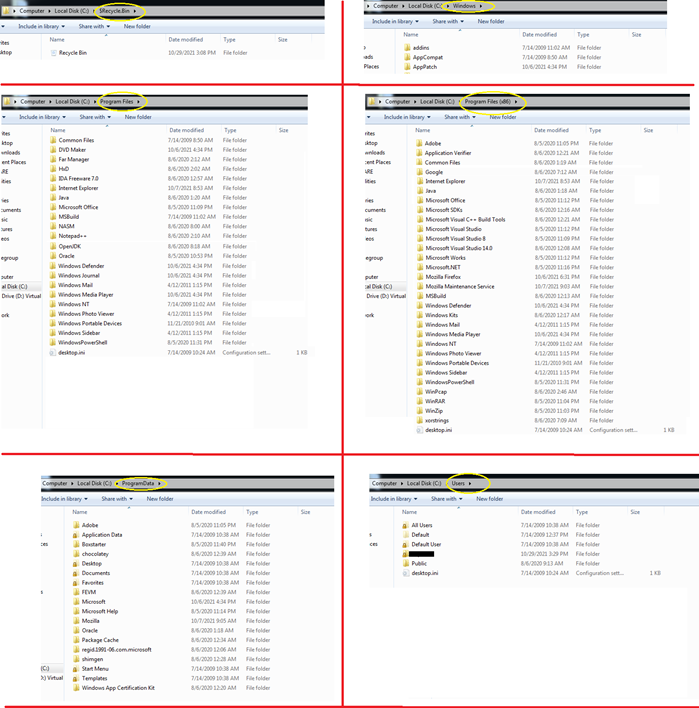
In addition to some specific files extensions, the KARMA ransomware also excludes some of the folders from the process of encryption. As shown in Figure12, it does not encrypt $RecycleBin, Windows, Users, Program Data, Program Files, Program Files (x86) folders.
Figure13
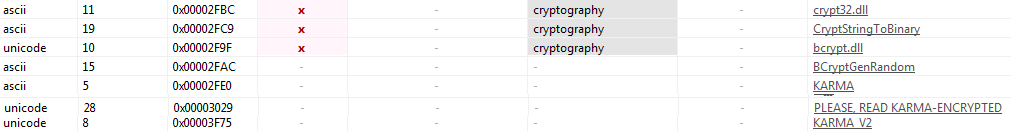
Figure13 above displays signs of cryptographic functions like CryptStringTOBinary and dlls like crypt32.dll used by the malware to encrypt the files present in the system. The KARMA and KARMA_V2 confirm the malware is KARMA Leaks ransomware. Figure14 given below also shows that the ransomware code is loading the library “crypt32.dll” by using LoadLibraryA API.
Figure14

Figure15 below shows that when the malware executes, it searches each drive and folder and drops a ransom note “KARMA_V2-ENCRYPTED.txt” which contains the contents mentioned in Figure16. The contents mentioned that the system is breached, and files are encrypted. In order to get the data back, the victim has to pay the ransom amount.
Figure15
Figure16
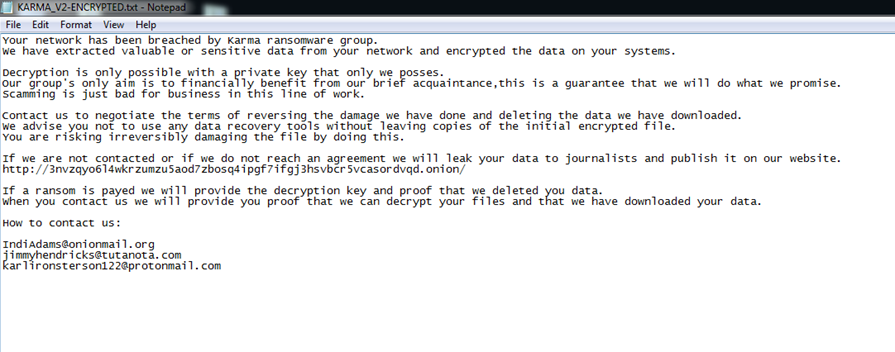
Figure16 above also mentioned the tor link where the data will be leaked if the victim is not able to pay the ransom. In addition to that three email-ids of onionmail, tutanota and protonmail are given in case the victim wants to contact the malware authors.
Figure17 shows all files in a folder get encrypted and the extension .KARMA_V2 is appended to them. The ransomware note KARMA_V2-ENCRYPTED.txt is also dropped in the folder. Further, the file with extension .exe is not encrypted as we mentioned earlier that the ransomware excludes some of the files having some specific extension like .exe. Figure16 shows the encrypted contents of a file.
Figure17
Figure18
Figure19
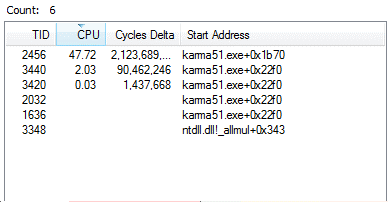
Figure18 shows the multiple threads running corresponding to the malware KARMA.
Figure 19 provides us with information about how the malware gets started. First, the thread is created and the .exe image of the malware is loaded into memory and after that, it loads the native API ntdll.dll. Further, it accesses the different registry entries and their values for managing sessions or getting information about the commands to be executed before loading any service.
Figure20 also shows us the number of 32-bit DLLs loaded by the malware like user32.dll, gdi32.dll, advapi32.dll. Advapi32.dll and sechost.dll are specifically important as they are used to access and manipulate registries and processes by the malware.
Figure20
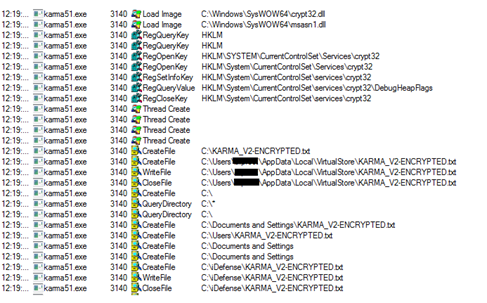
Figure21
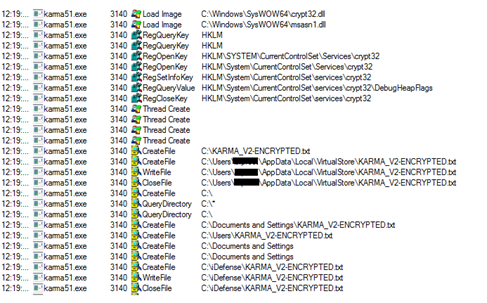
Figure21 shown above also indicates towards loading and usage of crypt32.dll by the malware for encryption purposes as mentioned earlier and also dropping ransom note KARMA_V2-ENCRYPTED.txt into different folders.
Figure22 below shows the list of all registries accessed or manipulated by the malware.
Figure22
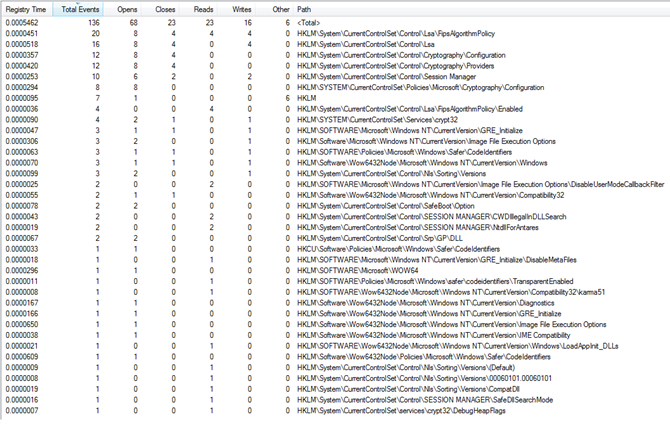
Figure23
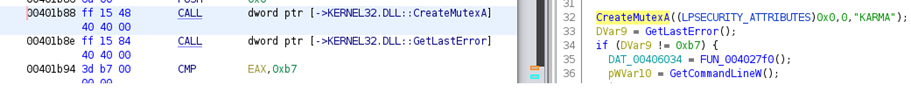
Figure23 above shows how the mutex is created by the malware as it is necessary that only one instance is running of the malware at a particular time.
List of IOCs:
| Sr No. | Indicator | Type | Remarks |
| 1 | 21e7fb1c4d27ebdfc0d081e59cbeca8f | File Hash | MD5 |
| 2 | 84d24a16949b5a89162411ab98ab2230128d8f01a3d3695874394733ac2a1dbd | File Hash | SHA256 |
| 3 | [email protected] | emailid | Malware author emailid |
| 4 | [email protected] | emailid | Malware author emailid |
| 5 | [email protected] | emailid | Malware author emailid |
Mitre Attack Tactics and Techniques:
| Sr No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | Phishing |
| Exploit Public-Facing Application | ||
| 2 | Execution (TA0002) | Malicious File |
| 3 | Persistence (TA0003) | Registry Keys |
| 4 | Defense Evasion (TA0005) | Registry Modification |
| Disable or modify tools | ||
| 5 | Discovery (TA0007) | File and Directory Discovery |
| 6 | Impact (TA0040) | Data Encrypted for Impact |
Recommendations: