Risk Score: 8
Confidence Level: High
Suspected Malware: FormBook Malware/Trojan
Function: Information Stealing, Credential Harvesting and download/drops stealthier malware
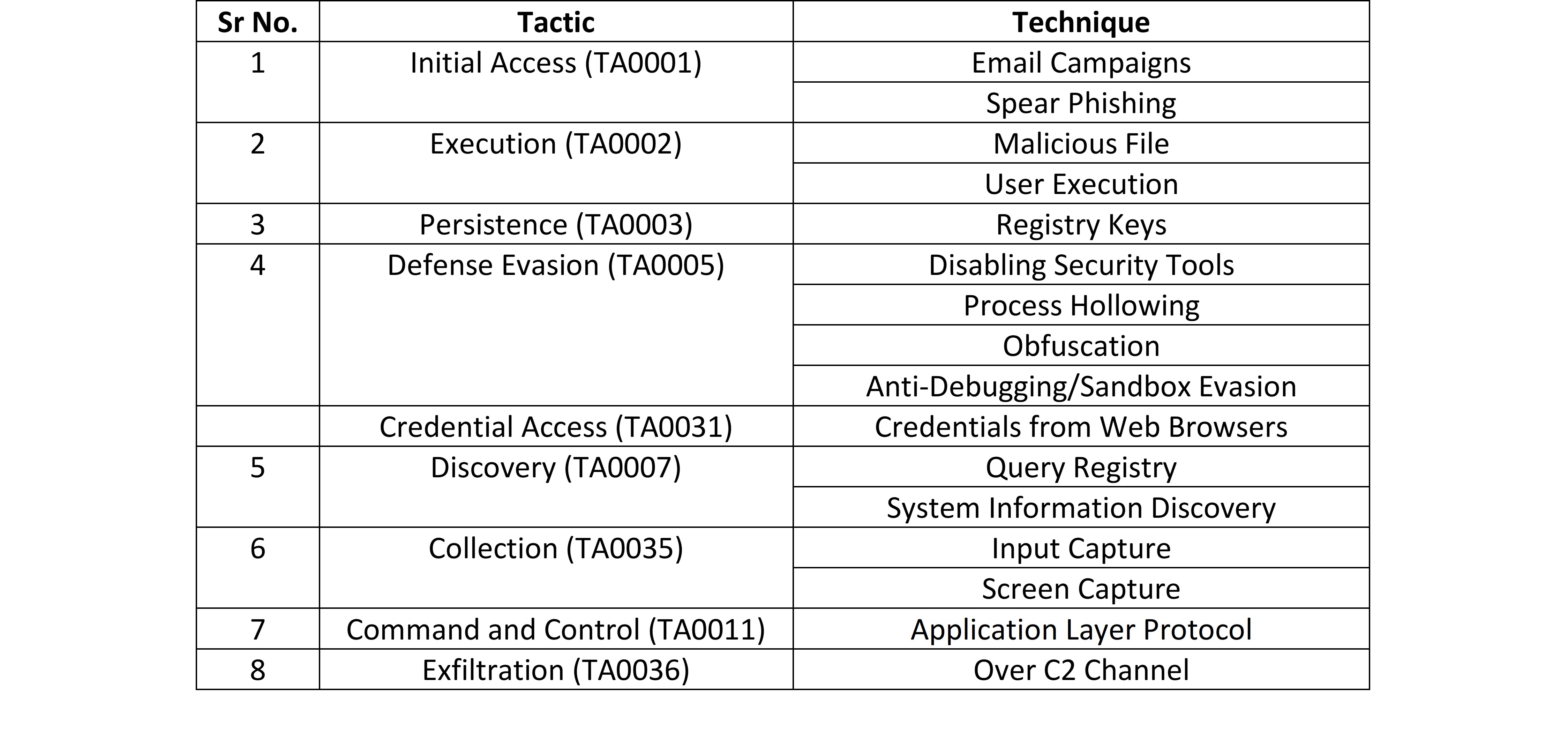
Tactic Used: Process Injection/Process Hollowing
Threat actor Associations: ng-Code
Other Malware related to FormBook: XLoader
First Seen: July 2016
Latest Seen: Nov 2021
Target Industry: Multiple
Target Countries: Multiple/Global Effect but predominately the US
Relevancy: Global Effect and used the latest zero-day vulnerability of Office-365 in 2021.
Brief Introduction: FormBook Malware is quite popular among attackers. It is basically an information stealer/trojan and is available in darkweb market as a Malware-as-Service. It is first seen in July 2016 and has been quite active since then. In 2020 it affected 4% of organizations worldwide and was among the top 3 list of trending malware. It logs and monitors keystrokes, searches and accesses files, takes screenshots, harvests credentials from different browsers, drops files, downloads, and executed stealthier malware as per commands received from Command-and-Control-Server (C2).
XLoader appears in 2020, consider as the successor of FormBook having similarities on the base of code and also advertise for sale in the same dark-web forums where FormBook was earlier sold. XLoader also has the capability to compromise macOS.
FormBook is mainly distributed using email campaigns, various infecting mechanisms and different types of file attachments including pdfs, doc, RTF document, exe, zip, rar etc. It takes advantage of various vulnerabilities like CVE-2012-0158 (Microsoft Windows Common Controls ActiveX Control Arbitrary Code Execution Vulnerability), CVE-2017-01182 (Microsoft Office Memory Corruption Vulnerability), CVE-2017-0199 (Microsoft Office/WordPad Remote Code Execution Vulnerability), and recently used an Office-365 zero-day vulnerability CVE-2021-40444 (Microsoft MSHTML Remote Code Execution Vulnerability).
File Details: As shown in Figure1, the following are the details related to the malware “FormBook”
File Type: Windows PE-32 Executable
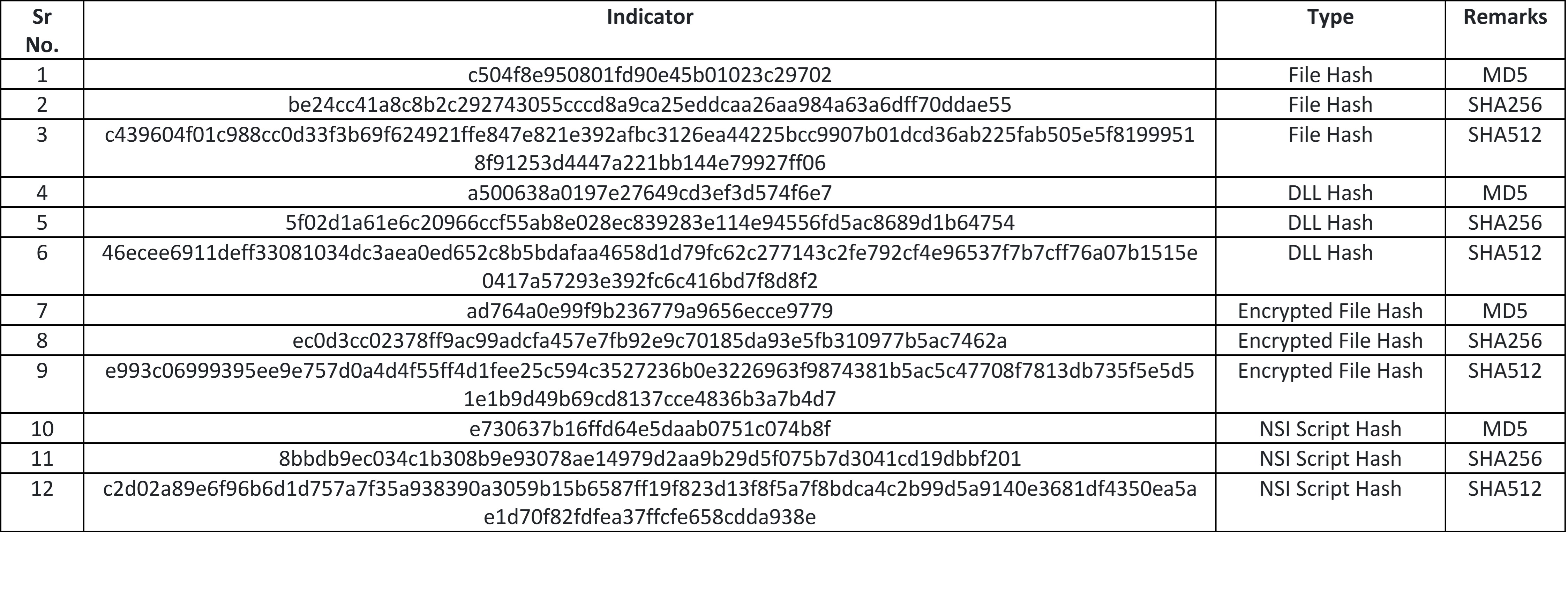
MD5: c504f8e950801fd90e45b01023c29702
SHA256: be24cc41a8c8b2c292743055cccd8a9ca25eddcaa26aa984a63a6dff70ddae55
Subsystem: GUI
Compilation Time: April 2016
Figure 1
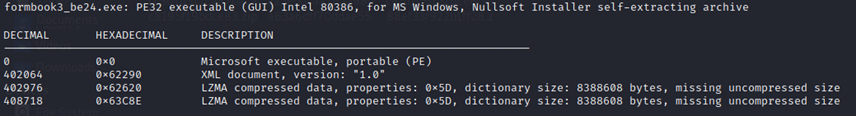
Figure1 above shows that FormBook Malware is a Windows PE-32 Executable and has the signature of Nullsoft Installer. The file has different parts, one PE executable along with an embedded XML document and two lzma compressed files.
Figure2 and Figure 3 show the different hash values corresponding to our malware file. Figure 2 also other basic information like it has GUI subsystem and compilation time of April 2016.
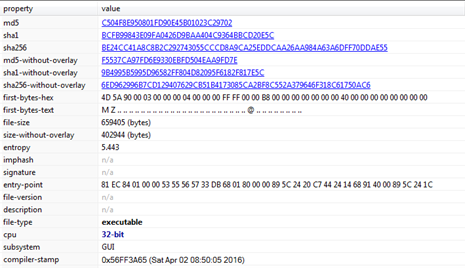
Figure2
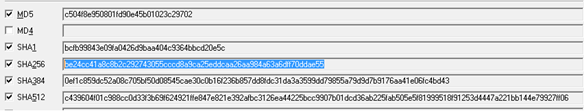
Figure3
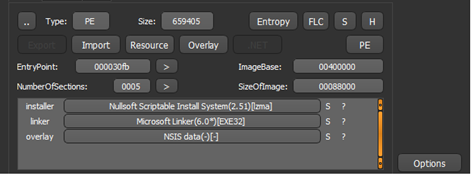
Figure4
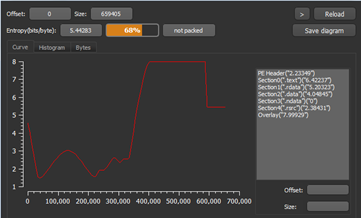
Figure5
Figure4 above shows that the malware has an NSIS installer, and it is present in the overlay part. We further examine and extract it. Figure5 shows the entropy curve corresponding to the malware. It mentioned it as not packed but the curve at the end is somewhat flat with high entropy provides us an indication of the presence of some packed code inside the executable file.
Figure6
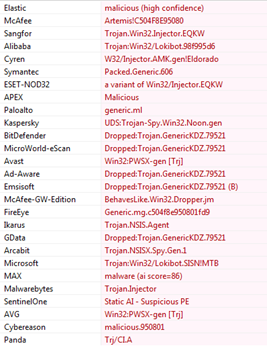
When we check, the malicious file in different anti-virus engines then it is detected as primarily a trojan/spyware/information stealer which is the main function of the FormBook malware.
Figure7
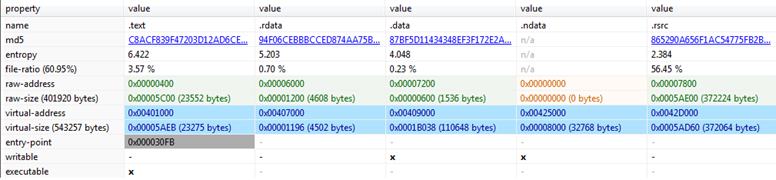
Figure7 above shows us different sections present in the FormBook. All are quite normal except .ndata which is totally a virtualized section means only available in memory.
Figure8
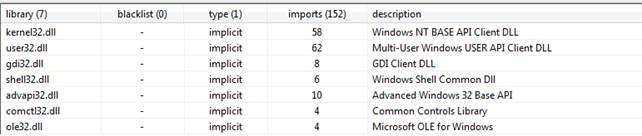
Figure8 above shows different libraries imported by the FormBook. All are important and provide us an indication of the functionality the malware incorporates. It includes memory, low-level functioning, user interface, graphical manipulation, registry access and manipulation capabilities. Shell32.dll and Ole32.dll are quite important here as ole32.dll is used for handling ole objects and is required for embedding ole objects of different applications to another application like excel-sheet embedded into a word document whereas shell32.dll is used to open webpages and files.
Figure9
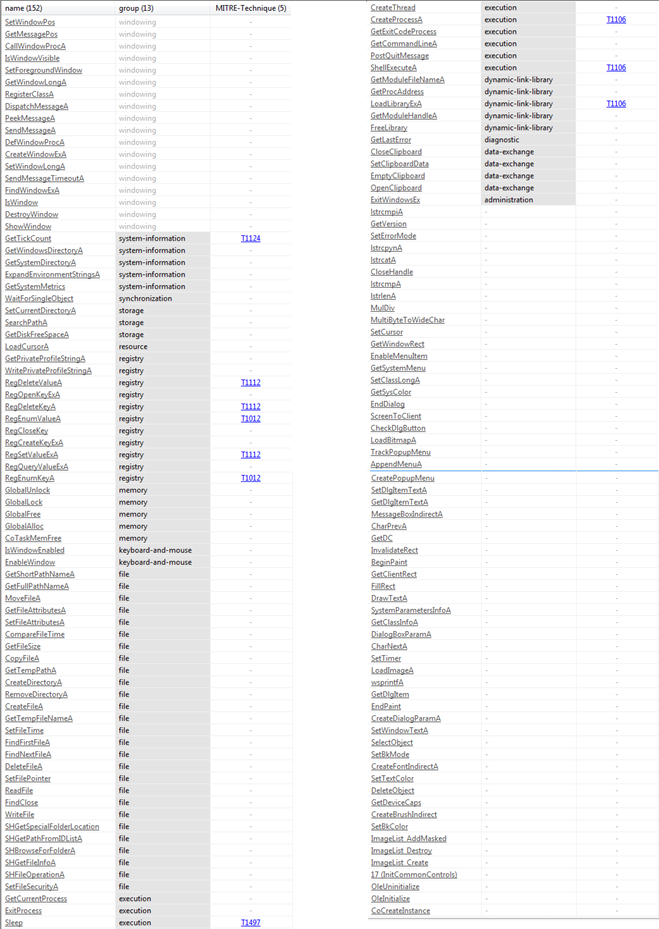
Figure9 above shows the various APIs/Functions corresponding to the above-mentioned libraries in Figure8 and provides us important information that the FormBook malware has the following capabilities:
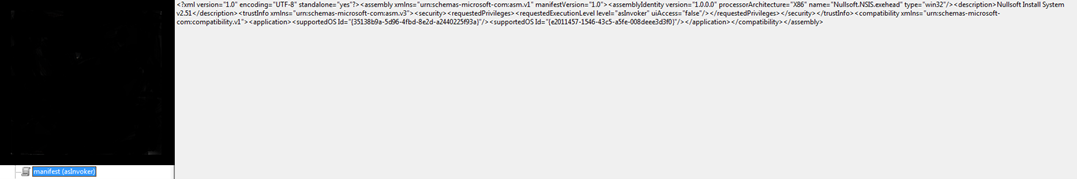
Figure10
Figure10 above shows the XML code present as manifest in the file. It contains meta-data corresponding to different files that are part of the same group or package. The privileges are used as “asInvoker” which means adopting any privilege assigned to the user. This further demonstrates the dependency on NullSoft NSIS and its version number. NSIS is a free framework used to bundle many elements of an application together including DLL or executable, and an NSIS script is also bundled along with the application/file/malware to control how all can be extracted and executed.
Figure 11 below also shows the overlay part present in the file. It also has the Nullsoft signature. FormBook most likely used it to bypass anti-viruses and load or extract the code/files present in the overlay section which are packed by using Nullsoft installer.
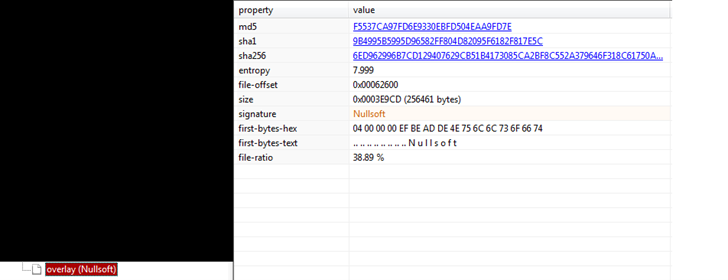
Figure11
We further extracted the hidden files present in our malicious executable as shown in Figure12 which are dropped by the file when it gets executed and used accordingly. There are three more files present in our malicious executable, one is the DLL “jnjvrzet.dll” which is present in the folder named $PLUGINSDIR and the second is the .nsi file which is the NSIS script to control that how to extract and use these files as mentioned above. The third file is “6ce1nlzjaolgh5df” which is in lzma compressed and encrypted also and most probably is an executable or DLL and the main payload.
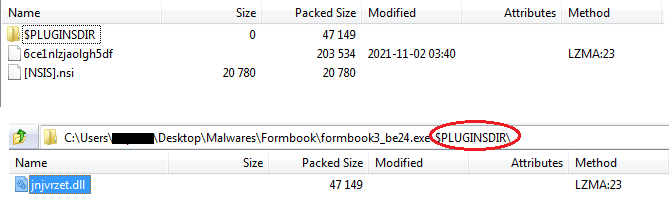
Figure12
Figure13 and Figure14 show hexdump corresponding to the file DLL “jnjvrzet.dll” and “6ce1nlzjaolgh5df”.
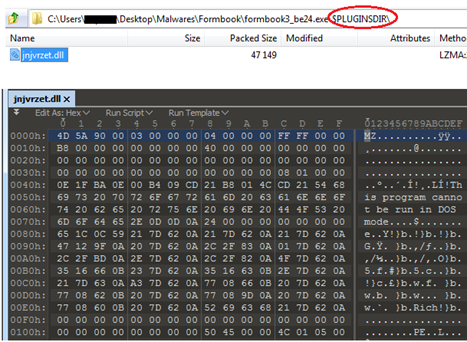
Figure13
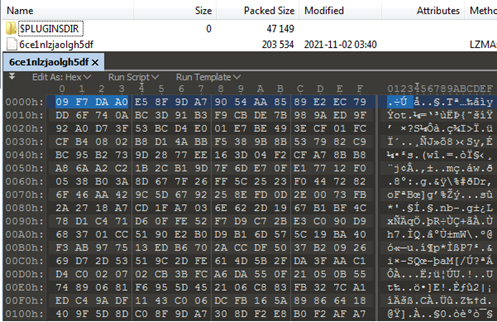
Figure14
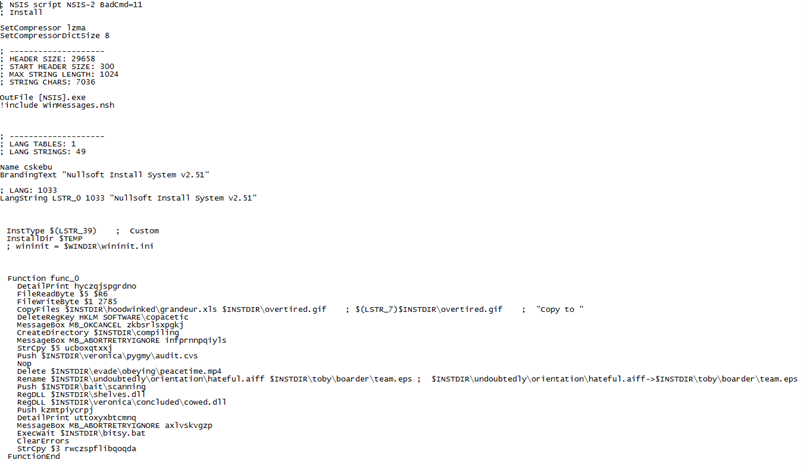
Figure15
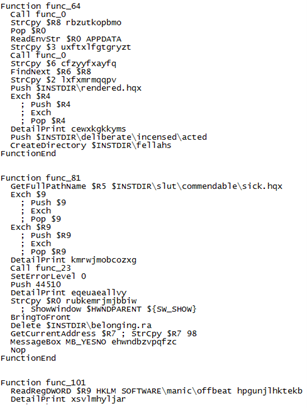
Figure16
Figure15 and Figure16 show the snippets of .nsi script corresponding to Nullsoft Installer to control the process of extracting these embedded files and how to use them for further exploitation. It accesses various folders, creating files, copying, and doing initialization, etc.
We further checked the extracted .DLL file “jnjvrzet.dll” as shown below in Figure17. It is Windows 32-bit DLL. We checked it through different anti-virus engines and found it to be malicious and they categorized it as mainly trojan as shown in Figure 18.
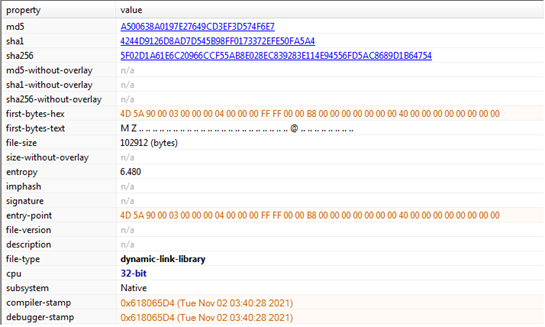
Figure17
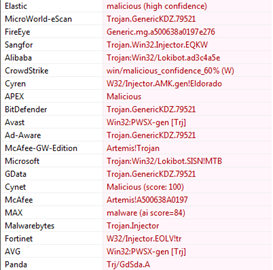
Figure18
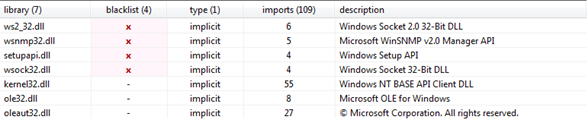
Figure19
The imported libraries corresponding to the extracted DLL are shown in Figure19 above. The presence of ws2_32.dll and wsnmp32.dll indicates that our extracted DLL is responsible for handling and managing network connections. Setupapi.dll is also quite important as it is used for setting up and installing the applications means the extracted DLL also helps in installing or setting up other malicious files for execution and most probably the main payload.
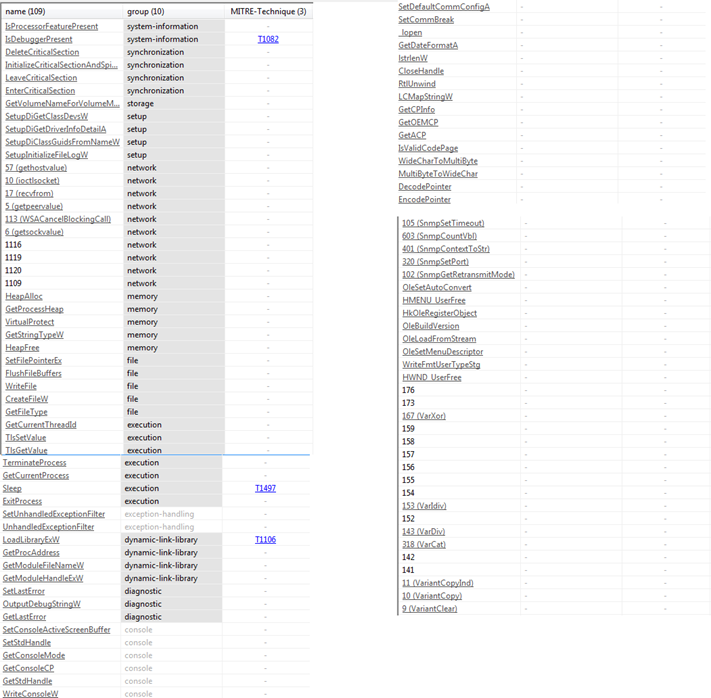
Figure20
Figure20 above shows the imported APIs/Functions by our extracted DLL. The DLL also has the following capabilities in-addition to the capabilities we mention for our malicious executable:
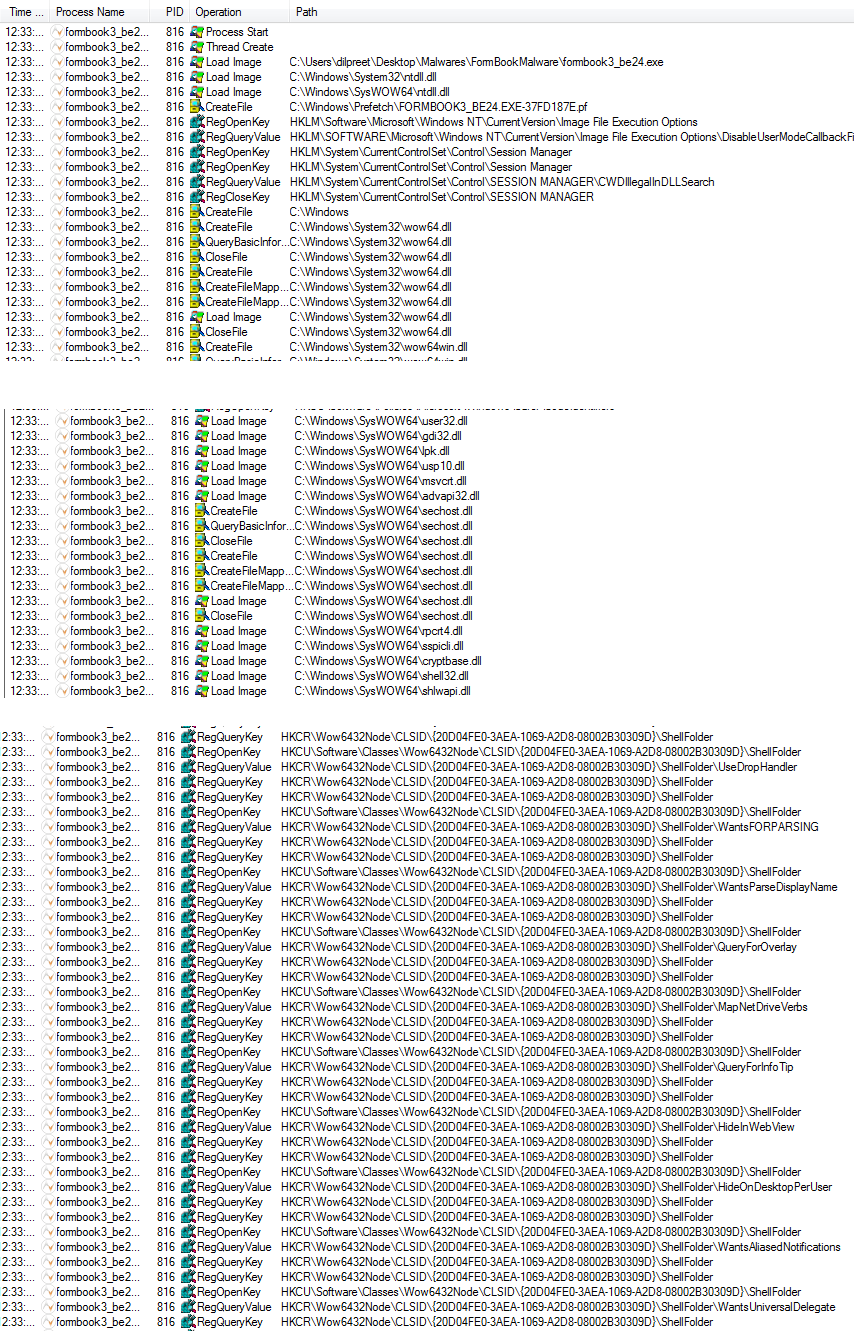
Figure21
Figure21 mentioned above shows the processes spawned by the malicious executable when it runs. It starts and creates various processes and threads, loads various system libraries, and accesses many registry entries.