



The Erbium malware is an information-stealer/ info stealer, which is distributed as Malware-as- a-Service (MaaS). CYFIRMA research team observed this malware binary in Aug-2022 while carrying out threat hunting activities. The team has also observed the stealer malware being advertised on Russian-speaking hacker forums.
The malware sample we have analyzed is a 32-bit executable binary. It contains obfuscated contents to evade detection by security products and firewalls. The malicious executable decrypts the obfuscated contents by using XORing logic after which it drops the 32-bit Erbium stealer DLL binary in the %temp% location and loads that dropped file in the current process by calling LoadLibraryA API. The dropped DLL files establish a connection to the Erbium stealer C2 server. Erbium malware establishes the connection to Discord’s Content Delivery Network (CDN) servers. Discord is a chat program that enables real-time communication between users through the internet and is being abused by threat actors to deliver malware. Info stealer malware developers sell these types of malware in underground forums and sell the harvest details in underground forums as well as criminal marketplaces. Ransomware affiliates or other threat actors purchase such details and then use these valid credentials, VPN, etc. as initial access to compromise the organization.
The malware [ErbiumStealer] has the following capabilities:
Recently CYFIRMA’s research team detected a new sample of Erbium stealer in wild. We observed one of the recent gaming campaigns where the threat actors lure gamers/players who want to acquire an unfair or prohibited edge over other players with the malicious binary posted on MediaFire [free service for file hosting]. Threat actors are spreading this malware using drive-by-download techniques and pretending as cracked software/game hacks. CYFIRMA’s research team on further monitoring activities associated with this campaign conclude that the identity of the threat actor is currently unknown for this Erbium stealer malware sample.
Erbium stealer malware is an information stealer, designed to gather sensitive data, including passwords for applications, credit card numbers, web browser cookies, auto-complete data, desktop files, machine data, installed software, crypto wallet stealing, etc, and send those details to the attacker command & control (C2) domain and can even download additional payloads from the C2 server.
From our analysis, we were able to find the following functionality available in the sample:
In recent years information stealers are one of the most popular malware types being used in the wild. Once the info stealers threat actor obtains the harvested information from victim systems, the threat actors/malware authors will act as an initial access broker[IAB]. These threat actors advertised those obtained details on the dark web such as breached[.]to as well as Russian language underground forum of XSS and special-access forums, along with cybercriminals marketplaces. Threat actors such as ransomware affiliates or other threat actors purchase these details. If a threat actor purchases these details, they have access to a variety of resources, which could lead to data exfiltration, lateral movement, and deploy other malware such as ransomware, etc. Even though there are other approaches, such as exploiting flaws in publicly accessible internet services, the use of stealer malware can cut down on costs and operation time. This is because this malware can access a system with valid credentials without hiring pen-testers for gaining initial access to the organization’s network, which reduces the risk of being discovered by perimeter protection systems.
A wide range of threat actors leverages commodity information stealers which are distributed as MaaS model that will be sold on the underground forum for USD (prices) based on a subscription basis. For example, Red Line stealer’s prices range from USD 100 to USD 300.
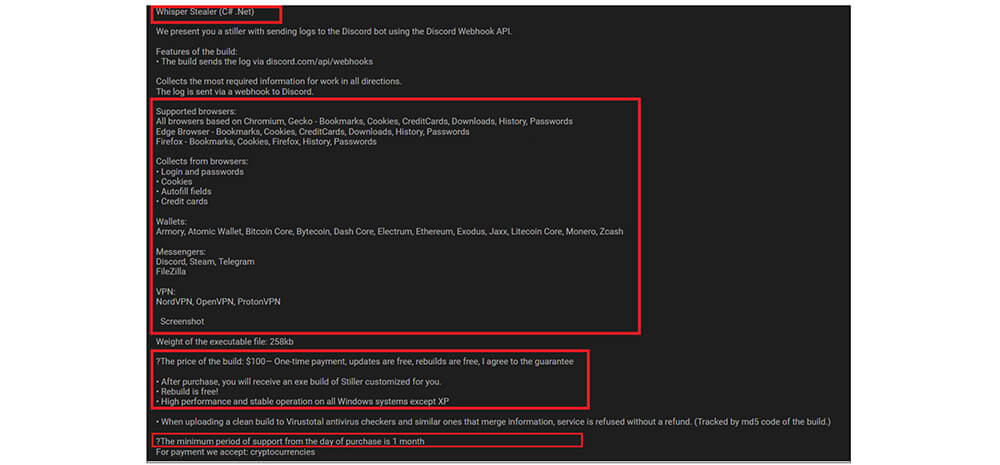
Another type of information stealer is private information stealers, which are developed by threat actors themselves by using already available stealer code on open-source platforms or developing [creating brand-new] information stealers, whenever the commodity information stealers do not fulfill threat actors’ requirements. private information stealers will be shared among a small set of cyber-criminals only for reduces the chances of detection. For example, recently, CYFIRMA’s research team observed Whisper Stealer selling on the underground forum for USD100 for a 1-month subscription. This stealer is C# .Net-based malware having the capabilities are collected from browsers, user credentials, cookies, autofill fields, credit cards, wallets, etc.
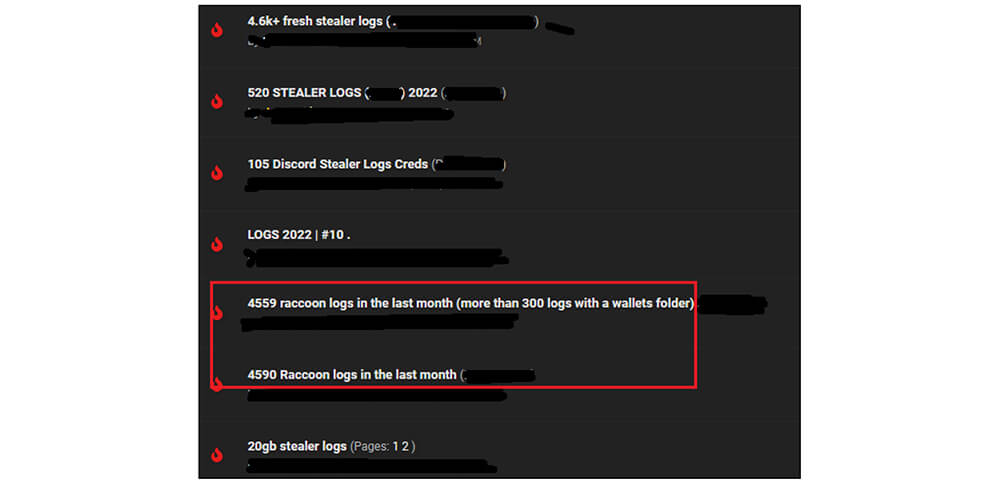
Just like the information stealer developers who sell malware samples developed by them in the underground forums, the malware developers also post their advertisements in the underground forum for selling the obtained logs [from victims] to cybercriminals.
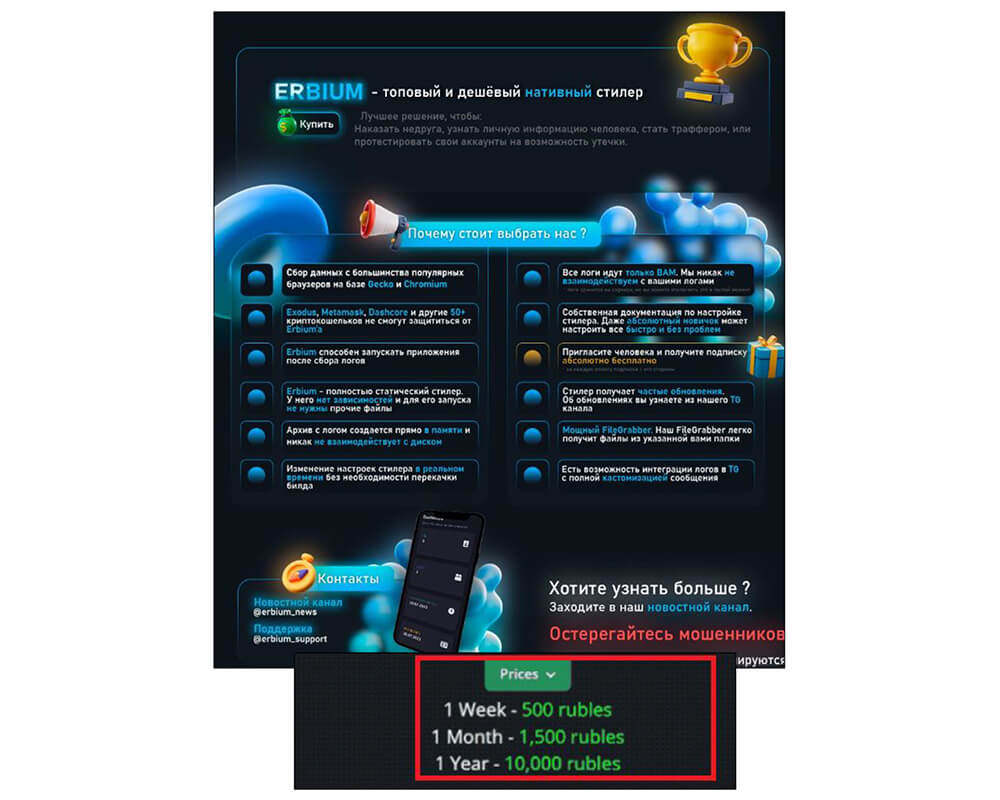
The Erbium stealer malware is being sold on one of the Russian hacker forums at 500 Rubles per week, 1500 Rubles per month, and 10,000 Rubles per year. The Erbium stealer team is running the technical support as well, indicating the malware team’s add-on functionality in the future.
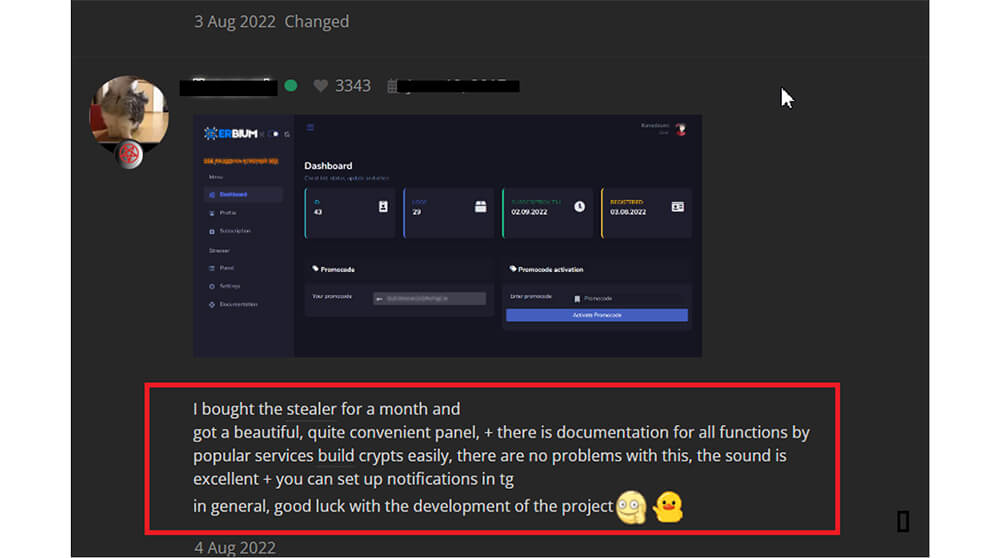
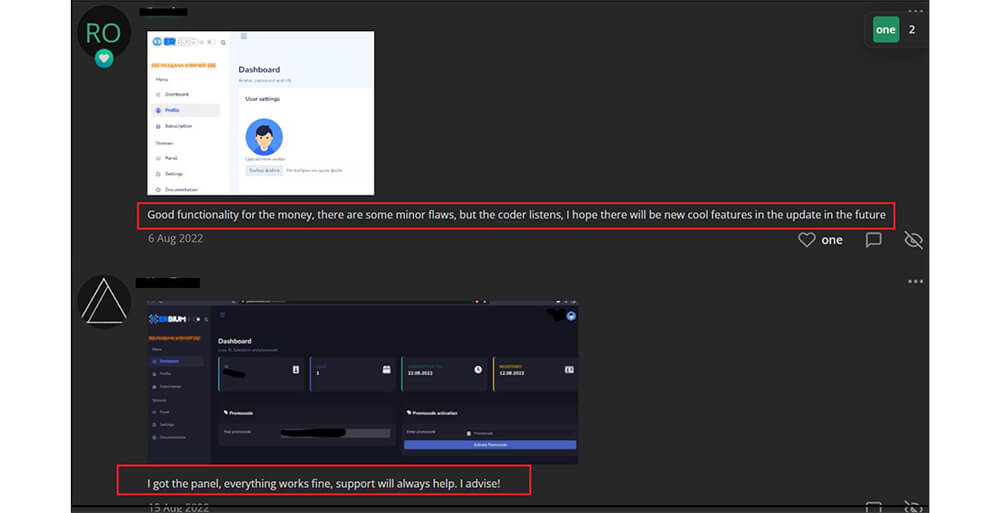
Below are screenshots of reviews given by Erbium stealer malware subscribers. on the dark web. Based on these reviews/feedback the Erbium stealer malware author makes modifications in the next version of the malware.

Basic Static Analysis of Erbium Stealer Malware:
Sample Details:
MD5: 1EF9C948E6045D8D8794A89CC9545B0F
SHA1: 7FA3530F3CC242075C04A43593FAEA2A8CE7A194
SHA256: 04642249B0AD41B1C6CC8862EC372C3B9B1E855D104A16A6A3FAE694CC23EC0C File Type: Windows PE
Architecture: 32 Bit
Subsystem: GUI
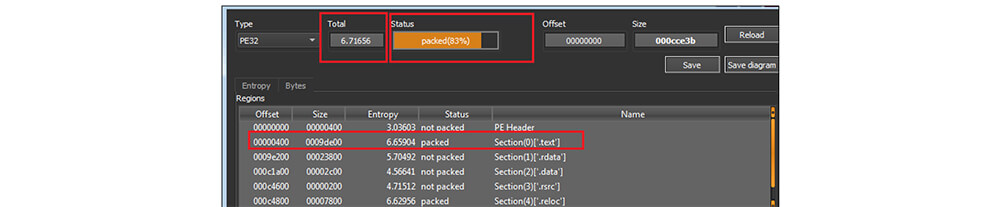
This malware was written in Microsoft Visual C++ programming language. This malware binary file’s size is 839227 (bytes). As shown in the below figure, this information stealer binary file has an entropy value is 6.71 and the code section was compressed by an unknown packer [custom].
Upon execution of this file, it decompressed the required dynamic DLL file names and file strings, URL, etc, which on execution are compressed by an unknown compressor[packer]. After that, it is dropping the information stealer [ErbiumStealer] DLL file in the temp location. Once the DLL file is dropped, that file is loaded in memory.
C:\Users\manoj\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\8LFDVDUP\clearkey[1].dll [md5:E53C97B18D69F5C6B7A854660E640700] ][product: Firefox] C:\Users\manoj\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BOT5RNIL\softokn3[1].dll [md5:3A59B504F6C41324B0D6CB6EDBE3AD61] ][product: Firefox] C:\Users\manoj\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\IIXT9CHD\freebl3[1].dll [md5:ED6249F72BA742802B2FA3EF20900D18][product: Firefox] C:\Users\manoj\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\IIXT9CHD\nss3[1].dll[md5:05ED4FFBF6B785750D2CDACCA9287F10][product: Firefox] C:\Users\manoj\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\TABIZERP\mozglue[1].dll [md5:5D59E053D45049FFB8C6C08D8944E30C][product: Firefox] C:\Users\username\AppData\Local\Temp\hiokcmapbccbelnex.dll[6BC81580D318DC8EBF48B3555DD4C9D7]
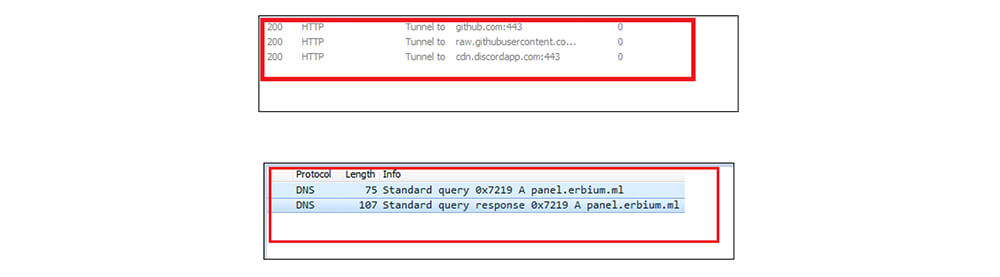
Once the Erbium Stealer file dropped the DLL file in the %temp% location, the dropped DLL [Erbium Stealer] file establishes a connection to the Panel: https[://] panel[.]erbium [.]ml, raw[.]githubusercontent[.]com and cdn[.]discordapp[.]com This malware tries to establish a connection to Discord’s Content Delivery Network (CDN) servers. While examining this malware code, this malicious file is not able to reach Discord’s Content Delivery Network (CDN) servers.
Recently CYFIRMA’ s research team published a research report on the malicious use of the discord app. You may visit the link: https://www.cyfirma.com/cyber-research-on-the-malicious-use-of-discord/, to get more in-depth knowledge that how threat actors use the application as a tool for malicious purposes:
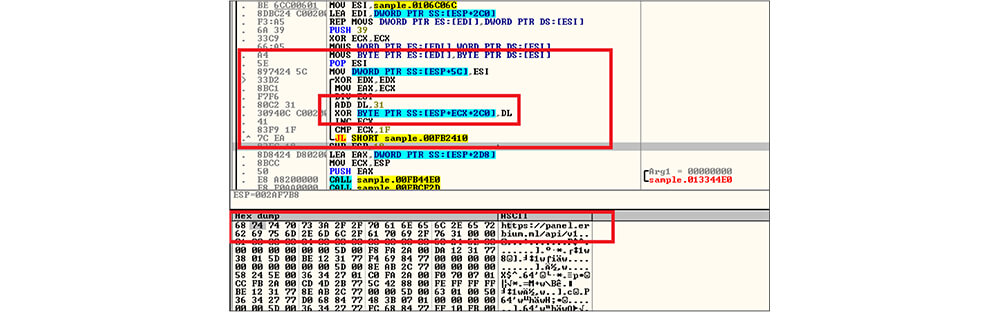
This information stealer malware is decrypting the obfuscated code by the XOR logic, to decode the encrypted code malware authors use the starting key 31[Hexadecimal value]. Depending upon the obfuscated content length the decryption keys are incrementing by 1. Before executing the malicious code this malware initially decrypts the Erbium Stealer panel URL.
Malware authors scatter the obfuscated contents as well as decryption logic code in the binary file to make it difficult for reverse engineering as well as writing the pattern [signature] to detect this malware by the antivirus engine.
It is followed by the malware getting the temp path by calling the GetTempPathA API then it creates a malicious DLL file [along with a legitimate DLL file] in the temp folder by calling the CreateFileA API.
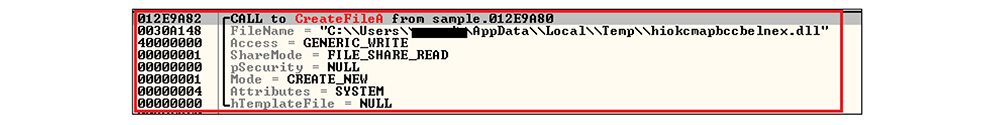
Next, the malicious executable writes the malicious DLL binary file content from the buffer to the created DLL file by calling WriteFile API.
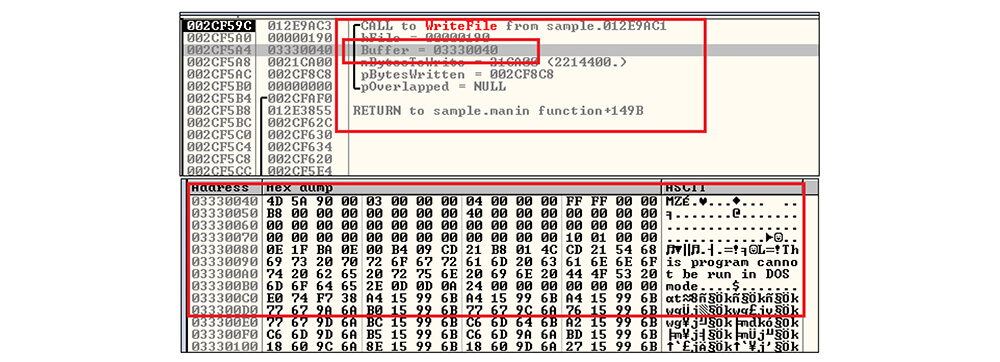
Once the malicious DLL file content has been written from the buffer to this file handle, the malware closes the handle and then decodes the required API function by executing above mentioned XOR logic. After that, this malicious DLL file loads into the address space of the calling process by calling LoadLibraryA API.

Basic Static analysis of dropped Erbium Stealer [DLL]
Sample Details:
MD5: 6BC81580D318DC8EBF48B3555DD4C9D7
SHA1: DABCED5B9F1EF63EFF6B29152192DFA1F1499481
SHA256: E3DD6D5CA0C9A16D95E4C591B7BBAD40E3D4D78BCF29CE6D8EA80B263C67F1C5
File Type: Windows PE
Architecture: 32 Bit
Subsystem: dynamic-link-library
This malware sample was also compiled in Microsoft Visual programming language. This malware’s binary file size is 2825728 (bytes). As shown in the below figure, this DLL file has an entropy value is 6.85 and the code section was compressed by an unknown [custom] packer.

Similar to file hash: 1EF9C948E6045D8D8794A89CC9545B0F this malicious file initially decrypts the required DLL files name, File contents, etc by the XOR logic. In this file, the decryption logic code also scatters to make it difficult and delay analysing the malicious code while doing reverse engineering.
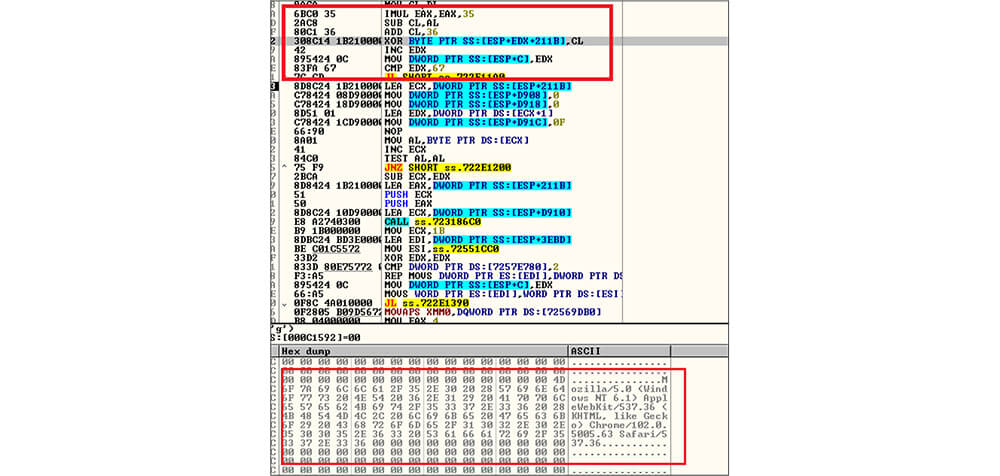
This DLL file is stealer malware that targets victim stored browser history and steals browser information, passwords for applications, credit card numbers, web browser cookies, auto-complete data, desktop files, machine data, installed software, crypto wallet stealing, authentication-related software, and password managers, etc. The below figure is one part of the memory strings.
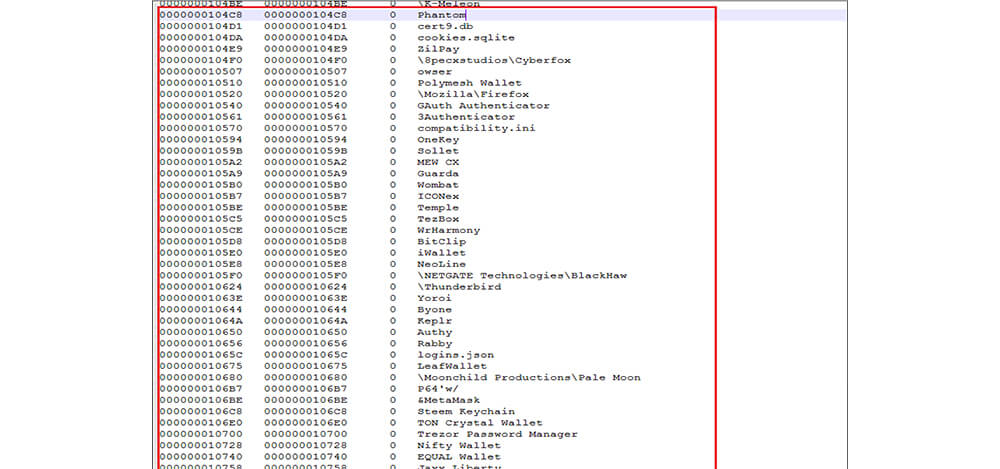
Erbium stealer malware steals passwords, cookies, and autofill information from the following web browsers as shown in the memory dump.
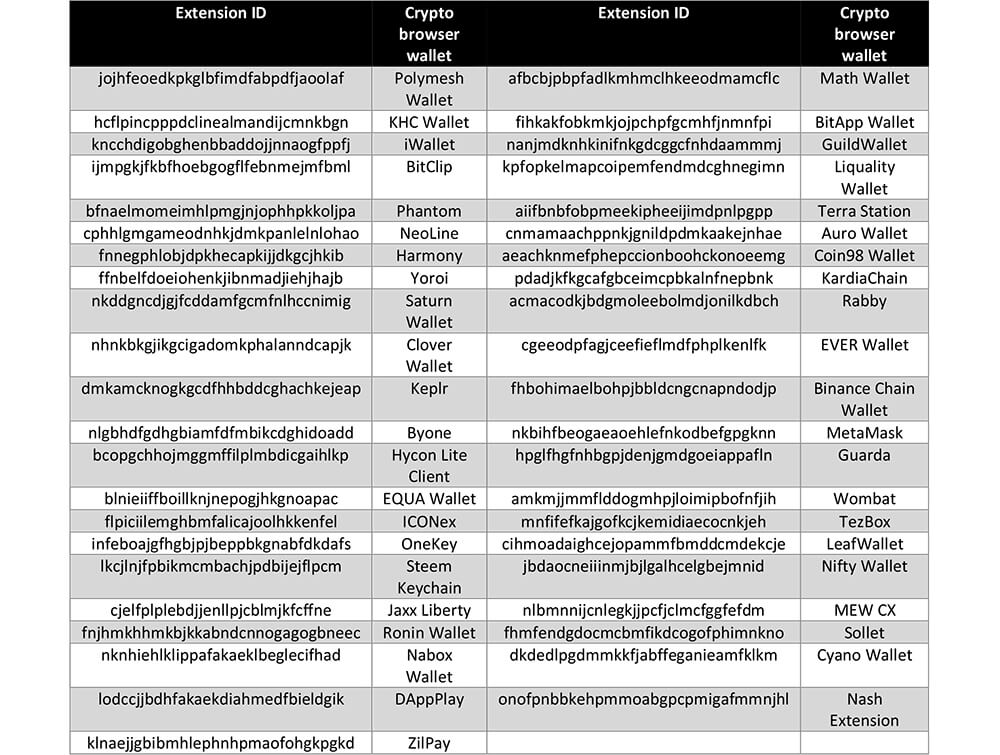
This malware also steals the data from the following crypto wallets:
This info stealer malware collects data from two-factor (2FA), multifactor authentication (MFA), and then password management software as well.
| Extension ID | Extension Name |
|---|---|
| bhghoamapcdpbohphigoooaddinpkbai | Authenticator 2FA |
| gaedmjdfmmahhbjefcbgaolhhanlaolb | Authy 2FA |
| oeljdldpnmdbchonielidgobddffflal | EOS Authenticator |
| imloifkgjagghnncjkhggdhalmcnfklk | Trezor Password Manager |
After that this DLL file de-obfuscate the obfuscated content, this malware obtains the user agent string Erbium-UA- 4ce7c27cb4be9d32e333bf032c88235a.
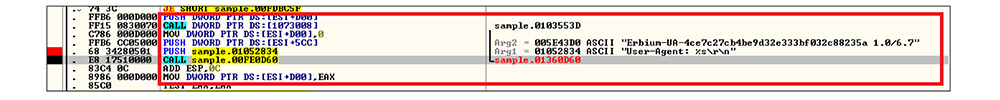
Like file hash: 1EF9C948E6045D8D8794A89CC9545B0F, this DLL file is decrypting the ErbiumStealer panel URL. In this DLL file memory and creating socket connection then establishing a connection to panel[.]erbium[.]ml.
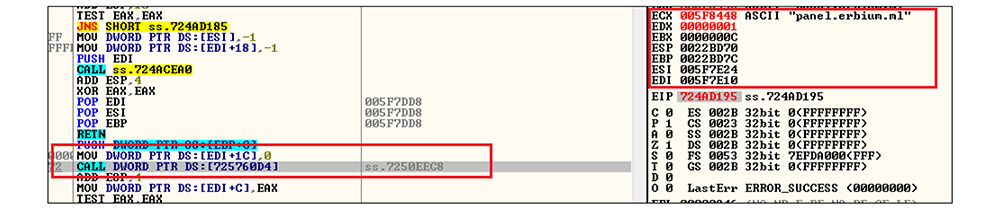
After that this DLL file creates a thread by calling CreateThread API and executing the malicious code on the thread.
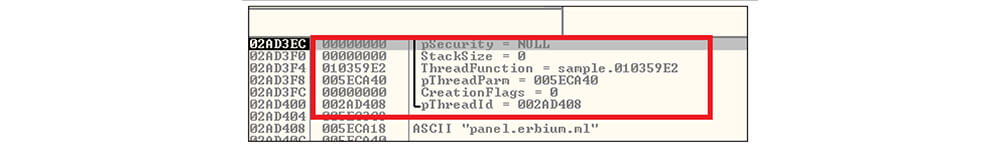
These threat actors sent the data to the threat actor-controlled server by calling the send API.
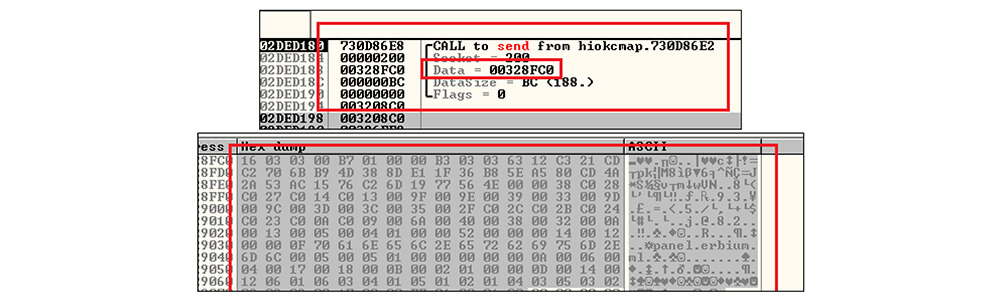
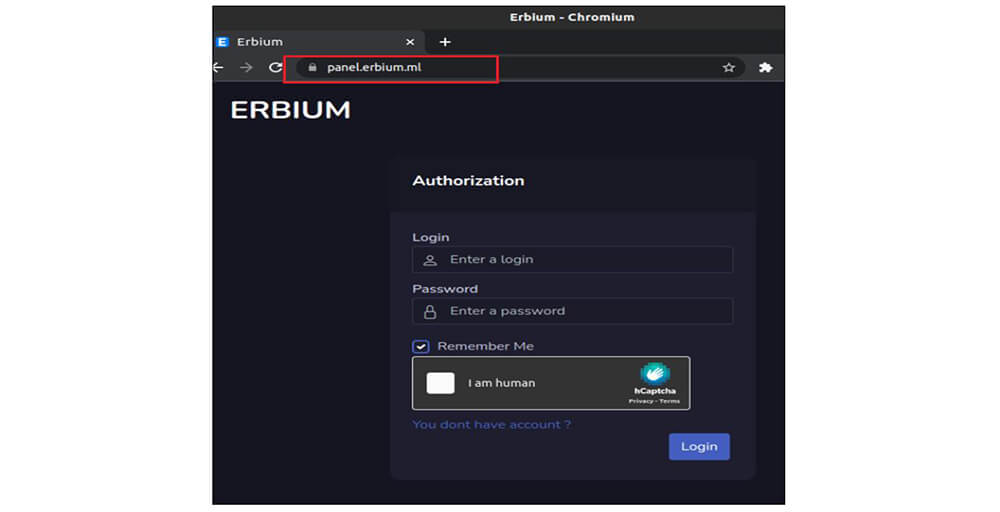
The figure below shows the Erbium stealer panel.
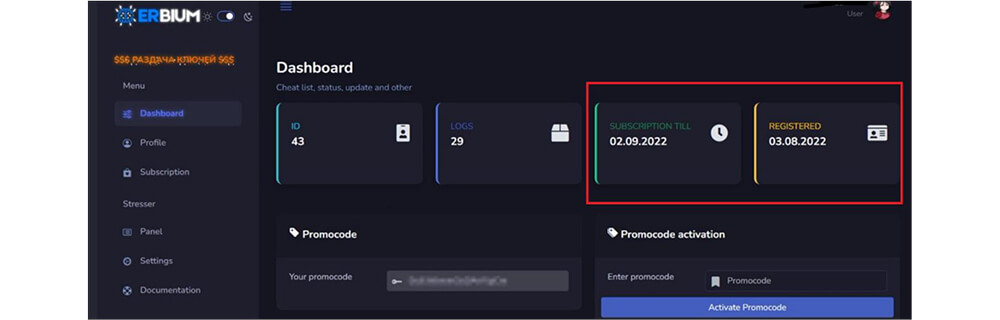
The figure below shows the Erbium stealer Dashboard. This Dashboard shows how many logs so far received from the victim machine. also, this Erbium stealer Dashboard shows when the subscription user registered with this MaaS service, and which date the subscription is going to end.
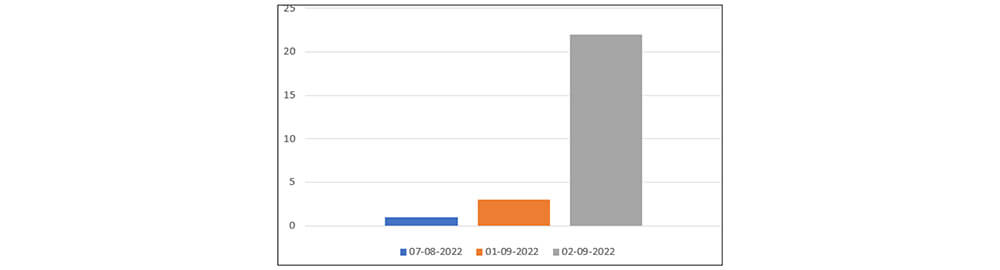
Recently, CYFIRMA’s research team observed the Erbium stealer malware sample volume increased on the 2nd of September, in the wild.
“Erbium stealer” malware is spread through several tactics, including spear-phishing, malicious advertising, exploit kits, and malware loaders such as Smoke Loader, Private Loader, etc. The malware is associated with an unknown threat actor. This malware gathers sensitive data, including passwords for applications, credit card numbers, web browser cookies, auto-complete data, desktop files, machine data, installed software, etc. This malware also has crypto wallet stealing capabilities. Finally, information stealer malware developers sell the gathered details on the underground forum and cybercriminal marketplaces.
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | 1EF9C948E6045D8D8794A89CC9545B0F | MD5 | sample |
| 2 | 6BC81580D318DC8EBF48B3555DD4C9D7 | MD5 | Erbium stealer DLL file |
| 3 | Erbium-UA-4ce7c27cb4be9d32e333bf032c88235a | strings | User-agent |
| 4 | Panel[.]erbium[.]ml | Ip address | Erbium stealer control panel |
| 5 | LrtmqR1muOHUwcTB | strings | File strings |
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Execution (TA0002) | T1106: Native API |
| 2 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| 3 | Credential Access (TA0006) | T1539: Steal Web Session Cookie T1552.001: Unsecured Credentials: Credentials In Files |
| 4 | Discovery (TA0007) | T1057: Process Discovery T1082: System Information Discovery |
| 5 | Collection (TA0008) | T1005: Data from Local System |
| 6 | Command and Control (TA0011) | T1573: Encrypted Channel |