



HTML smuggling is a highly evasive technique that abuses legitimate HTML5 and JavaScript features to evade detection and deploy RATs, banking malware, and other malicious payloads. The nation-backed hacking groups and other cyber criminals are extensively using this technique to compromise governments, individuals, and organizations. For example, the NOBELIUM group – suspected to be associated with Russia – targeted government and diplomatic entities around the globe and used the HTML smuggling technique in past. Microsoft researchers have tracked the malicious HTML attachments used by the NOBELIUM group in one of the campaigns as EnvyScout and described it as a malicious dropper capable of de-obfuscating and writing a malicious ISO file to disk.
HTML smuggling is a stealth technique adopted to deliver malicious payloads. Over decades threat actors have used Macros in Microsoft documents as their primary infection/attack vector. With Microsoft blocking VBA macros by default in Office applications, threat actors had to find alternative techniques to lure victims and deliver malicious payloads. For example, malware like Emotet, Icedid, and QakBot have already started using LNK files, ISO files, or IMG files and techniques like HTML smuggling to deliver malware. Even though such attacks and techniques are still evolving, researchers have observed a many-fold increase in their adoption since January 2022. Particularly nation-backed groups like NOBELIUM/APT29 along with prominent malware like Emotet, and QakBot are extensively utilizing the HTML smuggling technique to target individuals as well as organizations.
Generally, threat actors use HTML smuggling in one of the two ways:
There are several ways to write the same HTML smuggling logic in JavaScript code. Malware authors can use obfuscation and assemble the payload locally on the machine behind the firewall which makes this technique highly evasive. To mitigate such techniques, organizations need to adopt multi-layered and defense-indepth solutions in a collaborative manner.
CYFIRMA has observed that the HTML smuggling technique has been used by threat actors like NOBELIUM to deliver malware like Mekotio, AsyncRAT, Trickbot, and recently QakBot. This malware is essentially used to gain control of victim machines, effectively deliver payloads, and execute ransomware attacks.
In HTML smuggling, the attacker uses a specially crafted HTML attachment that carries an encoded malicious script. When the victim opens this malicious HTML file in their web browser, the browser decodes this embedded malicious script which on execution further assembles the payload on the victim machine. The main advantage to threat actors is that instead of passing the payload over the network, the malicious payload assembles on the victim’s machine. This makes the technique highly evasive because it could bypass standard security controls like web proxies, firewalls, and email gateways. As the payload is only created when the malicious HTML file is loaded on the victim’s machine through the web browser, the security solutions only see HTML or JavaScript traffic which can be further obfuscated to evade detection.
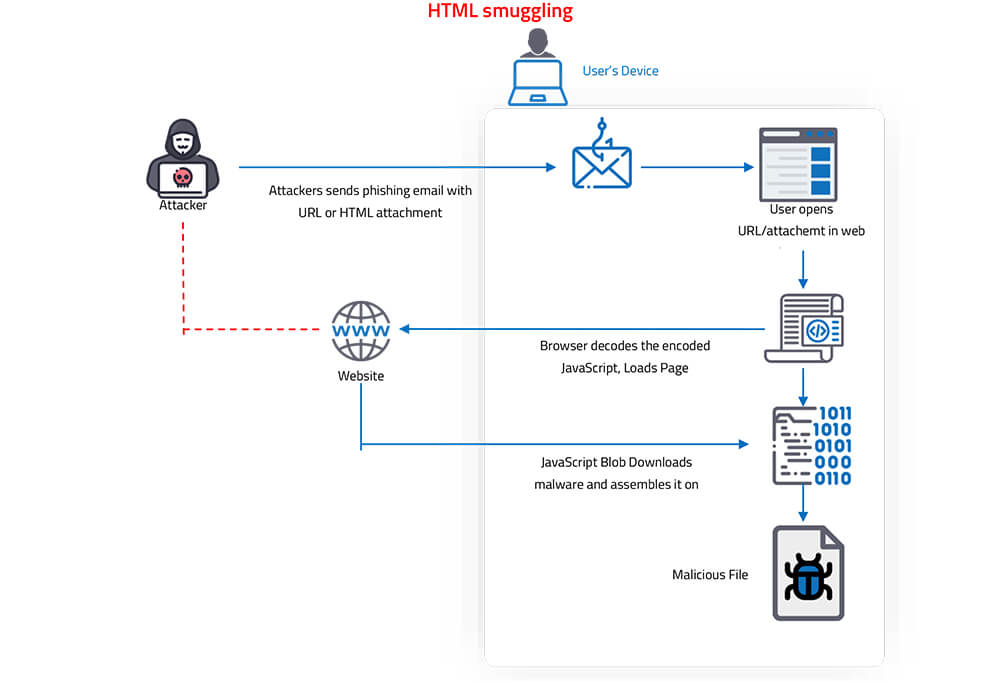
HTML smuggling uses legitimate features of HTML5 and JavaScrip browsers – to create malicious binaries behind the firewall. Specifically, the technique leverages HTML5’s “download” attribute for anchor tags, as well as the creation and use of a JavaScript Blob to put together the malicious payload on the victim’s machine.
Anchor Tag <a>: The anchor tag <a> is a tag in HTML which defines a hyperlink and is used to link from one page to another resource like the script, other HTML pages, or downloadable files.
The most important attribute of the <a> element is the href attribute, which indicates the link’s destination.
For example:
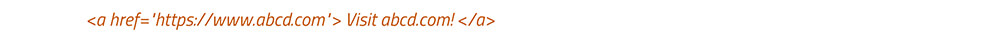
When <a> is used with the “download” attribute, it can be used to provide links to a downloadable file.
For example:

As shown above, when the user clicks a link “Click_Here” in our case, the “download” attributes automatically download the file referenced in “href” tag. The above code instructs the browser to download “malicious_document.docx” from the specified location and save it onto the victim’s machine as “trusted_document.docx”.
The JavaScript code also has an equivalent to an HTML anchor tag and its download attribute as shown below.

The use of JavaScript Blobs adds to the “smuggling” aspect of the HTML smuggling technique.
A Blob is an immutable object that represents raw data – simply a collection of bytes that holds the data stored in a file. The Blob data is stored in memory or file system depending upon the size of the Blob and the browser features. A Blob can be used anywhere, for instance, the Blob allows us to construct file-like objects on the user machine that can be passed as parameters to JavaScript APIs that expect URLs.
Therefore, instead of requiring that the web server provides a file, a Blob can be constructed locally using JavaScript. For example, a “malicious.exe” file hosted on a server is downloaded on the target system using HTML anchor tag and attribute download . In the same way, bytes of malicious.exe file or JavaScript Blob can be provided as input which can be downloaded and compiled on the user machine.
If the Blob is large in size, the Slice() function is used to divide a large payload and provide it as an input.
For example:
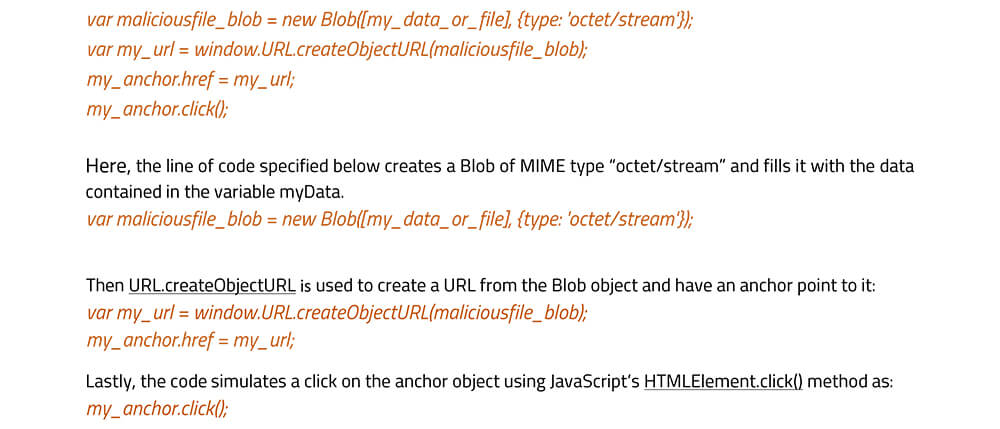
This will result in triggering the anchor’s click event, which in turn points to our blob to be downloaded as “maliciousfilename.doc”. These features are supported by all modern browsers. For older versions of Internet Explorer, msSave Blob method may be used to save a Blob object to disk.
In nutshell, a JavaScript Blob can store encoded data of a malicious file, which is later decoded and passed to a JavaScript API that expects a URL. So instead of providing a link that a user clicks manually to download such a file, it is automatically downloaded and created locally on the user’s machine using JavaScript code.
CYFIRMA research team is continuously monitoring new tactics, techniques used by threat actors along with ongoing campaigns and methodology followed by cyber-criminals to compromise organizations and individuals. Recently, in July 2022, our research team monitored an operation consisting of a series of emails related to the QakBot malware campaign.
QakBot, is also known by the name QBot, QuackBot, and Pinkslipbot. The malware is an information stealer that has been active since 2008. For initial infection, QakBot malware uses spam or phishing email, and it continuously evolved its infection techniques ever since it was initially identified in the wild. In this campaign, the spam emails contain an “HTML” file as an attachment which used the “HTML smuggling” technique to deliver a password-protected zip file. “HTML smuggling” is one of the other possible attack vectors using HTML attachments and JavaScript. And this is what is being used in this campaign in combination with the QakBot malware in spam emails.
Below are the snapshots of the code available in the attached HTML file of spam email:
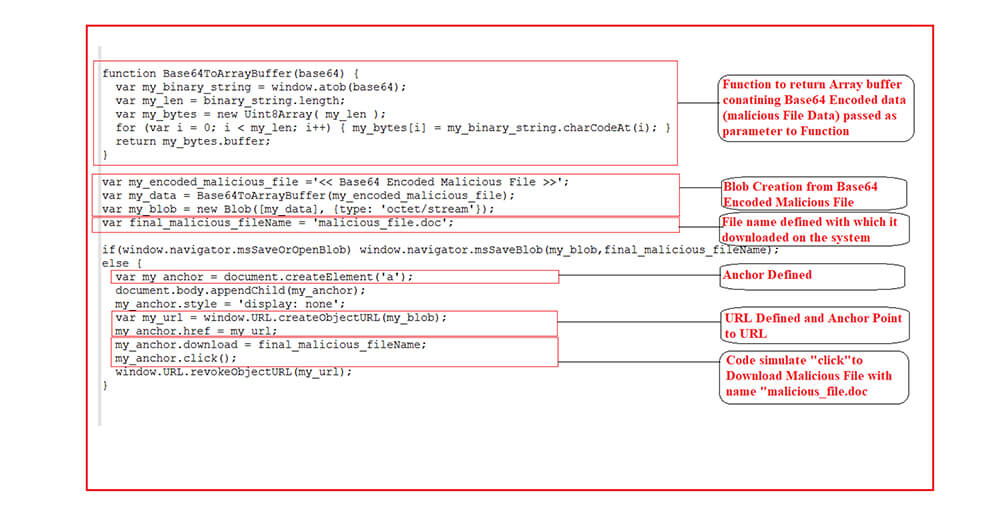
As shown below, the HTML file code has Base64 encoded malicious file code stored in the variable “text” which gets downloaded with the name “Report Jul 14 47787.zip”. There is also a series of functions defined at the end of the snapshot which is further obfuscated to implement the HTML smuggling technique and finally download the malicious zip archive with the name “Report Jul 14 47787.zip”.
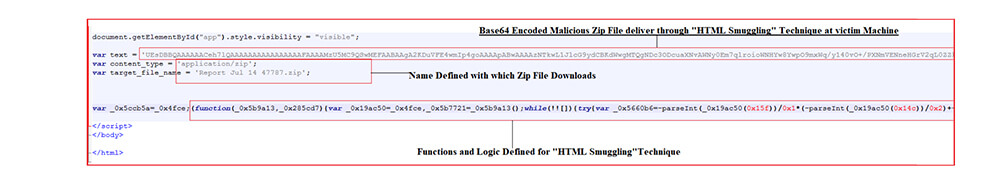
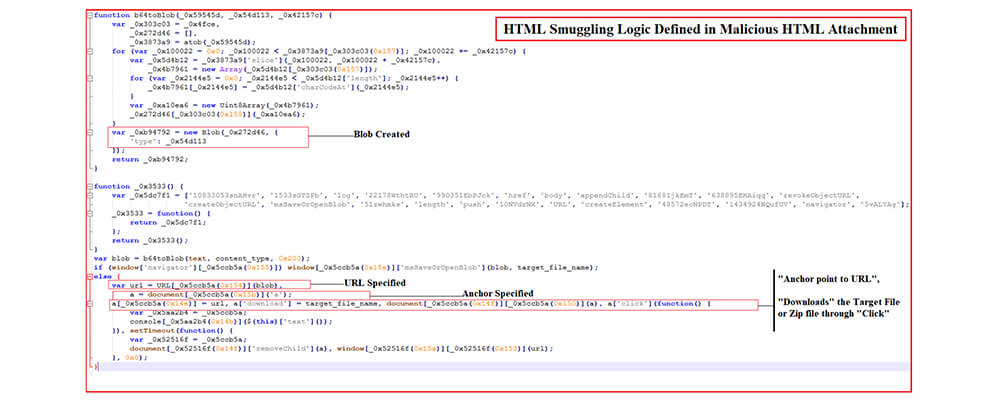
Above is a code snippet corresponding to the HTML smuggling technique’s implementation extracted and attributed for better understanding. In this instance, first, a JavaScript Blob is created containing data corresponding to a malicious Base64 encoded malicious zip archive. Subsequently, Anchor and URL objects are created where the anchor object point to the URL object, after which a click to download the malicious zip file is automatically simulated.
The zip file is password protected – the password is stored in the HTML file.
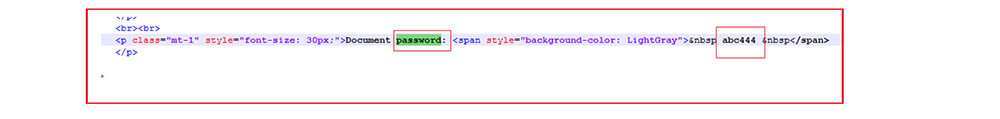
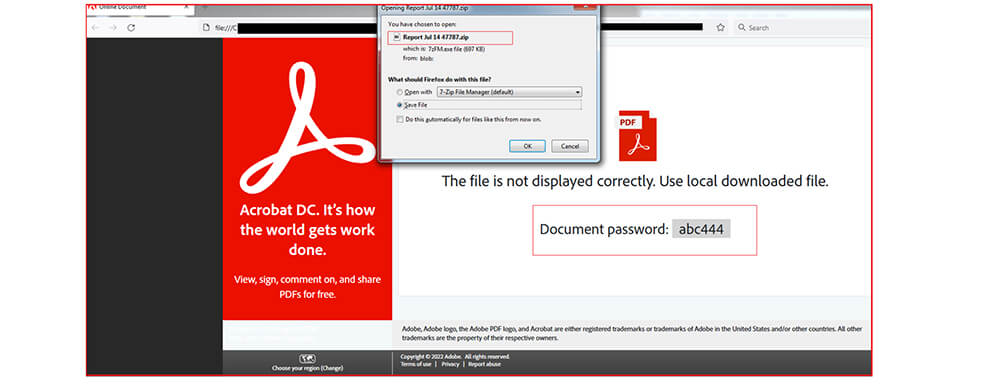
As shown below, when the victim opens the file, the zip file automatically downloads to the user’s system through the HTML smuggling technique as depicted above. The password is also displayed to the user to extract the zip file. The zip file contains an ISO file with the same name as the zip file but with extension iso |(i.e., Report Jul 14 47787.iso).
Upon extraction of this .iso file we get four files: a .Ink file, a legitimate calc .exe, WindowsCodecs.dll, 7533.dll.
This shortcut (.Ink) file points to calc.exe as shown below
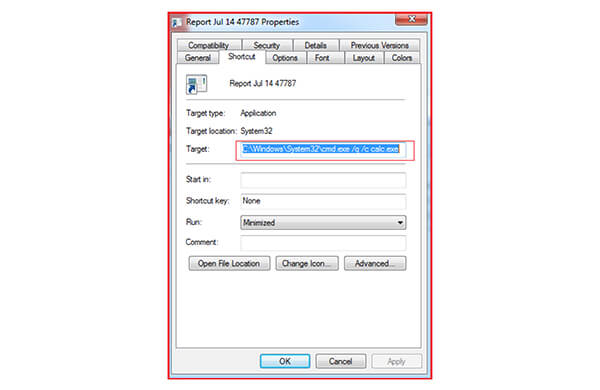
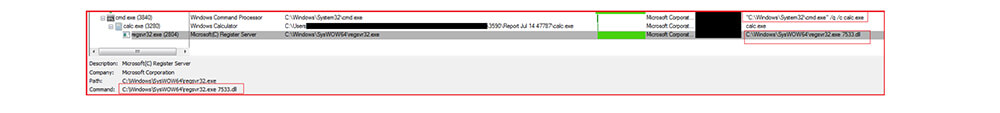
Upon clicking the shortcut file, the calc.exe gets executed and automatically loads the malicious WindowsCodecs DLL file. Here the malware authors are observed using another technique known as DLL sideloading to execute the malicious code. In this technique, malware author place legitimate applications (calc.exe) and malicious .dll (WindowsCodecs.dll) files together in the same folder. The malicious DLL name should be the same as the DLL or support file required by the legitimate application during execution so that the threat actor can leverage this technique and load the malicious DLL file. In this case, as specified calc.exe is a Microsoft legitimate application and WindowsCodecs.dll is the malicious DLL which disguised as a valid DLL, and loads by the calc.exe application, which further executes the final QakBot payload 7533.dll using windows living off the land binary regsvr32.exe as shown below.
Threat actors and malware authors are using techniques like HTML smuggling in their operations to deliver malware stealthily. The technique is more effective because it relies on the legitimate use of HTML and JavaScript as both are used to render valid webpages and as such their malicious users cannot be mitigated through conventional procedures. Groups like NOBELIUM and other cybercriminals continue to mature their tools and tactics, including new techniques like HTML smuggling to target governments, institutions, and organizations.
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Initial Access (TA0001) | T1566 Phishing |
| 2 | Execution (TA0002) | T1204 User Execution T1204.002 Malicious File T1059.007 Java Script T1027.006 Obfuscated Files or Information: HTML smuggling |