



Suspected Threat Actors: TA575
Summary
The security researcher identified a large cybercrime threat actor TA575 distributing Dridex malware using “Squid Game” lures – a TV mini-series on Netflix. Purporting to be entities associated with the TV mini-series, the threat actor used emails to entice potential targets to get early access to a new season of Squid Game or to become a part of the TV show casting. These emails carried macro-laced Excel documents which were to be opened by the victims. When enabled, the macros will download the Dridex banking trojan from Discord URLs which can be used to perform data theft and install additional malware such as ransomware.
Insights
As per the researcher, the threat actor group, TA575 is a Dridex affiliate and has been active since at least late 2020. This group is known to distribute malware via malicious URLs, Microsoft Office attachments, and password-protected files. According to the researcher, TA575 heavily relies on spam campaigns using thousands of emails per campaign and impacting hundreds of organizations. In addition, the Discord content delivery network (CDN) has also been used to host and distribute Dridex malware. The VoIP, instant messaging, and digital distribution platform – Discord – is an increasingly popular malware-hosting service among cybercriminals.
The lures used by TA575 generally include invoicing and payments, however, the threat actor groups have been observed using news, events, and cultural references on occasions. As such, Netflix’s “Squid Game” based lures are going to present a large pool of potential victims who might inadvertently interact with malicious content since the series is considered a major hit and is extremely popular worldwide.
CYFIRMA researchers observed Transource Services Corp (http://www.transource.com/) – a manufacturer of electronic computers and related peripherals – being impacted by the Grief ransomware. It is suspected that the operators have exfiltrated a large amount of business-critical and sensitive data. At the time of CYFIRMA’s observation, the threat actors have published samples of exfiltrated data as part of an advertisement to sell this data to potential buyers on their dedicated leak site.
The following screenshots were observed published on the dark web:
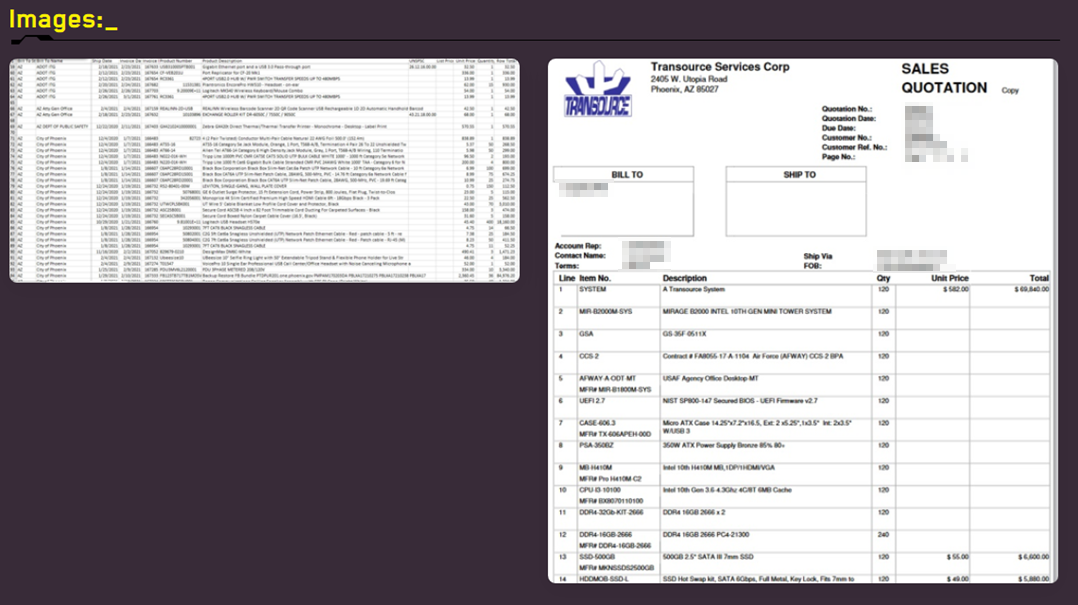
Source: Darkweb
Insights
Making an appearance around July this year, the Grief ransomware has recently entered the multi-billion-dollar ransomware market alongside another new ransomware player – Prometheus. Grief is comparatively a lesser-known ransomware group; however, they have claimed to have stolen data from multiple organizations to date. Their data leak portal located inside the TOR network employs “anti-crawl” protection that prevents cybersecurity researchers and defenders from automated monitoring of published content by various threat intelligence platforms.
Interestingly, the landing page of their data leak portal has a reference to GDPR (General Data Protection Regulation) Article 33 that essentially requires data controllers to notify any personal data breach to the appropriate authority – a clever form of scare tactic to extort money out of victims.
This tactic may perhaps turn fruitful for the operators since the victims are faced with a double-edged sword. On one hand, they are duty-bound to report such incidents, and on the other hand, the operator will leak the data in the event of non-payment of ransom demand which eventually becomes public knowledge.
Further, the GDPR empowers authorities to issue fines that will be comparatively much higher than possible ransom demands.
The portal also tries to incite the psychological bias of the potential victims by showcasing ‘facts’ such as the possible 10x times higher cost of an unplanned downtime when compared to ransom requests, furnished as infographics for easy and effective consumption.
Summary
A researcher recently disclosed information on a newly identified malware campaign targeting Windows 10 with malware that can infect systems via a technique that cleverly bypasses User Account Control (UAC) protection in Windows systems. According to the researcher, the goal behind this campaign is to steal sensitive data and cryptocurrency from infected systems. The attack chain is initiated when a user visits a malicious website on Chrome browser and a “browser ad service” prompts the user to take any action which eventually leads to the installation of an infostealer malware as a Windows application. The attackers used a compromised website – specially crafted to exploit the version of Google Chrome running on Windows 10 – to deliver the payload. Unclear from the research, however, users were coaxed into allowing the suspicious domain to send notification requests via the Chrome browser. Once enabled, the users were forwarded to a malicious Chrome browser update linked to a Windows application package called an MSIX type file.
Insights
As per researchers, the malware observed, in this case, has several tricks up its sleeve. Its delivery mechanism via an ad service as a Windows application (which does not leave typical web-based download forensic artifacts behind), Windows application installation path, and UAC bypass technique by manipulation of an environment variable and native scheduled task can go undetected by various security solutions or even by a seasoned SOC analyst.
Summary
Technical details related to a Windows zero-day privilege elevation vulnerability and a public proof-of-concept (PoC) has been disclosed by a security researcher. Under certain conditions the bug allows users to gain SYSTEM privileges. In August, Microsoft had released a security update for the vulnerability titled “Windows User Profile Service Elevation of Privilege Vulnerability” tracked as CVE-2021-34484. Further examination of the fix by a security researcher who discovered it revealed that the patch was not sufficient and allowed him to bypass it with a new exploit that he published on GitHub.
Insights
Abuse of this bug on a wider scale is less likely as observed in the case of PrintNightmare since the exploit requires the malicious actor to know the username and password of another user to trigger the vulnerability. However, the researcher highlighted that the vulnerability should be concerning as the threat actor would only need another domain account to exploit the vulnerability.
In addition, the bug affects all versions of Windows, including Windows 10, Windows 11, and Windows Server 2022.