



Suspected Threat Actors: WIRTE APT Group
Summary:
A threat actor named WIRTE targets government, diplomatic entities, military organizations, law firms, and financial institutions in the Middle East. The activities of the WIRTE group have been documented by cybersecurity researchers in 2019, who found it to be politically motivated with links to the Gaza Cyber group.
The group launched spear-phishing campaigns using weaponized Microsoft Office documents to deploy VBS/VBA implants. The weaponized Excel documents acted as droppers that use hidden spreadsheets and VBA macros to deliver a first stage implant, which is a Visual Basic Script (VBS). The VBS implant is a script that collects system information and executes arbitrary code on the infected machine. The first stage implant also downloads and installs a next-stage dropper named Ferocious that leverages a living-off-the-land (LotL) technique called COM hijacking to achieve persistence and execute another PowerShell script dubbed LitePower Stager
Insights:
WIRTE modified their toolset and how they operate to remain stealthy for a longer period. LotL techniques are an interesting new addition to their TTPs. This suspected subgroup of the Gaza Cyber group used simple yet effective methods to compromise its victims with better OpSec than its suspected counterparts. Whether WIRTE is a new subgroup or an evolution of existing Gaza Cyber group subgroups, we see them expanding their presence further in cyberspace by using updated and stealthier TTPs.
Source: Security Affairs
Israel’s Ministry of Defence has reduced the list of countries to which Israeli surveillance and cybersecurity firms could trade their products and services. 65 countries have been excluded from the existing export list, but now the number is reduced to 37 nations, by the Israeli Government.
The export list currently only includes Australia, Austria, Belgium, Bulgaria, Canada, Croatia, Cyprus, Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Iceland, India, Ireland, Italy, Japan, Latvia, Liechtenstein, Lithuania, Luxembourg, Malta, New Zealand, Norway, Portugal, Romania, Slovakia, Slovenia, South Korea, Spain, Sweden, Switzerland, the Netherlands, the U.K., and the U.S.
Israel’s Ministry of Defence removed countries such as Morocco, Mexico, Saudi Arabia, or the UAE, from the list because they abused the surveillance software acquired from the Israeli NSO Group.
The decision to cut the list comes after the announcement of The Commerce Department’s Bureau of Industry and Security (BIS) to sanction four companies for the development of spyware or the sale of hacking tools used by nation-state actors.
The new list will significantly complicate matters for Israeli cybersecurity companies, especially those selling offensive cyber tools, to operate in countries with totalitarian regimes or with a record of violating human rights.
The Israeli cybersecurity sector currently generates USD10 billion in annual revenue, with offensive cyber believed to be responsible for 10% of those sales. Some 13% of all cybersecurity companies operate from Israel, with 29% of all investments in the sector being directed to Israeli companies.
Summary:
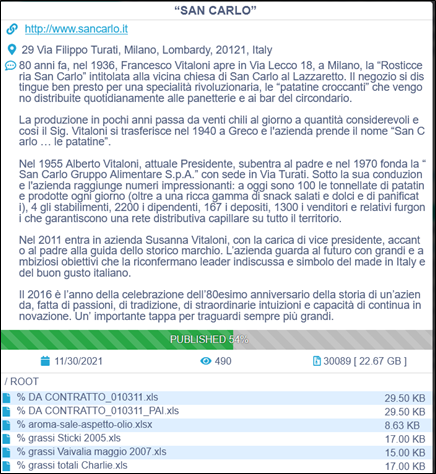
CTI observed San Carlo (http[:]//www[.]sancarlo[.]it) – an Italian manufacturer of snack foods – being impacted by the Conti ransomware group. The ransomware group is claiming to have exfiltrated approximately 22 gigabytes of potentially sensitive data. At the time of CTI’s observation, the ransomware group has started publishing exfiltrated data on their dedicated leak site.
The following screenshot was observed published on the dark web:
Insights:
Researchers have associated three vulnerabilities being exploited by the Conti ransomware operators which include CVE-2020-0796 affecting Microsoft products, and CVE-2018-13374 as well as CVE-2018-13379 existing in Fortinet’ FortiOS.
Researchers also believe that the Russian APT group Wizard Spider uses the Conti ransomware in its attacks.
The stolen data is first made available for sale to potential buyers. As the ransom payment gets delayed the ransomware operators resort to publishing parts of the data as time goes on. Ultimately, if no ransom is paid and the data is not purchased, the data is released to the public for free for anyone to download.
While most ransomware providers often put a lot of effort to establish their reputation and attempt to maintain some level of integrity likely to encourage and facilitate ransomware payments, Conti has shown atypical behavior. In recent cases, Conti did not keep up the promise after ransom payments were received from victims.
Last month, the Conti ransomware group appeared to alter its ransomware business plan by selling access to the infiltrated victim’s network. Researchers have pointed out that many of the ransomware groups are finding it hard to maintain their DLS and some are leveraging public file sharing services such mega[.]nz. However, hosting leaked data on the clear web has its downsides and such content gets taken down in a couple of days. In addition, due to Tor’s architecture, the download speed is considerably slower, and the datasets are often large. The DLS also leaves the ransomware group vulnerable to attacks. The REvil representatives recently revealed that their data-leak site was “hijacked”.
It is suspected that these difficulties are discouraging ransomware groups to continue the use of DLS style of ransomware operations and we may more creative solutions to overcome these challenges.
Summary:
Researchers discovered during August and November 202 four distinct Android banking trojans were spread via the Google Play store. As per researchers, the malware has infected approximately 300,000 devices by leveraging multiple dropper apps. The threat actor used refined techniques to bypass Google Play Store security checks. By introducing carefully planned small malicious code updates over a longer period and another technique that leveraged the look-alike command-and-control (C2) website matching the theme of the dropper app, the threat actor bypassed conventional detection methods. The droppers distributed Android banking trojan namely Anatsa, Alien, ERMAC, and Hydra.
Insights:
According to researchers, such kind of malware distribution campaign on the Google Play Store are very difficult to detect since the dropper apps have a very small malicious footprint. This is due to recently enforced permission restrictions by Google Play such as Accessibility Services. Threat actors in previous dropper campaigns used to abuse this service to automate the installation without user consent. The permission restriction forced threat actors to significantly reduce the footprint of dropper apps.
Summary
The vulnerability tracked as CVE-2021-40438 – a server-side request forgery (SSRF) can be exploited in Apache HTTP servers that have the mod_proxy module enabled. The critical flaw can be leveraged by an attacker using a specially crafted request to cause the module to route connections to an origin server of their choice. The flaw patched in version 2.4.49, affects version 2.4.48 and earlier versions. The German cybersecurity agency and Cisco, both have warned of attacks targeting this flaw.
Insights
As per researchers, successful exploitation would allow attackers to exfiltrate secrets (like infrastructure metadata or keys) or access other internal servers. An estimated 500,000 servers running vulnerable versions have been noted by the researcher at the time of reporting. However, researchers highlight that cloud services (such as AWS, Microsoft Azure, and Google Cloud Platform) protect against such attacks. Therefore, the organization running on-premises servers is mostly at risk.
It should be noted that multiple proofs-of-concept (POC) have already been published for CVE-2021-40438.