



IcedID & Qbot: Researchers have disclosed two new campaigns observed in March with English messages and contained ZIP attachments or links to ZIP files. Both campaigns ultimately aimed towards distributing banking Trojans. Researchers reveal in most cases the payload was IcedID, however, few samples delivered QBot. It was noted that the IcedID authors changed the downloader a bit by moving from x86 to an x86-64 executable and removed the fake C&Cs from the configuration observed in the previous version. As opposed to IcedID, QBot is a single executable with an embedded DLL.
A new malware dubbed Crackonosh was observed making its way to infect Windows devices via cracked and pirated copies of software and video games. The attackers are mining cryptocurrency without the user’s knowledge. The malware installs the coin miner XMRig to mine Monero cryptocurrency from within the cracked software and is suspected to have 2 million USD worth of XMR. With infecting devices rising approximately 1000 per day, the malware is suspected to infect 222,000 unique devices in more than a dozen countries.
Summary: While investigating samples of a remote access trojan (RAT) dubbed NukeSped, researchers came across several samples of Bundlore adware using the same fileless routine that was spotted in NukeSped. The backdoor, NukeSped attributed to Lazarus is known to have multiple variants targeting 32-bit systems and uses encrypted strings to evade detection. Recently a custom backdoor malware known as ThreatNeedle tracked under the cluster of Manuscrypt (aka NukeSped) was used to target organizations in the defence industry by leveraging COVID19-themed cyberespionage campaign.
The encrypted Mach-O file discovered in these samples has upgraded Bundlore to a stealthier and memory-resident threat. Recently the Bundlore has been reported to target macOS devices as well as linked to an attack on macOS Catalina users last year. Further investigation of Bundlore samples revealed the use of fileless routines, enabling the execution of payload directly from memory.
Insights: Researchers highlight no significant differences when running the Bundlore samples in macOS Big Sur and macOS Catalina. However, with the default settings of macOS, in which the System Integrity Protection (SIP) and Gatekeeper security features are enabled, the Bundlore samples are blocked and are unable to run.
Similarly, the Bundlore samples were also blocked and unable to run under the default settings of macOS Monterey, Apple’s recently released operating system.
Last month, researchers spotted Bundlore sample containing multiple Safari extension payloads which included two in the new App Extension format. These extensions were adware capable of injecting new advertisements and links, download links, and even redirected users. The samples observed in this campaign stand out from previous Bundlore versions to keep up with the recent updates in macOS and Safari – in particular, Apple’s changes in the format for Safari browser extensions.
It is clear that malware developers are quick to embrace the transition as technology changes and update their payloads scripts accordingly.
Summary: Researchers recently spotted yet another file format being used to distributed malware via spam. Impersonating courier companies, the spam contains a malicious WIM file disguised as an invoice or consignment note as attachments. Developed by Microsoft, WIM is a file-based disk image format to deploy Windows software components and updates and uses a “.wim” extension. The attachments, although having a “.wim.001” file extension may suggest they are the first part of a larger WIM file, have the complete file structure of a WIM file. Researchers highlighted that all the WIM attachments collected are not compressed and have a single file only. All the WIM file samples observed by researchers contained Agent Tesla Remote Access Trojan (RAT), one of the predominant malware.
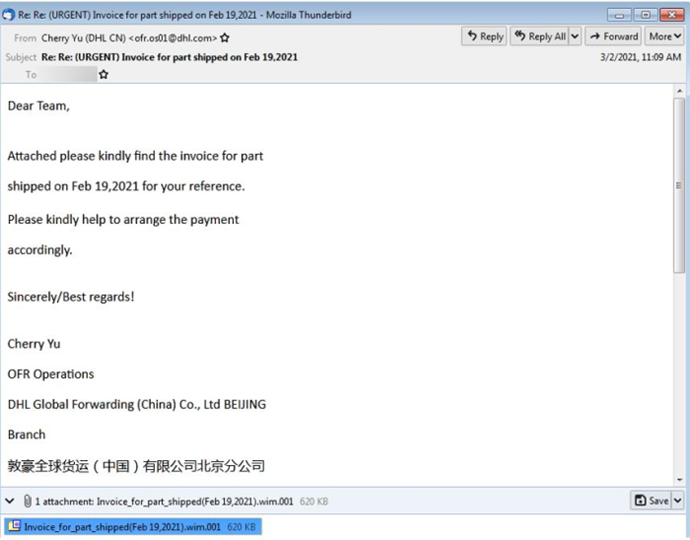
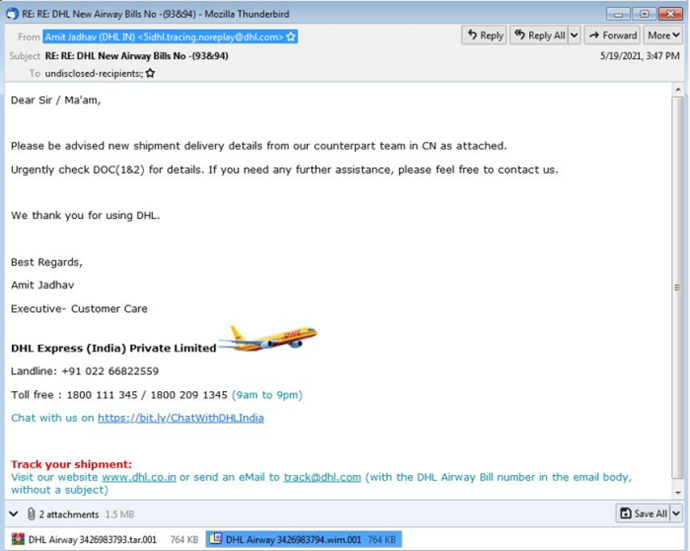
Insights: While attackers encapsulating malware in an unusual archive file format is often one of the common techniques to bypass gateways and security controls, the strategy is a double-edged sword and may pose hurdles to attackers. Using attachments with uncommon file format may allow attackers to bypass certain security controls, it is likely that they may not be acted upon if the targeted system does not have specialized tools and recipients may not make that extra effort to extract the files. The targeted system must recognize the file type or at least have an archiving utility installed which can unpack and process the file format.
On the other hand, the more popular disk image files such as .IMG and .ISO, the WIM files are not supported by Windows built-in ability to mount disk image files. Moreover, the popular archive utilities such as WinRAR and WinZip do not recognize the WIM disk image.
In the regular workflow, it is unusual having an inbound email containing a WIM file is not usual and should raise flags.
Summary: A vulnerability tracked as CVE-2020-3580 being actively exploited in Cisco ASA devices after a (Proof of Concept) PoC exploit was published on Twitter. Initially disclosed and last year the multiple vulnerabilities exist in the web services interface of Cisco ASA and Cisco FTD software that may allow unauthenticated, remote attackers to perform XSS attacks against a user of the web services interface of an affected device. Recently a security research team published a PoC exploit CVE-2020-3580 vulnerability on Twitter. Soon after the release of PoC a cybersecurity firm reported that attackers are exploiting CVE-2020-3580 in the wild. Cisco has also acknowledged that public exploit code exists for this vulnerability and being exploited.
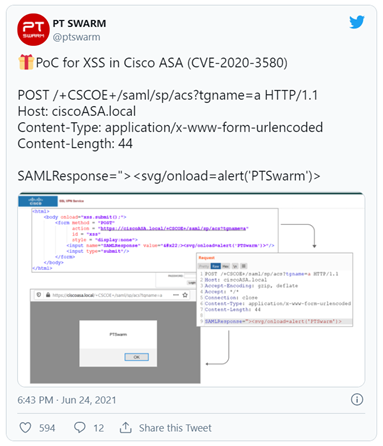
Insights: The vulnerabilities are caused due to insufficient validation of user-supplied input by the web services interface of an affected device. An attacker could leverage these vulnerabilities by persuading a user of the interface to click a maliciously crafted link. Upon successful exploitation, the attacker may execute arbitrary script code in the context of the interface or allow the attacker to access sensitive browser-based information.