



Suspected Threat Actors: Group123/ APT37
• Attack Type: Spearphishing, Social Engineering, Defence Evasion, Obfuscation
• Objective: Unauthorized Access, Malware Implant
• Target Geography: Russia
• Target Technology: Email, Microsoft Office
• Business Impact: Data Loss, Financial Loss
Researchers have disclosed information about an ongoing spearphishing campaign pushing Konni RAT (remote access trojan) to target Russia. The malware has been potentially linked to the North Korean threat actor group APT37. Researchers discovered two documents weaponized with the same malicious macro that was written in the Russian language. The lures leveraged the Russia – Korean Peninsula trade and economic, and meeting of the intergovernmental Russian-Mongolian commission. The campaign used two different UAC (User Account Control) bypass techniques and clever obfuscation. The threat actors cleverly placed the malicious JS (JavaScript) at the end of the document content and did not put it directly into the macro to avoid detection.
The Konni RAT is suspected to be used by APT37 to target its victims. The primary victims have been largely Russian and Korean political organizations. However, the RAT has been observed to target countries including Japan, Vietnam, Nepal, and Mongolia.
The RAT has been used in several campaigns in the past. Even though there are several differences between past campaigns and current reporting the main process of threat actors using a macro weaponized document to download a cab file and deploy the Konni RAT as a service remains the same.
Researchers highlight while the new sample is heavily obfuscated, there are no significant changes and it is similar to its previous version. They believe the threat actor leveraged heavy obfuscation to hinder all the security mechanisms. As a result, the OSINT detection rate was only 3 at the time of analysis, which indicates that the heavy obfuscation to bypass most of the AV products appears to have been successful.
• Attack Type: Rogue Mobile App, Malware Implant, Data Theft
• Target Industry: Social Media
• Target Geography: Global
• Target Technology: WhatsApp
• Business Impact: Data Loss, Financial Loss, Operational Disruption
Researchers discovered a trojan named Triada snook into one of the modified versions of the WhatsApp messenger called FMWhatsapp 16.80.0 along with an advertising Software Development Kit (SDK). This is similar to recent malicious code observed in APKPure where a payload downloader was embedded in the app. When the modified app is launched, the malware gathers unique device identifiers such as Device IDs, Subscriber IDs, MAC addresses, and the name of the app package where they are deployed. The collected information is then sent to a remote server to register the device. The remote server responds by sending a link to a payload which the trojan downloads, decrypts, and launches.
By analyzing files downloaded by FMWhatsapp, researchers identified different types of malware capable of performing the following functions:
• Download and launch other malicious modules.
• Display full-screen ads.
• Download and launch the xHelper trojan installer module and run invisible ads to increase the number of views.
• Signs up the device owner for paid and premium subscriptions.
• Exfiltrate data about the user’s device and mobile operator.
Researchers also highlight that FMWhatsapp victims grant the read permission of their SMS messages which allows attackers to automatically sign the victim up for premium subscriptions, even if a confirmation code is required. It should also be noted that all the further malicious modules loaded by the trojan gain access to victims’ SMS.
Rogue Mobile Apps, a counterfeit app designed to impersonate trusted brands is a constant problem for businesses as well as app stores trying to protect users from such malicious apps. Due to increased digitization and wider reach of social media penetration attackers have been increasingly using Rogue Mobile Apps as an attack vector.
• Attack Type: Vulnerabilities & Exploits
• Target Geography: Global
• Target Technology: Sophos UTM
• Vulnerabilities: CVE-2020-25223 (CVSS Score: 9.8)
• Vulnerability Type: RCE
Tracked as CVE-2020-25223, the vulnerability that affects the web administration console (WebAdmin) of SG UTM devices was fixed last year. Recently, researchers detailed how CVE-2020-25223 can be exploited by a remote, unauthenticated attacker for code execution with root privileges on a Sophos appliance. While Sophos stated it is unaware of any malicious attacks leveraging this vulnerability, researchers highlight it is incredibly easy for an attacker to exploit the vulnerability in a real-world environment.
Observing from a recent client engagement, the researchers’ highlight that not all Sophos customers have patched their devices and an estimated 3,100 systems that appear to expose the WebAdmin interface over the internet.
To exploit CVE-2020-25223, an attacker should send a single HTTP request. If the WebAdmin interface is exposed to the internet, it may be possible for an attacker to exploit the vulnerability directly from the web.
• Attack Type: Data Leak
• Target Industry: Telecommunication Services
• Target Geography: China
• Objective: Data Leak, Financial Gains
• Business Impact: Reputational Damage, Data Loss
CTI observed a potential data leak of China Telecom – a state-owned China Telecommunications Corporation company – advertised for sale in one of the underground forums by an unknown threat actor. From the sample observed, the data the leaked data was suspected to contain personally identifiable information (PII) as well as commercially identifiable information (CII).
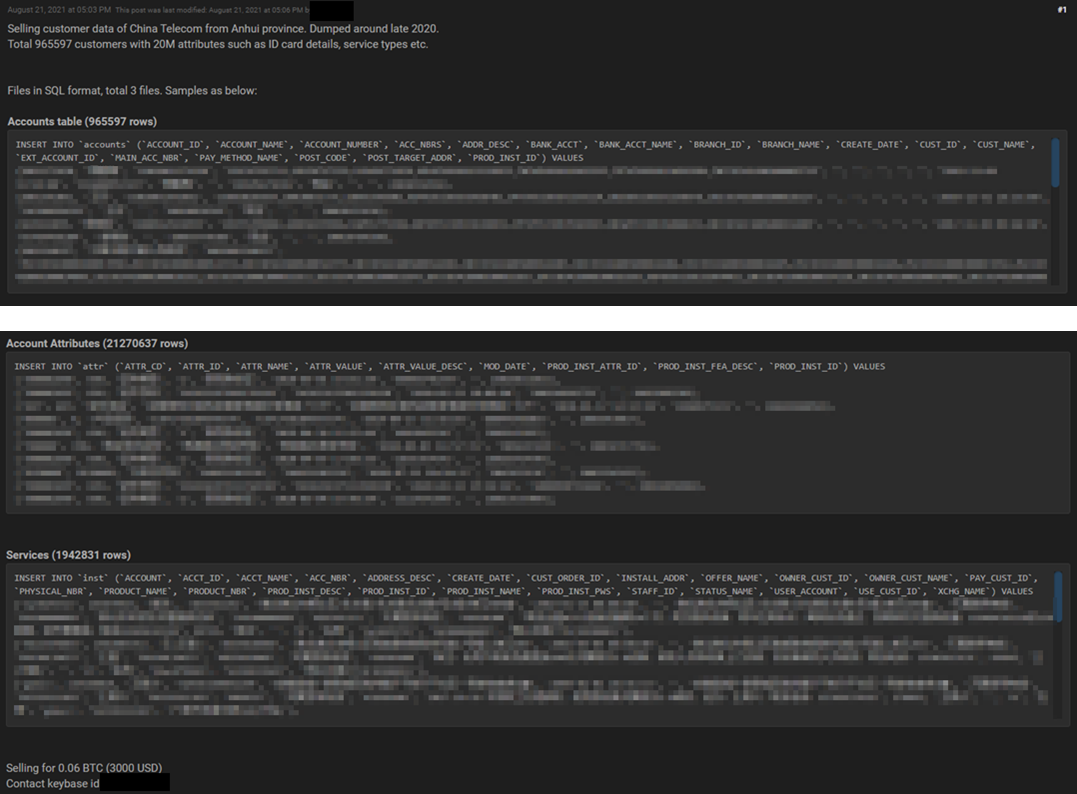
Source: Underground Forums
These incidents serve as an example of the importance of taking proactive measures. Since the consequence of such incidents is irreversible, it is always better to ensure preparedness in advance. Such leaks are often the outcome of opportunistic cybercriminals leveraging compromised credentials, social engineering, human error, or compromise of vulnerable systems.
For an affected organization, these incidents showcase flawed and outdated data security practices. The conversation surrounding a data leak has shifted from the question of “if” to “when” an organization will be compromised by cybercriminals. The fight remains between cybercriminals and the organization’s ability to adapt and protect against new and emerging threats.
One such area of improvement for the organization is inadequate simulation and training exercises that do not mimic real attack scenarios, do not account for behaviors that lead to a compromise, and are not measured against real attacks the organization encounters. Organizations that still rely on the traditional model of security awareness must move to behavioral science to change the habit that could potentially break the attack chain.