



Suspected Threat Actors: Donot Team (aka APT-C-35)
Researchers uncovered activists in Togo being targeted by shadowy cyber-mercenaries who leveraged covert cyberattacks to steal victims’ data to sell to private clients. In a report, researchers exposed links between the Donot Team attacks and a cybersecurity firm based out of India. The anonymous activist’s devices were believed to have targeted from December 2019 to January 2020 – ahead of the 2020 Togolese presidential election. The attack leveraged WhatsApp and email to trick potential victims into installing custom Android spyware. The spyware would allow attackers to access the camera and microphone, collect photos and files stored on the device, and even read encrypted WhatsApp messages. As per the report, the infection attempt failed, and the attacker switched to a different infection chain involving email with a malware-laced Microsoft Word document that would exploit the remote code execution vulnerability (CVE-2017-0199) to drop YTY framework –spyware for Windows machines. The spyware can be used to steal files from infected machines including connected USB drives, record keystrokes, take screenshots, and install additional spyware components.
According to researchers, Donot Team is known to use custom-made spyware, such as YTY for Windows and StealJob for Android. The cybersecurity community has shown links between Donot Team and other threat actors such as the Confucius group and the Operation Hangover attack campaign. It is not clear from publicly available evidence if these campaigns are all linked to the same threat actor, or to several threat actors that may have collaborated at some stage.
Researchers also highlight that hundreds of Togolese numbers of independent journalists and members of the political opposition were listed as potential targets of recently revealed NSO Group’s Pegasus spyware.
The National Security Agency (NSA) issued an advisory last week warning organizations on the use of wildcard TLS certificates and the recently disclosed ALPACA attack. Reported in the summer of this year, ALPACA allows an attacker to confuse web servers that run multiple protocols to respond to encrypted HTTPS requests via unencrypted protocols, such as FTP, IMAP, POP3, and other protocols. As per ALPACA researchers, successful exploitation would allow an attacker to extract session cookies and other private user data or execute arbitrary JavaScript in the context of the vulnerable web server, therefore bypassing TLS and web application security. The NSA advisory highlights the risk associated with broadly scoped wildcard certificates and the ALPACA attack.
The well-known risks from using wildcard certificates are based on the compromise of any single server that uses the certificate or a downgrade exploit of a connection to any single server, putting all other servers that can be represented by that certificate at risk. A malicious cyber actor who gains control of the private key associated with a wildcard certificate will provide them the ability to impersonate any of the sites represented and gain access to valid user credentials and protected information.
In addition to the well-known risks, cybersecurity researchers who disclosed ALPACA attacks have recently shown that using wildcard or other certificates that represent both HTTPS and non-HTTPS servers can lead to exploitable web vulnerabilities that don’t depend on TLS weaknesses or private key compromises.
However, ALPACA attack research highlights the cross-protocol attacks are practical, although the impact is limited and difficult to assess from lab experiments alone. In the real world, cross-protocol attacks will always be situational and target individual users or groups. However, it is also clear that existing countermeasures are ineffective because they do not address all possible attack scenarios.
Researchers disclosed details on three vulnerabilities affecting the IP video-surveillance systems created by Axis Communications. While examining the Axis Companion Recorder – a compact Network Video Recorder (NVR) – used to store IP surveillance video coming from connected cameras, the three bugs identified which later turn out affect all devices running the embedded AXIS OS. The vulnerabilities include:
As per researchers, all the attacks require that a victim visits a specifically crafted webpage or clicks on a malicious link while being logged into the device.
Insights
When it comes to the first vulnerability (CVE-2021-31986: Heap-based Buffer Overflow), researchers also noticed, the requests were not protected against cross-site request forgery (CSRF) attacks, which paves the way for exploitation without authentication. An external remote attacker leveraging successful social-engineering techniques can trigger memory corruption and possibly execute arbitrary code on affected device.
According to a recent report, the first half of 2021 saw 1.5 billion attacks targeting smart devices, with attackers looking to steal data (personal and corporate), mine cryptocurrency, or add infected devices to botnets. That represented a more than 100 percent growth in IoT cyberattacks. Since IoT devices, from smartwatches to smart home gear, have now become an essential part of our everyday lives, cybercriminals are skillfully switching their attention to them.
Summary
As part of routine threat hunting efforts, CYFIRMA researchers have observed a potential data leak from technology conglomerate Cisco. Advertised for sale by an unknown threat actor in one of the underground forums, the dataset contains Cisco employee details which the seller claims to have 136695 lines of record. The threat actor also claims the stolen dataset includes sensitive employee information. The data was gathered from “stealer” logs and was not a result of a compromise.
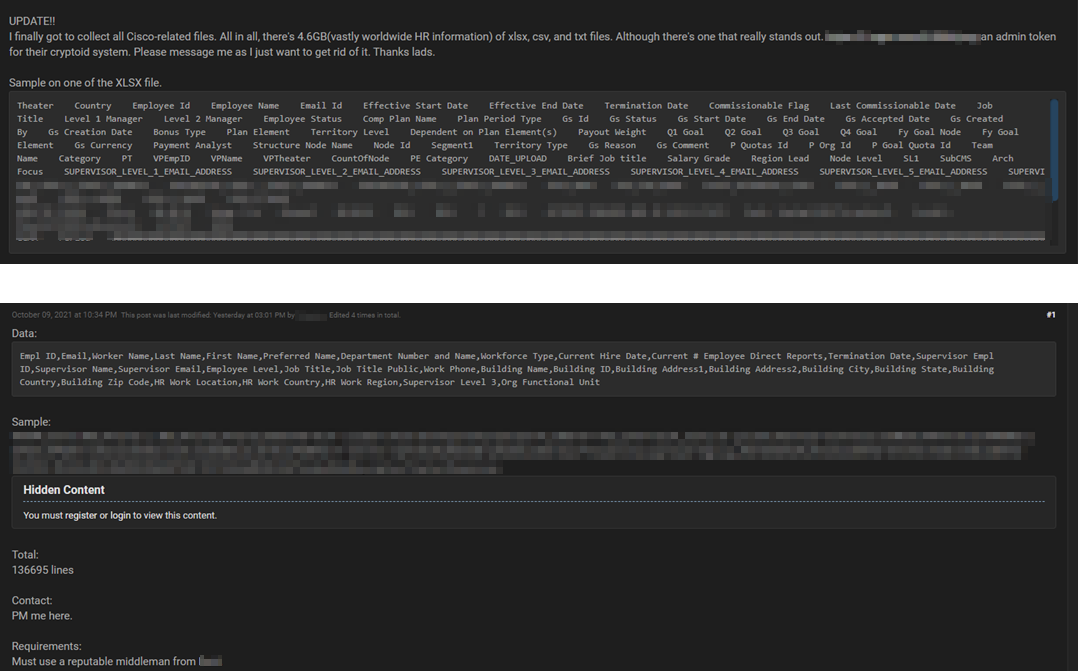
Source: Underground forum