Researchers recently detailed a ransomware attack where the attackers executed a custom Python script on the target’s virtual machine hypervisor, encrypting all the virtual disks and rendering the organization’s VMs offline. As per researchers, this was one of the quickest attacks taking only three hours from the time of initial compromise to the deployment of ransomware. The initial foothold was gained via the TeamViewer account of a user having Domain Administrator credentials. After logging in, the attackers took advantage of a built-in SSH service called the ESXi Shell which was left open by leveraging tools like Advanced IP Scanner and SSH client Bitvise. After three hours, attackers were able to deploy their Python ransomware and encrypt the virtual hard disks. The malware created a map of the drive, inventoried the VM names, and then powered each virtual machine off. Once they were all disabled, full database encryption began. OpenSSL was then weaponized to encrypt them all quickly by issuing a command to a log of each VM’s name on the hypervisor.
Researchers suggest malware running under a Linux-based environment such as ESXi is still uncommon, but it is even less common for IT teams to protect such an environment with endpoint security solutions.
The use of Python in ransomware is also not common, however, the language comes pre-installed in all Linux-based systems which may present a greater opportunity for an attacker to target these systems. In addition, ESXi servers are an attractive target for ransomware groups since they run multiple virtual machines where each machine may be running a business-critical application.
Ransomware groups have known to target ESXi servers including big game ransomware groups such as DarkSide. RasnomExx ransomware group has been observed to specifically target vulnerabilities in VMware ESXi servers to attack virtual hard disks. The vulnerabilities include CVE-2019-5544 and CVE-2020-3992.
A critical Remote Code Execution Vulnerability tracked as CVE-2021-22005 in VMware vCenter Server and Cloud Foundation file upload has been found to be actively exploited in the wild.
Upon analysis of the associated Indicators of Compromise (IOCs), CYFIRMA researchers observed indicators predominantly linked to several malware families such as Cobalt Strike, Dridex, Tofsee Backdoor, Smokeloader malware, and China Chopper.
Multiple threat actors have been seen abusing the vulnerabilities to carry out malicious activities. The threat actors include Emissary Panda, Stone Panda, Leviathan, MISSION2025 (Chinese), Lazarus Group (North Korean), and FIN11 (Russian).
The primary motive behind abusing the vulnerability appears to be theft of sensitive information for financial gains
In a recently published research, seemingly disparate malware campaigns have been linked to Chinese cyber espionage group APT41. The researchers were also able to connect an additional part of their infrastructure that was involved in carrying out a state-sponsored campaign that took advantage of COVID-themed phishing lures to target Indians. The latest research builds upon previous findings of other researchers which detailed a “global intrusion campaign” attributed to APT41 where the group used a malleable command & control profile with at least one of its Cobalt Strike Beacons – a similar malleable command & control profile was uncovered on GitHub. Further analysis led researchers to additional APT41 infrastructure and found overlapping IOCs with two previously documented campaigns linked to APT41. In this research, three additional phishing lures which impersonated Indian government entities (tax legislation) were observed.
Another research published in September 2020 describing a campaign using similar phishing lures – also targeting Indian nationals – was attributed to the Evilnum APT group. However, in current research, despite similar IOCs (or even identical) to those of the phishing lures previously investigated, researchers believe the attack was perpetrated by APT41 and not the Evilnum group.
These lures were part of an execution chain with the objective of loading and executing a Cobalt Strike Beacon on a victim’s network. The phishing lures and attachments also fit tactics that were previously used in infection vectors by APT41. These findings show that the threat group is still regularly conducting new campaigns and that they will likely continue to do so in the future.
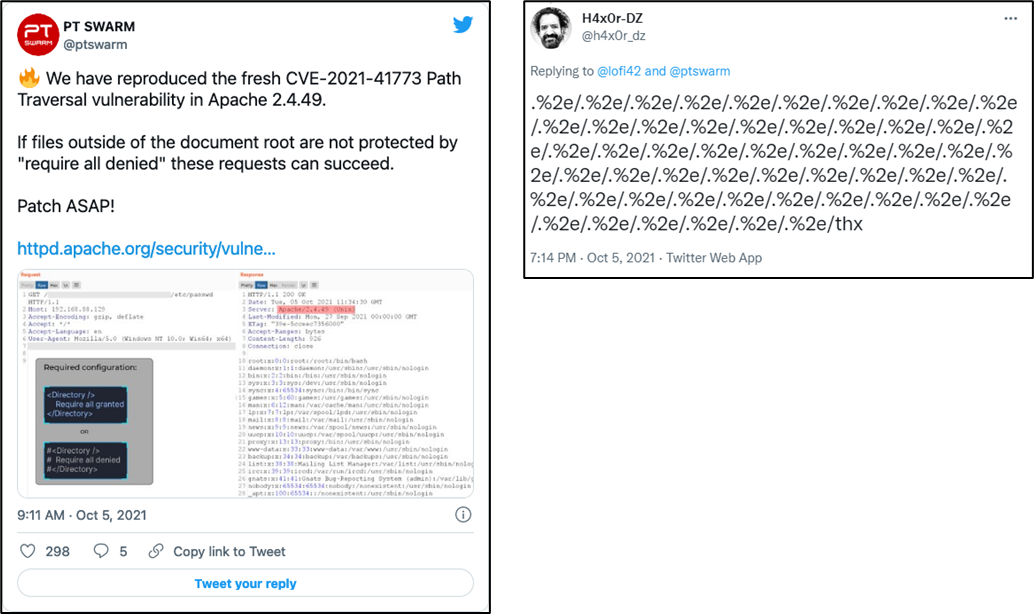
The Apache HTTP Server Project recently released a patch for the path traversal bug tracked as CVE-2021-41773 in Apache HTTP Server. The vulnerability was introduced in version 2.4.49, which was released on September 15 where a change was made to path normalization in version 2.4.49. Notably, this vulnerability only impacts Apache HTTP Server version 2.4.49 with the “require all denied” access control configuration disabled. According to the security advisory, the vulnerability has been exploited in the wild as a zero-day.
Successful exploitation would give a remote attacker access to arbitrary files outside of the document root on the vulnerable web server. According to the advisory, this flaw could also leak “the source of interpreted files like CGI scripts” which may contain sensitive information which attackers can exploit further.
Researchers with help of Shodan identified just under 112,000 Apache HTTP server running versions affected by this vulnerability. However, the number of vulnerable servers is expected to be more since many such servers may be configured to not reveal the version information as a best practice.
Researchers have also published PoC reproducing the vulnerability as well as payload required for successful exploitation on Twitter. It is suspected that working exploit code may become available in the future.