



Suspected Threat Actors: Unknown
Summary:
Researchers recently detailed two years long “DangerousSavanna,” – a financially motivated campaign that has been targeting multiple major financial entities in French-speaking Africa. The campaign’s target included organizations from Ivory Coast, Morocco, Cameroon, Senegal, and Togo. The threat actors leverage spear-phishing emails to distribute and deploy malware.
The initial infection starts with spear-phishing emails sent to multiple employees of the target that are written in French. In the early stages of the campaign, the threat actors leveraged Gmail and Hotmail services to send their phishing emails. However, to increase their credibility, they shifted to lookalike domains in addition to impersonating some of the financial institutions in Africa including Tunisian Foreign bank, Nedbank, and others. Within the last years, researchers also observed the use of spoofing email addresses of a local insurance advisory company that lacked SPF protection in its domain. The phishing emails are laced with malicious attachments including Word documents with macros, documents with remote templates, executables masqueraded PDFs, and other various file types in 2022.
The campaign infected organization with unsophisticated tools, both self-written and openly available tools including Metasploit, PoshC2, DWservice, and AsyncRAT. The researchers also observed the use of additional tools: remote access tool called DWService, Windows Subsystem for Linux (WSL), CrackMapExe, TITAN.exe (open-source anti-EDR tool known as Backstab), POPULAIRE.exe ( a basic keylogger known as LoggerStamp).
Insights:
The LockBit ransomware group has recently released its LockBit 3.0 variant, and the operation also introduced a few tweaks to their dedicated leak site including introducing a bug bounty program. The dedicated leak site now also shows what seems to be the amount of ransom to be paid by the victim alongside the old countdown timer. As time goes by and the timer approaches zero, the amount of ransom also decreases for some of the victims, and if no ransom is paid the exfiltrated data is leaked. The group has also introduced support for Zcash cryptocurrency as a payment option. Researchers indicate that the LockBit 3.0 appears to be inspired by another ransomware known as BlackMatter, (rebrand of DarkSide) by stating “large portions of the code are ripped straight from BlackMatter/Darkside.”
Recently a LockBit public-facing figure announced that the ransomware group is exploring DDoS as a triple extortion tactic on top of encrypting and leaking exfiltrated data. The move comes shortly after the group’s DLS went offline due to a DDoS attack. LockBit accused their latest victim (around that time) – a prominent software company of being responsible for this attack. While this is not something new for ransomware gangs, DDoS as a triple extortion tactic has been used by other ransomware gangs to make victims meet their demands. However, a troublesome factor in play would be the recent hype around a politically motivated DDoS attack that took place a couple of months back and was spearheaded by groups like Killnet. Although tangible outcomes and effects have remained negligible for Killnet, the popularity of DDoS has risen to keep organizations hostage or coerce them to agree by threatening to launch a DDoS attack. With LockBit being one of the prominent players in the ransomware ecosystem, would not only provide a new business avenue for DDoS providers within the cybercriminal underground community but also may incite other ransomware gangs to do so.
Summary:
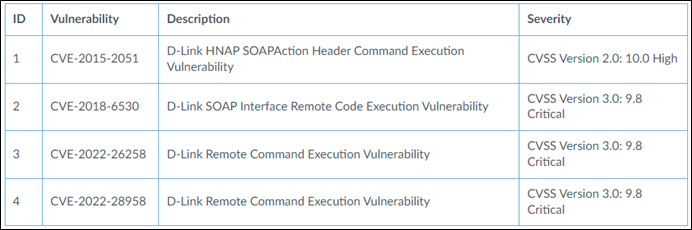
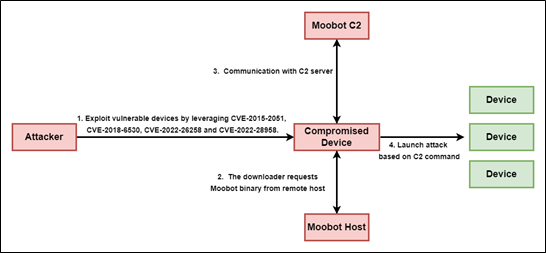
Researchers reveal that attacks involving the exploitation of several vulnerabilities in D-Link devices were observed in early August. When devices are compromised, they will be controlled by attackers and may be utilized in further attacks including DDoS. As per researchers, they observed exploit attempts that targeted these vulnerabilities to spread MooBot – a Mirai variant that targets exposed networking devices running Linux. Once getting hold of the device, the attackers used wget to download and deploy MooBot.
Following are the four known vulnerabilities being exploited in this attack.
Source: Surface Web
Source: Surface Web
Insights:
Summary:
Researchers disclosed a now-patched high severity vulnerability in the TikTok android app that could allow attackers to take over accounts. As per researchers, a simple click on a specially crafted link could allow hijacking of the account without users’ awareness. Upon successful exploitation, attackers are permitted to access and modify users’ TikTok profiles and sensitive information including private videos. The bug could have also facilitated sending messages and uploading videos on behalf of the victim.
Insights: