Published On : 2022-03-27
Facestealer Spyware Infects 100,000+ Google Play Users
- Attack Type: Impersonation, Rogue Mobile App, Malware Implant, Social Engineering, Data Exfiltration, Defence Evasion
- Objective: Data Theft, Payload Delivery
- Target Technology: Android
- Target Industry: Unknown
- Target Geography: Global
- Business Impact: Data Loss
Summary: A popular mobile app called “Craftsart Cartoon Photo Tools” on the Google Play store and third-party application stores – raking up more than 100,000 installs – was found to have embedded an Android trojan called Facestealer. The Android malware relies on social engineering to steal users’ Facebook credentials and was found making connections to a Russian server. Attackers behind this malware have full access to the Facebook account of victims and all data contained. Apart from mimicking the behaviour of a legitimate photo editing app, researchers also observed the application being injected with code that allowed it to slip past Google Play’s security checks.
Insights:
- According to researchers, the trojanized app makes connections to a domain registered in Russia which has been used by various other malicious mobile applications in the past 7 years, that at some points were available on Google Play. This points to the common practice among cybercriminal to repackage mobile apps to ensure presence on Google Play. The practice of repackaging is entirely automated in some cases.
- Threat actors are constantly employing new tricks while also maintaining their old tried-and-tested tactics. One such evergreen tactic is to deploy malicious duplicates of popular Android Apps in the Play store, such as photo editing or VPN service to sneak malware into users’ devices. As such, in January 2022 Facestealer samples were also observed in 15 different malicious applications which included apps for Wallpaper, Proxy, photo editing, VPN, and document scanner.
New Dell BIOS Bugs Affect Millions of Devices
- Attack Type: Vulnerabilities & Exploits, Code Execution
- Target Technology: Dell BIOS
- Vulnerability: CVE-2022-24415(CVSS score: 8.2), CVE-2022-24416(CVSS score: 8.2), CVE-2022-24419(CVSS score: 8.2), CVE-2022-24420(CVSS score: 8.2), and CVE-2022-24421(CVSS score: 8.2)
- Vulnerability Type: Improper Input Validation
Summary: Researchers have reported five new vulnerabilities in Dell BIOS that could result in remote code execution attacks. All the security bugs scored an 8.2 severity rating under CVSS, and the impact is considered high. These bugs affect Dell products including Alienware, Inspiron, Vostro line-ups, and Edge Gateway 3000 Series. The flaws exist due to improper input validation vulnerabilities affecting the System Management Mode (SMM) in the firmware. Notably, the SMM code executes at the highest privilege and remains invisible to the underlying OS, which makes it ripe for abuse to deploy persistent firmware implants.
Insights:
- Researchers who identified the bugs state that the active exploitation of all the discovered vulnerabilities cannot be detected by firmware integrity monitoring systems due to limitations of the Trusted Platform Module (TPM) measurement. The remote device health attestation solutions will not detect the affected systems due to the design limitations in the visibility of the firmware runtime.
- A couple of months ago, 16 high-impact vulnerabilities in HP devices and 23 other additional vulnerabilities affecting major enterprise vendors have been reported. The ongoing discovery of such vulnerabilities is described by the researchers as “repeated failures” due to a lack of input sanitization and insecure coding practices.
- These failures are a direct result of the complex codebase and inadequate security consideration for legacy components that are still widely deployed.
Suspected DarkHotel APT Activity Update
- Attack Type: Spear-Phishing, Malware Implant, Persistence, Data Exfiltration
- Objective: Unauthorized Access, Payload Delivery, Data Theft
- Target Technology: Email, Microsoft Excel
- Target Industry: Hotels, Restaurants & Leisure/ Consumer Services
- Target Geography: China
- Business Impact: Data Loss, Financial Loss
Summary: Researchers recently disclosed detail on a first-stage malicious campaign targeting luxury hotels in Macao, China which has been active since at least the latter half of November 2021.
The attacker used a spear-phishing email aimed at the hotel’s management staff. The spear-phishing email used in this campaign contained an Excel sheet attachment that tricked potential victims to enable malicious macros. These macros enabled several mechanisms including macros creating a scheduled task, data listing, and data exfiltration, enabling communication with the Command-&-Control(C2) server to exfiltrate data. The macros used the known LOLBAS (Living Off the Land Binaries and Scripts) technique to perform PowerShell command lines as trusted scripts.
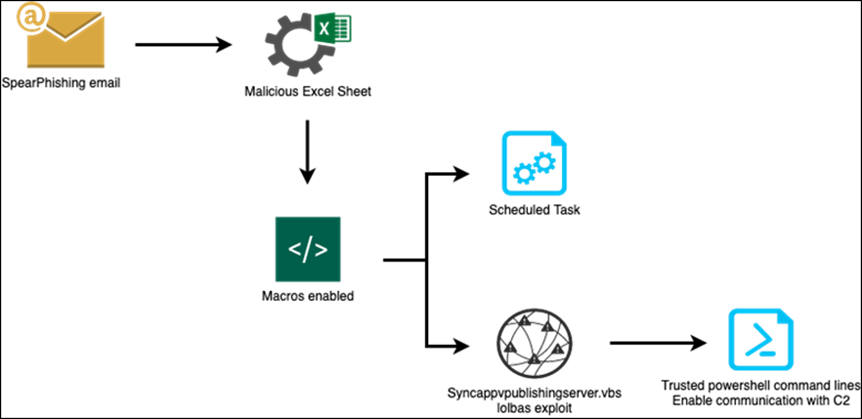
Source: Surface Web
This campaign was attributed to DarkHotel APT group with moderate confidence by researchers based on the below findings:
- The threat actor used an IP previously attributed to DarkHotel C2 activity by researchers.
- The targeted industry and geography fit within DarkHotel’s target profile.
- The C2 panel presents known development patterns attributed to DarkHotel APT.
Insights:
- To avoid attribution, most APT groups move on to different infrastructure once their TTPs becomes public. Interestingly, however, in this case, a previously attributed IP address remained active for quite some time even after being publicly exposed. In addition, the IP address was also part of other malicious activities not related to this campaign.
- The DarkHotel APT group got its name by targeting hotels through spear-phishing and the current campaign demonstrates that the hospitality industry is still a desirable target. Researchers suspect that current activity was to lay a foundation for future campaigns. For instance, multiple scheduled conferences would have been of threat actor’ interest.
Italy’s Data Privacy Watchdog Investigates How Kaspersky Manages Italian Users’ Data
Italy’s data privacy watchdog has launched an investigation into potential risks associated with the use of Kaspersky’s antivirus solutions. The Italian authority aims at validating how the Russian firm processes the data of Italian users and whether it exfiltrates the collected information outside the EU, including Russia.
The watchdog has asked Kaspersky Lab to specify the number and type of Italian customers, including detailed information on the way the company’s solutions process Italian users’ personal data. In addition, the Agency has also requested Kaspersky Lab to cast light on requests made by other nation’s government authorities related to Italian entities.
The announcement follows the recommendation issued by Italy’s cybersecurity agency to reduce the use of Russian software warning of a potential “technological risk” following the ongoing invasion of Ukraine.
Recently Germany’s cybersecurity agency recommended consumers uninstall Kaspersky anti-virus software. The Agency warns that the cybersecurity firm could be associated with hacking activities during the ongoing Russian invasion of Ukraine.
bChannels Ltd Impacted by Conti Ransomware
- Attack Type: Ransomware, Vulnerabilities & Exploits
- Target Industry: Media
- Target Geography: United States
- Ransomware: Conti
- Objective: Data Exfiltration, Financial Gains
- Business Impact: Data Leak, Financial Loss, Operational Disruption
Summary: CTI observed bChannels Ltd (www.bchannels.com) – a global technology marketing agency – being impacted by the Conti ransomware. The ransomware group has started to publish sample evidence on their dedicated leak site claiming an attack. In the event of non-compliance to their ransom demand, the ransomware group is likely to publish all exfiltrated data on their dedicated leak site for anyone to download.
The following screenshots were observed published on the dark web:
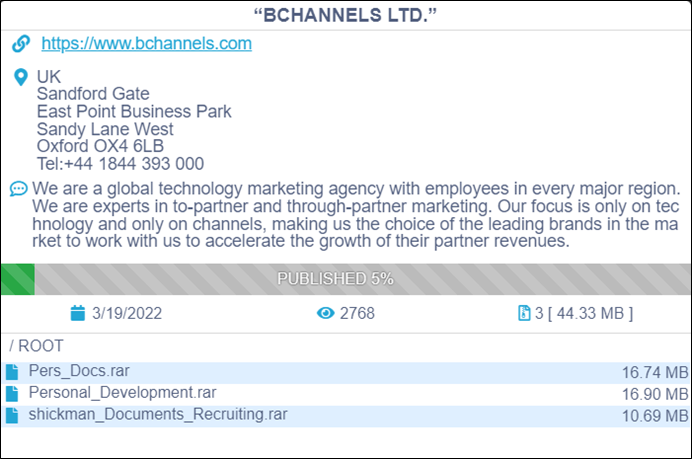
Source: Dark Web
Insights:
Researchers have associated vulnerabilities being exploited by the Conti ransomware operators which include:
-
- CVE-2020-0796 affecting Microsoft products, and CVE-2018-13374 & CVE-2018-13379 existing in Fortinet’s FortiOS.
- CVE-2020-0796 (CVSS Score: 10) a critical RCE/ PE vulnerability – also goes by the names CoronaBlue and SMBGhost – is one of the top exploited vulnerabilities of 2020.
- CVE-2018-13379 (CVSS Score: 9.8) is a critical RCE vulnerability that allows for unauthenticated attacks.
- CVE-2018-13374 (CVSS Score: 8.8) is a high-rated vulnerability used to compromise web applications.
- Researchers also believe that the Russian APT group Wizard Spider uses the Conti ransomware in its attacks.
- The stolen data is first made available for sale to potential buyers on Conti’s dedicated leak site. As the ransom payment gets delayed the ransomware operators resort to publishing parts of the data as time goes on. Ultimately, if no ransom is paid and the data is not purchased, the data is released to the public for free for anyone to download.
- Recently, the Conti ransomware group appeared to alter its ransomware business plan by selling access to the infiltrated victim’s network. Researchers have pointed out that many of the ransomware groups are finding it hard to maintain their DLS and some are leveraging public file sharing services such mega[.]nz. However, hosting leaked data on the clear web has its downsides and such content gets taken down in a couple of days. In addition, due to Tor’s architecture, the download speed is considerably slower, and the datasets are often large. The DLS also leaves the ransomware group vulnerable to attacks. For instance, the REvil representatives recently revealed that their data-leak site was “hijacked”.
- It is suspected that these difficulties are discouraging ransomware groups to continue the use of DLS style of ransomware operations, and we may see more creative solutions to overcome these challenges.
- CYFIRMA’s analysis of recent Conti Leaks reveals that the Conti gang operates much like an organization within the cybercrime ecosystem. It includes outsourcing their initial access requirements, HR operations, performance review, and physical offices. The gang also uses extensive business intelligence to understand the financials of potential victim organizations to ensure high returns for their efforts. The gang also invests in major security solutions, not just for their own defense, but also to test malware and TTPs to remain one step ahead of defenders.





