



Summary:
A joint advisory from multiple US government agencies including the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) warns that certain Advanced Persistent Threat (APT) groups have exhibited the capability to gain full system access to multiple ICS/SCADA devices including:
The APT groups have developed custom tools designed to target ICS/SCADA devices which allow them to scan, compromise, and control affected devices once they have established initial access to the Operational Technology (OT) environment. They are also capable of compromising Windows-based engineering systems which may be IT or OT environments by exploiting CVE-2020-15368 which affects the ASRocksigned motherboard driver.
Insights:
The U.S. government accused North Korea-linked APT Lazarus of the recent USD 600 million Ronin Validator cyber heist. The U.S. Treasury stated in a notice the sanctions against the Ethereum address used by the APT to receive the stolen funds.
On March 23rd, threat actors allegedly stole almost USD 625 million in Ethereum and USDC (a U.S. dollar pegged stablecoin) tokens from Axie Infinity’s Ronin network bridge. The cyber heist was discovered after a user was unable to withdraw 5,000 ether.
The Ronin Network is an Ethereum-linked sidechain managed for the blockchain game Axie Infinity. The attackers have stolen approximately 173,600 ether and 25.5 million USDC.
Axie Infinity revealed the security breach through the official Twitter and Discord accounts, and by Ronin Network. The amount of stolen funds makes this attack the largest crypto hack in history, passing the USD 611 million hack of the DeFi protocol Poly Network in August 2021.
Axie Infinity launched an investigation into the incident and discovered that cyber thieves have already managed to launder about 20% of the stolen funds. Over the last years, North Korea- linked APT groups have conducted multiple attacks against cryptocurrency exchanges evolving their TTPs.
Russia-linked Gamaredon APT group (a.k.a. Armageddon, Primitive Bear, and ACTINIUM) continues to target Ukraine and it is using new variants of the custom Pterodo backdoor (aka Pteranodon).
Gamaredon has been launching cyber-espionage campaigns in Ukraine since at least 2014. Researchers revealed that the APT group is using at least four variants of the custom Pteredo backdoor in recent attacks.
Pteranodon is a multistage backdoor created to collect sensitive information or maintain access to compromised machines. It is distributed through spear-phishing messages with weaponized office documents that appear to be designed to lure targets.
Recent attacks attributed to Gamaredon were indicated by the deployment of multiple malware payloads on the targeted systems. The payloads delivered by the threat actors are usually different variants of the Backdoor.Pterodo that have been designed to perform similar tasks. The researchers pointed out that each variant will communicate with a different Command-&-Control (C&C) server.
Summary:
As per researchers, Ukraine-related scams that started as fake donation website, fake Red Cross portals, phishing pagesan also be found on social media. Particularly, on Twitter researchers have spotted scammers who are setting up imitation accounts of users asking for donations. One such request came from a well-known Twitter handle @Xenta777 asking for donations related to certain military equipment. The scammer set up an imitation account with the Twitter handle @Xenta7777 and replied to users who were willing to help @Xenta777 with his own PayPal address.
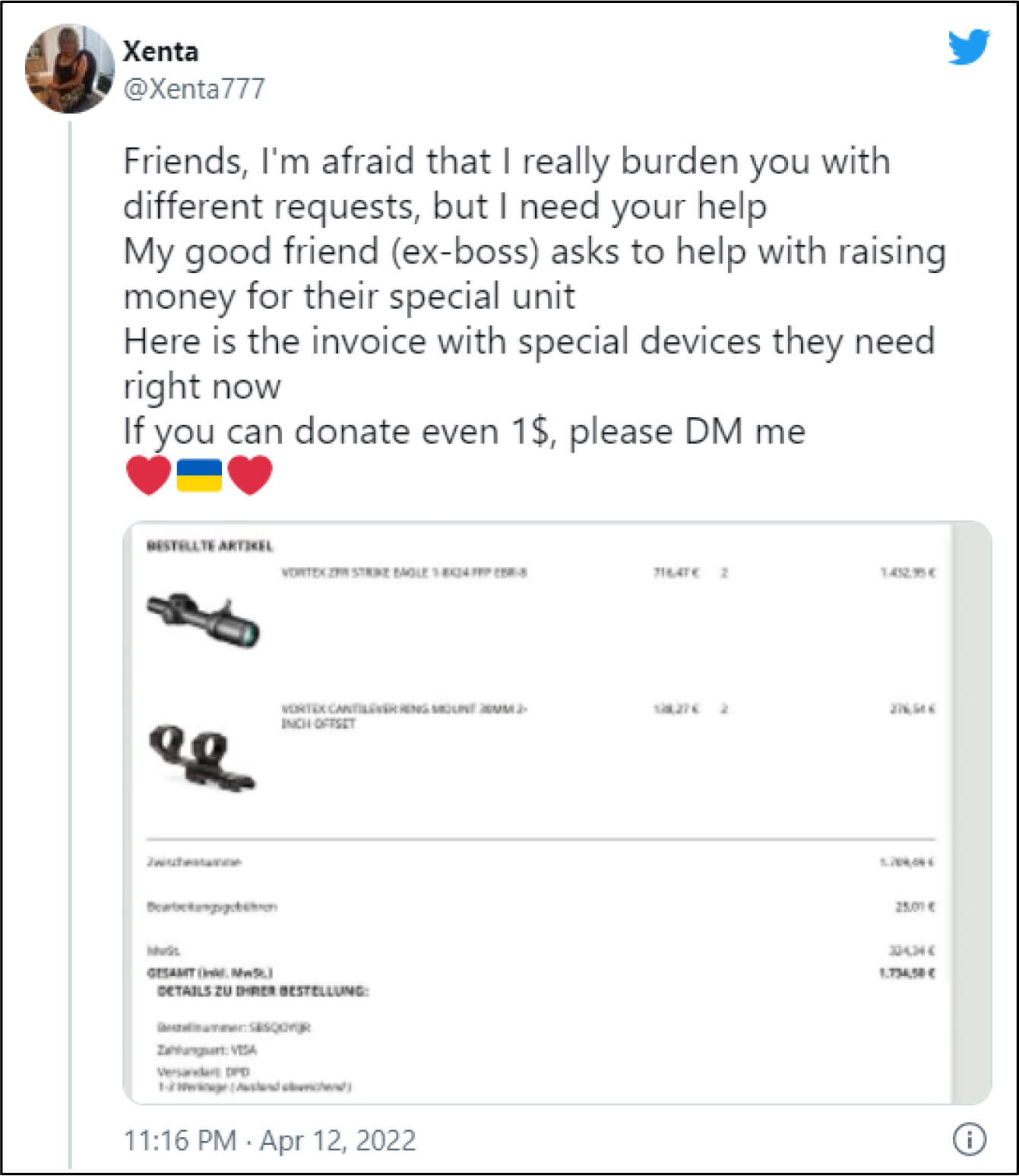
Source: Surface Web
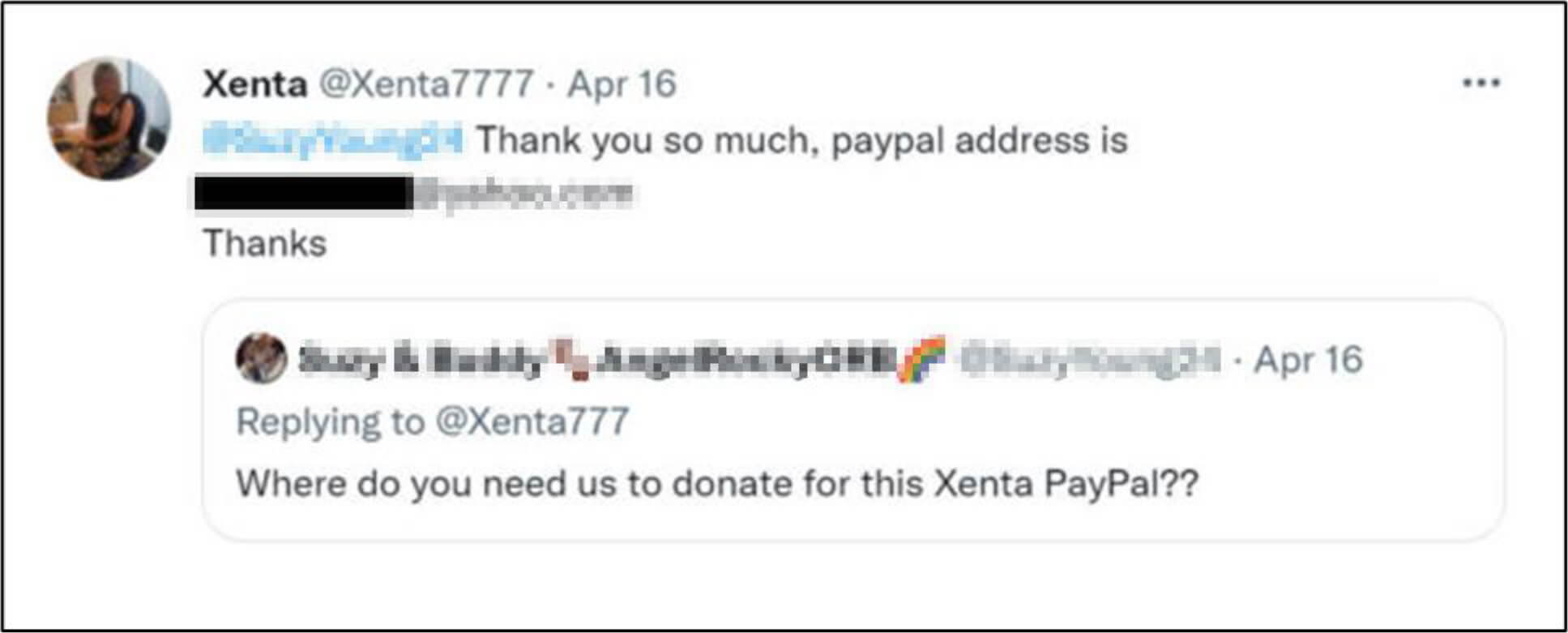
Source: Surface Web
Insights:
Since the Russian invasion of Ukraine, scammers are finding ways to take advantage of the opportunity. Given the situation in Ukraine, there are some legitimate users using social media to ask for donations, and medical assistance to aid whatever has been required. Some of these users become well-known with their tweets seeking help while others are already well-known Twitter handles. In the past scammers used a similar trick to direct victims to a phishing page. The current tactic is quite simple and can yield easy wins for the scammer.
Summary:
The zero-day vulnerability tracked as CVE-2022-1364 is a high severity bug that was reported by a researcher from Google’s Threat Analysis Group. The bug was related to a type confusion in Chrome’s V8 JavaScript engine. While the bug has received a patch, Google has also stated that an exploit exists in the wild. In addition, this vulnerability was also listed on CISA’s Known Exploited Vulnerabilities (KEV) Catalog last Friday.
Insights:
It should be noted that CISA’s KEV Catalog is an excellent resource for organizations to keep up with trending vulnerabilities among attackers. The initiative aims to catalog the most important vulnerabilities that have been previously exploited by attackers and pose a serious risk. Organizations must monitor and prioritize these vulnerabilities listed in this catalog.