



Cybersecurity researchers have released details on the MISSION2025 threat actor group – state-sponsored cyber espionage originating from China – compromising at least six US government organizations including other organizations, sometimes repeatedly during May 2021 and February 2022.
During the timeframe, researchers observed deliberate campaigns targeting the US state government. They used exploitation of vulnerable internet-facing web applications, including using a zero-day vulnerability in the USAHerds application (CVE-2021-44207) and the infamous zero-day vulnerability in Log4j (CVE-2021-44228). The threat actor group was also observed exploiting SQL injection and directory traversal vulnerabilities.
While the motive behind remains to be unknown, through investigation researchers have learned about a variety of new techniques, malware variants, evasion methods, and capabilities leveraged by MISSION2025.
The threat actor group exploited deserialization vulnerability in a proprietary web application through deserialized JScript webshell exploit, USAHerds (CVE-2021-44207) Zero-Day vulnerability, Log4j (CVE-2021-44228).
After securing initial access to an internet-facing server, the group carried out active reconnaissance, credential harvesting, and exfiltration. Researchers commonly observed deployment of ConfuserEx obfuscated BADPOTATO binary, Mimikatz, DUSTPAN (consistent with StealthVector) during the reconnaissance stage. The group also leveraged anti-analysis techniques through DEADEYE launcher, LOWKEY backdoor, DEADEYE.EMBED and VMProtect. To remain persistent Windows version of the KEYPLUG backdoor, LOWKEY.PASSIVE, DEADEYE.APPEND malware.
MISSION2025’s activity against US government entities holds significant new capabilities including new attack vectors, post-exploitation tools, and techniques. The threat actor groups can quickly adapt to their initial access techniques by using an entirely different vector to re-compromise an environment or rapidly leverage a fresh vulnerability. The group is also willing and capable of retooling and deploying capabilities by incorporating new attack vectors as opposed to holding onto them for future use.
A new Wiper malware dubbed RURansom by its developer has been spotted by researchers. The MalwareHunterTeam caught the variant on 1st March and several other samples of this malware have been found and analyzed by a security vendor. The motive and target of this malware are pretty apparent from the ransom note file observed by the researchers during the analysis.
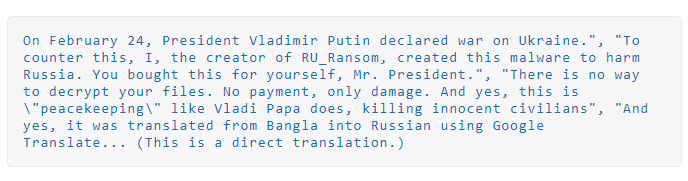
Source: Surface Web
Between February 26 and March 2, 2022, different versions of this malware have been spotted by researchers. The malware is written in .NET programming language and spreads like a worm by copying to all removable disks and mapped network shares itself under the file name “Россия-Украина_Война-Обновление.doc.exe”. which translates to “Russia-Ukraine_War-Update.doc.exe”. After spreading itself the malware applies encryption to all file extensions except .bak files.
A “ransom” note (more accurately “wiper note”) file under the name “Полномасштабное_кибервторжение.txt” – translated as “Full-blown_cyber-invasion.txt” – is then dropped into each directory.
Due to its name “RURansom”, the malware was originally suspected to be a type of ransomware. However, despite its name, the analysis by researchers revealed it to be a type of wiper and not ransomware. The malware causes irreversible destruction of encrypted data from victim systems.
Additionally, as per the contents of the “wiper note” dropped by the malware, the author does not appear to have any financial motive and is largely driven by the ongoing Russian invasion of Ukraine.
Among the several versions spotted by researchers, some of the versions of this malware run IP check to validate if the malware is launched in Russia, in case otherwise – the malware stops its execution. This shows a conscious effort to infect the system only located in Russia.
With the ongoing Russia-Ukraine conflict, even malware authors have been observed to be taking sides and displaying their loyalties. While the recent leaks and incidents from Conti and TrickBot is part of the Russian effort to deploy destructive wiper targeting Ukrainian organizations, the RURansom is seeking Russian targets – reflecting the current mood of the escalation between the two nations.
CTI suspects the RURansom is just another attempt by an individual or group among many cyberattacks exchanges caused by the conflict that aim to support their position. While there has not been any victim reported so far, the malware itself is under development by researchers. The individual or group behind this malware is expected to continue updating their malware to deal some form of damage to Russian organizations.
A cybersecurity researcher has recently disclosed the details of a Linux vulnerability that allows an attacker to overwrite data in arbitrary read-only files. The vulnerability tracked as CVE-2022-0847 affects Linux Kernel 5.8 and later versions but was fixed in Linux 5.16.11, 5.15.25, and 5.10.102. According to the security researcher, the vulnerability is like CVE-2016-5195 “Dirty Cow” but easier to exploit. A proof-of-concept exploit has also been released publicly.
As per the researcher, the vulnerability leads to privilege escalation because unprivileged processes can inject code into root processes.
To make this vulnerability more interesting, it not only works without write permissions, but it also works with immutable files, on read-only btrfs snapshots, and read-only mounts (including CD-ROM mounts). That is because the page cache is always writable (by the kernel) and writing to a pipe never checks any permissions.