Malware, in particular, njRAT – a .NET Remote Access Trojan with several in-built evading techniques, FormBook – information stealer malware, and NanoCore – another .NET featured Remote Access Trojan providing highly customized plug-ins for a tailored attack have been observed targeting organizations for multiple objectives including data encryption, data exfiltration, and payload delivery.
Most of these malware use phishing as their initial attack vector. Apart from these attack methods, exploitation of vulnerabilities and defence evasion tactics have been observed.
Insights: CYFIRMA – as part of its cyber-threat predictions for 2021 – had highlighted that threat actors would potentially recycle and repurpose existing malware to carry out cyber-attacks. The commodity malware such as njRAT, Formbook, NanoCore, and Avaddon Ransomware have been leveraged effectively in the past and will continue to be used by threat actors looking for easily available and affordable malware samples.
Summary: In recent development, the active RedEcho – one of many Chinese government-sponsored cyber-espionage threat actor groups has taken down its attack infrastructure after having its operations exposed at the end of February 2021 by security researchers. The group was linked to a campaign that targeted India’s power grid and critical infrastructure entities. The web domains used to control the ShadowPad malware identified in targeted intrusion activity against Indian power grid now appear parked.
Insights: RedEcho has strong infrastructure and victimology overlaps with Chinese groups APT41/ Barium and Tonto Team, while ShadowPad is used by at least 5 distinct Chinese groups. The earliest signs of RedEcho attacks date back to early 2020, but operations gained significant momentum after a May 2020 border dispute between India and China. It is likely that public disclosure of RedEcho’s Indian operations in February 2021 has put the targeted entities in defensive mode. Further, being a cyber espionage group, stealth tactics are of utmost importance to be efficient and threat actor groups often react to public disclosure by moving infrastructure to new servers.
Insights: On March 25th, it was observed that the Anonymous hacking group (a decentralized international activist/hacktivist collective/movement which started in the early 2000s) has identified organizations and entities who are known supporters of the Myanmar military coup as potential targets. The campaign is codenamed ‘Operation Myanmar’.
On March 28th, the group posted an updated link with details of a DDoS program and TangoDOWN update file. The bin site also included a list of targets including many organizations based in Japan.
CYFIRMA researchers are monitoring the situation and will update as new developments unfold.
Insights: Several members of the Bundestag (German federal parliament) and Landtag (German legislative bodies) have been the target of cyberattacks in the past few days – presumably from Russia. In today’s scenario, parliamentarians need to be present on social media such as Facebook, Twitter and Instagram, and cyber attackers may have compromised their login details on these platforms. The administration of the German Bundestag was promptly informed. The attack has also resulted in Parliament’s consideration for an overhaul of their IT system.
Insights: Australia’s leading cybersecurity agency is investigating a suspected breach of the country’s parliamentary email system as well as the Australian media company cyber-attack. Internet-facing databases are easy pickings for threat actors as well as amateur cybercriminals. In recent times, organizations that have not protected their critical databases have suffered attacks from ransomware campaigns. Threat actors are using automated scripts to continuously scan for exposed databases, probing for vulnerabilities such as unsecured ports, software vulnerability, inadequate access controls, lack of encryption, or even non-password protected databases.
Insights: The yet-to-release US Government executive order would require software vendors to disclose security breaches to the government and its customers. Software vendors would be requested to work together with specialized government agencies, such as the FBI and CISA when investigating cyber-incidents. Likely a reaction to the recent SolarWinds attacks, the proposed order is expected to impact the relationship between major software vendors and government agencies. The order is expected to push federal agencies to improve their security posture through the adoption of multi-factor authentication and data encryption within their environments.
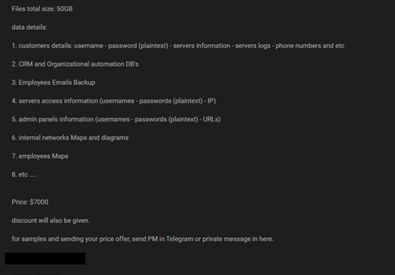
Summary: EXEDY Corporation, a Japanese manufacturer of automobiles, industrial vehicles, and construction machinery components is suspected to have been targeted by Avaddon ransomware operators. The exfiltrated data may include confidential and business-critical data such as financial documents, company financial statements, bank transaction details, contracts, employee details, employee credentials as well as personal information of customers and employees. The threat actor also indicated his intention to perform DDoS attack until a response is received. Threat actors are observed targeting third parties (suppliers, vendors, and partners) to make inroads into the primary target’s infrastructure. The compromised systems and stolen information may also be used for extortion and tailored attacks on the organization. Entities affiliated with EXEDY Corporation via supply chains may also be exposed and run the risk of suffering similar attacks.
The following screenshots were published in one of the dark web forums:

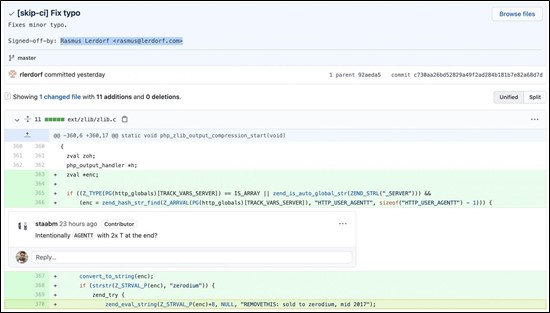
Summary: Unidentified threat actors, posing as PHP developers and maintainers – Rasmus Lerdorf and Nikita Popov – attempted to compromise the PHP codebase. According to researchers the root cause of the incident is currently unclear with suspicion towards the compromise of git.php.net server rather than the compromise of an individual git account. The malicious first breach was identified and action taken within a couple of hours. As a precaution, the PHP maintainers have discontinued the use of this server.
The screenshot here shows the malicious update where hackers masqueraded as Rasmus Lerdorf. The hackers were planting a remote code execution backdoor.
Insights: Last year, security experts highlighted that attacks surged by 430% targeting open-source components and with GitHub reporting 26 open projects on its platform being compromised in a massive supply chain attack. As part of CYFIRMA’s 2021 Cybersecurity Predictions, as goods and services are now flowing through digital systems, a compromise at any stage can have a devastating impact on the organization. Cyberattacks will hit upstream and downstream of supply chains.
Summary: Recently an external researcher had discovered two vulnerabilities – tracked as CVE-2020-27170 and CVE-2020-27171 – which impact all Linux kernels prior to 5.11.8. While CVE-2020-27170 can be abused to reveal content from any location within the kernel memory, CVE-2020-27171 can be used to retrieve data from a 4GB range of kernel memory. The researcher highlighted that the new vulnerabilities may be used to get around Spectre countermeasures in Linux by taking advantage of the kernel’s support for extended Berkeley Packet Filters (eBPF) to extract the contents of the kernel memory.
Insights: Google published a JavaScript exploit to demonstrate the effectiveness of using the Spectre vulnerability in browsers to access information in memory. This Proof of Concept (PoC) exploit is reportedly able to operate with a variety of architectures, operating systems, and hardware generations. It proves in practice that the protective mechanisms added by developers to their browsers (for example, site isolation, Cross-Origin, Cross-Origin Read Blocking, and so on) do not work.
As part of CYFIRMA’s Cybersecurity predictions for 2021, we have predicted that risk associated with perimeter defense, passwords and authentication, data storage, protection, back-up, and retention will present more challenges to cybersecurity teams. Especially, cybercriminals will adopt new attack methods that exploit the vulnerabilities presented by the ever-increasing adoption of digital technologies.
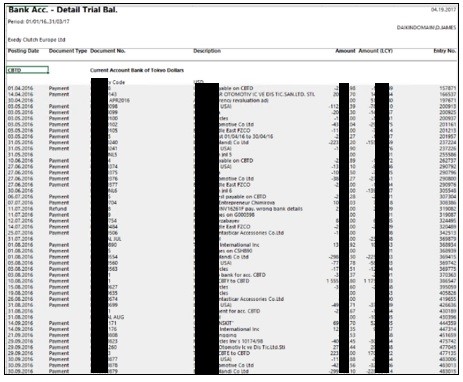
Summary: A threat actor appears to have secured access to critical data (from 2018-2021) of one of the major Indian telecommunication giants. The observed data leak in one of the underground forums includes confidential information such as customer details (username, password, phone number), employee email backup as well as critical information about the infrastructure of impacted organization such as credentials for server access, admin panels, internal networks details, and more.
The following screenshot was taken from the underground forums:
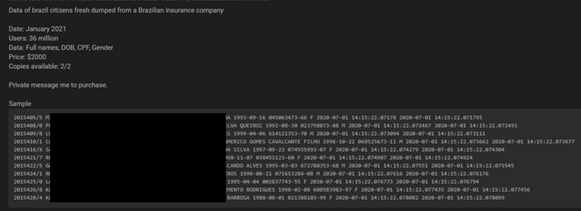
Summary: Around 36 Million user records pertaining to Brazilian citizens were observed to be put up for sale in the underground forums. The leaked data includes details such as full name, date of birth, CPF, and gender. The threat actor appears to have secured access to the information around January 2021.
The following screenshot was taken from the underground forums: