



Summary: Over the past 7 days, malware and phishing attacks continued to be the top attack methods leveraged by hackers.
Malware, in particular, njRAT – a .NET Remote Access Trojan with several in-built evasion techniques, Formbook – an infostealer trojan sold as PHP control panel as part of Malware-as-a-Service (MaaS) offerings, and Remcos – sophisticated remote access Trojan (RAT), have been observed targeting organizations for multiple objectives including data encryption, data exfiltration, and payload delivery.
Most of the malware use phishing, and social engineering techniques as their initial attack vector. Apart from these attack methods, exploitation of vulnerabilities and defence evasion tactics have also been observed.
Insights: Threat actors are recycling and repurposing existing malware to carry out cyberattacks. Commodity malware such as njRAT, Formbook and Remcos has been leveraged effectively in the past and will continue to be used by threat actors looking for easily available and affordable malware samples.
Ransomware operators such as DopplePaymer has been observed using “Ransom DDoS attacks (RDDoS)” to extract payment from their victims. This tactic is in addition to the “name-and-shame” threats which have been used by many ransomware operators. Ransomware attacks are likely to increase in the coming months.
Summary: APT-C-23, active since at least 2012, is believed to be part of a larger group known as Molerats and are mostly located in Palestine. The group generally relies on social engineering techniques namely spear phishing, impersonated website of new organization, and ensnare victims through conversations to install their malware. There are several different families of malware but most start with a self-extracting archive that executes H-Worm backdoor. Researchers reviewed a server that was previously identified as serving malware for targeted attacks. The toolset includes malware used for espionage against political opponents, tools to identify vulnerable routers, a voice-changing application, custom tooling to use compromised email accounts to send phishing emails, and phishing code for webmail logins.
Insights: The APT-C-23 group is known to have used both Windows and Android components in its operations, with the Android components first described in 2017 under the name “Two-tailed Scorpion.” Researchers have attributed the below campaign to the groups:
The group has used a fake android app store to distribute its malware. The malware was hidden in apps posing as AndroidUpdate, Threema and Telegram. The latter two of these lures also downloaded the impersonated apps with full functionality along with the malware.
Impersonation (that involves altering voice) is a prevalent and evolving issue that cannot be mitigated using traditional, rule-based measures. The technique of leveraging voice changing software could easily lure users who are not cautious about minute indicators that hint at vishing/phishing attacks.
Chinese cyber espionage group Cycldek has demonstrated advanced attack techniques in a recent malicious campaign against government and military organizations in Vietnam. Over the past year, it is noticed that many of Chinese-speaking groups are investing more resources into their campaigns and sharpening their technical capabilities. In recent campaigns, they have added many more layers of obfuscation and significantly complicated reverse engineering. This indicates that these groups may be looking at expanding their activities. In their latest campaign, dozens of computers were affected of which 80% of the computers were in Vietnam, and some were in Central Asia as well as Thailand. Most of these computers belonged to the government or military units, while some were related to health, diplomacy, education, or politics.
The campaign may seem like a local threat, but the techniques can be propagated to other countries easily.
European Commission (EC) has confirmed that a cyberattack had affected several European (EU) institutions, bodies, and agencies’ IT infrastructure. The investigation is ongoing and EC representatives are working with Computer Emergency Response Team (CERT-EU) and the affected IT solution provider.
Internet-facing servers/databases are easy pickings for threat actors and amateur cybercriminals. Threat actors are using automated scripts to continuously scan for exposed databases, probing for vulnerabilities such as unsecured ports, software vulnerability, inadequate access controls, lack of encryption, or even non-password protected databases.
Summary: A US-based firm, Diversified Plastics Corporation, was hit by DopplePaymer ransomware. The operator has published the exfiltrated data in a dark web forum which may include business-critical or sensitive data belonging to the organization. Threat actors are observed targeting less secured systems of suppliers, vendors, and partners to make inroads into the primary target’s infrastructure. Further, compromised systems and stolen information may also be used for extortion and tailored attacks on the organization. Organizations affiliated with Diversified Plastics Corporation via supply chains may also be exposed and subject to similar incidents.
The following screenshots were observed published in one of the dark web forums:
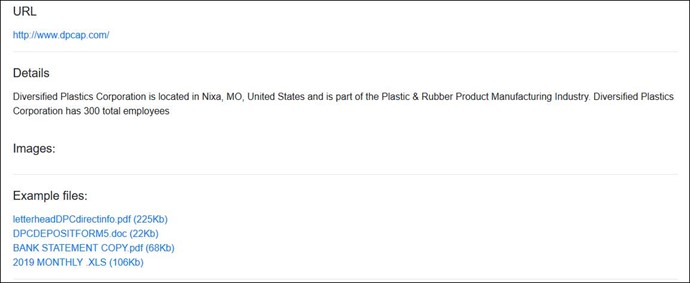
Insights: Ransomware groups continue to leverage data exfiltration as a tactic, though there is no guarantee that the data will not be leaked after paying the ransom. The attackers will likely re-purpose the data and sell it to potential competitors or auction it in underground forums for financial gains. CTI recommends victims refrain from considering ransom payment as a possible solution. Organizations are also increasingly susceptible to vulnerabilities hosted by complex supply chains that offer potential attackers a foothold into the organization’s infrastructure. Ransomware operators are moving beyond operational disruption, reputation damage, the threat of leak data, double extortion techniques to Ransom DDoS (RDDoS) as means to extract financial gain from target organizations and their vendors.
Summary: The website, SecuriElite, claims to be an offensive security company located in Turkey offering pentests, software security assessments, and exploits. It has a link to their PGP (Pretty Good Privacy) public key at the bottom of the page. The researchers who were targeted by the same group in January, highlight that a similar tactic of hosting a PGP key on the attacker’s blog, lured them to visit the site where a browser exploit was waiting to be triggered. To establish the company’s legitimacy, the threat actors have even set up fake LinkedIn profiles.
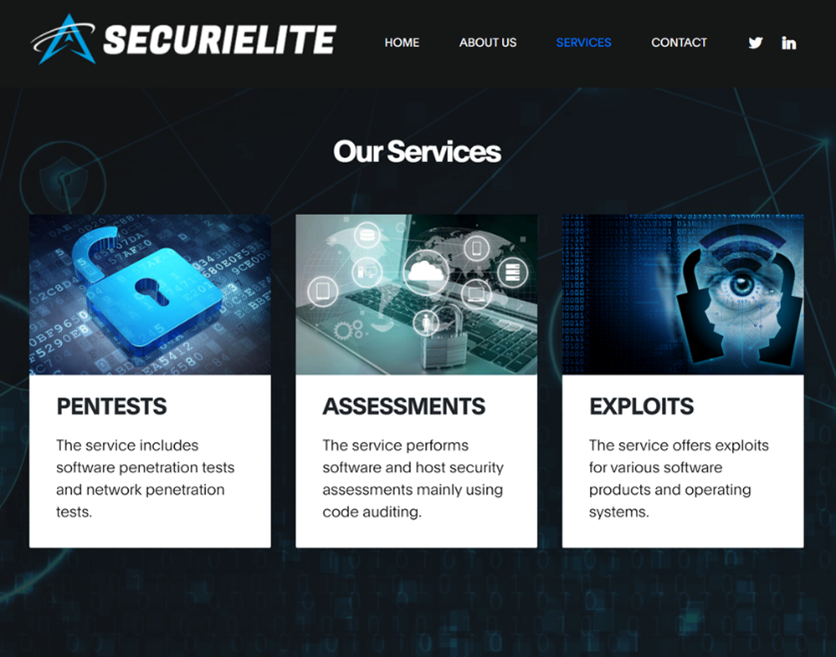
Insights: In the past, North Korean threat actors have executed various campaigns using cleverly crafted social engineering techniques. One such campaign – Operation Dream Job – is suspected to be carried out by the Lazarus Group. Upon initial compromise, the suspected threat actors allegedly use victims’ systems to gain access to the organization’s network, carry out lateral movement, implant malware, and possibly exfiltrate sensitive details. The threat actors could possibly use the details to sell to competitors for financial gains or work in alignment with their government’s political and economic interests.
Summary: VMware Carbon Black Cloud Workload appliance 1.0.0 and 1.01 has an authentication bypass vulnerability that may allow a malicious actor with network access to the administrative interface of the VMware Carbon Black Cloud Workload appliance to obtain a valid authentication token. Successful exploitation of this issue would result in the attacker being able to view and alter administrative configuration settings. An update in version 1.0.2 is available to remediate this vulnerability in the affected versions of the appliance.
Insights: Apart from applying the patch, the organization should adhere to best security practices. In this case, limit access to the local administrative interface of the appliance.
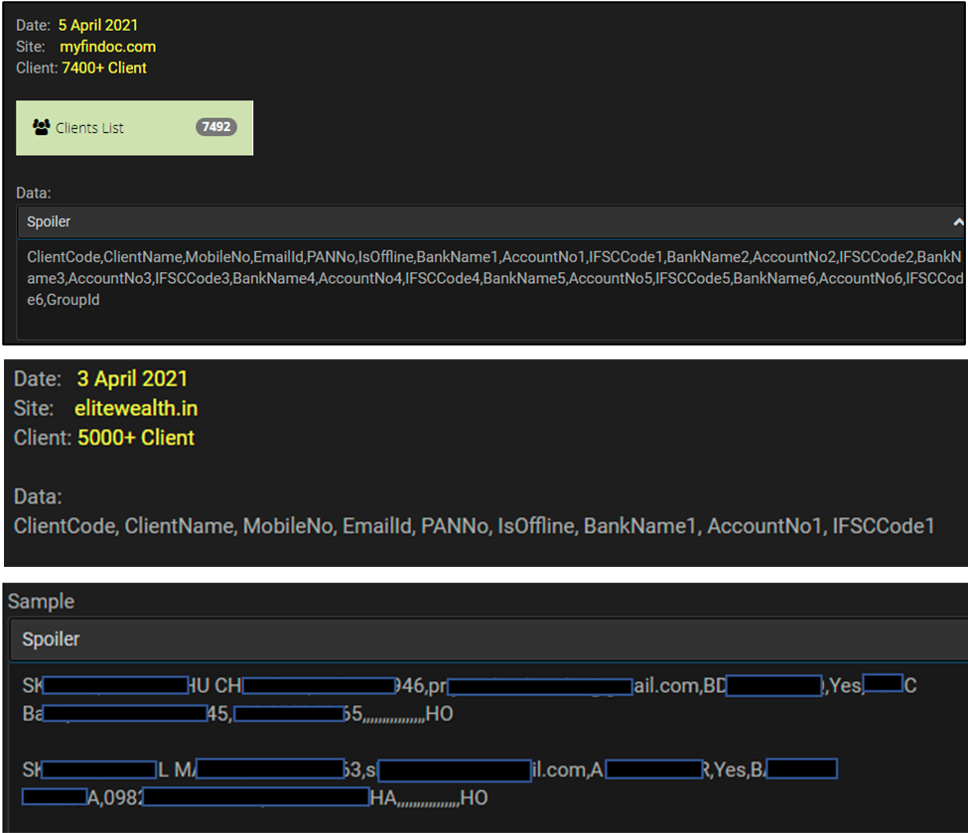
Summary: Details of approximately 7,400 and 5,000 clients of myfindoc.com, elitewealth.in respectively have been observed to be advertised for sale by unknown threat actors in the underground forums. The leaked records include personally identifiable information (PII) such as client name, mobile number, email address, PAN (Permanent Account Number), and other financial information related to the affected client.
The following screenshots were shared by the researchers:
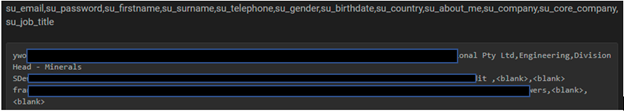
Summary: A database containing user details of MiningMagazine.com based out of South Africa has been observed to be advertised for sale by unknown hackers in the underground forums. The leaked data include personally identifiable information (PII) such as email address, password, first name, surname, telephone, gender, date of birth, and employment details identifying users potentially subscribed to the service.
The following screenshots were shared by the researchers:
Insights: These incidents highlight the importance of securing databases and the critical information stored in them. Organizations must pay special attention to business-critical data and take appropriate steps to help prevent mishaps involving unintentional exposure. Defining a well-documented policy involving repeatable processes and training on those processes is an important first step. Also, technical controls such as secure configuration, encryption (both in transit and at rest), privileged access, and vendor advisory must be adhered to help minimize such incidents.