



The Gartner Security & Risk Management Summit 2019 was held from August 5th to 7th, 2019. On the first day of the event, the Platinum Sponsor Session was organized, featuring Mr. Takashi Amano, Director of Cyber Security Center of Toshiba Corporation, and CYFIRMA Chairman and CEO, Kumar Ritesh. Herein is the broad outline of this lecture. Note that the lecture materials can be downloaded by completing the form listed at the end of this article.
Expectedly, the lecture was fully booked prior to the event, prompting the organizers to relocate to a larger venue to accommodate the additional influx of attendees. About 200 people attended the Platinum Sponsor Session on the first day of the Gartner Security & Risk Management Summit 2019.
Agenda of this lecture covered;

Kumar Ritesh’s presentation first addressed the challenges he faced while serving as CISO (Chief Information Security Officer) of a globally prominent organization.
Next, Kumar Ritesh explained the five factors that are contributing to Japanese companies and organizations’ standing as prime targets for cyberattacks.
Furthermore, he touched upon the threat situation surrounding the Japanese manufacturing industries, financial institutions, and organizations managing critical infrastructure systems. Prominent companies in these industries are the targets of state sponsored hacker groups and such hacking campaigns were explained with examples. In light of these developments in the cyber landscape, Ritesh stated:

We introduced CYFIRMA’s Cyber Threat Intelligence Analysis Platform v2 (abbreviated as CAP) as a complete and proactive solution to protect against increasing cyber threats targeting Japanese companies and organizations. CAP collects information from over 280,000 data sources, including closed/private dark web forums, and analyzes with 5 AI and machine learning engines, thereby providing comprehensive threat visibility and intelligence specific to individual companies and organizations.
Ritesh described the advantages and value provided by CAP as thus:
Next, we introduced the three main modules that make up CAP v2.
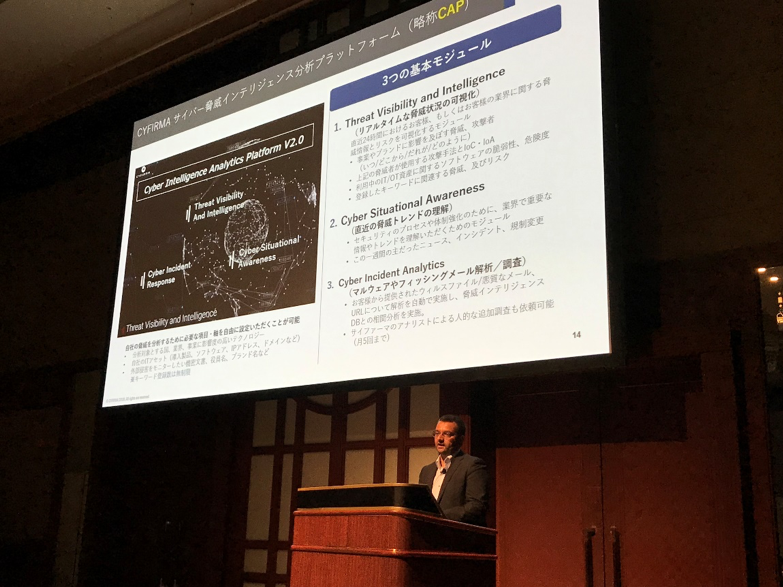
For details on CAP, please request a demo from the form below.
After detailing the CAP, Ritesh explained the use cases specific to a major US financial institution. The latter was struggling to respond to cyber-attacks targeting its online trading and transaction systems and couldn’t determine which hacking group or country was responsible for the same. As a result of CYFIRMA’s investigation, the organization was able to identify that the attacks were being carried out by the North Korean Lazarus group. Based on CYFIRMA’s insights, the CISO of the financial institution reviewed their own cyber security strategy and measures, and redefined procedures such as incident response based on information about the hackers’ attack vectors, campaigns, and tools used. Additionally, by utilizing the IoC information used by Lazarus, the organization was able to reduce cyber-attacks by 78% month on month.
As a second use case, Mr. Amano, General Manager of Cyber Security Center, Toshiba Corporation, gave a presentation and introduced Toshiba’s cybersecurity efforts. In the presentation, after touching on Toshiba’s business portfolio and efforts to contribute to their customers’ digital transformation through Cyber Physical System (CPS) technology, the associated increase in cyber-attack risk due to the spread of CPS was taken up as an issue. Mr. Amano cited the following three points.

He explained that Toshiba’s basic philosophy is to respond to increasingly sophisticated and diversified cyber-attacks based on the following three viewpoints.
Based on the above concept, “Life Time Protection” and “Value Chain Protection” initiatives were explained, followed by the introduction of Cyber Defense Management Platform (CDMP), an orchestration and automation platform that realizes risk-based security management.
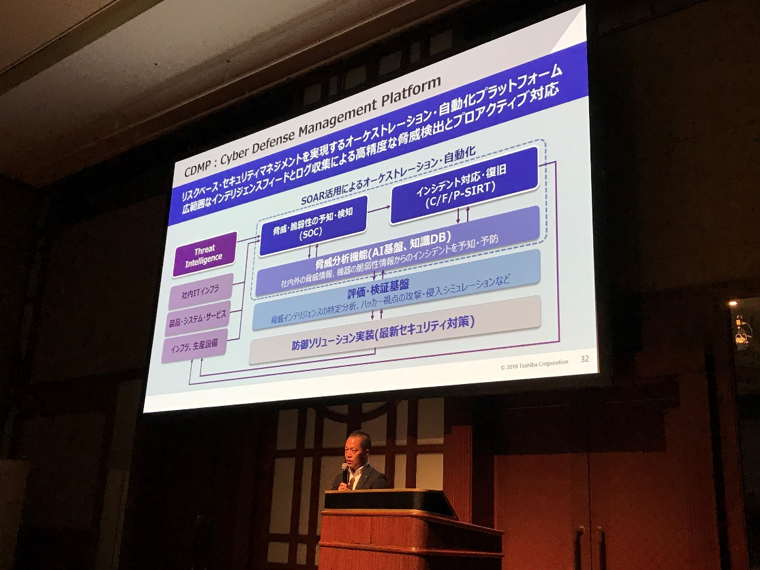
CDMP is a unique platform that enables high-precision threat detection and proactive response through extensive intelligence feed and log collection. CYFIRMA’s threat intelligence is used as one of its intelligence sources.
CYFIRMA’s threat intelligence is used as one of its intelligence sources.
Mr. Amano introduced slides depicting the types of threat intelligence services from Toshiba’s perspective and detailed four examples highlighting the usage of threat intelligence at Toshiba. Finally, he explained the following four points as strengths of, and expectations from, CYFIRMA.
1. Strategic intelligence and advanced analytics by analysts
2. Global support ability
3. CPS advancement, proposal for SOAR
4. Expected to improve dashboard menu and UI
In summation, the Platinum Sponsor Session at the Gartner Security & Risk Management Summit 2019 was a resounding success. The assembled audience got the opportunity to listen to Kumar Ritesh’s expert insights on the Japanese cybersecurity landscape, followed by an advanced lecture from Amano-san about the management of cybersecurity at a leading Japanese multinational conglomerate, Toshiba.
You can download the materials (partial) of the day by completing the form below. If you do have any queries, please reach out to us.