


Cyber Protect gives you limitless power to cultivate deep trusted partnerships with your customers, build your unique differentiator, and sets you on the path of hypergrowth
Get Started
Cyber Protect is a hyper-optimized digital risk monitoring service that is power packed to give business owners and entrepreneurs the expanded protection needed to keep digital businesses secure everywhere.

It is the essential protection right-sized to meet the budget and need of your customers.

It helps you establish deep connection with your customers and elevates you to the coveted role of a trusted advisor.

And yes, you get to expand your offering, build a powerful differentiator in your business, and get ready to drive profits beyond imagination.
We have helped hundreds of B2B companies establish deep connections with their customers, transforming our partnerships into a highly valued customer acquisition channel. Now, it’s your turn.
Come on board, you’ll have the expertise, technology and go-to-market strategies to drive the highest revenue and profits.

Complete your service offering with Cyber Protect and stand out from the competition today.
70% of cyberattacks on businesses hit small companies. And 80% of small businesses attacked fail within a few months. Cybercrime not merely a nuisance, it is an existential threat. Cyber Protect for GoDaddy is the Hyper-Optimized Digital Risk Monitoring Service for smart entrepreneurs everywhere.
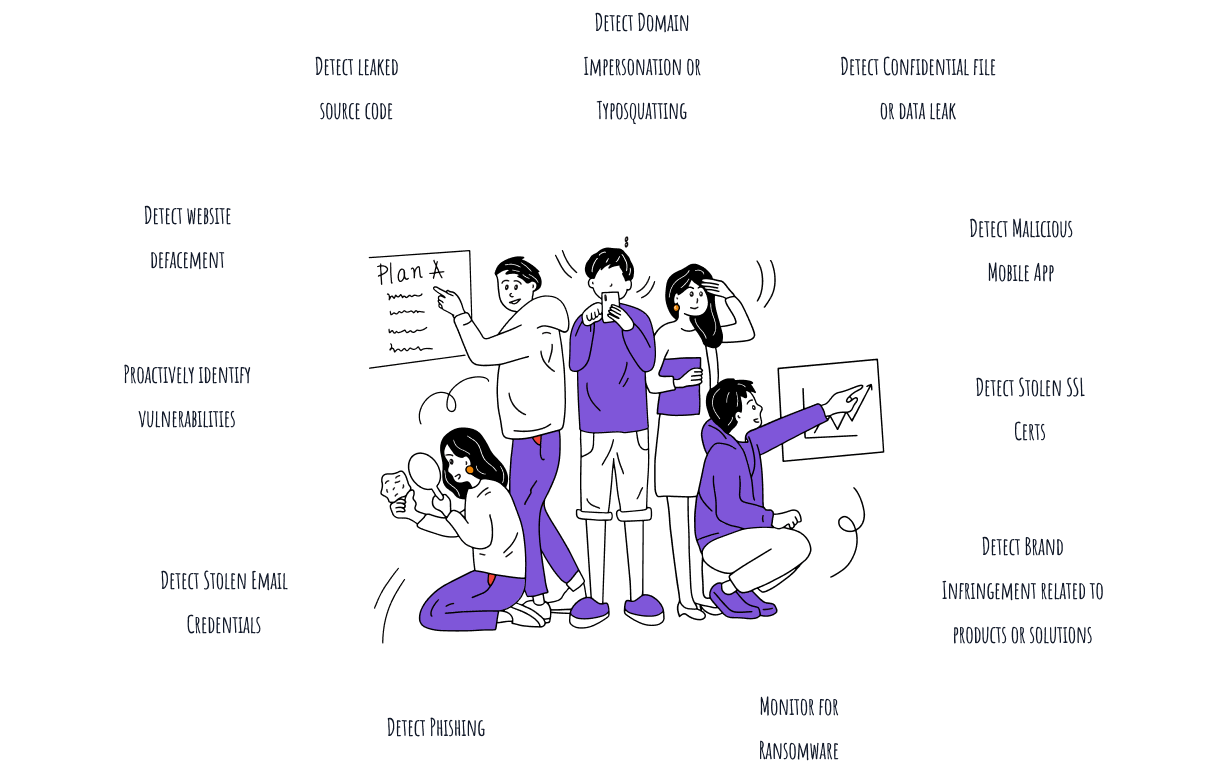

Your domain name is the calling card for your business. It is how you show up to the world. Ensure it is not at risk of being impersonated or held hostage by cybercriminals.
Your intellectual property, customer data, financial records must stay safe from preying eyes.
You need to know if hackers are selling your employees' emails and passwords in underground forums so you can take action to stem the damage.

Copycat websites are created by cybercriminals using domain names that look like yours to trick your customers into divulging confidential data.

Don't let scammers and hackers have their way with you and your business.

Enterprise-grade cybersecurity protection that delivers that punch in the gut to cybercriminals everywhere

Real-time continuous monitoring to identify shadow IT that could be compromised by cybercriminals. Gain awareness so you can decide how to shrink your attack surface.

Cyber Protect brings to your attention data which has been stolen and available for sale in underground marketplaces. This includes data which has been exfiltrated by ransomware groups
Cyber Protect scans deep, dark and surface web and social media to look to signs of impersonation and infringement
With Cyber Protect, you would always know if your IP and confidential data has been exposed, including lookalike or malicious apps. Receive alerts on social sentiments that could present a threat to you or your business.

Gain insights to your third-party's digital risk profile. Ensure employees, business partners and third-party contractors have not inadvertently shared sensitive information which could subject the company to cyberattacks and risks
Cyber Protect is built using the industry-leading digital risk discovery and protection platform designed for businesses of all sizes. From fast-growing start-ups to Fortune 500 companies, its powerful capabilities have been used to protect people, data and assets from cybercriminals and emerging threats. Here’re the quick 3 steps to get you protected immediately.

Sign up for either Basic or Advanced package

Cyber Protect only requires the Domain Name you’d like to monitor for digital risk exposure. Provide us that Domain Name.

You will be automatically on-boarded to Cyber Protect platform. Once you have completed your purchase, look out for the log in details sent to your email. You can access the platform and start monitoring for cyber threats, risks, exposed data and vulnerabilities.
Simple, transparent pricing that grows with you.
Our most popular plan for small teams.
Our most popular plan for small teams.
Go through the frequently asked questions to resolve your queries regarding the product. If you don’t find your answer, please write to [email protected]
