Published On : 2021-08-11
EXECUTIVE SUMMARY
Russian Cybercriminals – FIN11 Group is suspected of leveraging common target infrastructure indicators (IoCs) across two major campaigns attributed to them known as EmB0 and Topaz Stone, which are tracked and monitored by CYFIRMA in DeCYFIR.
Based on our research and analysis, we observed multiple similarities between the campaign’s target industry & geography, TTPs (Tactics, Techniques, and Procedures), threat actor’s motives, the malware used, along with shared infrastructure and indicators.
The potential collaboration with North Korean hackers as part of hacker-as-a-service (HaaS) and Chinese hackers under ransomware-as-a-service (RaaS), is also suspected post the detailed analysis that was carried out.
The widespread primary motive of both these campaigns appear to be to the exfiltration of sensitive information, Customer information for financial gains.
CYFIRMA recommends using the reported IOC details for measures against this campaign and threat hunting within your environment.
CYFIRMA Risk Rating for this Research is Critical.
FIN11 GROUP CAMPAIGNS
CYFIRMA observed several similar target infrastructure indicators shared between two major campaigns suspected to be carried out by the Russian Cybercriminals – FIN11 Group.
The two campaigns are EmB0 and Topaz Stone. Following are the details of both the campaigns:
Campaign 1
- Campaign Name: EmB0 is suspected to be launched on 12 April 2021.
- Target Industries: Critical Infrastructure, Electricity Supply, Water Management, Transportation, Logistics, Equipment Making, Supply Chain.
- Target Geographies: USA, Japan, South Korea, Taiwan, European Nations, South-East Asia.
- Motivation: Exfiltrate design, supply chain information, sensitive information, Personally Identifiable Information (PII), Customer Identifiable Information (CII), Financial Gains.
- Method Discussed by Hackers and their Interest: Exploiting vulnerabilities, Implanting specialized malwares and ransomware, Lateral movement into the organization.
Campaign 2
- Campaign Name: Topaz Stone aka камень топаз is suspected to be launched on 1 February 2021.
- Target Industries: Financial Institutions, Trading, Financial Regulatory Bodies, FinTech, Supply Chain.
- Target Geographies: Thailand, Singapore, India, Australia, USA, Japan, South Korea
- Motivation: Exfiltration of sensitive information, system information, financial and customer information for financial gains.
- Method Discussed by Hackers and their Interest: Malwares, Custom-built exploit, keen on taking over administrative accounts using specialized malware implants.
Similarities between both campaigns:
Following are the similarities observed between both the campaigns:

COMMON TARGET INFRASTRUCTURE
Following are the common target infrastructure indicators observed between both the campaigns:

HYPOTHESIS – POTENTIAL TTPs
Based on our quick research and analysis of the target infrastructure indicators leveraged by the threat actor, the following malware details are observed:
Dewmode Backdoor: CYFIRMA identified DEWMODE web shells associated with the campaign activities. A set of threat actors named UNC2546, UNC2582 with possible ties to FIN11, Clop, and Ryuk ransomware gangs. The backdoor was suspected to be used in Accellion FTA attacks. Dewmode could download files, delete footprints on the target asset from commands executed by the malicious user remotely.
Ryuk Ransomware: Ryuk is a highly sophisticated type of ransomware that is being used to target organizations all over the world since its discovery in August 2018. With its payloads being found in roughly one out of every three ransomware attacks over the last year, Ryuk is one of the top ransomware-as-a-service (RaaS) groups to amass a fortune of at least USD150 million. The use of worm-like capabilities by developers of Ryuk ransomware suggests that the ransomware operators are evolving in their attack techniques with the motive of cyber espionage and financial gains.
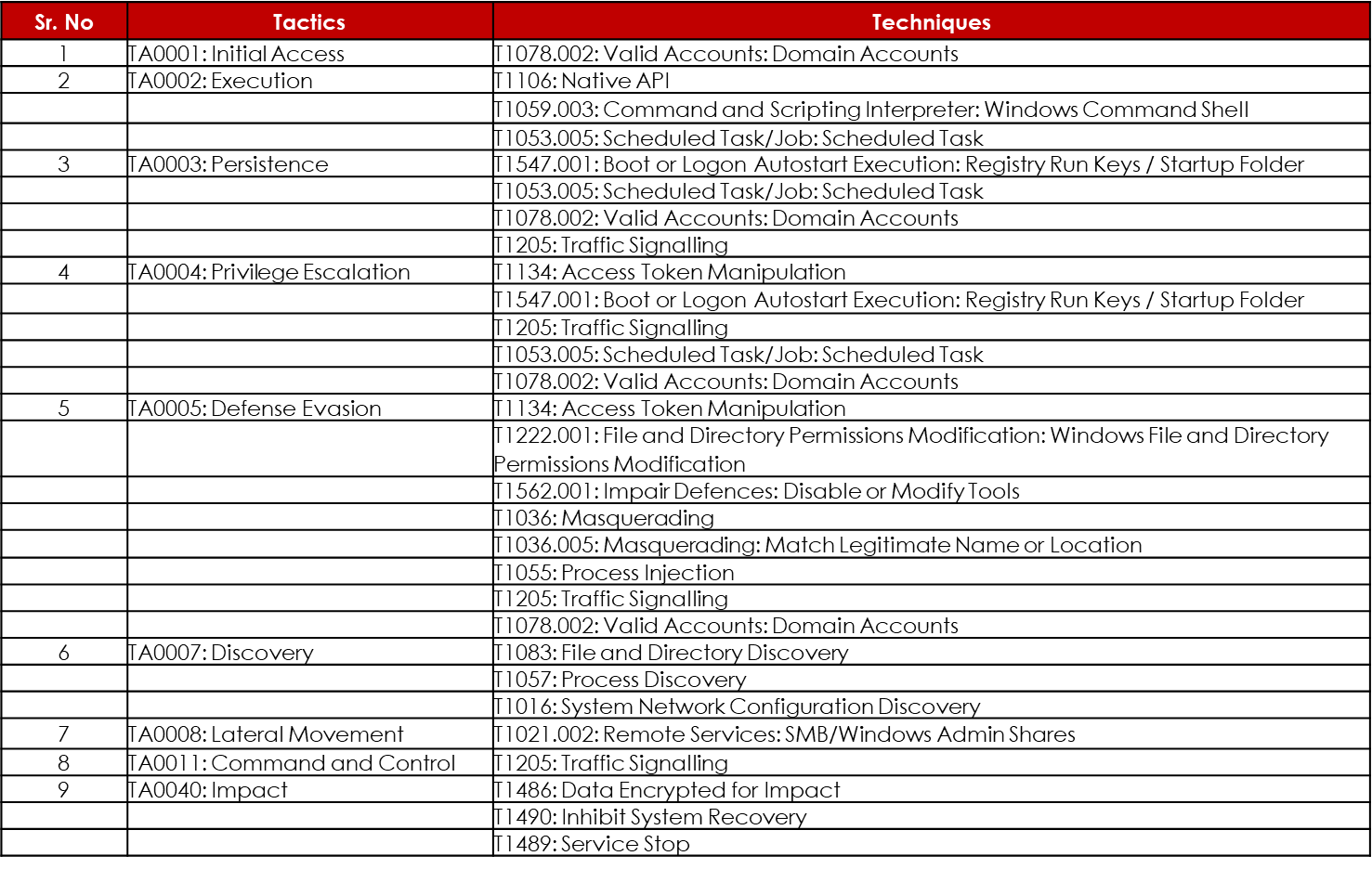
Based on the Attack Mitre framework, the following techniques and tactics are suspected to be used by Dewmode malware/Ryuk Ransomware potentially leveraged by FIN11 Group as part of the campaigns:
INSIGHTS
- The Russian cybercriminals have been observed to be very active and have targeted multiple organizations in the past. Our findings show their clear interest in potentially targeting organizations across multiple industries, geographies, and leveraging the common infrastructure indicators during the campaigns.
- The primary intent of these hacker groups in targeting foreign organizations appears to be to exfiltrate sensitive details to be sold in the grey market or to potential competitors for financial gains.
- CYFIRMA observes clear indicators of Russian cybercriminals suspected of expanding their attack surface and targeting multiple geographies and industries. It is suspected that the cybercriminals and ransomware operators could be operating under the guidance of their masters in carrying out these campaigns.
- CYFIRMA observed clear potential indicators of Russian Cybercriminals: A) Collaborating with Chinese Threat Groups and Ransomware Operators under Ransomware-as-a-Service (RaaS model), and B) Possible collaboration with North Korean Groups as part of Hacker-as-a-Service (HaaS model).
- Based on the initial analysis of the indicators, it appears the threat actors are interested in exfiltrating data for financial benefits.
- We strongly recommend organizations be prepared against potential cyberattacks by the FIN11 Group and other potential Russian Cybercriminals.
RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/blocking the IOCs and strengthen defences based on the intelligence provided.
- Webservers and application servers need to be updated/patched to prevent attacks such as remote code execution (RCE), which could lead to data exfiltration, data breach, etc. This may also need to be done as needed if critical exploits exist, and a patch and/or workaround is available.
- Configure network defence systems such as intrusion detection systems (IDS), intrusion prevention systems (IPS) for real-time alerts.
- Deploy an advanced Endpoint Detection and Response (EDR) engine as part of the organization’s layered security strategy.
- Limit the unsuccessful login attempts with account lockouts and progressive delays into the login process to make it effective.
- The use of CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is effective against automated bots.
- Restrict the logins to a specific range of IP Addresses.
- Implement Multi-Factor Authentication (MFA) to reduce the risk of potential data breaches.
- Make the root user inaccessible via SSH by editing the sshd_config file and implementing ‘DenyUsers root’ and ‘PermitRootLogin no’ options.
- Move to a non-standard port for SSH instead of using the default port 22 and edit the new port line in the sshd_config file.
- Move to a non-standard port for SMB, RDP instead of using the default ports.






