



CYFIRMA Research – 10 Jun 2020
CYFIRMA’s researchers have tracked Maze as early as Jun last year, and on 10 Jun, Maze group have released a long list of companies who have fallen victim to their cyberattacks. Affected companies span from the US and South America to the UAE.
Maze ransomware operators are known to launch their attack under the surface and have a history of first stealing the data before locking their target devices. As an extortion cartel, Maze operators capitalize on victim organizations’ fear of reputation damage, potential lawsuit, and other business impact to extract maximum financial benefits. Run-of-mill ransomware demands are usually in the range of hundreds to thousands of dollars (bitcoin equivalent), but with Maze, the amount can run into millions.
The modus operandi of Maze hackers would entail releasing threats of data dump on public forum if ransom is not paid. When such data is made available, other hackers and cybercriminals will have access to the sensitive data, and would continue their separate exploits, including reselling stolen data in dark web marketplaces.
Maze operators have targeted a number of high-profile large enterprises, and government-linked corporations, across wide-ranging industries. Their recent breaches include Cognizant, a global IT services powerhouse with 290,000 employees and annual revenue turnover of almost US$17B in 2019, and ST Engineering, a Singapore government-linked company involved in defence and military projects.
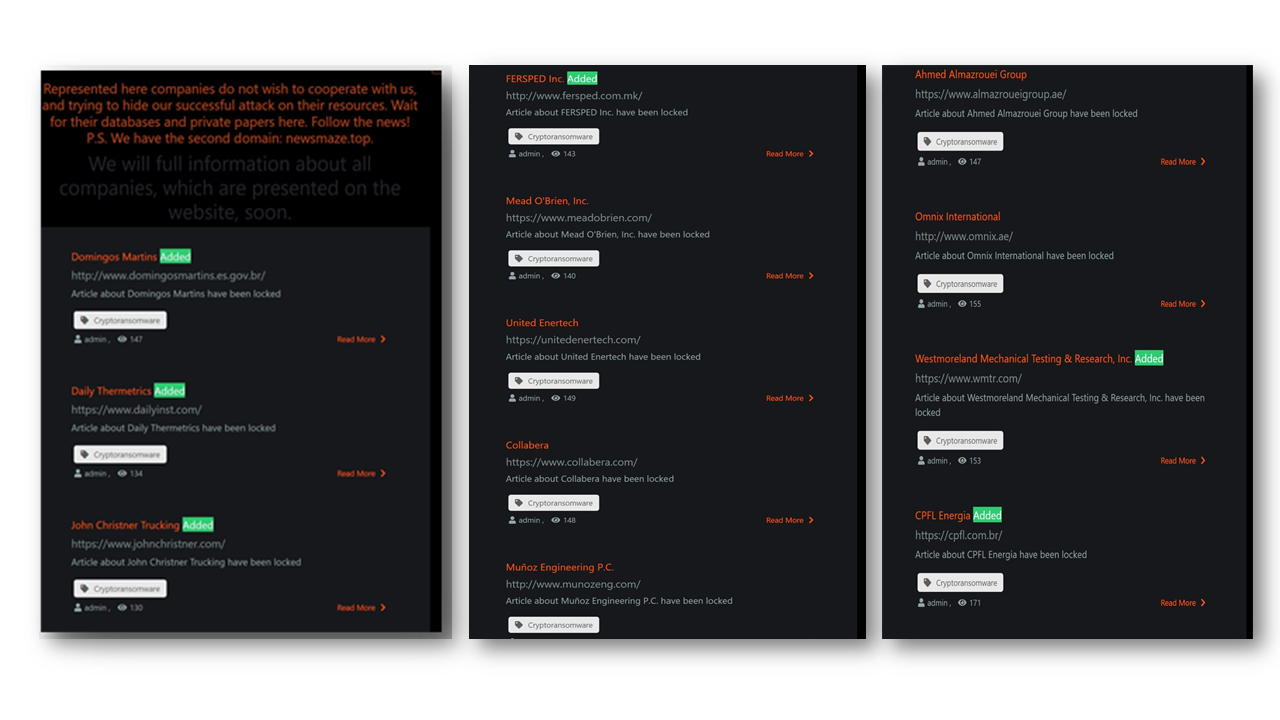
Here is the latest list of companies who have been compromised by Maze operators and shared in Maze website:
Domingos Martins – Brazilian government website containing information related to Domingos Martins municipal. Breached data could include citizens’ information such contact details, taxes, e-government services rendered.
Daily Thermetrics – A US firm providing process engineering industries with precise temperature measurement instrumentation.
John Christner Trucking – A family trucking business based out of Oklahoma.
FERSPED Inc. – A shipping and freight-forwarding company based in Macedonia.
Mead O’Brien, Inc. – The company provides valves & valve automation, steam & hot water products and systems, instrumentation products, skid designs, field services, surveys, assessments, and consulting services, and is based in Kansas City, USA.
United Enertech – A US construction, building and engineering company based in Tennessee
Collabera – A HR recruitment, search and training company located in New Jersey, USA.
Munoz Engineering P.C. – Provides engineering, land surveying and building and construction services, based in New York, USA.
Ahmed Almazrouei Group – Engineering and Design Services, General Trading, Property Management, Facilities Management, Oil & Gas, Educational and Food retail business headquartered in Abu Dhabi, UAE.
Omnix Int’l – A provider of business analytics, BPM, mobility solutions, information management, ERP implementation and IT networking services to public and private sectors, based in Dubai, UAE.
Westmoreland Mechanical Testing and Research, Inc. – A material testing facility for the additive manufacturing, aerospace, automotive, composites, and medical and power generation industries, based in Pennsylvania, USA.
CPFL Energia – A large energy company with businesses in distribution, generation, commercialization of electricity and services serving 9.6 million customers in Brazil.
Here are extracts of the stolen data belonging to the above organizations which are now publicly available.

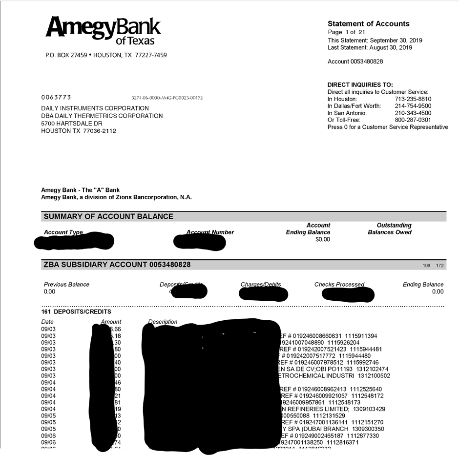
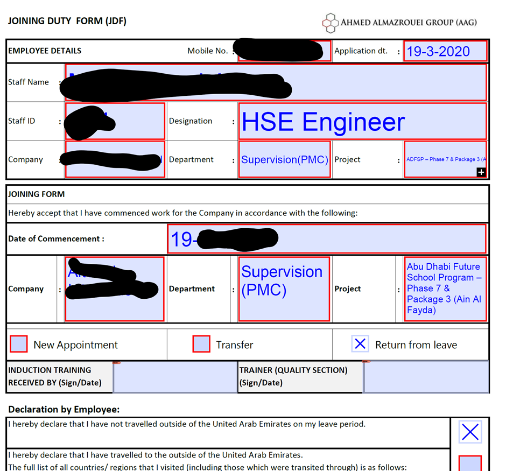

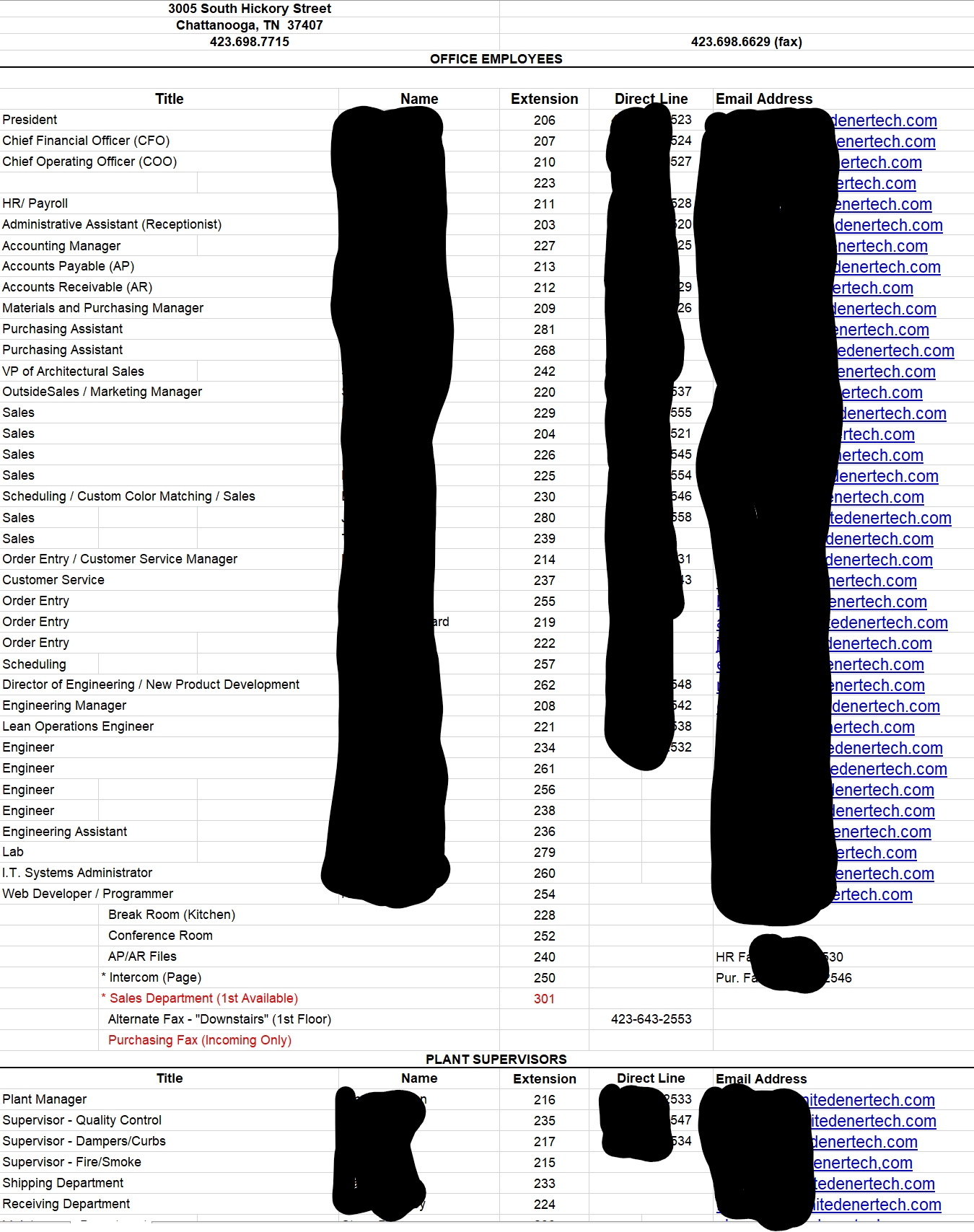


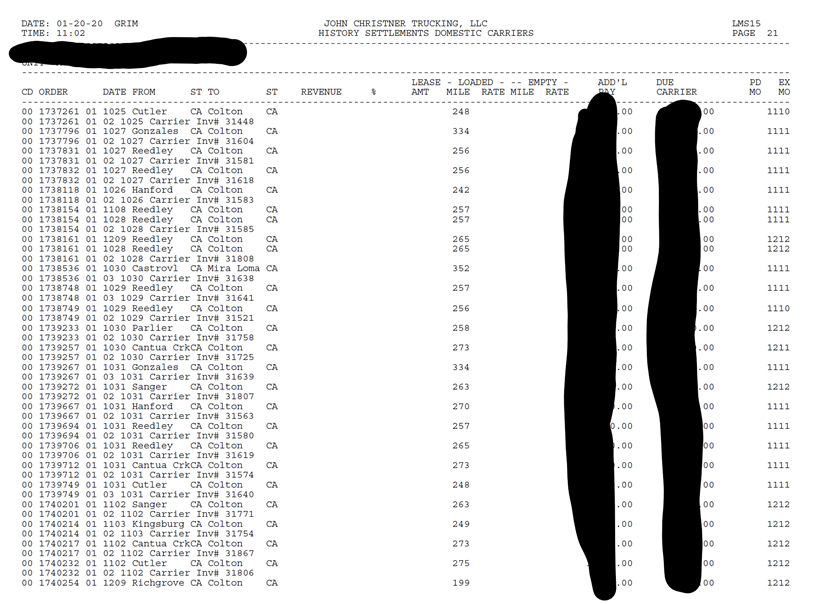

Here’re the screens as captured from the Maze Group forum where the hackers announced their successful campaigns of locking down victims’ systems:
Maze ransomware operators have a history of first stealing the data before locking their target devices and demanding ransom. They capitalize on the reputational consequences of their target as their strategy is “steal, lock and inform.” Suspected threat actors appear to be Russian-based APT28 (Confidence Level: Moderate) and TA2101/APT29 ((Confidence Level: Moderate).
The IP addresses <Details Masked> mentioned in Cognizant attack vector was seen exploiting two old vulnerabilities CVE-2016-7255 and CVE-2018-8453. Both these Win32k Elevations of Privilege Vulnerabilities targeting Windows server was exploited by suspected Russian state sponsored threat actor APT28 in the past.
The threat actor group APT28 leverages TTPs like obfuscated files or information, PowerShell, exploitation of remote services for lateral movement, credential stealing through spear-phishing links and data-staged techniques. These similar TTPs were seen in the Cognizant hack due to Maze ransomware.
The mentioned IP addresses like <Details Masked> belong to Russian origin which gives us the glimpse that Russian threat actor groups (possibly APT28) are behind the attack.
On similar lines, the threat actor group TA2101 had leveraged Maze Ransomware targeting German, Italian and U.S. organizations with malicious emails carrying samples of Maze ransomware in November 2019. TA2101 has been actively using Maze ransomware for attacks.
Maze Ransomware usually deploy phishing emails with MS Office attachments and fake/phishing websites laced with Exploit Kits. Recipients should be cautious when handling emails from unknown sources, downloading attachment, or clicking on suspicious links as Maze operators utilizes social engineering tactics aggressively.
To strengthen security controls, software and applications should contain the most updated patch. Avoid pirated and counterfeit software as they could be laced with malware.
Maze tends to use known vulnerabilities like the Pulse VPN CVE-2019-11510 to break in and this means employees working from home must be mindful when accessing sensitive company information. More actions can be taken to protect your organization from Maze ransomware.