


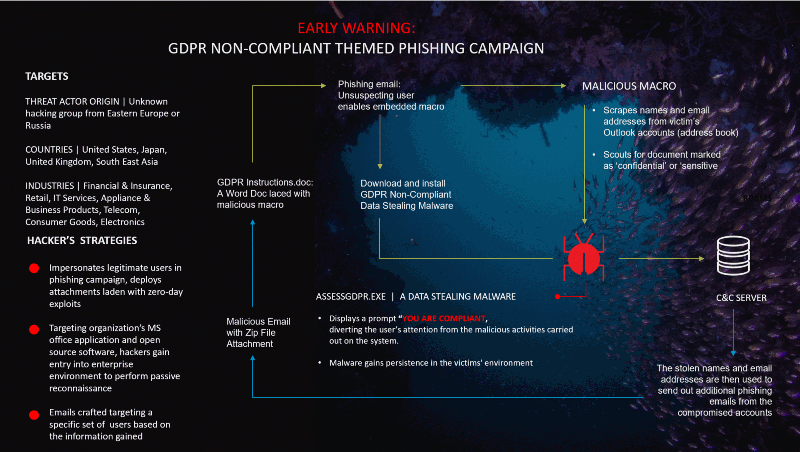
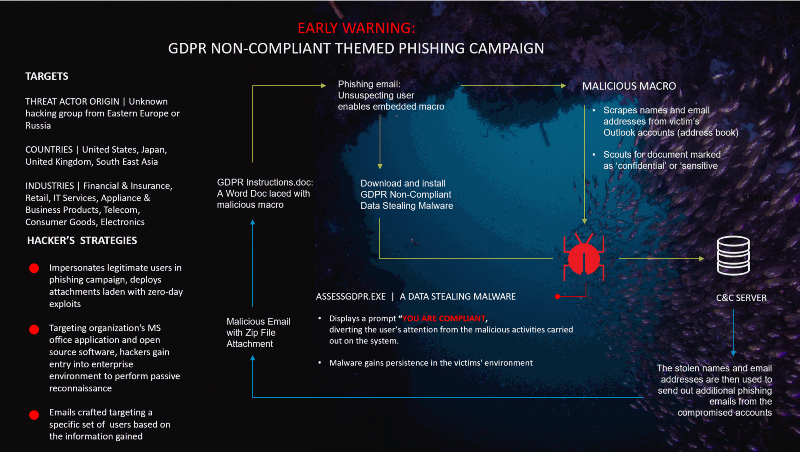
CYFIRMA’s cyber intelligence research center has discovered a potentially new GDPR Non-Compliant themed phishing campaign which distributes a Data Stealing malware in an attached infected Word document zip file. After the malicious file is executed, it then downloads an executable (AssessGDPR.exe) that enables the attacker to exfiltrate data from the infected system.
Our analysis points to a yet-to-be-named Eastern Europe or Russian threat actor group connected to this phishing campaign.
This campaign is being directed towards the following industries:
Financial and Insurance, FMCG, IT Services, Appliances and Business product, telecommunication, electronic and consumer goods companies.
Indicators of attack and compromise:
Our analysis indicates that the attackers will use a carefully scripted phishing email attempting to exploit a user’s susceptibility to GDPR non-compliance issues, demanding immediate actions to be undertaken by the target organization. The email will have a Zip file with the filename “[GDPR instructions.doc.zip]” as an attachment containing a malicious macro allowing the attacker to communicate with its remote server, triggering the download of the data-stealing malware in the form of an executable file: “[AssessGDPR.exe]”
1. GDPR Instructions.doc is a Microsoft Word document attached to the phishing email containing an embedded macro allowing the hacker to read contact details from the user’s address book and search for documents with confidential and sensitive keywords, and then further downloads a second malicious executable file, AssessGDPR.exe.
2. AssessGDPR.exe is data-stealing malware which once installed on the target system, exfiltrates data to the attacker’s command and control server. A visual prompt of “You are Compliant” is displayed to the user after the file is executed. Attackers use these common diversion techniques to distract the attention of the user while the malicious activities on the target system are being undertaken in the background.
Fake Sender Email Addresses which might be used to send malicious phishing email:
nochange@gdpr-rules2018[.]com
actnow@gdrpupdate[.]co[.]uk
non-compliant@cyber-risk2376[.]net
emea-gdpr@euro[.]com
GDPRCompliance@boker[.]net
GDPR-check@eurp[.]co[.]uk
non-compliant@cyber-risk2376[.]net
nochange@gdpr-rules2018[.]com
Potential fake URLs which might be leveraged by attackers as part of the phishing emails to dupe users:
http[:]//compliancechecker-gdpr18[.]com
www[.]gdpr-maker[.]com
www[.]avoid-gdpr[.]co[.]kr
http[:]//gdpr-lockdown[.]com
www[.]gdp-1844[.]net/publish[.]asp
www[.]cyber-risk2376[.]net/validatenow[.]exe
http://checkitnow18[.]net/gdrp-check[.]exe
www[.]gdrp-2018-compliant[.]co[.]uk/18form-updat[.]xls
C&C IP addresses can be used to send the phishing emails, facilitating download of malicious executable and sensitive data collection from infected systems:
77.94.35.168
210.52.109.22
77.94.35.131
77.94.35.168
193.206.239.215
Potential malicious payload, which can search the compromised end-point for any document marked as ‘confidential’ and ‘sensitive’ and exfiltrate email address book.
Suspected Data exfiltration malware
51801EA54CC24857858B1B4325D18721
AB09DD54C5D39D150B1B5E5ACDE0F141
Address book exfiltration malware
3bd07212d1e1573f66bd7ea12b025214
006cc1d3984b2b810295e63b11835016
Recommendations:
・ Monitor or Block malicious malware files and C&C IPs via web proxy servers, AV solutions, firewalls, phishing controls and email gateways
・ Block IOCs (Indicators of Compromise) such as malicious URLs, IP Addresses, SHA fingerprint, Hashes under firewalls, proxies, endpoint, spam and phishing security control
・ Do not open emails from untrusted sources-Always verify sender email address before opening any emails coming from a source outside the organization.
・ Configure Anti-Virus/IDS (Intrusion Detection System) repositories with the identified hash signatures associated with the threat to protect all endpoints.
・ Build an APT-IR strategy, which is agile and proactive, keeping in mind business goals and priorities
・ Establish a Cybersecurity Awareness and Training (CSAT) Program and run regular checks, educate employees to download applications from trusted Appstore only.
・ Implement Network Segmentation-Limiting communication between services and systems on the organization network level helps contain an infection and keeps a malware or a persistent threat from spreading.
・ Apply appropriate anti phishing and spam control with stringent email policy
About CYFIRMA
CYFIRMA defends against cyber attacks by supplying organizations with real-time threat intelligence that enables them to take a more proactive security approach. By aggregating, correlating and analyzing information from hundreds of thousands of sources on the open and dark web, CYFIRMA, helps companies anticipate what types of attacks are most likely to occur and provide the most effective response. CYFIRMA is a business division of Antuit, a global analytics firm.