Cobalt Strike is a penetration testing tool that allows an attacker to deploy an agent named ‘Beacon’ on the target machine. The beacon includes a variety of functions like command execution, keylogging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning, and lateral movement. Beacon is in-memory/file-less, in that it consists of stageless or multi-stage shellcode that once loaded by exploiting a vulnerability or executing a shellcode loader, will reflectively load itself into the memory of a process without touching the disk. It supports C2 and staging over HTTP, HTTPS, DNS, SMB named pipes as well as forward and reverse TCP; Beacons can be daisy-chained. Cobalt Strike comes with a toolkit for developing shellcode loaders, called Artifact Kit.
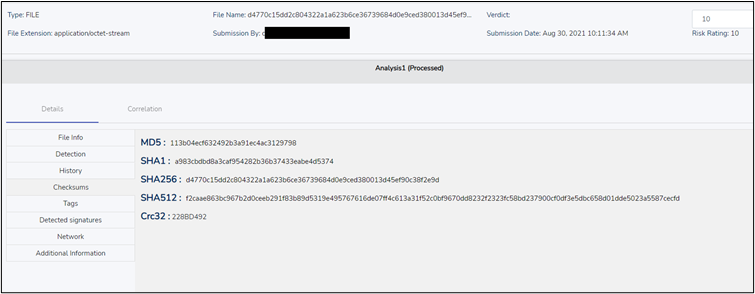
MD5 |113b04ecf632492b3a91ec4ac3129798
SHA-1 | a983cbdbd8a3caf954282b36b37433eabe4d5374
SHA-256 | d4770c15dd2c804322a1a623b6ce36739684d0e9ced380013d45ef90c38f2e9d
Risk Score: 10
Confidence Level: High
Suspected Malware: Cobalt_Strike
Function: Backdoor
Threat actor Associations: Leviathan
Target Industry: Multiple
CYFIRMA’s Threat Discovery and Cyber-Intelligence platform, DeCYFIR, has flagged the file as ‘Suspicious’ due to the factors illustrated in this report.
The file was analyzed in DeCYFIR and below are findings based on the analysis:
The malware was seen to have multiple suspicious TTPs as shown below:
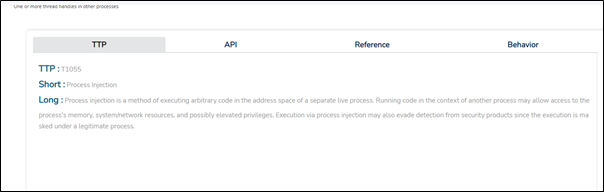
Usually, the Cobalt Strike beacon injects itself into any running process to evade detection and stay persistent.
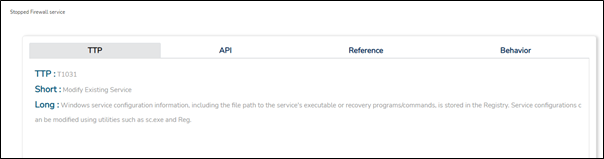
It was found to be blocking or disabling the system security services to execute the malware flawlessly. This sample was trying to find out the firewall service and terminate it.
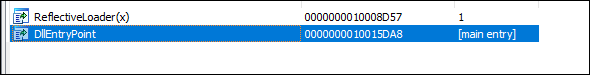
The DLL file has 2 export functions:
Anti Debugging function IsDebuggerPresent() is used to identify the presence of the debugger by returning a non-zero value.
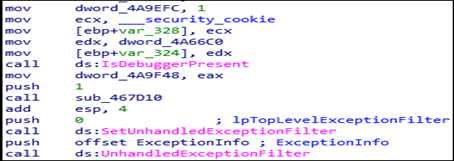
The kernel32 UnhandledExceptionFilter() is also used as an anti-debugging parameter to detect debugger.
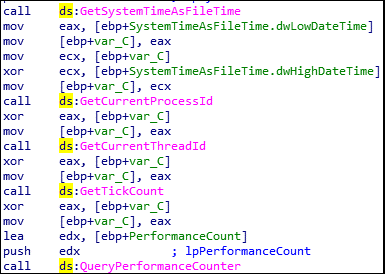
The function GetCurrentProcessId() is used to get all process id along with ThreadId, the GetSystemTimeAsFileTime() to obtain current time. The GetTickCount() will take time as parmeter to make malware idle.
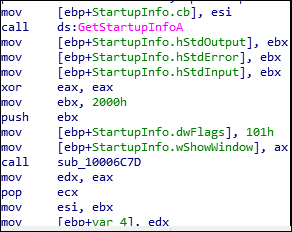
GetStartupInfoA is used to retrieve the content of the STARTUPINFO structure from when the calling process is created.
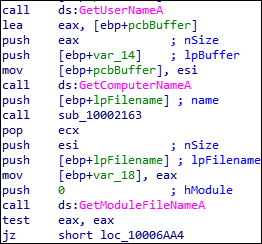
GetUserNameA is used to retrieve the name of the user associated with the thread. To retrieve the name of the local computer GetComputerNameA API is used. The malware extracts the name of the files in the current directory.
HttpOpenRequestA is used to create an HTTP POST request handle.
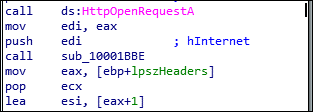
HttpOpenRequestA API is used to send the request to an HTTP server.
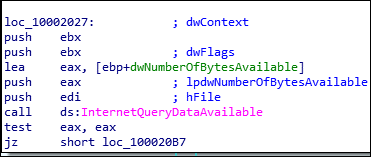
The malware queries the server to determine the amount of data available using the InternetQueryDataAvailable API.