



Much has been said about the massive disruption to economies caused by the Covid-19 pandemic. Lives and livelihoods have been irrevocably changed and the post-pandemic world may look very different from what we used to know. The dark web, too, reveals a different veneer in terms of hacker targets, methods of attacks, and the rise of state-sponsored threat actors.
While researching for cyberthreats against our global clients in the high-tech manufacturing, financial services, F&B, critical infrastructure industries as well as government bodies, we have uncovered an exponential uptick of cybercrime. The noise in the dark web has become louder and more audacious as hackers capitalize on the pandemic for financial gain, create brand damage, and jostle for geopolitical supremacy.
Cyber criminals have always profited from corporate espionage by stealing customer information, financial records, and other valuable assets. Spear phishing email, combined with trawling staff information from social platforms, has proven to be effective conduits for delivering hackers payloads. Over the last three months, with the pandemic in full force, a number of cyber criminals have diverted their targets towards high-value individuals. These are influential personalities with access to intellectual property, trade secrets and other sensitive information. Hackers have taken the path of least resistance by attacking individuals as opposed to investing vast amounts of resources to break into corporate systems.
With millions of employees working remotely and away from the protection of corporate layered defenses, vulnerabilities to cyber attacks have increased dramatically. Work patterns have shifted on a massive scale, and as reported by the European cybersecurity agency, ENISA, and the UK’s National Cyber Security Centre, the number of coronavirus-themed phishing attacks has gained momentum among remote workers. This scenario presents significant business risks when high-value individuals enter cyber criminals’ radars.
Hackers have shifted their attention to exploiting communication applications such as VPNs, video-conferencing systems, and VOIP devices. Cyber criminals have created many fictitious VPN clients to trick people into disclosing credentials to gain access to corporate networks. These fake VPN clients include perennial brands such as FreeVPN, ExpressVPN, PrivateVPN, as well as new VPN clients such as PandaVPN, RemoteArCon, and FreeRemoteConnect_CN.
Our analysis revealed a global reconnaissance campaign called Redwall, where suspected Chinese hackers have listed hundreds of publicly accessible VPN devices, proxy servers, firewalls, switches, and global load balancing devices and appliances in dark web forums and communities. These remote working tools and software have become the new source of monetization for hackers who are taking advantage of the pandemic crisis. Hacker groups such as REvil (Sodinokibi) are also observed to be actively crawling the web for vulnerable VPNs.
Our intelligence revealed hackers working on new variants of EMOTET malware, Clickbait Ad Revenue Generation, Mining cryptocurrency, as well as utilizing existing variant of malware like Agent Tesla, LokiBot, RemcosRAT, TrickBot, and FormBook as weapons for more cyber exploits.
Phishing attacks have become a primary mechanism for tricking individuals and businesses into clicking fictional Centers for Disease Control (CDC), and the World Health Organization (WHO) themed messages or announcements.
Threat actors also create fake online stores to deceive customers into downloading malware, enabling hackers to exfiltrate personal and financial information.
By re-purposing existing malware or simply using commodity malware, hackers can quickly re-calibrate their weapons and launch new attacks.
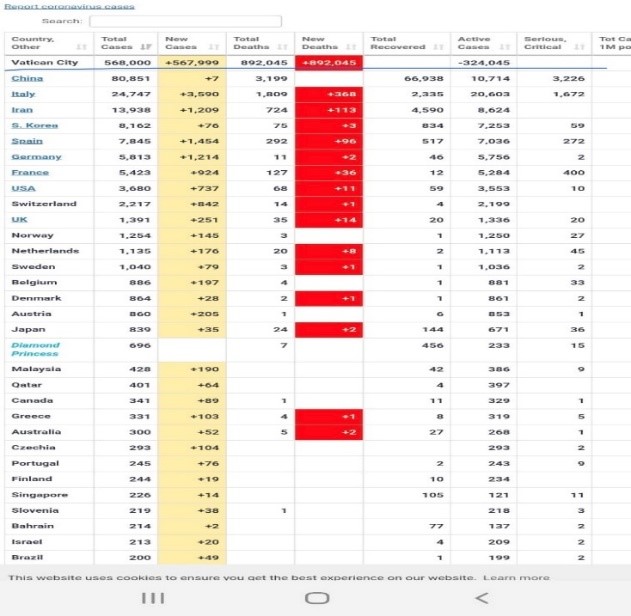
Under the cloak of fear and uncertainty, misinformation campaigns have gained traction in recent months. Hackers have breached WorldofMeters website and grossly inflated the data on COVID-19 deaths in Vatican City. The intention was to stimulate negative social sentiments and create unrest against specific communities.
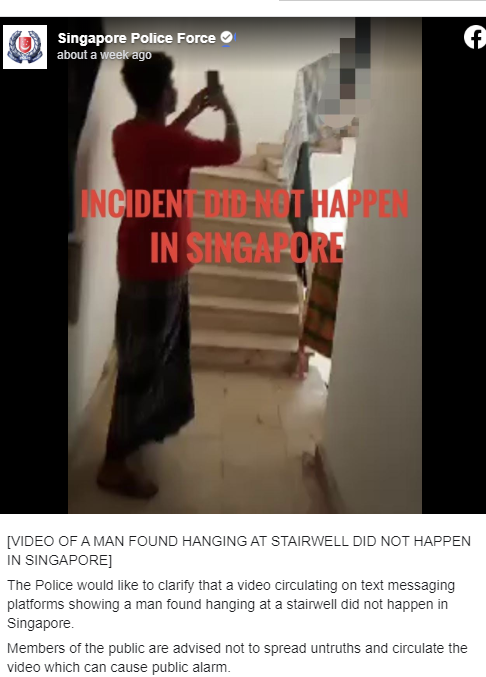
Speculation, rumours, scams, and outright falsehoods have spread like wildfire. In Singapore, fake videos of foreign workers fighting in the dormitories and committing suicide, allegedly in frustration at having been mistreated during the outbreak of the pandemic, have been widely shared and circulated.
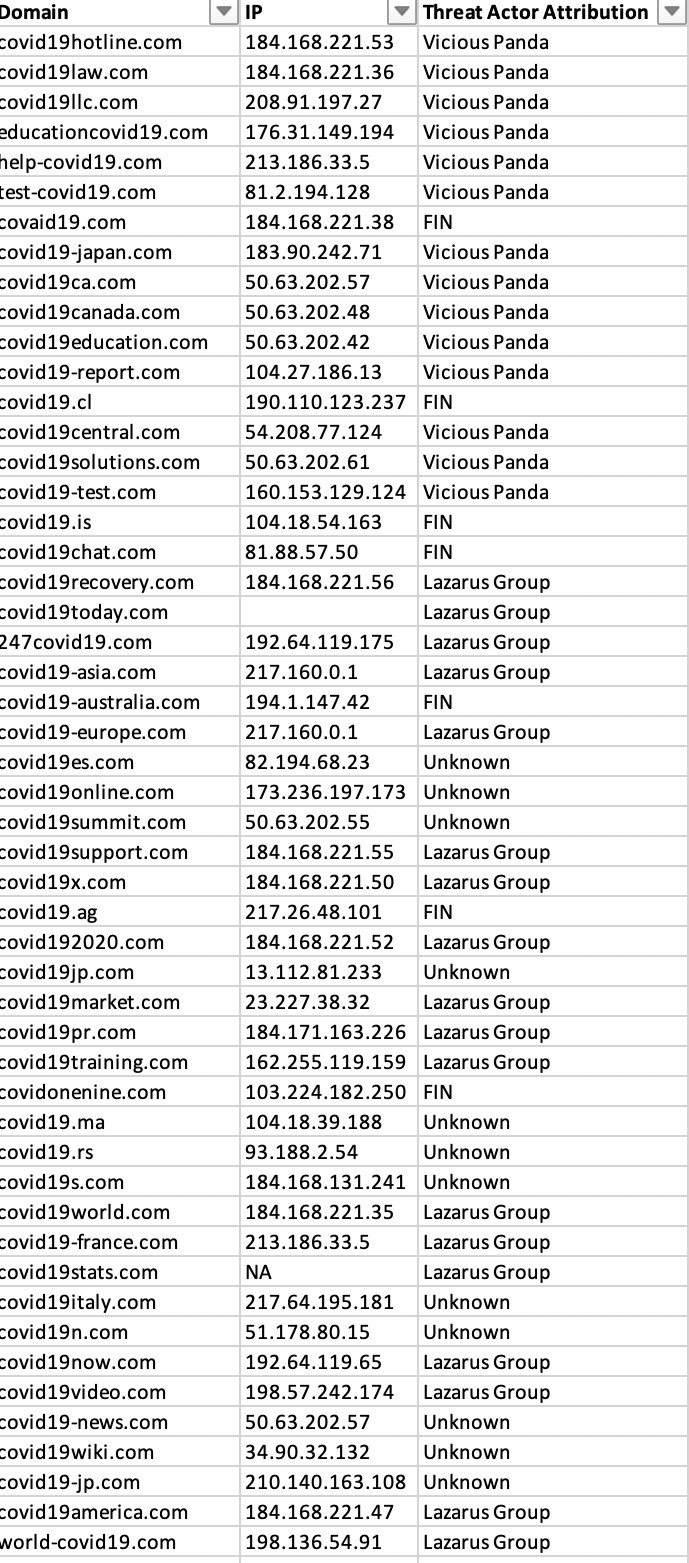
We analysed 14,649 COVID-19 related domain names, of which at least 8 per cent were associated with Vicious Panda (Chinese), 11 per cent Lazarus Group (North Korean), and 6 per cent FIN Group (Russian). These are known state-sponsored or affiliated groups.
There are over 124,600 domains registered with COVID-related keywords such as “COVID-19,” “COVID,” “Corona,” “CVD-19,” “C-Virus,” “MASK,” “C-COVID,” “WUHAN,” “HYDROXYC,” “KIT” and “HYDROXYCHLORO.”
The pandemic has triggered a response from state actors not quite seen before. These well-funded, well-oiled, cyber-war machines have jumped into the fray, maximizing the crisis in their efforts to achieve geopolitical supremacy.
By researching the hacker groups, we have seen their modus operandi and the objectives driving the many campaigns.
The COVID-19 pandemic has triggered many changes in the cyber-crime world. Criminals are fast adapting their attack methods and weaponizing the coronavirus. The defence paradigm of cybersecurity practitioners needs to shift quickly to impede these attackers. Cyberthreats have gained momentum over the course of three months with the level of creativity and ingenuity not quite seen before. It is time for defenders to understand threats and risks coming from outside the wire.