


By CYFIRMA Research
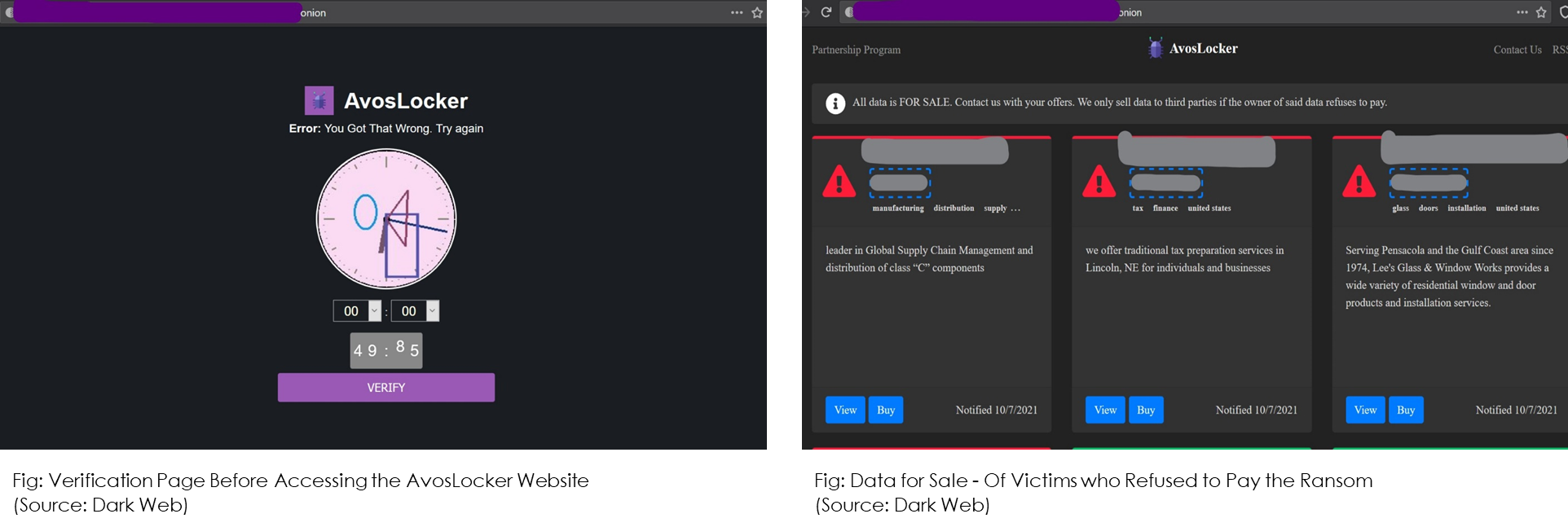
The world of ransomware double-extortion schemes is changing. The extortion model, which started back in 2019 by the operators of the Maze ransomware group, is now being improvised into an even more profitable money-making model. AvosLocker, a RaaS (ransomware-as-a-service) group, has revamped its website by creating a system through which they plan to auction data of the victims who refuse to pay the ransom.
Typically, in a double-extortion ransomware model, if a victim does not pay the ransom, threat actors release sensitive files for free on the dark web through “leak sites”. But by adding the auction feature, AvosLocker is changing the landscape of this type of ransomware attack.
Recently, a report quoted AvosLocker among three other emergent ransomware groups which have the potential to create havoc in the cyber world with their targeted attacks.
The modus operandi this ransomware group starts with data encryption and moves on to adding its own extension “GET_YOUR_FILES_BACK.txt” to each of the folders having these encrypted files. Based on the discussions on dark web forums, CTI observes that the group is looking for affiliates, at the same time just like its competitors AvosLocker does provide technical support to its victims which providing the decryption tool.
While a small section of the threat intelligence fraternity believes that given that AvosLocker carries less than 10 attacks in a week and thus the auction feature should be taken lightly; we can not deny the fact that the group has launched some major attacks in Belgium, Spain, Lebanon, UAE, UK, and the USA.
Prioritize resources (based on classification, criticality, and business value) and understand the true scope and impact of a potential ransomware event. It is an important factor in contingency planning for future ransomware events, emergency responses, and recovery actions allowing an organization to prioritize the response and recovery activities.
Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in the organization’s cloud and local environments.
Consider using security automation to speed up threat detection, improved incident response, increased visibility of security metrics, and rapid execution of security checklists.
Employ User and Entity Behavior Analytics (UEBA) in tracking, collecting, and analyzing user and machine data to detect threats within an organization.
Implement least privilege access in the system to locations that could potentially have critical information and be targeted by ransomware.