



The following list contains recent campaigns observed by CYFIRMA Threat Intelligence (CTI) that are attributed to the MISSION2025 and or its affiliates last seen in 2022.
• C Guard
• Vision2025
• UNC038
• UNC041
• Think pocket
• UNC036
• Uplift19
• Slow Walker
• UNC026
• Bupa Street
• UNC033
• UNC044
• UNC032
• JQC18
These recent campaigns are tracked by CYFIRMA and believed to be active during following time frame.
• C Guard (Jun 19, 2020-May 15, 2022)
• Vision2025 (Oct 31, 2017-May 14, 2022)
• UNC038 (Jan 30, 2022-May 10, 2022)
• UNC041 (Feb 10, 2022-May 10, 2022)
• Think pocket (Aug 21, 2021-Apr 28, 2022)
• UNC036 (Jan 30, 2022-Apr 28, 2022)
• Uplift19 (Jul 31, 2020-Apr 27, 2022)
• Slow Walker (Dec 1, 2020-Apr 24, 2022)
• UNC026 (Mar 15, 2020-Apr 23, 2022)
• Bupa Street (Nov 17, 2020-Apr 18, 2022)
• UNC033 (Dec 19, 2021-Apr 18, 2022)
• UNC044 (Feb 25, 2022-Apr 1, 2022)
• UNC032 (Dec 19, 2021-Feb 14, 2022)
• JQC18 (Jan 1, 2021-Feb 2, 2022)
Out of the 14 campaigns observed by CTI this year – attributed to MISSION2025 – most campaigns were targeted at multiple counties across the globe. Almost all the campaigns were targeted at three or more nation states and not a single campaign observed by CTI appeared to target single specific nations.
The below figure illustrates all the counties which were targeted in these campaigns.
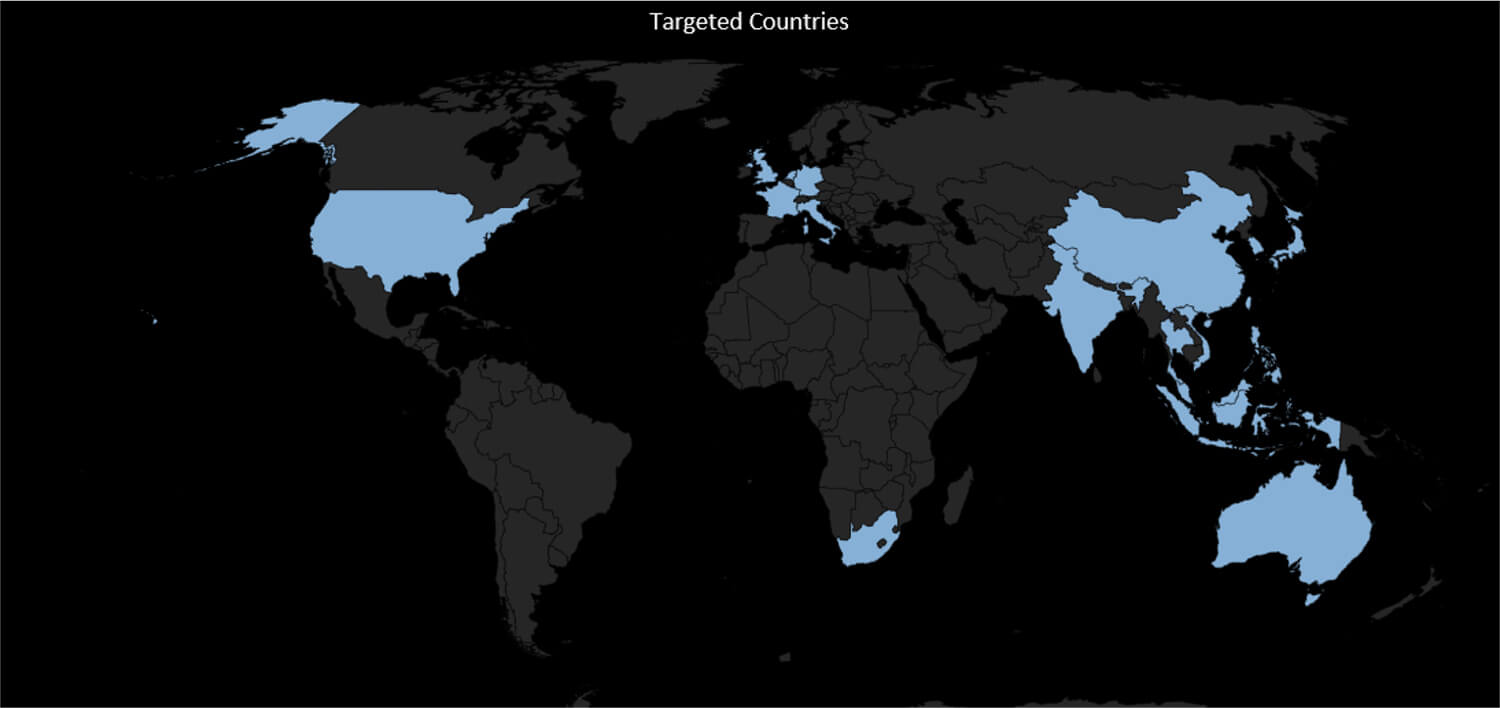
The following figure illustrates the targeted countries which were subject to the MISSION2025 campaigns.
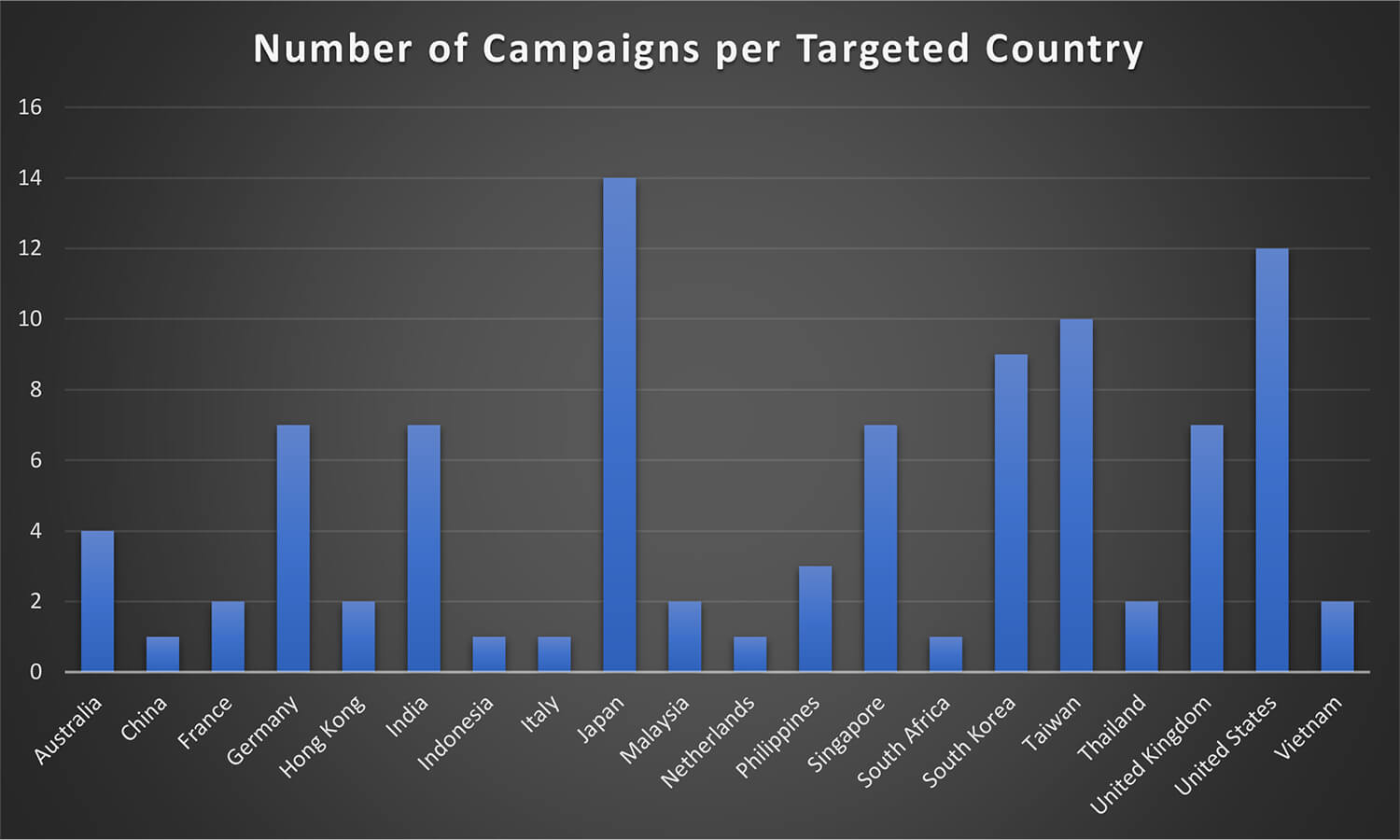
The United States and Japan have been the most favourable targets for MISSION2025 and were targeted in all the 12 campaigns respectively out the total 14 campaign. Countries like Taiwan and South Korea – while not at the top – remain to be of particular interest to the this group and also featured in multiple campaigns.
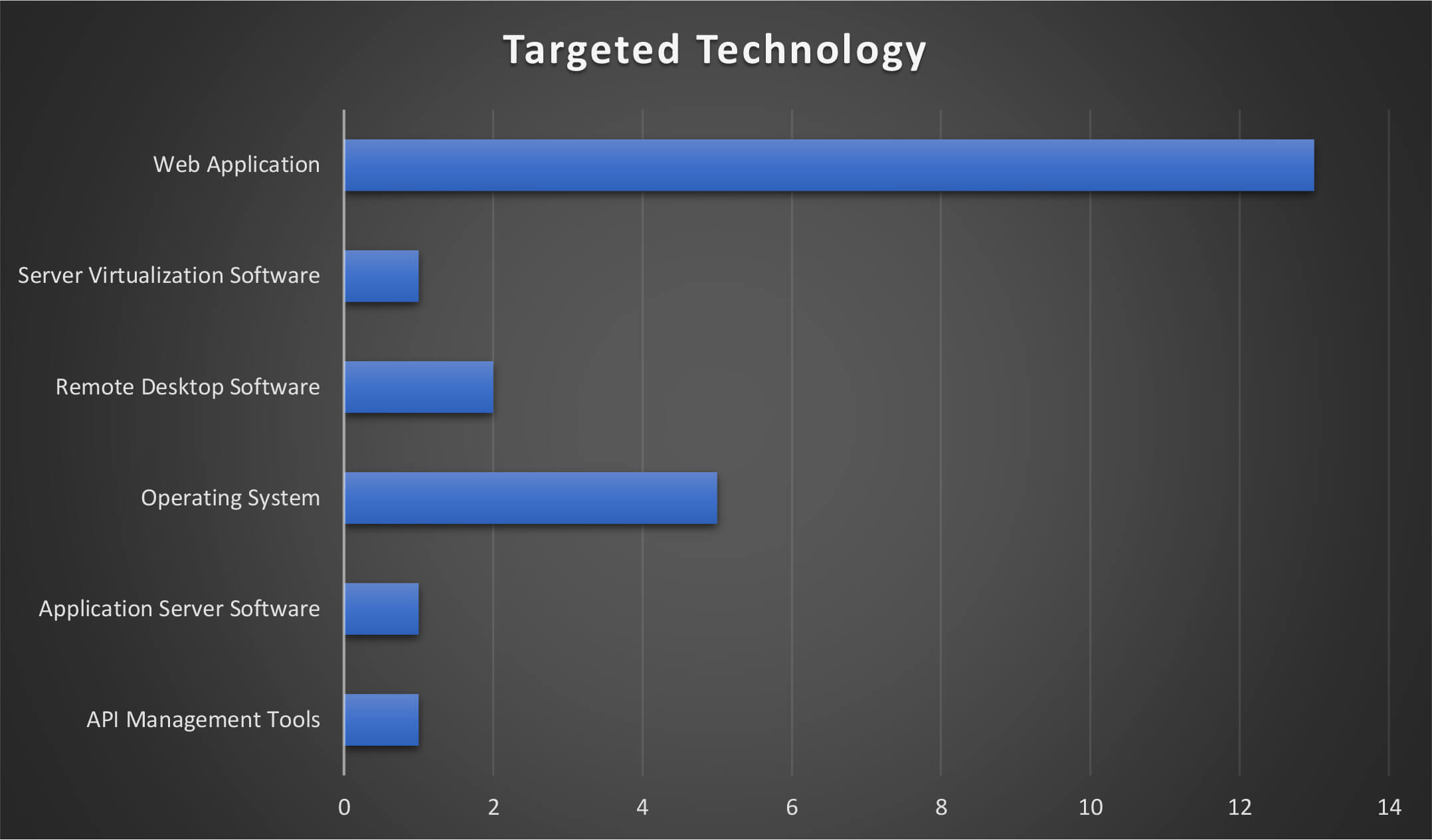
The MISSION2025 leveraged vulnerabilities & exploits in Application Server Software, Web Application, Operating System, Server Virtualization Software, API Management Tools, Remote Desktop Software to infiltrate the network and systems of potential victims.
The below figure illustrates the technologies that were targeted by the threat actor group during these campaigns. From the trends, it can be observed that exploiting weaknesses in web application-related software and products is the most favoured method by the MISSION2025. In addition, attempts to exploit remote access solutions and virtualization have been observed.
From the campaign observed by CTI in 2022, MISSION2025 attacked organizations from more than 40+ industry verticals. The targeted list of industries includes:
• Aerospace & Defense
• Auto Components
• Automobiles
• Aviation infrastructure
• Banks
• Commercial Services & Supplies
• Communications Equipment
• Construction
• Construction & Engineering
• Construction Materials
• Diversified Financial Services
• Electronic Equipment
• Energy Equipment & Services
• Entertainment
• Food & Staples Retailing
• Gas Utilities
• Government
• Health Care Equipment & Supplies
• Health Research
• Hotels
• Housing
• Industrial Conglomerates
• Infrastructure Development
• Instruments & Components
• Insurance
• Interactive Media & Services
• Internet & Direct Marketing Retail
• IT Services
• Large Equipment Making Companies
• Media
• Metals & Mining
• Multiline Retail
• Oil Gas & Consumable Fuels
• Optical Sensor
• Professional Services
• Railways
• Restaurants & Leisure
• Software
• Storage & Peripherals
• Technology
• Technology Hardware
• Telecommunication
• Trading Companies & Distributors
• Transportation Infrastructure
• Wireless Telecommunication Services
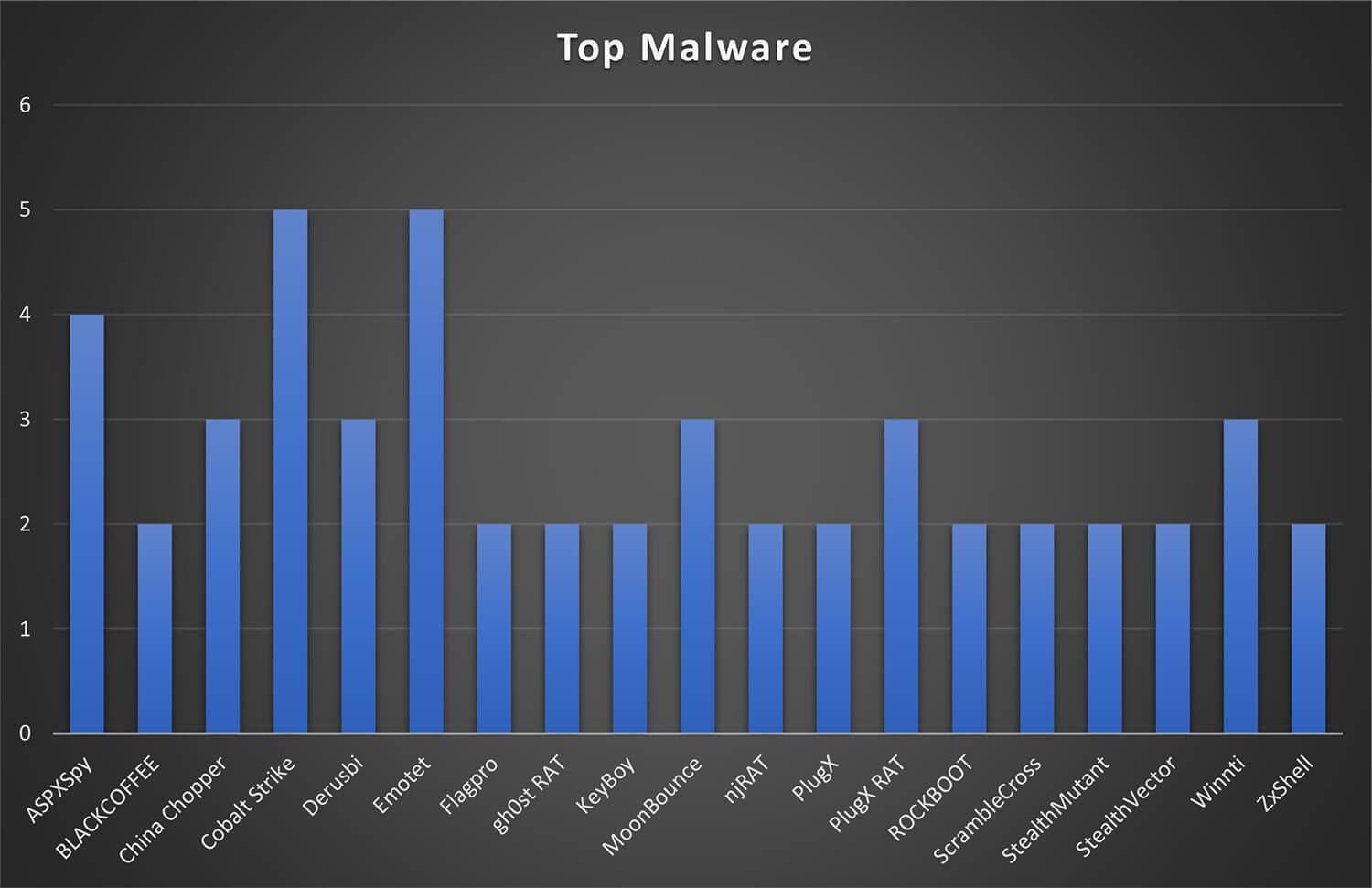
Below is the list of all the malware used by MISSION2025 in their campaigns. Interestingly, the threat actor group has used a single malware in entire campaign – examples include UNC026 campaign used Urnsif, and in Bupa Street campaign the Emotet malware was used.
A complete list of malware observed by CYFIRMA during these campaigns is as follows:
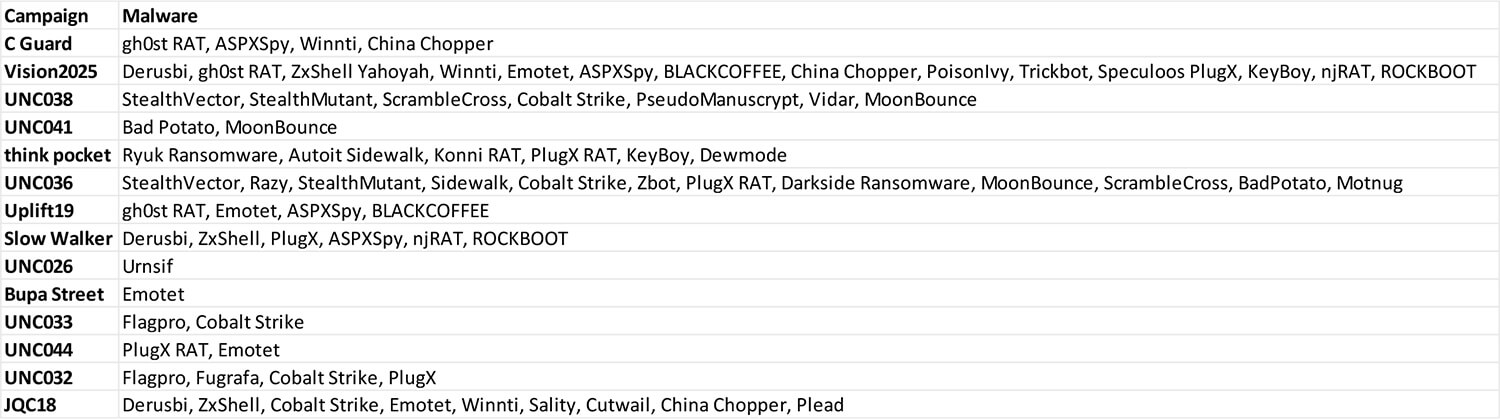
While numerous malware was used by the MISSION2025 in these campaigns, the malware namely Cobalt Strike, Emotet, and ASPXSpy were the most observed by CTI.
Alias: APT 41, APT-41, APT41, BARIUM, Gref, IQGRABBER, Mana Mr. StealYoShoes, PassCV, SparklingGoblin, UNC78, UNIT2025, Winnti, Winnti Umbrella Group
Origin: China
Description: MISSION2025 is suspected to be a Chinese state-sponsored threat actor, possibly working for the Chinese government. The threat actor is believed to be active since at least 2012. It is suspected of executing various campaigns against organizations in multiple industries such as Automotive, Retail, Healthcare, Energy, Hi-Tech, Media, Finance, Healthcare, Telecom, Supply Chain, Travel, etc. The threat actor group is believed to target nations such as the US, UK, Japan, India, France, Italy, Switzerland, Turkey, South Africa, South Korea, Hongkong, Thailand, Myanmar, etc. with the intent of financial gains and/or espionage purpose.
Targeted Countries: Brazil, France, Germany, India, Italy, Japan, Kazakhstan, Myanmar, Netherlands, Pakistan, Province of China, Republic of Korea, Russia, Singapore, South Africa, Taiwan, Thailand, Turkey, United States of America, Cambodia
Targeted Industries: Aviation, Cryptocurrency, Education, Energy, Finance, Gaming, Government Entities, Healthcare, Hi-Tech, Manufacturing, Media, Military, Pharmaceuticals, Retail, Software Development, Supply Chain, Telecommunications, Travel, Automotive
Tools: The group has been known to utilize the following tools in their attacks chain:
LOWKEY etc. RATs such as GH0ST””, Meterpreter, BlackCoffee, MessageTap, Living off the Land, Crackshot, EASYNIGHT, Derusbi, HDRoot, FRONTWHEEL, XDOOR, ASPXSpy, DIRTCLEANER, TERA, HKDOOR, X-DOOR etc. Credential Stealing malware such as ACEHASH””, BIOPASS RAT, Cobalt Strike, HighNote, PlugX, pwdump, Barlaiy, LIFEBOAT, Mimikatz, POTROAST, DOWNTIME, Jumpall, WIDETONE, Skip-2.0, China Chopper, RedXOR, ZXShell, COLDJAVA, CROSSWALK, GearShift, NTDSDump, ROCKBOOT, WINTERLOVE, DEADEYE, ADORE.XSEC, PipeMon, TIDYELF, PACMAN, certutil, ShadowPad Winnti, xDll, HIGHNOON, LATELUNCH, SAGEHIRE
Malware: The group has been known to utilize the following malware in their attacks chain: “China Chopper, Speculoos Backdoor, ASPXSpy, Winnti, ROCKBOOT, njRAT, ZxShell, gh0st RAT, Derusbi, MoonBounce, BLACKCOFFEE”
Motive: CYFIRMA believes that MISSION2025 group is a state-sponsored and financially motivated threat group, as they have been targeting global companies in multiple industries in the past and possibly could have expanded their target base to other industries. They may have attempted to implant trojans and backdoors to steal sensitive information and are primarily motivated to carry out cyber-espionage campaigns. These campaigns could be carried out to assist the local Chinese companies as part of Made in China 2025 vision with IP, Trade Secrets, and Blueprints, with the possible intent of either Information Exfiltration, Corporate Espionage, or Financial Gains via sale across the Deep/Dark web.
Recent Activity:
The threat actor has been suspected of carrying out ‘Operation CuckooBees’ to deploy a previously undocumented malware strain called DEPLOYLOG along with new versions of their known malware, including Spyder Loader, PRIVATELOG, and WINNKIT. The attackers leveraged the Windows CLFS mechanism and NTFS transaction manipulations which provided them with the ability to conceal their payloads and evade detection by traditional security products. The intent of the threat actor in this campaign seems to be cyberespionage and intellectual property theft.
Link: https://www.cybereason.com/blog/operation-cuckoobees-a-winnti-malware-arsenal-deep-dive#iocs
MITRE ATT&CK TTPs
10TA0009: CollectionT1560.001: Archive Collected Data: Archive via Utility
T1005: Data from Local System
T1056.001: Input Capture: Keylogging11TA0011: Command and ControlT1071.001: Application Layer Protocol: Web Protocols
T1071.002: Application Layer Protocol: File Transfer Protocols
T1071.004: Application Layer Protocol: DNS
T1568.002: Dynamic Resolution: Domain Generation Algorithms
T1008: Fallback Channels
T1105: Ingress Tool Transfer
T1104: Multi-Stage Channels
T1090: Proxy
T1102.001: Web Service: Dead Drop Resolver12TA0040: ImpactT1486: Data Encrypted for Impact
T1496: Resource Hijacking
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | TA0042: Resource Development | T1588.002: Obtain Capabilities: Tool |
| 2 | TA0001: Initial Access | T1190: Exploit Public-Facing Application T1133: External Remote Services T1566.001: Phishing: Spearphishing Attachment T1195.002: Supply Chain Compromise: Compromise Software Supply Chain T1078: Valid Accounts |
| 3 | TA0002: Execution | T1059.001: Command and Scripting Interpreter: PowerShell T1059.003: Command and Scripting Interpreter: Windows Command Shell T1059.004: Command and Scripting Interpreter: Unix Shell T1203: Exploitation for Client Execution T1053.005: Scheduled Task/Job: Scheduled Task T1569.002: System Services: Service Execution T1047: Windows Management Instrumentation |
| 4 | TA0003: Persistence | T1197: BITS Jobs T1547.001: Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder T1136.001: Create Account: Local Account T1543.003: Create or Modify System Process: Windows Service T1546.008: Event Triggered Execution: Accessibility Features T1133: External Remote Services T1574.001: Hijack Execution Flow: DLL Search Order Hijacking T1574.002: Hijack Execution Flow: DLL Side-Loading T1574.006: Hijack Execution Flow: Dynamic Linker Hijacking T1542.003: Pre-OS Boot: Bootkit T1053.005: Scheduled Task/Job: Scheduled Task T1078: Valid Accounts |
| 5 | TA0004: Privilege Escalation | T1547.001: Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder T1543.003: Create or Modify System Process: Windows Service T1546.008: Event Triggered Execution: Accessibility Features T1574.001: Hijack Execution Flow: DLL Search Order Hijacking T1574.002: Hijack Execution Flow: DLL Side-Loading T1574.006: Hijack Execution Flow: Dynamic Linker Hijacking T1055: Process Injection T1053.005: Scheduled Task/Job: Scheduled Task T1078: Valid Accounts |
| 6 | TA0005: Defense Evasion | T1197: BITS Jobs T1480.001: Execution Guardrails: Environmental Keying T1574.001: Hijack Execution Flow: DLL Search Order Hijacking T1574.002: Hijack Execution Flow: DLL Side-Loading T1574.006: Hijack Execution Flow: Dynamic Linker Hijacking T1070.001: Indicator Removal on Host: Clear Windows Event Logs T1070.003: Indicator Removal on Host: Clear Command History T1070.004: Indicator Removal on Host: File Deletion T1036.004: Masquerading: Masquerade Task or Service T1036.005: Masquerading: Match Legitimate Name or Location T1112: Modify Registry T1027: Obfuscated Files or Information T1542.003: Pre-OS Boot: Bootkit T1055: Process Injection T1014: Rootkit T1218.001: Signed Binary Proxy Execution: Compiled HTML File T1218.011: Signed Binary Proxy Execution: Rundll32 T1553.002: Subvert Trust Controls: Code Signing T1078: Valid Accounts |
| 7 | TA0006: Credential Access | T1110.002: Brute Force: Password Cracking T1056.001: Input Capture: Keylogging T1003.001: OS Credential Dumping: LSASS Memory |
| 8 | TA0007: Discovery | T1083: File and Directory Discovery T1046: Network Service Scanning T1135: Network Share Discovery T1016: System Network Configuration Discovery T1049: System Network Connections Discovery T1033: System Owner/User Discovery |
| 9 | TA0008: Lateral Movement | T1021.001: Remote Services: Remote Desktop Protocol T1021.002: Remote Services: SMB/Windows Admin Shares |
The MISSION2025 has been known to be linked to the Chinese government and working in alignment with their political and economic goals to target organizations and exfiltrate sensitive information. CTI suspects the MISSION2025 will likely continue collaboration with other threat actor groups to meet their objectives. In the past, it is suspected Chinese state-sponsored threat actor groups are continuously targeting strategically essential countries associated with their “Belt and Road” initiative – and opposing China in the South China Sea. It may be possible that with the help of state-sponsored hackers, China could retaliate and launch cyber-espionage activities against Quad nations.
With China’s growing influence across the world, its efforts to maintain bilateral relations, and pursuance of partnership in support of its Belt and Road Initiative, researchers have assessed that the Chinese threat actor groups will continue to target organizations to gain new insights to achieve objectives such as economic espionage or for intelligence-gathering purposes.
Page Break