



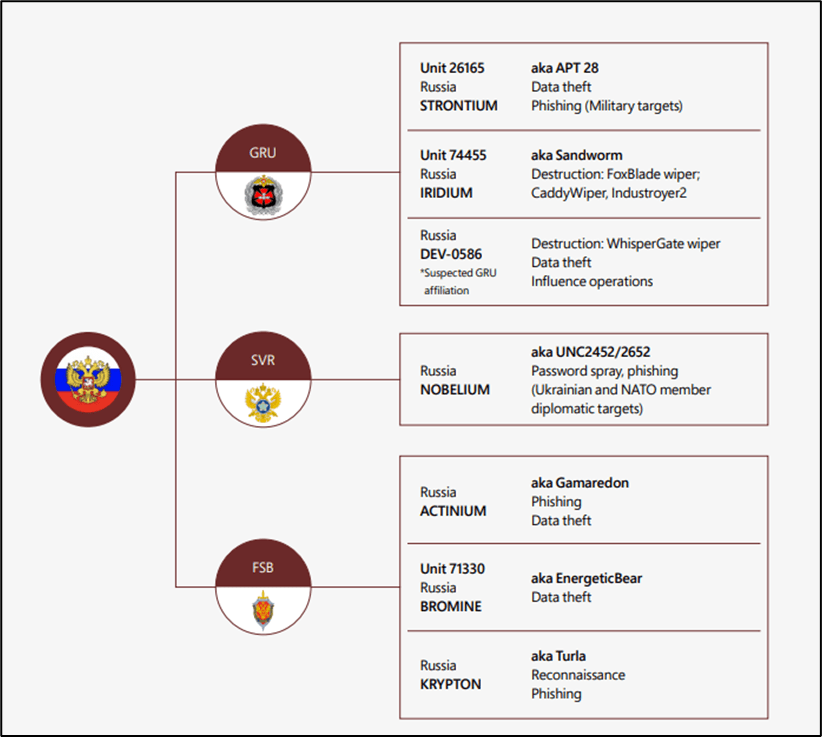
In the light of the ongoing Russian invasion of Ukraine, Microsoft in a report stated that at least six Russian-linked threat actor groups were observed launching attacks against Ukrainian systems just before the invasion.
Microsoft saw more than 237 operations that include ongoing destructive attacks which threaten civilian welfare. The destructive attacks also include espionage and intelligence operations, degrading systems of Ukrainian institutions, seeking to disrupt public access to reliable information and critical life services, and trying to tremor the people’s confidence in leadership. A limited set of espionage activities have also been targeted at NATO member states and some disinformation operations have also been observed.
Source: Surface Web
The destructive malware tracked by researchers include: WhisperGate / WhisperKill, FoxBlade aka Hermetic Wiper, SonicVote aka HermeticRansom, CaddyWiper, DesertBlade, Industroyer2 Lasainraw aka IssacWiper, FiberLake aka DoubleZero.
Due to the dynamic nature of the conflict, a level of uncertainty will be introduced, and as military action carry on, threat actor groups with a vested interest in the conflict are likely to operate under ever increased requirements. They would be playing an essential role in filling out gaps in critical intelligence gathering and tasked with specific tactical objectives. These cyber operations are also likely to, if not impact then influence the cybersecurity landscape globally.
The cyber operations of Russian threat actor groups are following the footsteps of Russian military actions, therefore, cyberattacks are likely to get escalated as the conflict goes on. Moreover, Russian threat actor groups may also expand their attack surface to target countries that are lending a helping hand to Ukraine to fight back the Russian aggression.
Researchers reported that an APT group linked to China’s People’s Liberation Army Strategic Support Force (PLA SSF), named Curious Gorge, is targeting Russian government agencies. Researchers warn that an increasing number of threat actors are using the war as a lure in their attacks. It is also being observed that threat actors are increasingly targeting organizations in the critical infrastructure.
Curious Gorge, a group researchers attribute to China’s PLA SSF, has remained active against the government, military, logistics, and manufacturing organizations in Ukraine, Russia, and Central Asia. In Russia, long-running campaigns against multiple government organizations have continued, including the Ministry of Foreign Affairs. Over the past week, the researchers identified additional compromises impacting multiple Russian defense contractors and manufacturers and a Russian logistics company.
It was also observed that the Russia-linked APT28 (aka Fancy Bear) cyberespionage group is targeting users in Ukraine with a new variant of a .Net malware distributed via email attachments inside of password-protected zip files (ua_report.zip). The malware can steal cookies and saved passwords from Chrome, Edge, and Firefox browsers.
First observed in July 2021, the BlackByte is a RaaS that has similarities with other ransomware groups such as LockBit 2.0 and prefers avoiding Russian targets. The BlackByte operators are known to exploit ProxyShell vulnerabilities to gain a foothold into corporate networks.
Similar to other ransomware groups, BlackByte also leverages double extortion techniques as part of its attacks. They use a name-and-shame approach using a. onion dedicated leak site where they publish stolen victim data.
Researchers have observed multiple variants of BlackByte ransomware including Go and .NET variants as well as one variant being written in a mix of both Go and C programming languages. These variants employ various obfuscation and anti-debugging features. The ransomware also has worm-like capabilities allowing operators to increase the scope of the attack with little effort.
IoT security researchers are warning that a popular library for IoT products is vulnerable to DNS cache poisoning attacks. The vulnerability exists for at least 10 years. They discovered that predictable, incremental transaction identifiers (IDs) in DNS response and requests are being generated in DNS implementation of uClibc and uClibc-ng C libraries that are used in numerous popular IoT products. The uClibc library, known to be used by Linksys, Netgear, Axis, and some Linux distributions was stopped being maintained in 2012. The list of vulnerable devices has been kept private due to the bug being unpatched, however, the devices they tested include “a range of well-known IoT devices running the latest firmware versions with a high chance of them being deployed throughout all critical infrastructure.”
The primary risk of DNS-cache poisoning attacks is that an attacker being able to poison the DNS records can forge an authentication response. It involves an attacker poisoning the DNS records to deceive a DNS client into accepting forged responses. This can be used to re-route the network traffic to attacker-controlled endpoints.
A DNS-poisoning attack can then result in Man-in-the-Middle attacks since the attacker is able to direct the network traffic to a device of their control. It would allow them to steal or tamper with data being transmitted by users.
A joint advisory issued by the U.S. and other allied cybersecurity authorities from Australia, Canada, New Zealand, and the UK detailed the top 15 routinely exploited by threat actors in 2021 as well as other frequently exploited vulnerabilities. The authorities assess threat actors aggressively leveraged the newly disclosed critical vulnerabilities in software against a broad set of targets that included public and private sector organizations globally in 2021. The threat actor targeted internet-facing systems such as email servers and virtual private network servers with exploits associated with these vulnerabilities. The top 15 routinely exploited vulnerabilities include:
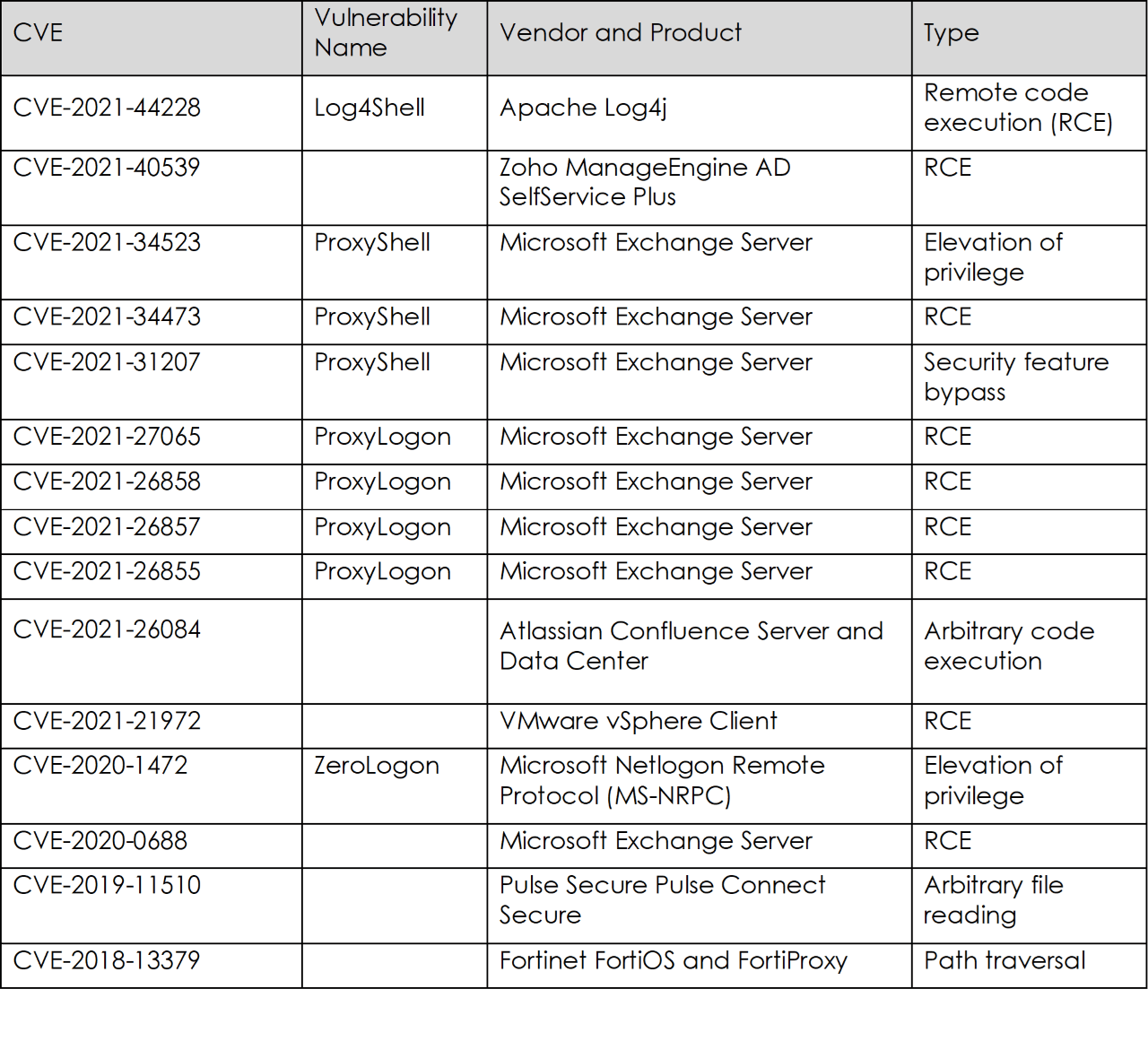
For most of these vulnerabilities, a PoC (Proof of Concept) code was made available to the public within the span of two weeks from the disclosure of the vulnerability – either by the researchers or other threat actors.
As per researchers, affiliates ransomware groups namely Hive, Conti, and Avoslocker have recently exploited vulnerabilities including Log4j, Microsoft Exchange, and Fortigate Firewall (CVE-2018-13379 and CVE-2018-13374) for securing initial access to corporate systems alongside using spear-phishing, credential abuse of Remote Desk Protocol (RDP).