


CYFIRMA’s cyber intelligence research center has discovered a potentially new Tokyo Olympics 2020 themed spear phishing and SMS/text-based smishing campaign.
Olympics events have always attracted the attention of a broad range of threat actors, ranging from the ones seeking notoriety to state-sponsored agents seeking to harm the reputation of the host nation by disrupting key infrastructure and services. Additionally, there is an increasing number of financially motivated cybercriminals who seek to profit from selling counterfeit tickets or distributing ransomware through phishing campaigns to unsuspecting recipients. Even though the 2020 Tokyo Summer Olympics is expected to be a memorable sporting and cultural display, the true convergence of sportsmanship and digital innovation, this event is increasingly attracting the participation of threat actors who also want to make their mark on one of the world’s greatest and most public event.
MOTIVATION:
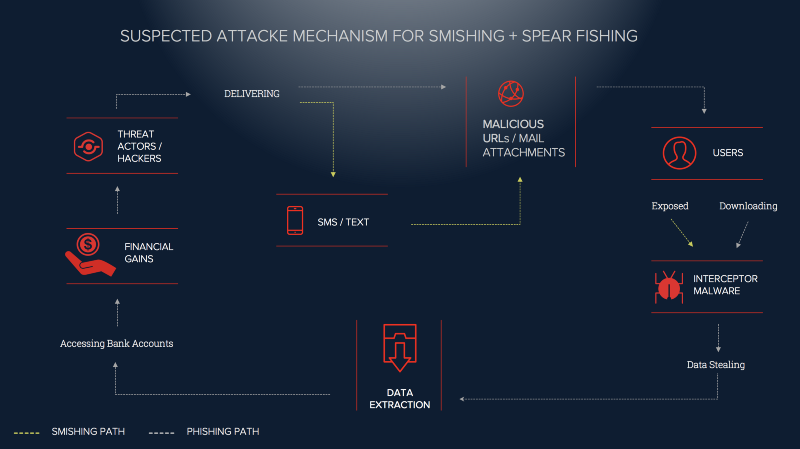
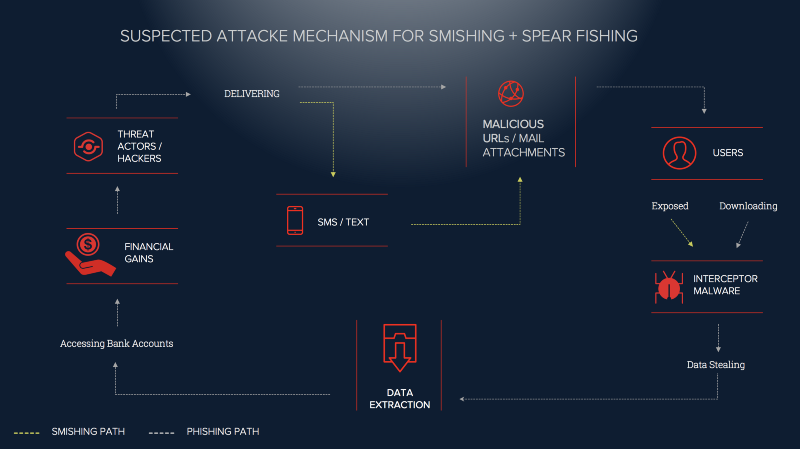
The Tokyo Olympics 2020 Themed Spear Phishing/Smishing Campaign analysis indicates that threat actors are seeking to exfiltrate data including Personal Identifiable Information and even bank login details. Financial gain appears to be the prime motive of these threat actors. Their secondary agenda, however, appears to be causing reputational damage to the host nation and specific target enterprise through successful Business Email Compromise (BEC) and conversation hijacking attacks.
SPEAR PHISHING CAMPAIGN:
Our analysis suggests that the spear phishing campaign appears to be part of a broader Business Email Compromise (BEC) and conversation hijacking attacks. As part of this campaign, we suspect threat actors intend to send customized phishing emails to targeted enterprise users, offering free tickets to the 2020 Tokyo Olympics and misleading unwitting users into clicking malicious links. Additionally, in their endeavor to ensure a higher hit rate, hackers have been orchestrating to run a false advertisement, offering a US$600 gift hamper to ‘lucky’ participants.
A significant part of the hacker discussions focused on implanting data stealing or interceptor malware executable, delivered via email attachments or downloaded through malicious links clicked by the unsuspecting user.
Following are the details of the Spear Phishing Campaign Mails:
・ Fake-Sender Email Addresses which might be used to send malicious phishing email:
wintickets@tokyo20yelo[.]com
freetokyo2020@oci-tokyo2020[.]com
event2020live@gmail[.]com
freetickets[.]tokyo20@outlook[.]com
freetickets[.]tokyo20@gmail[.]com
・ To: Employee/contractor in the organization
・ Subject: Free Tickets To Tokyo Olympics (Fun) or Free Tickets Olympics
・ Potential fake URLs which might be leveraged by attackers as part of the spear phishing emails to dupe users:
www[.]kennicwa-tokyo2020.io/bolde12[.]exe
www[.]ticket-sales.com/index[.]htm
www[.]20gamestokyo[.]net/emp[.]asp
http[:]//livetokyo2020[.]net/media-ch[.]asp
http[:]//freeloaderstokyo[.]com/fill-form[.]html
Potential malicious payload, which can search the compromised end-point for sensitive data and exfiltrate to the remote hacker-controlled Command and Control Server.
Suspected Outlook 2013 and 2016 address book stealing malware
363866ac0141d2f0d6e38703ec085c6c
2139c711f37a62a60f4d7e7d23b84168
・ Suspected Interceptor malware
0b262b2d4620be8362ce951b9a6371dd
SMS/TEXT BASED SMISHING CAMPAIGN
CYFIRMA’s cyber intelligence research center has also observed threat actors discussing malicious links being delivered to users via a SMS/Text based smishing campaign. Cyber-criminals are suspected of delivering fake URLs to unsuspecting users. These URLs are offering the same free tickets to Tokyo Olympics 2020 or a chance to win US$600 gift hampers upon completion of registration post clicking these URLs.
Following are the details of the Smishing Campaign Messages:
・ SMS Details: Unknown at this stage
・ Originated from: Unknown at this stage
・ Potential fake URLs which might be leveraged by attackers as part of the smishing campaign to dupe users:
www[.]ticket-sales[.]com/index[.]htm
http[:]//freeloaderstokyo[.]com/fill-form[.]html
http[:]//tokyogames[.]net/contact-bankdetails[.]htm
http[:]//2020tokyogame[.]cn/gtui/gifthamp[.]js
MITIGATION MEASURES:
・ Block IOCs (Indicators of Compromise) such as malicious URLs, IP Addresses, SHA fingerprint, Hashes under firewalls, proxies, endpoint, spam and phishing security control
・ Apply appropriate anti -phishing and spam control with stringent email policy
・ Do not open emails or URLs from untrusted sources. Always verify sender email address before opening any emails coming from a source outside the organization
・ Be careful while clicking on the link mentioned in the emails/SMS.
・ Establish a Cybersecurity Awareness and Training (CSAT) Program and run regular checks, educate employees to download applications from trusted Appstore only
・ Implement Network Segmentation-Limiting communication between services and systems on the organization network level helps contain an infection and keeps a malware or a persistent threat from spreading
・ Configure Anti-Virus/IDS (Intrusion Detection System) repositories with the identified hash signatures associated with the threat to protect all endpoints
・ Build an APT-IR strategy, which is agile and proactive, keeping in mind business goals and priorities