


Why is the NIST worried about quantum computing when it’s going to take some time for it to become a reality? How is quantum computing disrupting the world of cyber? Does China lead the quantum technology race?
Traditional computers perform calculations with standard ‘bits’ that exist in states of 0 or 1, whereas quantum computers use ‘qubits.’ These quantum analogs of the ‘bit’ exist in a superposition of all possible states, allowing for a significant, even exponential, advantage in computing capabilities. Bits function similarly to switches in that they can be either up or down, on or off. Qubits, on the other hand, are more like dimmer dials in that they can have an infinite number of different values between on and off, along with other computational functionality.
Quantum computing is fundamentally different from the laptops and smartphones on which we depend on today. Instead of ever smaller transistors, quantum machines operate on particle physics principles and excel at solving complex statistical problems with multiple variables. Even though quantum computing is not a complete reality today, it is capable of adding significant value to areas like medical research, artificial intelligence, weather forecasting, military affairs, and cyber security. Ironically, it also creates a significant cybersecurity threat, potentially requiring a change in how we encrypt our data.
Recognizing this fact, many private sector companies and nation-state research institutions have begun to invest in R&D. Many experts in this field believe that the advancement of quantum computing technologies will not follow the typical smooth progression curve. Companies and countries that have begun to invest in and develop plans to achieve quantum supremacy in their operations have a much better chance of capitalizing on the future market during this early development phase.

Considering the potential impact of quantum computers in the future, many governmental institutes and private agencies have funded research and development in quantum computing technologies. Despite the fact that many market-ready and mature technologies, such as artificial intelligence and blockchain, exist, quantum computing has attracted the interest of global superpowers, particularly China and the United States.
Companies in the United States such as IBM, Google, Honeywell, and Amazon are making significant investments to achieve quantum computing supremacy, whereas China has placed quantum information science at the center of its national security strategy, capturing the attention of the Chinese top leadership. China’s supreme leader Xi Jinping has emphasized the strategic importance of quantum technologies to national security, particularly cybersecurity. The “All-of-government” approach is being used by China to develop quantum technology, clearly, the nation has recognized it to be a strategic national priority.

Various available data points show that China recognizes the importance of quantum supremacy in realizing its dream of becoming a global superpower capable of displacing the United States, and believes that this competition will be a marathon, not a sprint. China has consistently funded basic and applied research in this scientific domain since the 1990s, primarily through China’s National High-Technology Research and Development Plan. Since the 11th Five Year Plan, China has made quantum computing a strategic priority (2006).
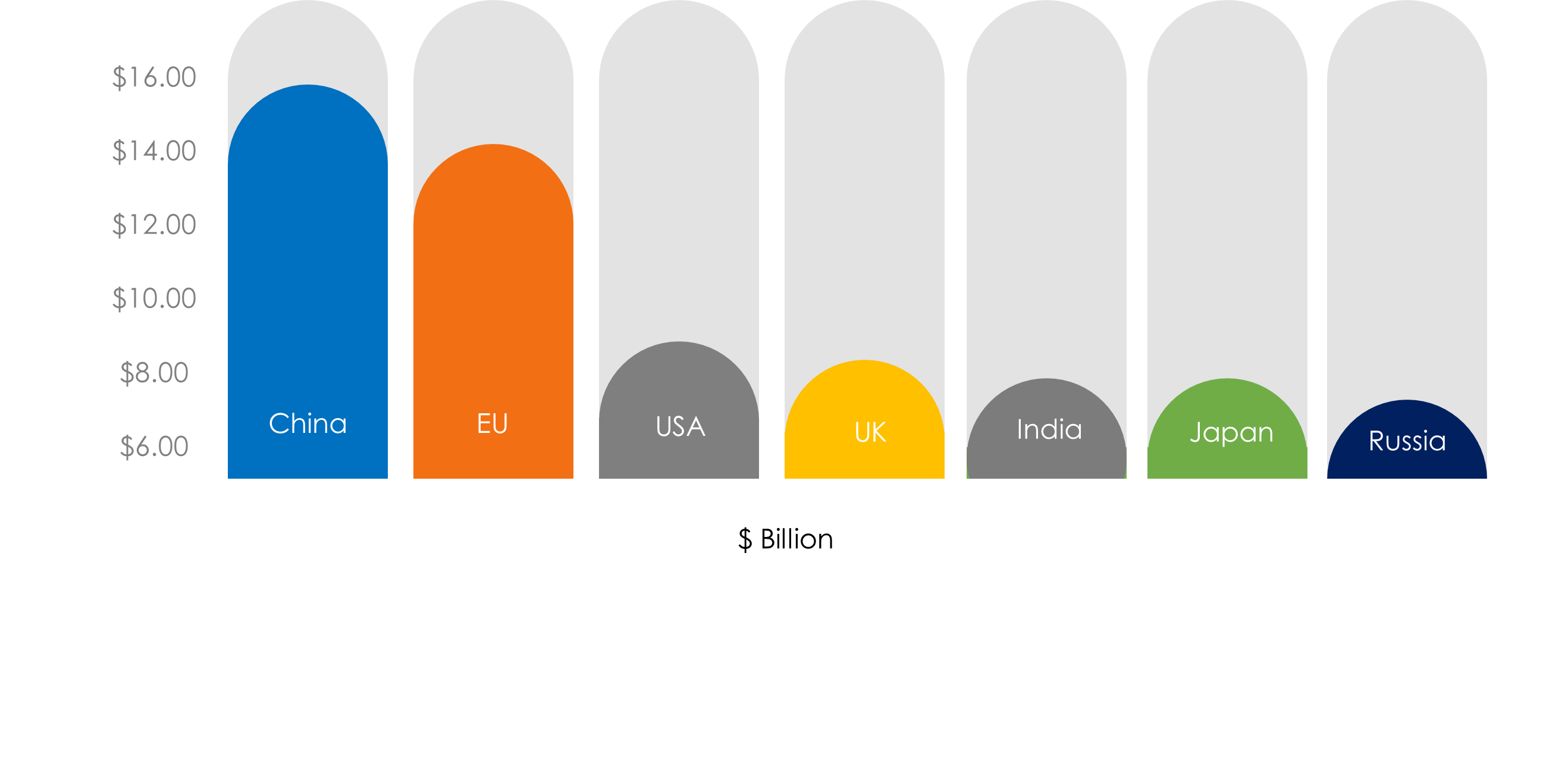
In its 14th Five Year Plan, China ranked quantum computing second only to AI as a top technology priority. Recognizing its significance, the CCP committed to ongoing funding support for Quantum Computing research and development. Around USD 15 billion in funding has been announced for leading institutions such as the National Laboratory for Quantum Information Science and the Beijing Academy of Quantum Information Sciences to develop some of the world’s top quantum research facilities.
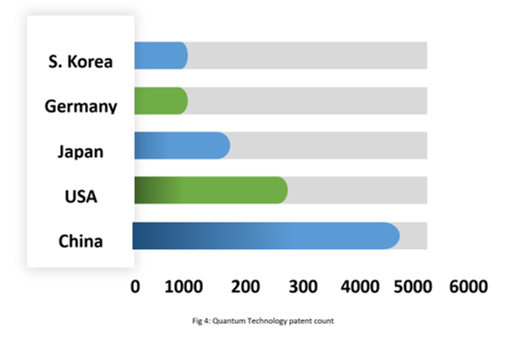
In 2015, Xi Jinping included quantum communications in his list of major science and technology projects that are prioritized for significant breakthroughs by 2030, given their importance from the perspective of China’s long-term strategic requirements.

Apart from the numerous benefits of quantum computing, there are a few negative consequences as well.

Because quantum computers can process data at an exponential rate, they pose significant cyber threats to existing cryptosystems. However, current quantum computers lack the hardware required to break this algorithm. Many applications, including web browsing, online payments, digital signatures, and email, rely heavily on asymmetric encryption schemes like the RSA algorithm. The RSA algorithm is based on traditional computers’ inability to find factors of the product of two large prime numbers. A quantum computer with 4000 qubits and 100 million gates is estimated to be required to crack a 2048-bit RSA key. Other public-key encryption schemes, such as Diffie-Hellman and ECC, are rendered ineffective in the face of a quantum computer. On the one hand, this will disrupt the encryption ecosystem; on the other hand, it will reveal potentially sensitive information from previously exfiltrated encrypted data from various historical cyber-attacks by nation-state groups and cybercriminals.

In future warfare, technological superiority over the number of soldiers in the armed forces will determine victory. Quantum sensing has the potential to be used in a variety of technologies with direct military applications. Quantum radar, in particular, can detect targets that conventional radar cannot detect, and quantum navigation uses quantum properties to create a precise form of positioning system that may eventually replace GPS. Such technologies, when combined, could be critical to China’s future military capabilities, as well as a key focus of technological competition with other rival countries such as the United States.
The realization of quantum radar, imaging, and sensing would improve domain awareness while potentially undermining rival countries’ investments in stealth technologies or even allowing submarine tracking, particularly in the South China Sea, thereby proving a strategic advantage in the geopolitical battleground. Collectively, these advancements support the Chinese People’s Liberation Army’s (PLA) continued development as a leader in these new technological frontiers of military power.
China can use cyberespionage to undermine global technology and academic organizations’ quantum research in order to quickly close technological gaps and achieve quantum computing supremacy. If China succeeds in becoming a leader in quantum computing, the leveraging of such massive computing capabilities could provide a strategic advantage, putting sensitive information systems at risk around the world, particularly in the United States and rival countries.

As China strives to become a global superpower, it has recognized the importance of quantum supremacy in that endeavor, and as a result, quantum technology has captured the attention of the Chinese leadership at the highest levels. Furthermore, the PLA is actively engaged in developing quantum technology as a strategic enabler to bridge the gap between its military capabilities and those of potential adversaries.
The PLA’s interest in quantum technology reveals its intent to use advances in quantum technology in adversarial activities. Because China is known for its offensive cybersecurity capabilities and collaboration with cybercriminals and nation-state actors, quantum supremacy by China could have a devastating impact on rival nations such as the United States and Southeast Asian countries.
In any potential conflict with China, a rival country’s use of stealth would be critical, allowing naval vessels to approach the Chinese mainland and aircraft to penetrate Chinese airspace, putting Chinese operational assets at cyber risk. As a result, quantum radar would be a hugely disruptive force in the PLA’s arsenal of anti-access/area denial or “counter-intervention” capabilities. If deployed, quantum radar could not only undermine competitors’ stealth advantages but also increase the potential costs of war by forcing them to accept higher operational risk and nullifying billions of dollars spent on stealth coating for platforms operating in the Pacific Ocean.
When China achieves quantum technology supremacy, it will gain a first-to-market advantage. This may assist China in including backdoors enabling surveillance in the technology or equipment supplied, as seen in Chinese telecommunications vendors Huawei and ZTE in the 5G wireless network equipment.
Military affairs, espionage, supply chain manipulation, and offensive cyber activities will take center stage as China strives for quantum supremacy and the status of a global superpower.

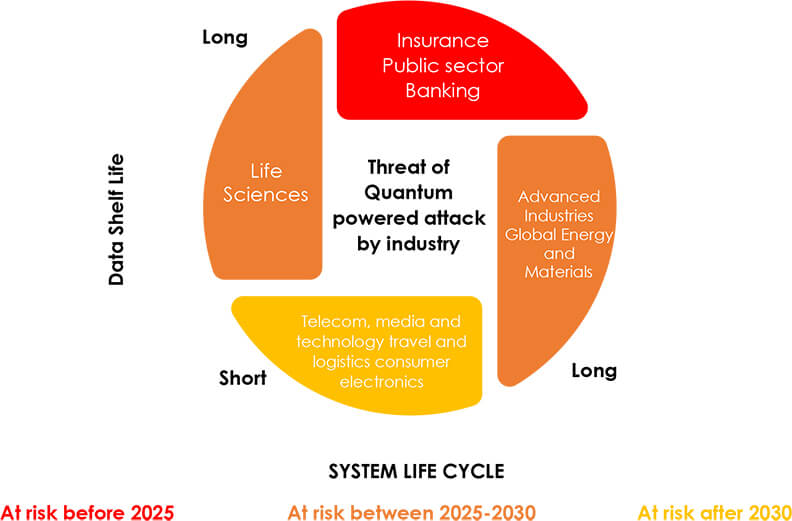
Today there is no quantum computer capable of managing the hundreds of thousands to millions of qubits needed to handle the sort of factoring that would crack current cybersecurity. But looking at the angle of a quantum computer as a strategic priority for national security, in another 10-15 years quantum computers will be a reality. They will be capable of disrupting the current cryptography ecosystem. Quantum computers in the hands of rogue nations and cybercriminals will be nothing less than a cyber disaster. In organizations that store or transmit data with long shelf life, or entities whose cybersecurity systems have a long lifecycle, the risk of quantum computing is imminent. For example, data that are being encrypted today by a quantum-vulnerable algorithm, such as RSA, can be intercepted by an adversary now, for decryption later, when the quantum computing technology is available to do so. Thus, these sectors, specifically the financial, insurance, or government sectors, must act now, by integrating post-quantum cryptography into their security infrastructure to avoid compromise of their long-term certificates or encryption keys. Scientists and forward-thinking policymakers are already working on quantum cryptography to stay ahead of critical transformation to secure sensitive data and avoid its access by cybercriminals.
NIST invited proposals and algorithms for Post Quantum Cryptography (PQC) in 2016 and released its encryption criteria and guidelines for public submissions. Initially, 69 viable candidates from around the world were submitted. NIST chose the first set of encryption tools designed to withstand an attack by a future quantum computer after careful cryptanalysis. The organization expects to have a draft standard by 2024, if not sooner, to be added to web browsers and other internet applications and systems.
Quantum computing will have an impact on everything from apps to internet search, web development, cybersecurity, and beyond. It is prudent to stay ahead of current technological trends so that when new features are released, we have the knowledge and tools needed to weather the start of the modern technological era.
If cybercriminals use quantum computing before we adopt PQC, they will be able to deduce someone’s encryption key and use it to impersonate the person, forge transactions, forge digital signatures, find and print data, and extort or disclose the harvested data.
When it comes to China’s role in quantum computing, Chinese leaders recognize quantum science and technology’s strategic potential to enhance the economic and military dimensions of national power. These quantum ambitions are inextricably linked to China’s national strategic goal of becoming a science and technology superpower. Instead of relying solely on the absorption of foreign technologies in its pursuit of indigenous innovation, China intends to achieve truly disruptive, even radical, innovation in strategic emerging technologies. Data points discussed reveal that China’s bet big on quantum computing has achieved significant milestones.