Published On : 2022-07-09
Weekly Attack Type and Trends
Key Intelligence Signals:
- Attack Type: Ransomware, Vulnerabilities & Exploits, Ransomware-as-a-Service (RaaS), Malware Implant, Data Exfiltration, Remote Code Execution (RCE), Data Leak, Social Engineering, XML External Entity Injection (XXE), Impersonation, Insecure Deserialization, Path Traversal, Potential Insider Threat
- Objective: Data Exfiltration, Unauthorized Access, Data Theft, Financial Gains, Data Encryption
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Operational Disruption
- Ransomware – Hive| Malware – YTStealer and XFiles
- Hive – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Malware – YTStealer and XFiles
- Behavior – Most of these malware use phishing and social engineering techniques as their initial attack vector. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus
Lazarus Group A Suspect in Harmony hack
Suspected Threat Actors: Lazarus Group
- Attack Type: Social Engineering, Malware Implant, Impersonation
- Objective: Unauthorized Access, Financial Gains
- Target Technology: Harmony’s Horizon Bridge
- Target Industry: IT
- Target Geography: United States
- Business Impact: Data Loss, Financial Loss, Regulatory Implications
Summary: Recently, threat actors stole approximately USD 100 million in cryptocurrency from a Blockchain company – Harmony. The incident was reported to the authorities and it is under investigation by the FBI aalongside several other cybersecurity firms. According to a blockchain security firm that published a detailed analysis of said incidents on 24 June, a bridge exploit was used on Harmony’s Horizon bridge and stolen funds were still being held in the exploiter’s address.
On June 27, the threat actors began transferring the funds (roughly USD 39 million) through the Tornado Cash mixer service to launder the stolen funds. Fortunately, these transactions were analyzed by another blockchain security firm that suspects that North Korea’s Lazarus Group may be behind this theft. Their assessment is based on the nature of the incident and subsequent laundering efforts. According to researchers “the theft was perpetrated by compromising the cryptographic keys of a multi-signature wallet – likely through a social engineering attack on Harmony team members.” These techniques have been frequented by the Lazarus Group in the past.
Insights:
- The Lazarus Group is also believed to have stolen approximately USD 2 billion in crypto assets from various cryptocurrency exchanges and DeFi services in the past.
- In April, the CISA, the FBI, and the US Treasury Department also published an advisory alerting on the use of trojanized cryptocurrency applications by the North Korean Lazarus Group to target organizations operating in cryptocurrency and blockchain industries. As suspected in the Harmony incident, the Lazarus Group make use of social engineering to trick employees into downloading and installing malicious apps which are used to gain access to the target’s computer, spread throughout the network, and steal private keys that allow them to perform fraudulent transactions emptying crypto assets from victim’s wallets.
Major Geopolitical Developments in Cybersecurity
FCC Calls for Removal of TikTok from App Stores
The commissioner of the FCC (Federal Communications Commission) Brendan Carr, called upon the CEOs of Apple and Google to remove TikTok from their app stores. In a letter dated June 24, Carr told the CEOs that “TikTok poses an unacceptable national security risk due to its extensive data harvesting being combined with Beijing’s apparently unchecked access to that sensitive data.”
In a Twitter thread the FCC commissioner pointed out security risks associated with the app including;
Excessive data collection: TikTok is said to be collecting “everything” from search, browsing histories, keystroke patterns, biometric identifiers, voiceprints, location data, draft messages, metadata, and data stored on the clipboard, including text, images, and videos. He highlighted several incidents as evidence of TikTok’s dubious data collection practices.
Links to CCP (Communist Party of China): In the letter, Carr stated that the developer ByteDance “is beholden to the Communist Party of China and required by Chinese law to comply with the PRC‘s surveillance demands.” Previously, cybersecurity researchers, privacy, and civil rights groups have also brought similar concerns to the attention.
Unclear use of collected data: TikTok appears to be one of those apps that do not abide by the clause where they must specify how they use the data being collected. In the letter, he stated, “Numerous provisions of the Apple App Store and Google Play Store policies are relevant to TikTok’s pattern of surreptitious data practices — a pattern that runs contrary to its repeated representations.”
Rise in Malware/Ransomware and Phishing
CAN Capital impacted by Hive Ransomware
- Attack Type: Ransomware, Data Exfiltration
- Target Industry: Financial Services
- Target Geography: United States
- Ransomware: Hive
- Objective: Financial Gains, Data Theft, Data Encryption
- Business Impact: Data Loss, Financial Loss, Reputational Damage
Summary: CTI observed CAN Capital, Inc. (www.cancapital.com) – provider of capital to small and medium-sized businesses – being impacted by the Hive ransomware. The ransomware group claimed CAN Capital as one of their victims by disclosing the update on their dedicated leak site HiveLeaks, on 04 July. The update also claims the encryption of the company’s data was conducted on 28 May. At the time of CTI’s observation, sample evidence of exfiltrated has been published by the ransomware group. It appears that the ransomware group is awaiting ransom negotiation and in case of non-compliance to their ransom demand, the group will likely publish all exfiltrated data on their dedicated leak site for anyone to download.
The following screenshot was observed published on the dark web:
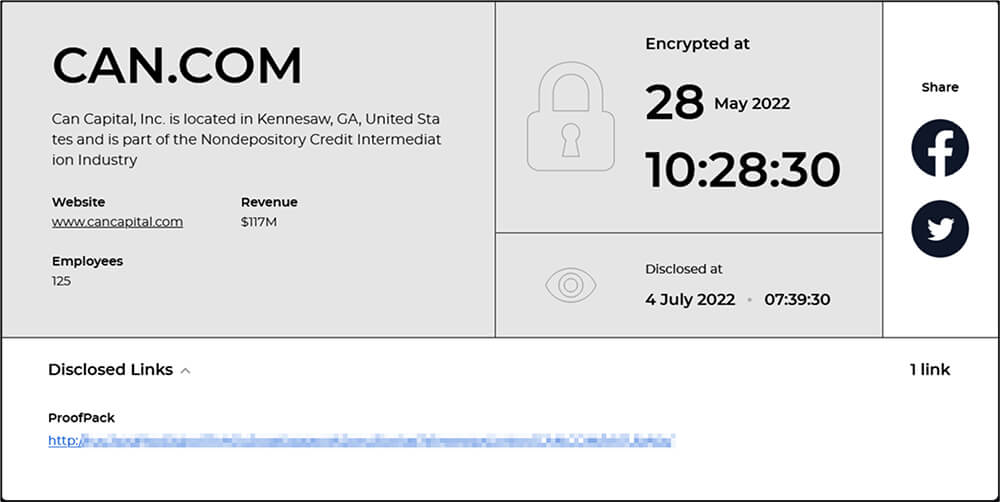
Source: Dark Web
Source: Dark Web
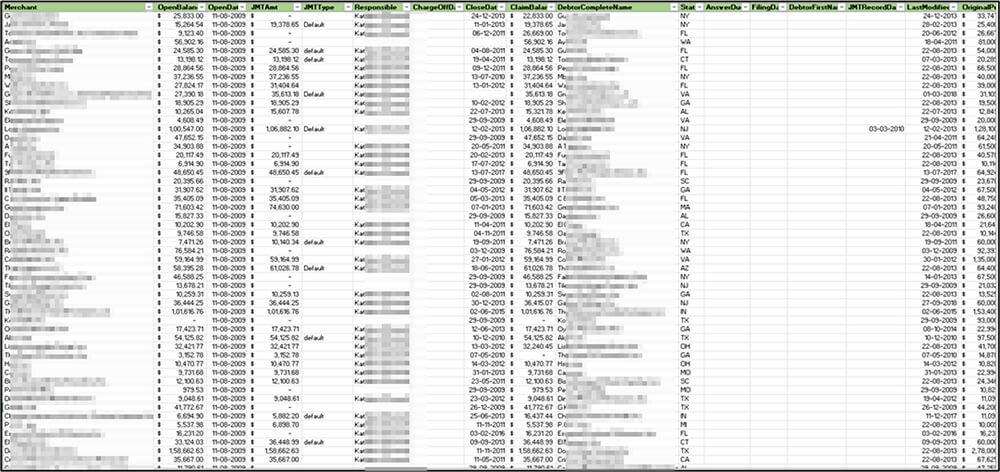
Source: Dark Web
Insights:
- The Hive ransomware was first observed in June 2021 and suspected of running as affiliate-based ransomware similar to the majority of the ransomware groups at current times. The ransomware group employs a wide array of tactics, techniques, and procedures (TTPs) in their attacks. They leverage multiple methods to compromise an organization’s networks, which include phishing emails with malicious attachments to foothold into the network and exploiting Remote Desktop Protocol (RDP) for lateral movement.
- It uses a double-extortion strategy for attacks. The attackers threaten to publish the exfiltrated data (victim data) if victims are not ready to pay the ransom.
- The ransomware operators implemented a new IPfuscation (obfuscation) technique to conceal the Cobalt strike beacon payload. The payload was disguised as an array of ASCII IPv4 addresses in the malware executable binary. Code obfuscation is a technique that helps threat actors hide the malicious code from security analysts or security software to evade detection.
- The Hive ransomware operators changed its VMware ESXi Linux encryptor to the Rust programming language to make it more difficult for security researchers to eavesdrop on victims’ ransom conversations. This feature is implemented from the BlackCat ransomware operation.
- According to the most recent report from Microsoft, the latest variant of Hive ransomware has been upgraded and received a complete overhaul. The most notable changes include code migration from GoLang to Rust programming language and the use of a more complex encryption method.
Latest Cyber-Attacks, Incidents, and Breaches
“Free UK visa” Scam on WhatsApp
- Attack Type: Impersonations, Phishing, Social Engineering
- Objective: Financial Gains, Data Theft
- Target Industry: Education, Government
- Target Technology: WhatsApp
- Target Geography: Global
- Business Impact: Data Loss, Financial Loss
Summary: Researchers have discovered a new phishing campaign on WhatsApp targeting individuals interested in working in the United Kingdom. The attackers behind the campaign send out messages that claim to be from the UK government and offer a free visa and other benefits including travel expenses, housing, accommodation, and medical facilities, to individuals who are willing to move to the UK. The scam starts by sending messages on WhatsApp in which recipients are told that the government is running a recruitment drive for over 186,000 vacancies.
If the potential victims click through, they are served a fraudulent domain impersonating UK Visas and Immigration website. This website is aimed at gathering various personally identifiable information. Regardless of what information is supplied, the free application form is automatically “approved”. The attacker then attempts to collect even more information and generate revenue by asking them to invite 15 friends or share on 5 groups on WhatsApp to make others aware of the program. In the final stage, victims are further redirected to other suspicious websites.
Insights:
- Phishing scams with the Visa theme are fairly common. A similar scam was spotted by researchers several months back where attackers attempted to dupe individuals who also wanted to work or study in the United Kingdom.
- In March this year, experts warned WhatsApp users about rising scams case on the popular platform where the UK reported a huge spike of 2000% by the end of 2021. The high growth of WhatsApp scams is attributed to organized cybercriminals groups constantly changing their methods and adapting at a rapid pace.
Vulnerabilities and Exploits
Critical Bug in ManageEngine ADAudit Plus Allows Network Takeover, Mass Data Exfiltration
- Attack Type: Vulnerabilities & Exploits, RCE, XXE, Data Exfiltration, Insecure Deserialization, Path Traversal
- Target Technology: Zoho ManageEngine ADAudit Plus
- Vulnerability: CVE-2022-28219 (CVSS score: 9.8)
- Vulnerability Type: Improper Restriction of XML External Entity Reference
- Impact: Confidentiality (High), Integrity (High), Availability (High)
Summary: The researcher detailed a critical severity security flaw in ManageEngine ADAudit Plus that allows an unauthenticated attacker to exploit XXE, Java deserialization, and path traversal vulnerabilities. This chain can also be leveraged to achieve unauthenticated remote code execution. Notably, this vulnerability has been exploited by NodeZero – an autonomous penetration testing product, according to researchers. In some cases, the product was not only able to execute code remotely but compromised domain administrator accounts.
Insights:
- This vulnerability can enable attackers to easily take over a network given they already have initial access. The attackers could also exploit this vulnerability to deploy additional malware including ransomware, exfiltrate sensitive business data, or disrupt the business operations of an affected organization.
- According to researchers who discovered the bug the vulnerability is easy to exploit and does not require prior knowledge. In addition, the exploitation is not easy to detect since it makes use of the natural behaviour of the ADAudit Plus application.
- They also highlight that ADAudit Plus remains an attractive target for threat actors due to its integration with Active Directory and access to high-privileged domain user credentials. An attacker having initial access to a compromised network could exploit this vulnerability to exfiltrate high-privileged data, perform lateral movement and take over the network entirely.
Data Leaks
More Similar Leaks Follow After 1 billion Chinese Citizens Database Leak
- Attack Type: Data Leak, Potential Insider Threat
- Target Industry: Government
- Target Geography: China
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage, Regulatory Implications
Summary: After the reports of the leak from an anonymous threat actor selling databases that claim to have contained more than 22 terabytes of stolen information of roughly 1 billion Chinese individuals appeared, a few more similar leaks were observed by CTI. In one such leak, an unknown threat actor who claims to be from the Chinese Police department and was inspired by the aforementioned incident also leaked multiple “police databases” in an underground forum for free. On the same day, the same threat actor this time advertised another database for 1 BTC in the same underground forums which he claimed to be from the Henan National Police (HNGA). This database includes details of approximately 90 million Henan citizens containing PII such as Name, Age, Address, National Identification Number, and Mobile number.
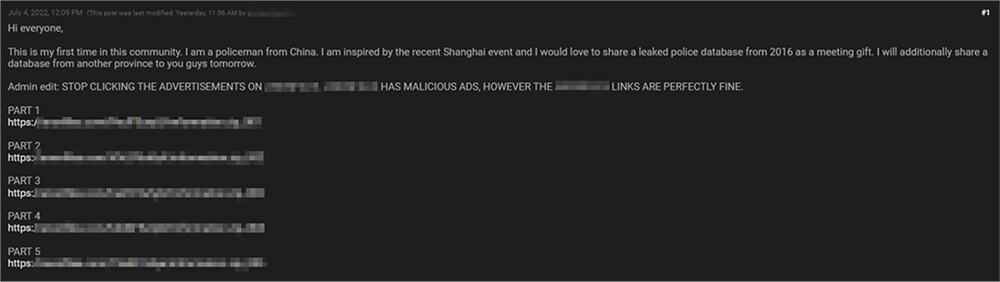
Source: Underground Forums
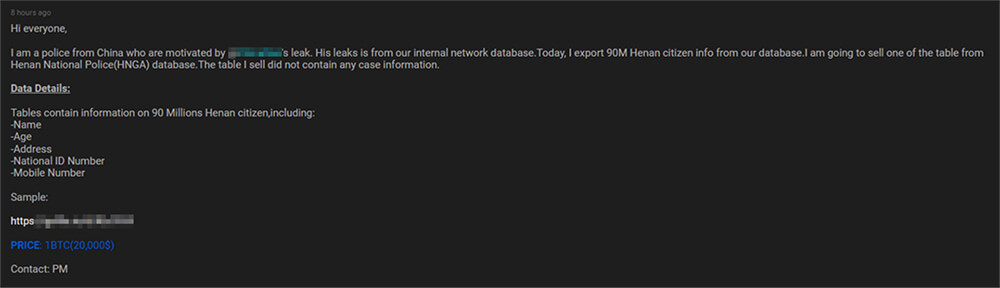
Source: Underground Forums
Insights:
- Some of the members of this underground cybercrime community are suspecting the well-known threat actor who uses the alias ATW (aka AgainstTheWest, Blue Hornet, APT49) is back in action. ATW is known to be operating campaigns and leaking datasets targeting Chinese entities and is a fairly active member of this community. However, these suspicions have not been confirmed yet.
- Opportunistic cybercriminals motivated by financial gains are always on the lookout for exposed and vulnerable systems and applications. The majority of these attackers operate in underground forums engaging in related conversations and buying/selling stolen digital goods. Unlike other financially motivated attackers such as ransomware groups or extortion groups who often publicize their attacks, these attackers like to operate under the hood. By taking advantage of an unpatched system or exploiting a vulnerability in an application or system – they gain access and steal valuable data. The stolen data is then advertised for sale in underground forums, resold, and repurposed by other attackers in their attacks.
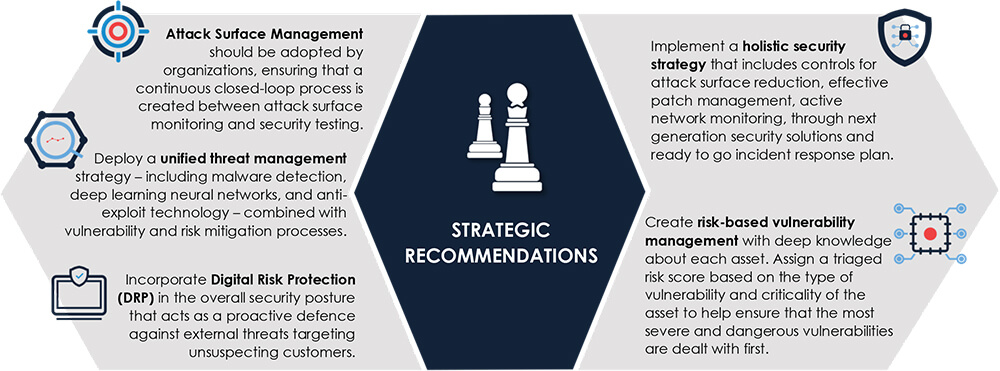
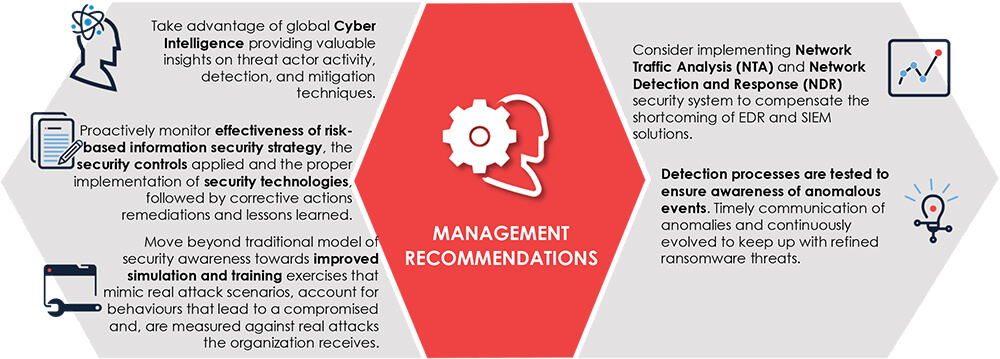
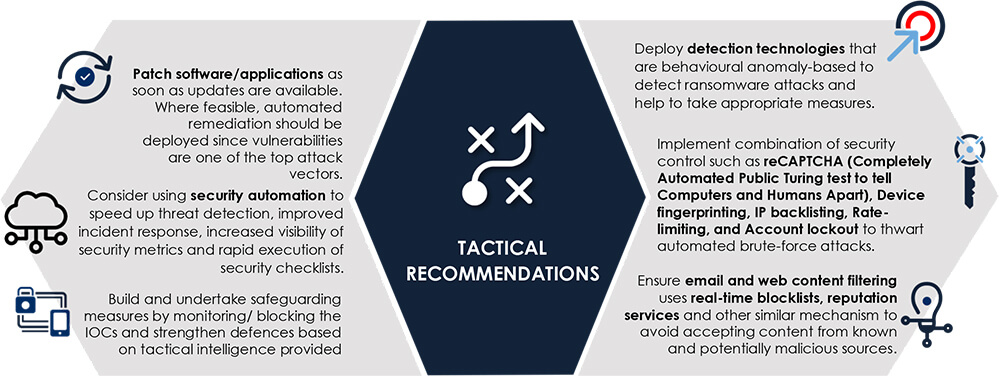
Recommendations [NEW]