



Threat Actor: TA505
Alias: ATK 103, Chimborazo, Evil Corp, Gold Evergreen, Gold Tahoe, Graceful Spider, Hive0065, SectorJ04, TA 505, TA-505, TA505
Origin: Russia
Description: The threat actor is a well-established financial crime group that has recently focused its operations on ransomware and extortion. The group has been active since 2008. They are notable not for their sophistication, but for the sheer volume of extraordinary messages they send. The group has leveraged a number of malware as part of their campaign, and this also shows their deep connections to underground malware resources. The threat actor is also believed to have an infrastructure that overlaps with other threat actors.
Targeted Countries: Australia, Canada, Czech Republic, Germany, Hungary, India, Japan, Romania, Serbia, Singapore, South Korea, Spain, Thailand, Turkey, UK, and the US
Targeted Industries: Education, Financial, Healthcare, Hospitality, Restaurants, Retail, Supply Chain
Tools/ Malware: The group has been known to utilize the following tools and malware in their attacks chain
FlowerPippi, Locky Ransomware, AndroMut, GameOver Zeus, Gelup, Dudear, Get2, Bart, Amadey, CryptoLocker, EmailStealer, FlawedGrace, GlobeImposter, Shifu, EmailStealer, TinyMet, Shifu Trojan, SDBbot, Jaff, GameOver Zeus, RMS, Amadey, Dridex, FlawedAmmyy, FlawedAmmy RAT, Bart, Philadelphia, Zeus, Clop Ransomware, FlowerPippi, Dridex Malware, GlobeImposter Ransomware, FlawedGrace, Locky Ransomware, Dudear, CryptoLocker, CryptoMix, RockLoader, Snatch, AndroMut, Pony, Gelup, ServHelper, MINEBRIDGE, Kegotip, Get2, Jaff Ransomware, Neutrino
Motive: Financial Crime, Financial Gains, Espionage
Recent Activity:
The threat actor has launched a new ransomware dubbed Macaw Locker to evade US sanctions that prevent victims from making ransom payments. In two of the attacks, it was observed that the threat actors demanded a 450 bitcoin ransom, about USD 28 million, for one attack and USD 40 million for the other victim. The Macaw Locker seems to have evolved from Wasted Locker ransomware; it encrypts victims’ files and appends the .macaw extension to the file name when launching attacks.
These recent campaigns are tracked by CYFIRMA and are believed to be active during the following time frame:
Out of the 5 campaigns observed by CTI this year – attributed to TA505 – most campaigns were targeted at multiple counties across the globe. Almost all the campaigns targeted multiple nation-states.
TA505 attacked a total of 35 different nations in only 5 campaigns observed by CTI which is unusual when compared to other threat actor groups who often restrict their efforts to geographies of their interest and attack them repeatedly. Further, the campaign UNC054 targeted 29 countries.
The figure below illustrates all the counties which were targeted in these campaigns.
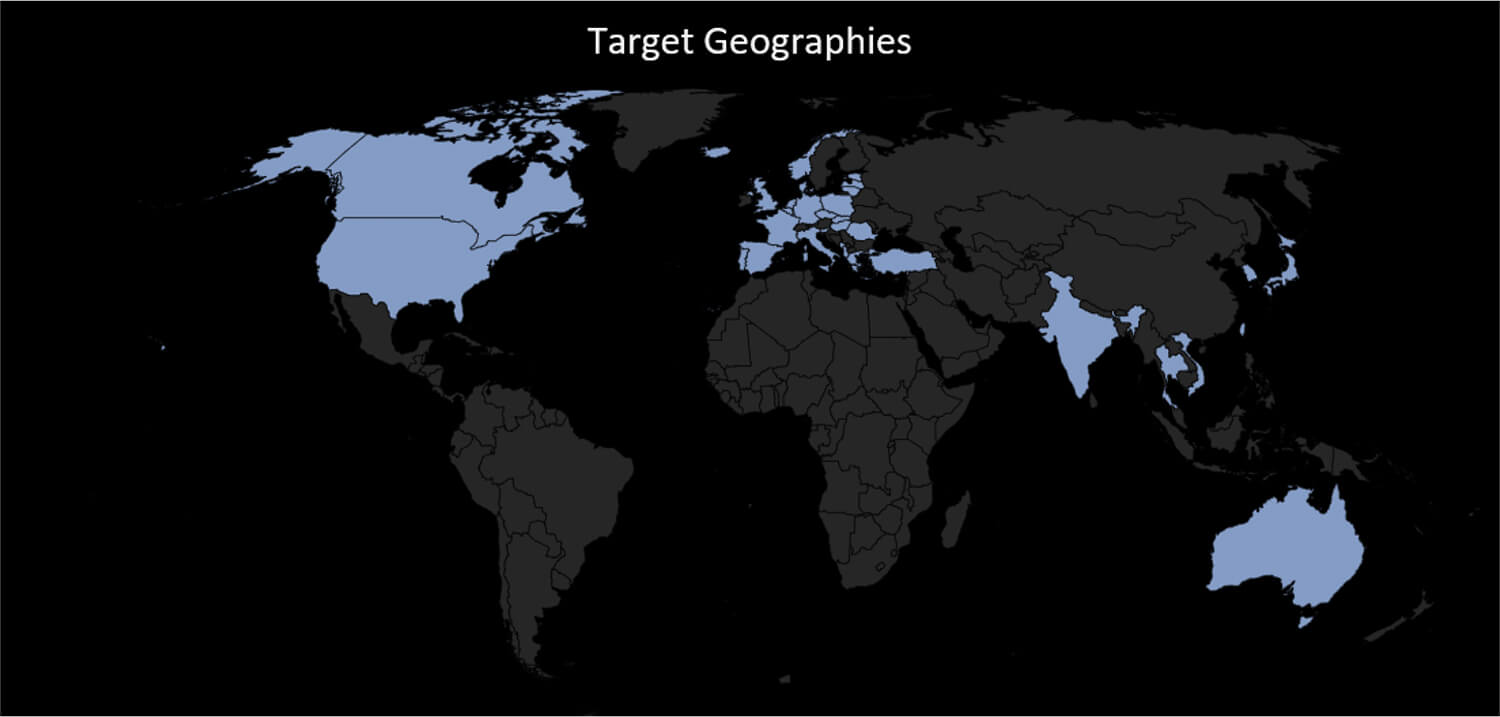
The following figure illustrates the targeted countries which were subject to the TA505 campaigns.
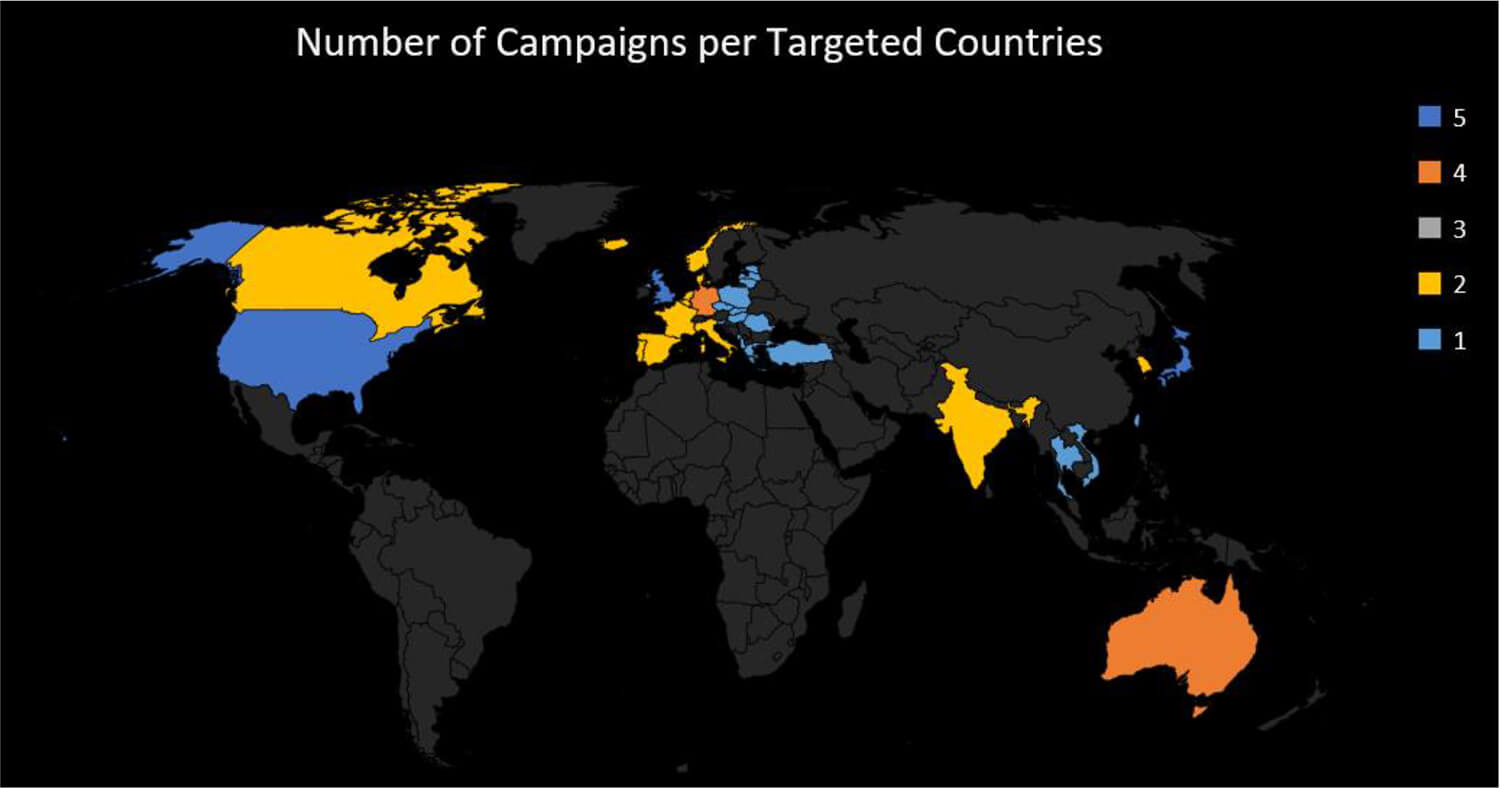
The United States, Japan, and the United Kingdom have been the top targets for TA505 and were targeted in all the five campaigns.
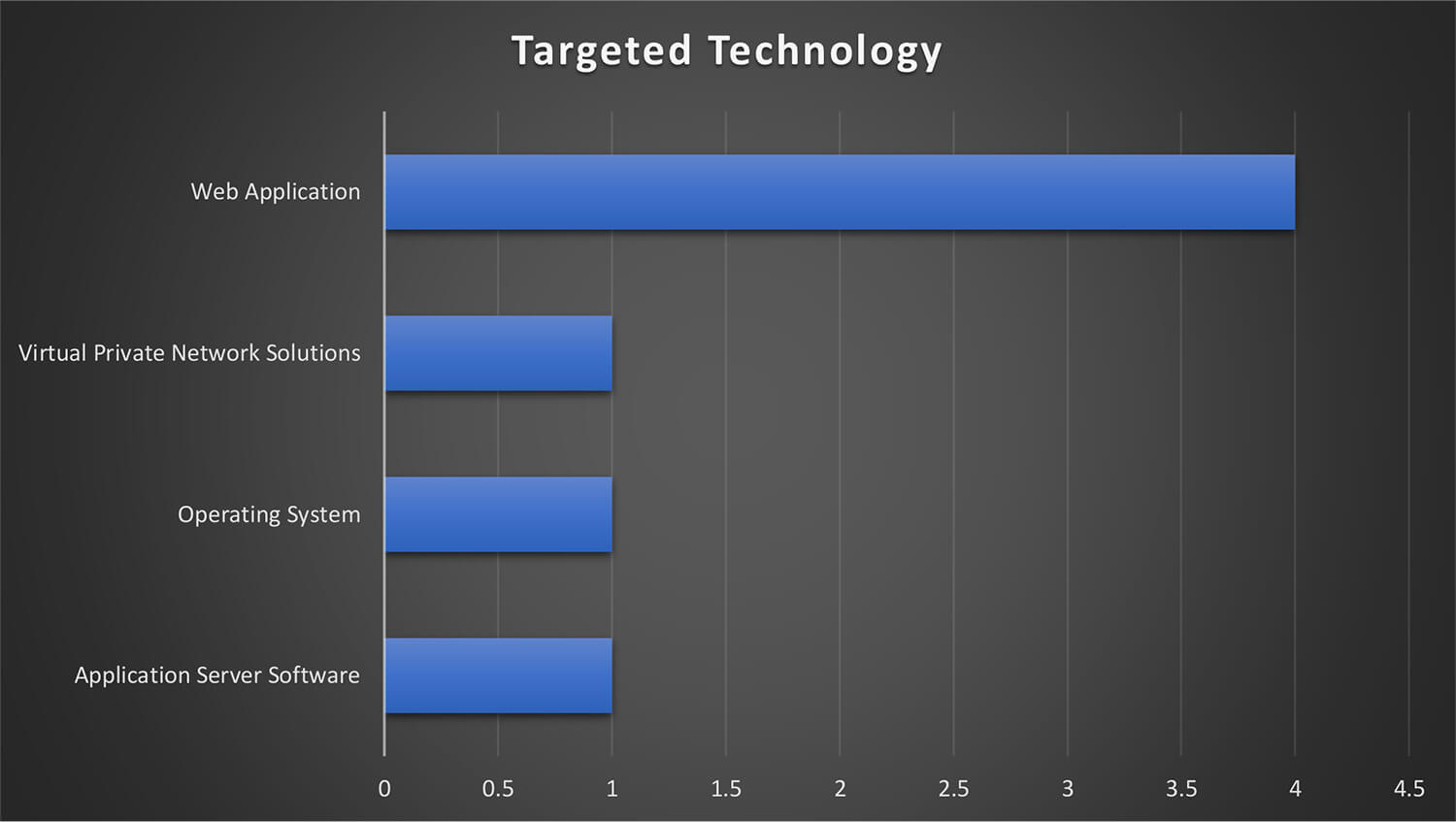
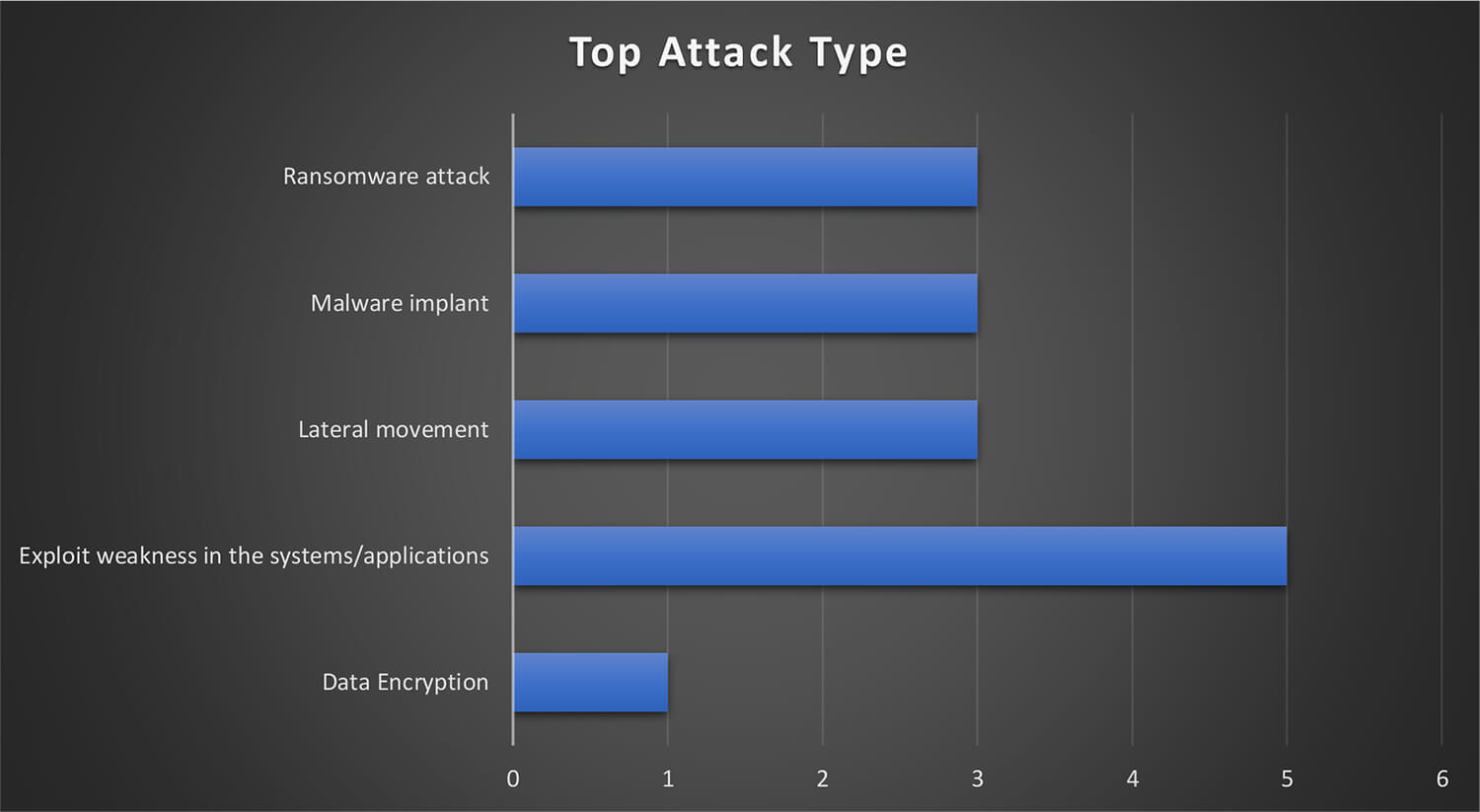
The TA505 leveraged vulnerabilities in Web Application, Virtual Private Network Solutions, Application Server Software, and Operating Systems to infiltrate the network and systems of potential victims.
The figure illustrates the technologies that were targeted by the threat actor group during these campaigns. From the trends, it can be observed that exploiting weaknesses in web application-related software and products is the most favoured method by the TA505.
From the campaign observed by CTI in 2022, TA505 attacked organizations from more than 25+ industry verticals. The targeted list of industries includes:
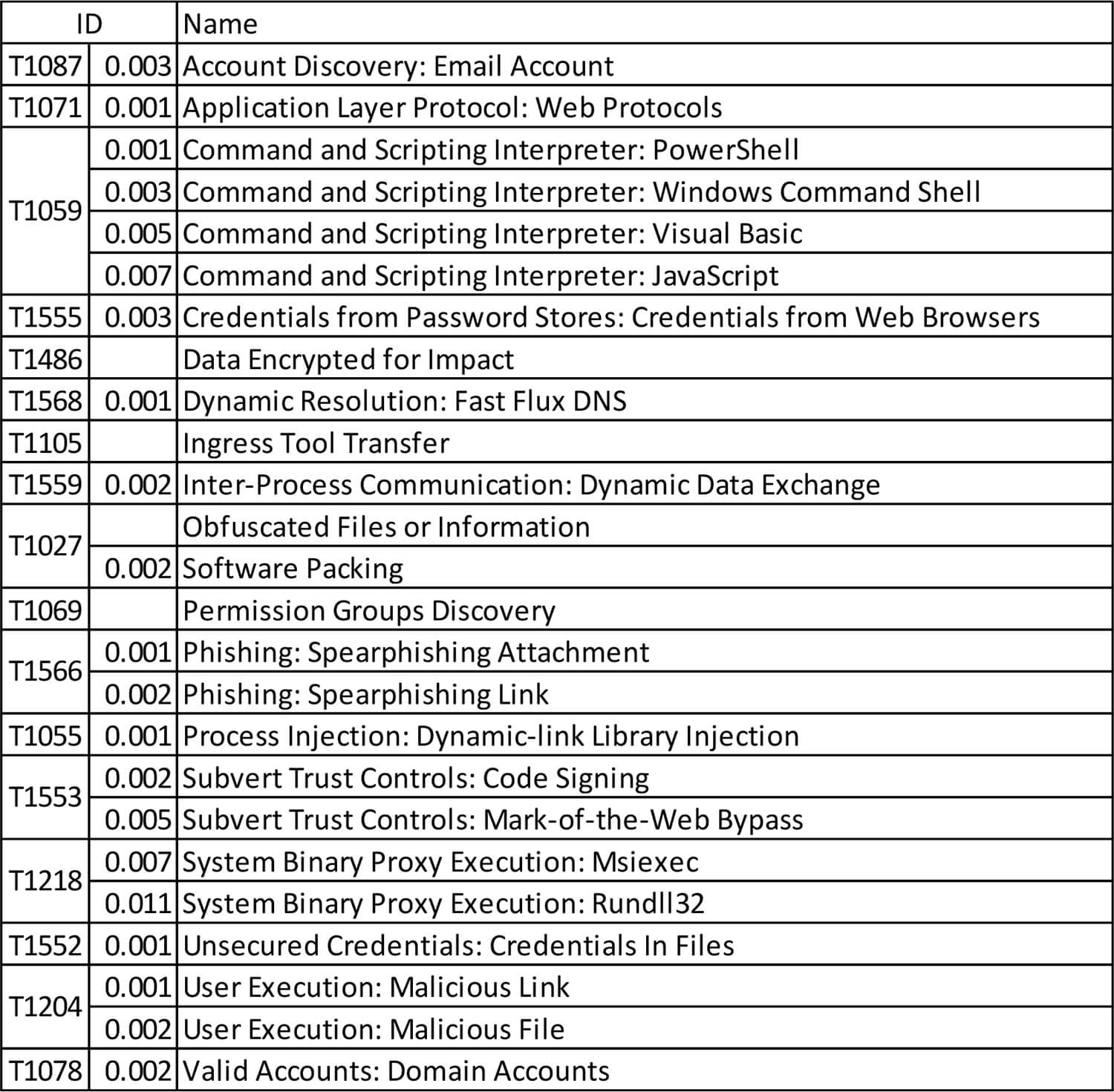
Below is the list of all the malware used by TA505 in their campaigns.
The Dridex malware appears to be the go-to choice for TA505. In the campaign observed by CTI the malware was used in 4 out of 5 campaigns.
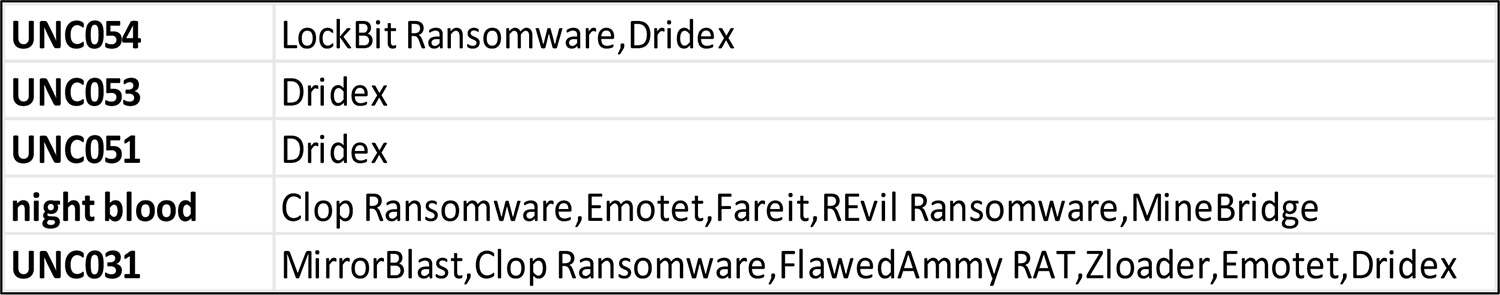
All of the observed campaigns carried out by the TA505 involved heavy use of exploiting vulnerabilities in internet-exposed systems or applications and the use of ransomware implants among other malware was also a common tactic.
CTI has observed Russian cybercriminal groups, such as TA505 and its affiliates, collaborate with and leverage ransomware groups such as Conti, LockBit, REvil, etc. as part of the Ransomware-as-a-Service (RaaS) model. Recently, researchers and law enforcement agencies have correlated TA505 aka Evil Corp leveraging LockBit ransomware under the RaaS model to target organizations.
CYFIRMA has observed TA505 targeting organizations in Critical Infrastructure, Energy, Mining, and Manufacturing industries leveraging potential ransomware such as LockBit for reconnaissance or potential attacks under CYFIRMA tracked campaigns UNC053 and UNC054. These campaigns are suspected to be potential retribution from Russia against nations who have imposed sanctions on them due to the ongoing Russia – Ukraine conflict.